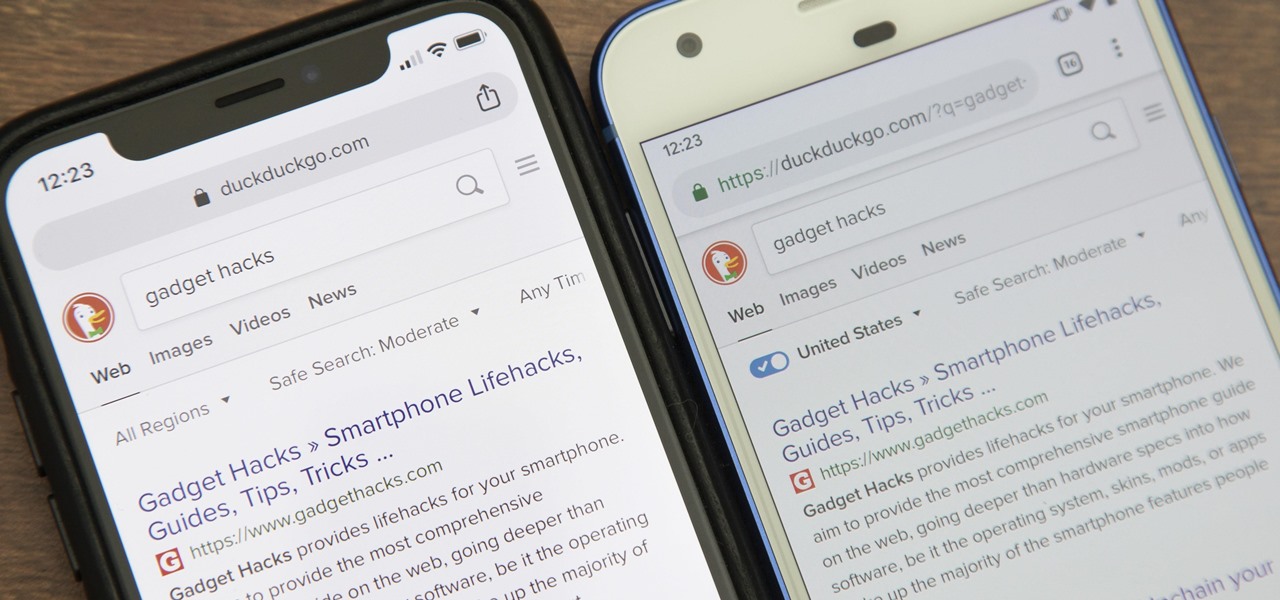
While Google would rather you use Google as the default search engine in Chrome, there's a way to switch to the more privacy-geared DuckDuckGo search engine for all your web browsing needs. With DuckDuckGo, the company does not track anything you search or allow anyone else to track it, so you can effectively search from your iPhone or Android phone anonymously.

While TouchWiz as an Android skin isn't a favorite among many, Samsung Internet is a fantastic web browser that S9 owners should be happy to have preinstalled out of the box. But you don't need to buy Samsung's latest flagship to try their browser — Samsung Internet is available to all compatible Android phones.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.
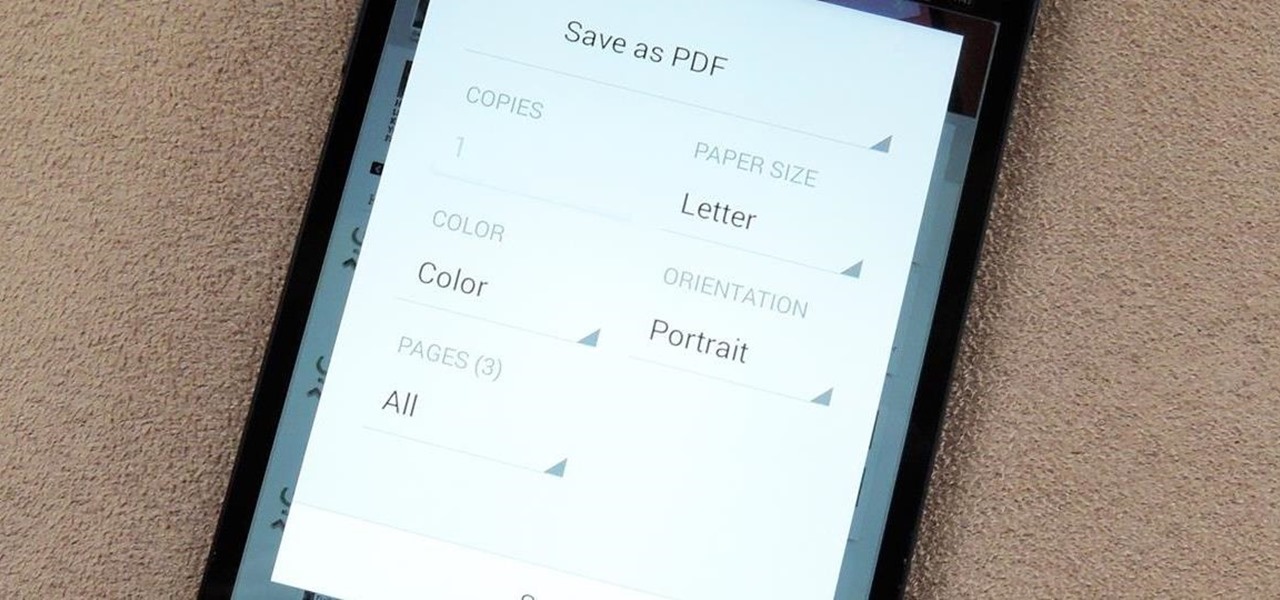
You may not always be connected to the internet, but if you're anything like me, your thirst for web content is insatiable. Whether you're on an airplane or stuck in an area with no reception, having some offline content stored on your Nexus can definitely save the day.
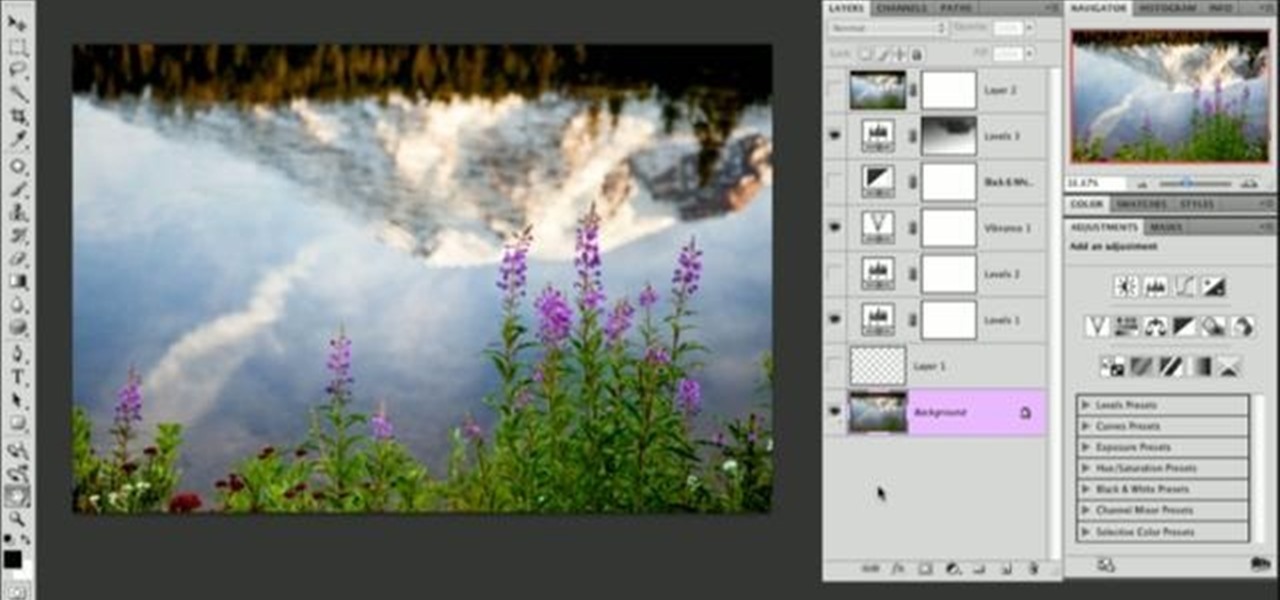
Learn how to toggle layer visibility in Photoshop in this video tutorial. Nocole Young will show you how to do this easily. When you are working on any image in Photoshop, you usually create a number of layers. You would like to see what the image will look like before you start editing the image. You can always toggle the visibility between the layers by clicking the ‘eye-ball’ toggle on the right hand side of the page on the layer panel. Click the ‘eye-ball’ toggle next to a layer and you w...

How to install Java JDK (Java Development Kit) Go to the Oracle Java SE Download Page and click "Download".

Ever find a really cool article on the web that you'd like to read next time you are out and about, waiting in line or riding the bus? Watch this video to learn how to use iCloud to share links between your computer and your iPhone.

Scouring the web for instructions on how to factor quadratic equations in algebra? Look no further. This free video algebra lesson will teach you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test).

Shallisubscribe teaches viewers how to change the slide to unlock words on the iphone! First, you need to jailbreak your iPhone or iPod Touch! Next, open up Cydia and search for 'iFile'. Next, after downloading this open up Cydia and search for 'Slide to Unlock Killer'. You will also want to download this. Next, open up iFile and at the top left corner press that button 'var'. Scroll down until you find the folder that reads 'stash'! Next, find the 'theme' folder and click on the 'Entriegel K...

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

This videos is a tutorial for using custom FBML coding on facebook fan page.The video begins by logging into facebook account.Then go to the search bar at the upper right hand corner and tpe "static fbml" and hit enter.This takes to the application page and click on "add to my page" below the default fbml picture.A window opens up showing a list of user pages and after selecting the page click on "add to page".Close the window and go to your fan page and click on "edit page".This shows a list...

This video instructs you on how to backup your files on windows 7. To do this, first you must go to Start>Control Panel. After that you must look at System and Security, and click on back up your computer. Next you must click set up back up, then pick where you want to save your files and click next. In the video, ComputerRepairexpert uses a external hard drive, which is strongly suggested. On the next screen you must pick how you want it backed up. Click on Let me choose and click next. Afte...

In this Computers & Programming video tutorial you are going to learn how to configure Windows Netmeeting. It is very easy to do. This video is from Fix PC Freeze. Go to start > all programs > accessories > windows explorer. Now click on SA(C:) > program files > Hewlett-Packard > Netmeeting > conf. On the NetMeeting installation dialog box click next and type in your name, email and other details and click ‘next’ twice. On the following box, select ‘local area network’ and click ‘next’ thrice...

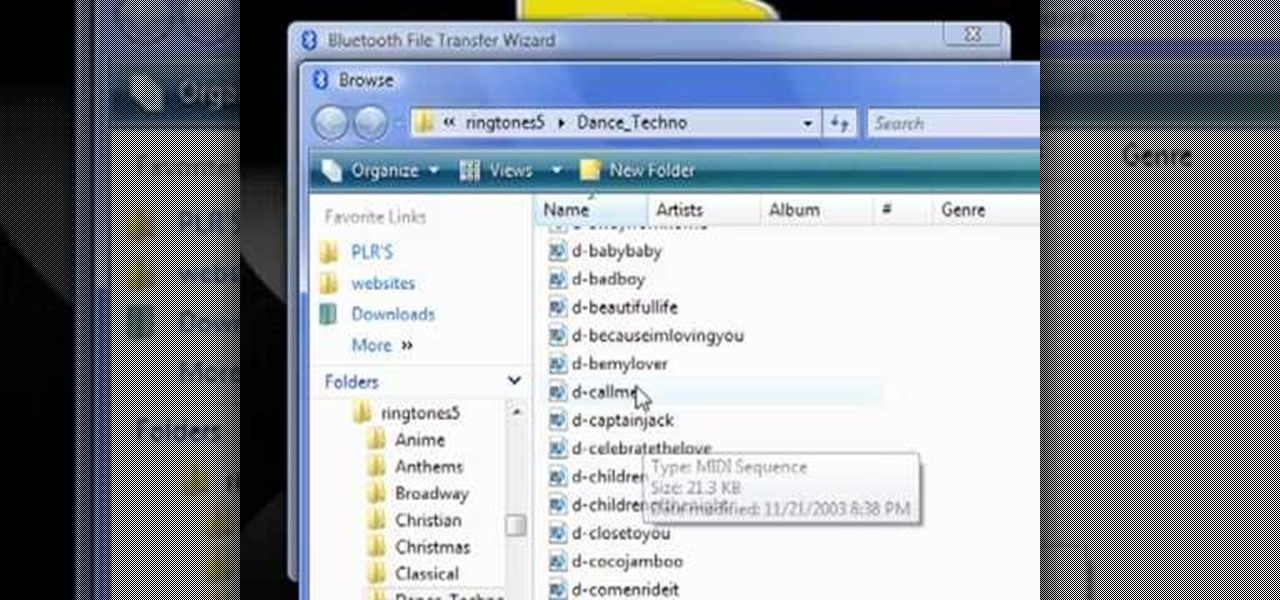
The video demonstrates how to connect your Bluetooth phone to your computer and send/receive files between them through Bluetooth. You need to first switch on Bluetooth in your phone and then click on the icon for Bluetooth connectivity in the computer. Then click on the option called 'Add a Bluetooth Device'. You can see a setup wizard pop up in your computer screen where you have click on the check box and then click on Next button. Once the phone is detected, select it and click on Next. T...

Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

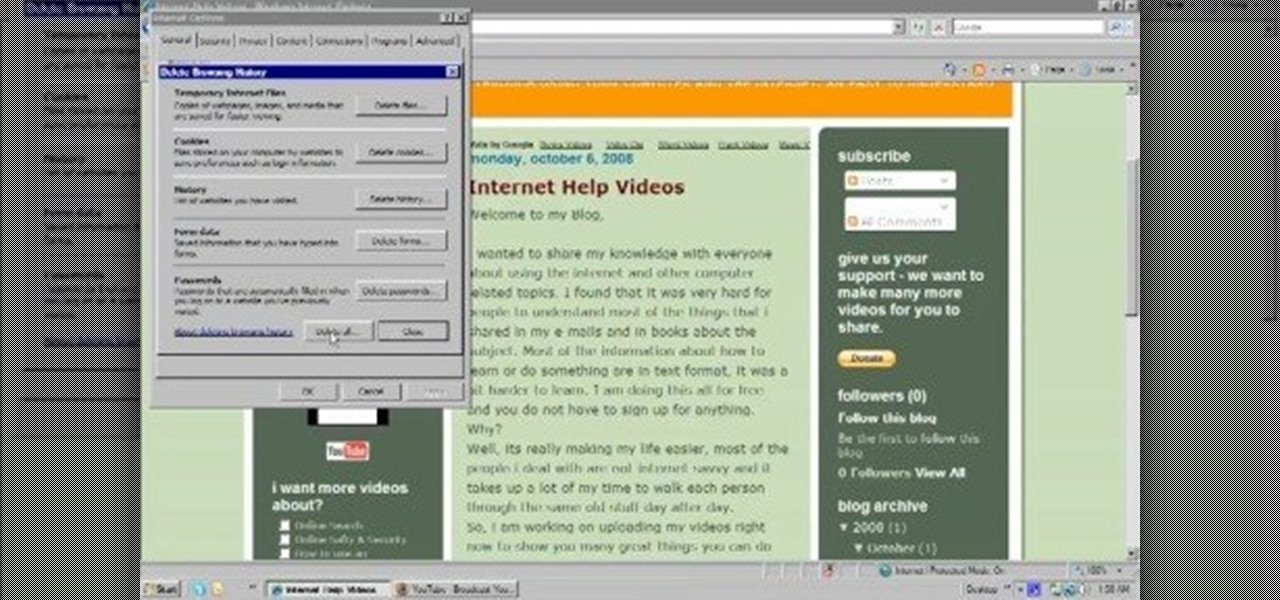
In this video, we learn how to delete browsing history, cache, and cookies. First, go to your internet browser and click on "tools". After this, go to the internet options, then go to "delete". After this, you will see different sections of things you can delete on your computer, with brief descriptions underneath all of them. If you want to delete it all, click on the bottom on the bottom of the window, then it will start to load and when finished you can exit out of the window. After this, ...

Ninja-Pi-Ro is a point-and click adventure game on PencilKids where you play as the ultimate geek character: a shapeshifting ninja-pirate-robot. This video will walk you through the entire game.

This clip will show you how to add external CSS stylesheets to an HTML document in a number of different ways while explaining the significance of ordering. Whether you're using a fancy WYSIWYG (or what-you-see-is-what-you-get) page editor like Adobe Dreamweaver CS5 or a barebones text editor like Notepad, if you want to build websites, you'll need to have some understanding of HTML (for the structure of your web pages) and CSS (for their style). And this free coder's guide will get you start...

Forget tables, start using list items and some css to start styling your forms. In this CSS tutorial, you learn just that. Whether you're using a fancy WYSIWYG (or what-you-see-is-what-you-get) page editor like Adobe Dreamweaver CS5 or a barebones text editor like Notepad, if you want to build websites, you'll need to have some understanding of HTML (for the structure of your web pages) and CSS (for their style). And this free coder's guide will get you started along that path.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.

Two companies armed with web-based augmented reality tools, Vertebrae and Shopify, are ready to help online retailers boost their sales.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

Magic Leap loves to stoke mystery around its still unreleased product, the Magic Leap One: Creator Edition, and now we've found yet another piece of the puzzle in the form of an Easter egg on the company's website.

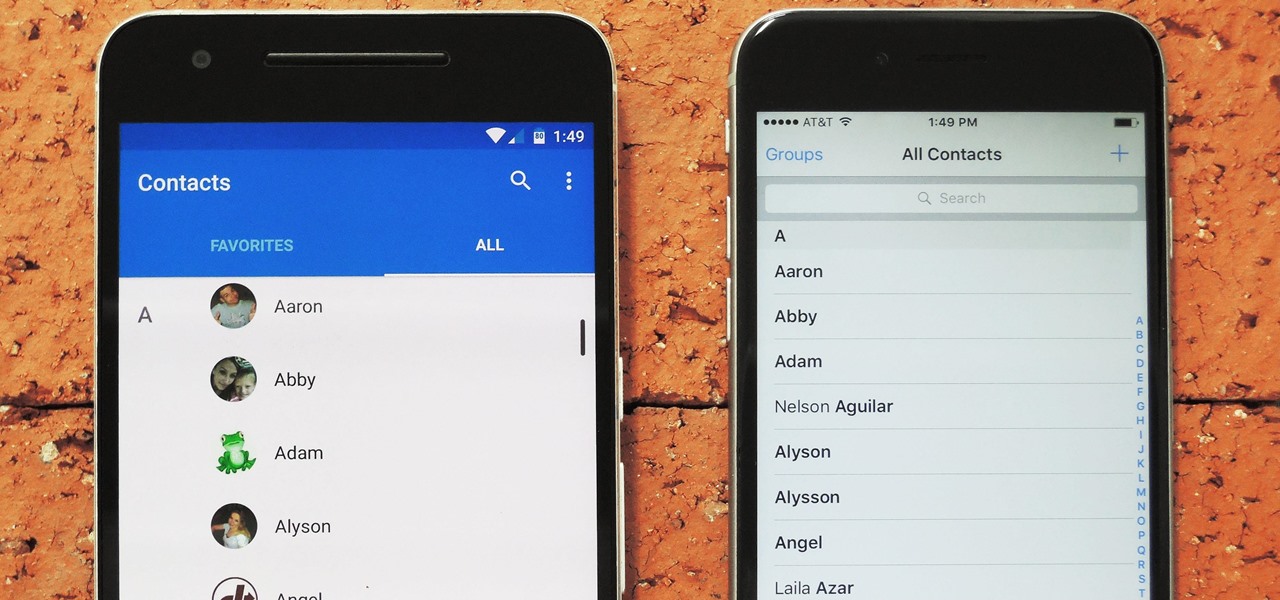
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're restoring to a previous iTunes backup, or just want to remove it from your list of iCloud devices.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

This video describes how to make a system restore point. First we have to go to click the start on the keyboard. Next select the computer and go for the properties. Next go to system protection. Next go the protection settings and highlight the operating system and give option of “on” on the protection and just click the create. Then you will get a box of system protection. Next you can give a name and then click ok to that it will take some time. Next if you go for system properties you ...

OCR is usually a bad word to most computer users, but in Acrobat it's the next best thing to sliced bread. Adobe Acrobat 7 Professional not only employs Optical Character Recognition for your text, it does Page Recognition to preserve the geometry of your pages. Everything stays in place and your paper documents become searchable, reusable text!

There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders.

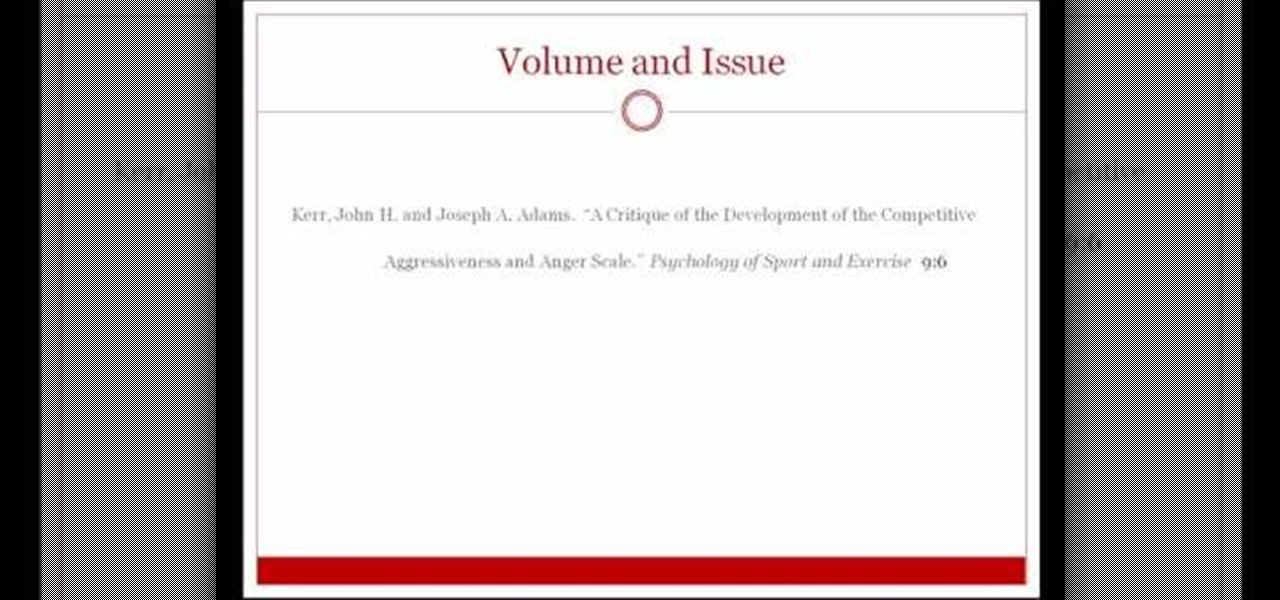
This video shows viewers how to properly cite scholarly journal articles in the MLA format. In your works cited page, the citation should begin by placing the author's last name first, followed by his first name. If there are multiple authors, all subsequent authors should have their first name first followed by their last name. Placing a period after this, the next item is the title of the article, placed in quotation marks and followed by a period. The name of the scholarly journal is place...

In order to prevent accidental CAP LOCKS, you can use a number of new, innovative and free software solutions. With your Windows 7, there are functions available to assist you.