In this video tutorial, viewers learn how to unzip a zipped file using the 7-Zip extraction tool. Begin by going to the website and click on the Download link. Wait for the screen to load and click on Save File. Once downloaded, double-click on the file and follow the instructions to install it. Now simply right-click the zipped file. Go to 7-Zip and select either Extract files or Extract Here. The files will be extracted into a new folder that contains all the content...

In this video tutorial, viewers learn how to eject and recover a stuck CD or DVD on a Mac computer. There are several ways to eject a disc. The first method is to click on File and select Eject. The second method is to press the Command and E buttons on the keyboard. The third method is to click on the disc and drag it to the eject icon in the dock. The fourth method is to access Disc Utility in the Utility folder. Then click on the disc drive and click on the eject button. This video will be...

Guide dogs are trained to help the visually impaired or people who are completely blind. Learn how guide dogs are trained from a training expert in this free educational video series.

This is a Photoshop tutorial for digital photographers. Putting a grunge effect on your image is simple to do. Creating the grunge backgrounds is even simpler. Just watch the tutorial to see how easy it is to get this effect.

This is a Photoshop tutorial for digital photographers. Learn how to fix flash highlights. Here's a technique that will help you to fix the highlights that are created when taking flash photography.

Light up your keyboard with this illuminating tutorial from Make Magazine's Kipkay. To get started on this hack, which should take roughly a half an hour and cost no more than $5, you'll need the following: (1) a regular computer keyboard (most any model will do), (2) a screwdriver, (3) a drill, (4) telephone wire, (5) heat shrink tubing, and (6) two 5 mm high-brightness, white LEDs. For comprehensive, step-by-step instructions on building your own light-up keyboard, simply watch this hacker'...

PICC stands for a peripherally inserted central catheter, and is usually inserted somewhere in your patient's uppper arm, giving access to the larger veins in the chest region. PICC lines are often desirable because they are the least risky way of giving central access to the veins near the heart, especially when your patient will need to have one for an extended period of time. This tutorial shows you everything you'll need to know about how to properly and safely insert a PICC line into you...

For 3D artists new to 3DS Max, learning your way around this massive piece of software can take a long time. It need not do. This video will teach you how to use some of the many hotkeys in the program to navigate it like a pro, easily accessing all of the most popular tools and allowing you to save a lot of time modeling. Now that you know what buttons to press to access functions, watch some of our other 3DS Max tutorials for more advanced functions.

In order to build a good chuck box, you will need to do a lot of planning in advance, in order to make sure that you have the essentials and keep the weight of your chuck box down.

In her video, Carol describes her skin care regimen, which she claims has been very effective in treating her acne and improving her skin. This regimen is for acne-prone / combination skin types and involves the use of multiple products, including cleansers, scrubs, masques, washes and moisturizers. Carol takes us through her morning, evening and weekly cleansing routines, explaining which of various products she uses for each such routine. She also discusses each product, explaining its stre...

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Just watch this video tutorial with loads of easy to understand information about how to use and understand Apple's iPhone, For Dummies.

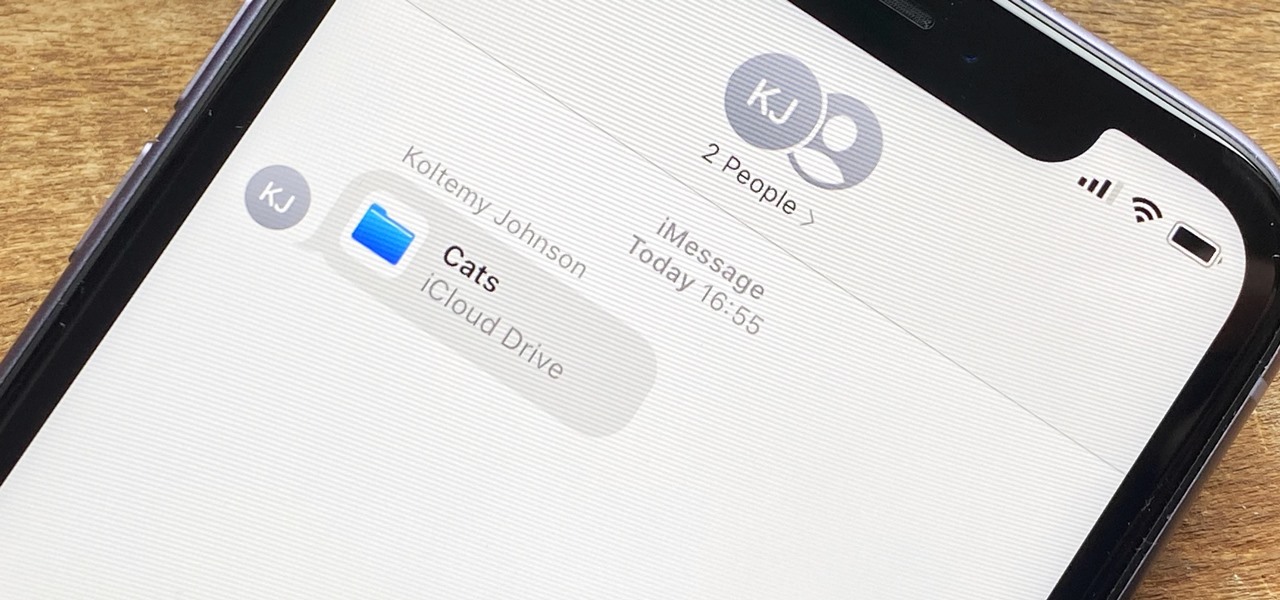
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

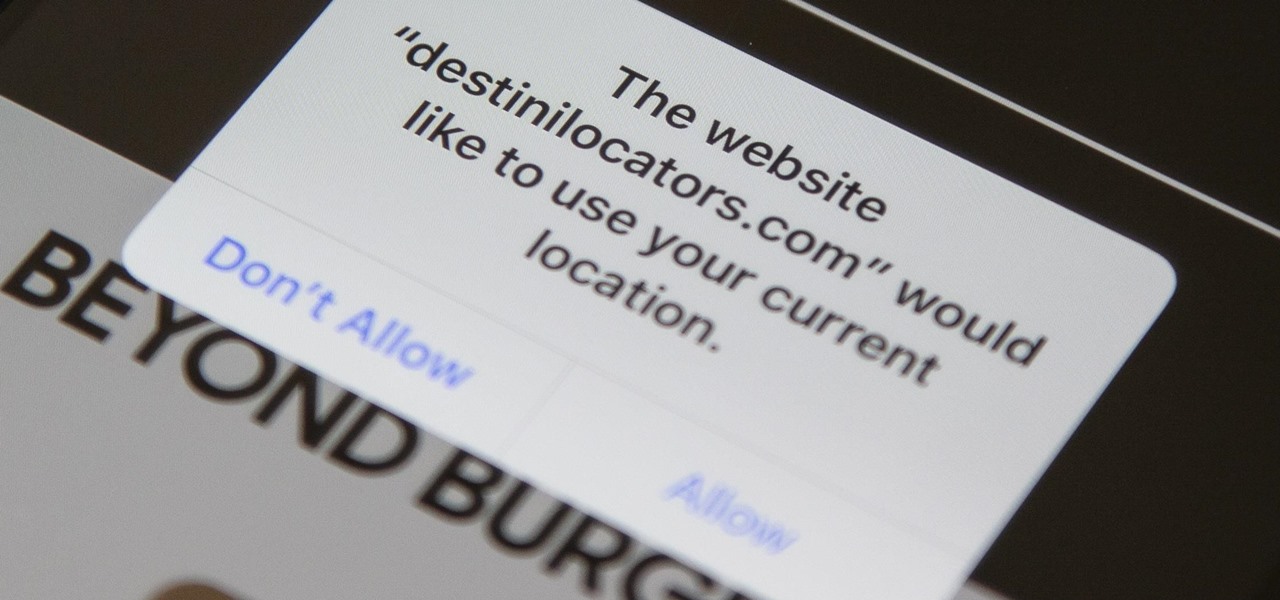
In iOS 13, Safari has become even more powerful, especially when it comes to privacy. The browser will warn you when you create a weak password for a new account. Your history and synced tabs in iCloud are end-to-end encrypted now. And there are per-site settings that let you choose which domains can and can't have permission to use particular device hardware or sensors.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

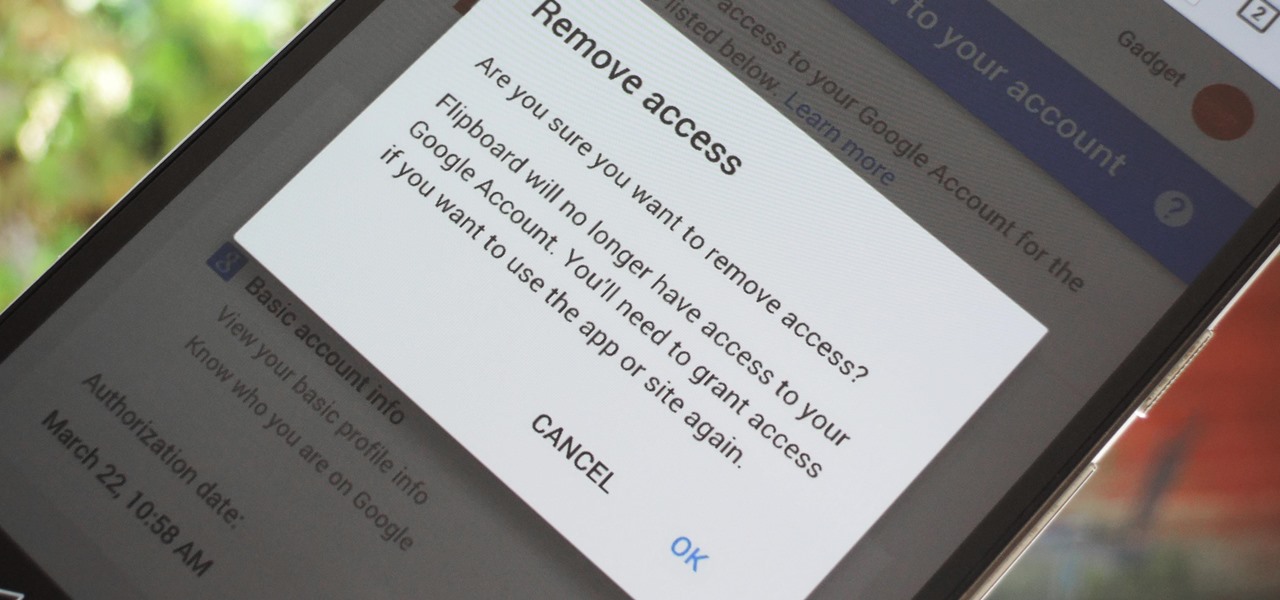
Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

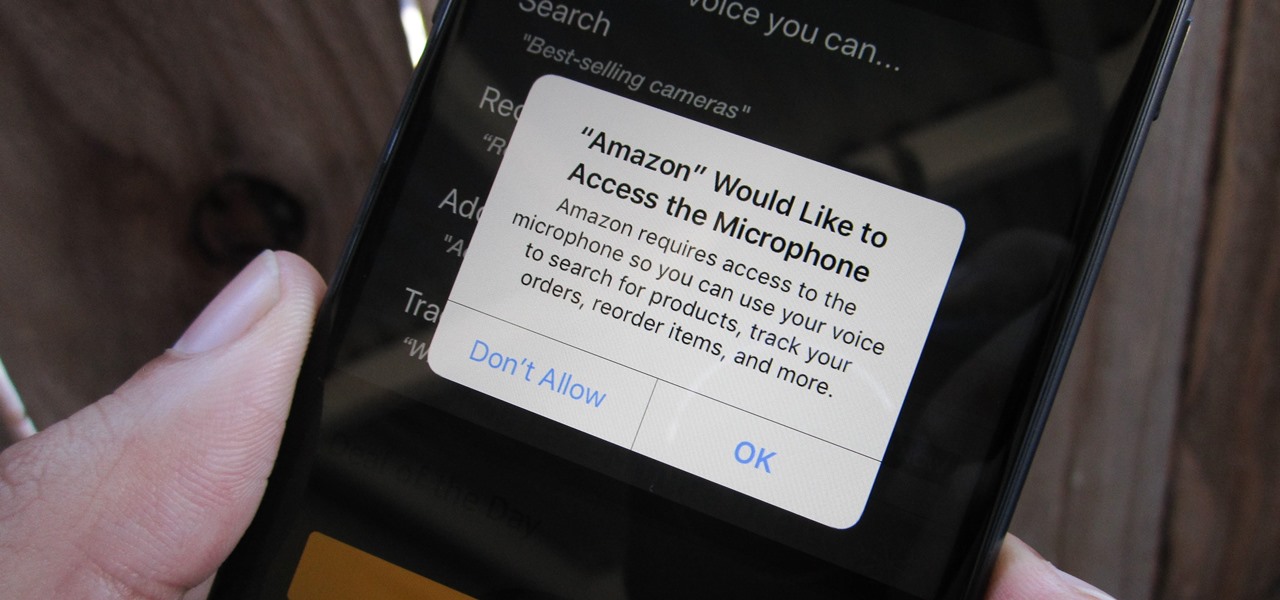
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Many apps and services that are available for Android can only work if they have access to your Google account. While you're setting up one of these apps, you'll see a popup that says something like "This app would like to access your Google account," and the options are "Accept" or "Cancel." Of course we tap "Accept" here to ensure that the app will work properly, but what are the long-term repercussions of doing that?

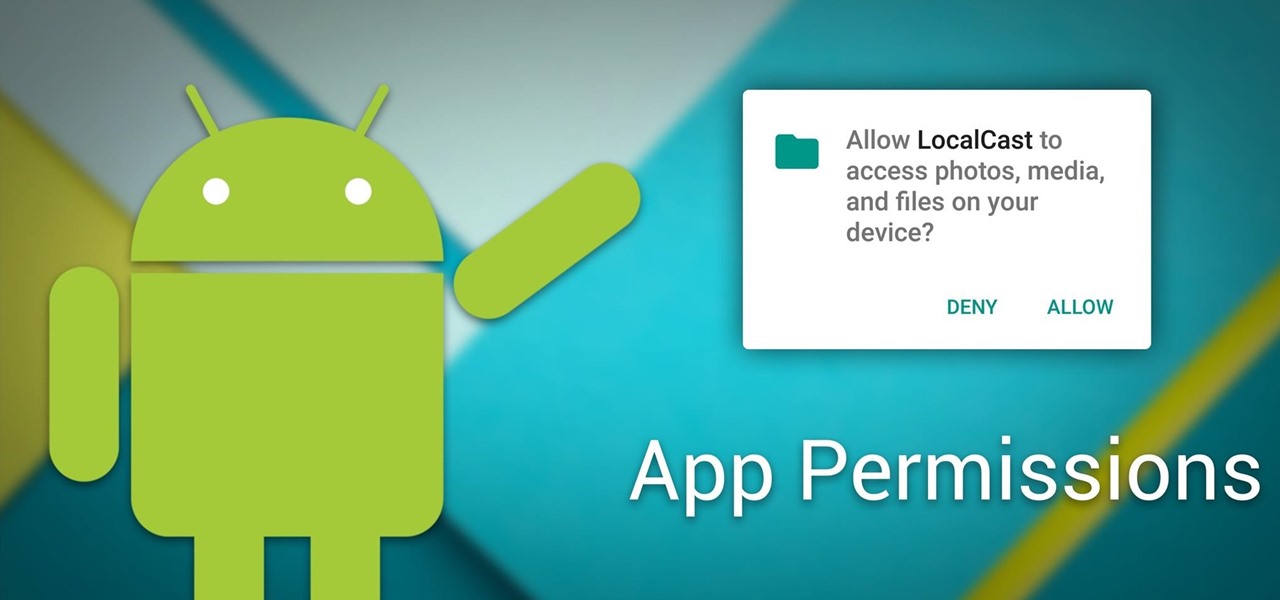
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

The Google Now gesture included in the Google Now Launcher and on Nexus devices isn't something I regularly utilize, and you might not either. There is a way to disable it, which is a good idea if you were executing it accidentally, but what's even better than disabling it? Repurposing it!

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

OnePlus One's CyanogenMod firmware comes packed with personalization options that standard Android devices could only achieve with root-level access. By simply entering the Settings app, OPO owners can make changes to their lock screen, status bar, and notification drawer, as well as apply themes and gestures to make their device a little more customized.

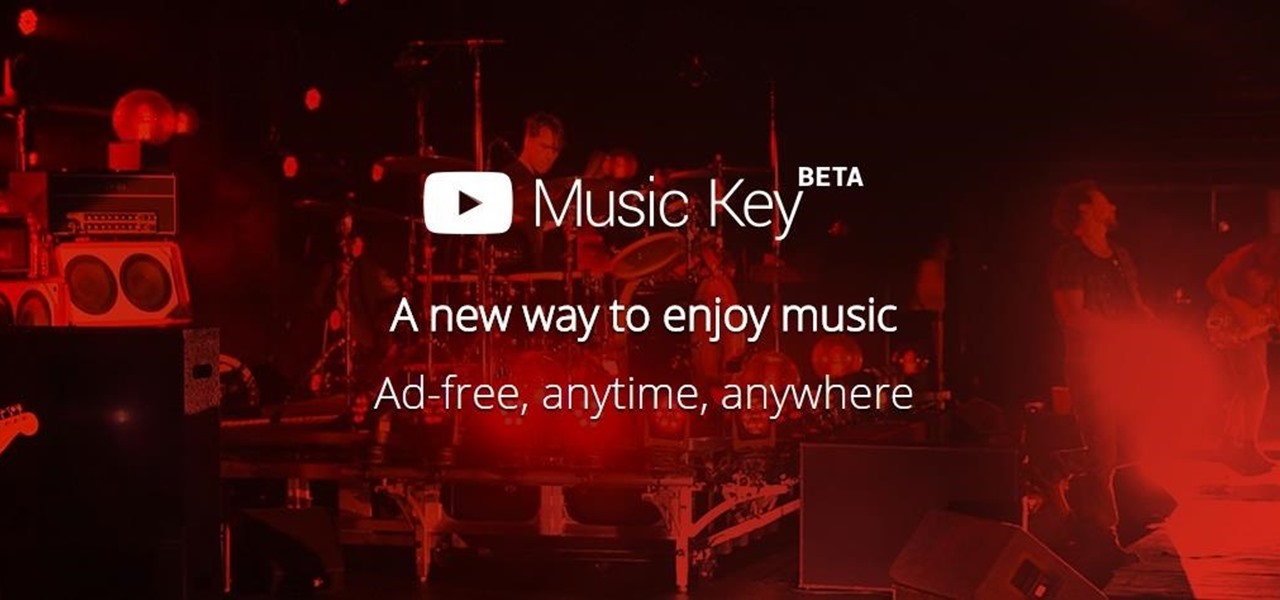
It's been rumored for months, but now we've got some official news about Google's newest music offering, YouTube Music Key. The subscription service will allow for an ad-free experience with background listening (i.e., having your screen off) and offline playback.

Accessing your recent contacts just became a hell of a lot quicker with iOS 8. In addition to accessing recent apps, double-pressing your Home button now shows off recent contacts at the top of your screen.

Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

In a nutshell Bocas del Toro is an arcipelago on the Carribean coast of Panama. It's located about 20 mi south of the Costa Rican border and you can get there from both San Jose and Panama City. The main islands are Colon, Bastimentos, and Carenero, but there are over 100 islands you can explore by boat.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

If you've ever jailbroken an iPhone, iPad or iPod Touch, then you're probably already well acquainted with PwnageTool. What you may not know, however, is that, thanks to the efforts of an iPhone hacker named Johnny Franks, there now exists a PwnageTool bundle for the beta version of iOS 4.3, iOS 4.3b1.

In this tutorial, we learn how to quickly find your MAC address. This is the address that identifies your computer on a network. When you go to a campus, you will need to register your computer with a resnet so you can access the internet. To find the address, you will head to the Apple menu, then click 'about this MAC'. Click on the 'more' button and then click on 'network' and 'built in Ethernet'. This is the MAC address that you will need to register your computer, you may have a few of th...

In this video, we learn how to bypass WebSense at school using an http tunnel. First, open up Internet Explorer, then type in http tunnel and go to the website. Download the first link to your computer. Next, start the program and click on "free service". Now, open up the browser again and go to "internet options". Once you are on this, go to "connection", then "lan setting". Check to use a proxy server, then click "advanced", then enter in "http 127.0.01 port 1080". Click "ok", then exit out...

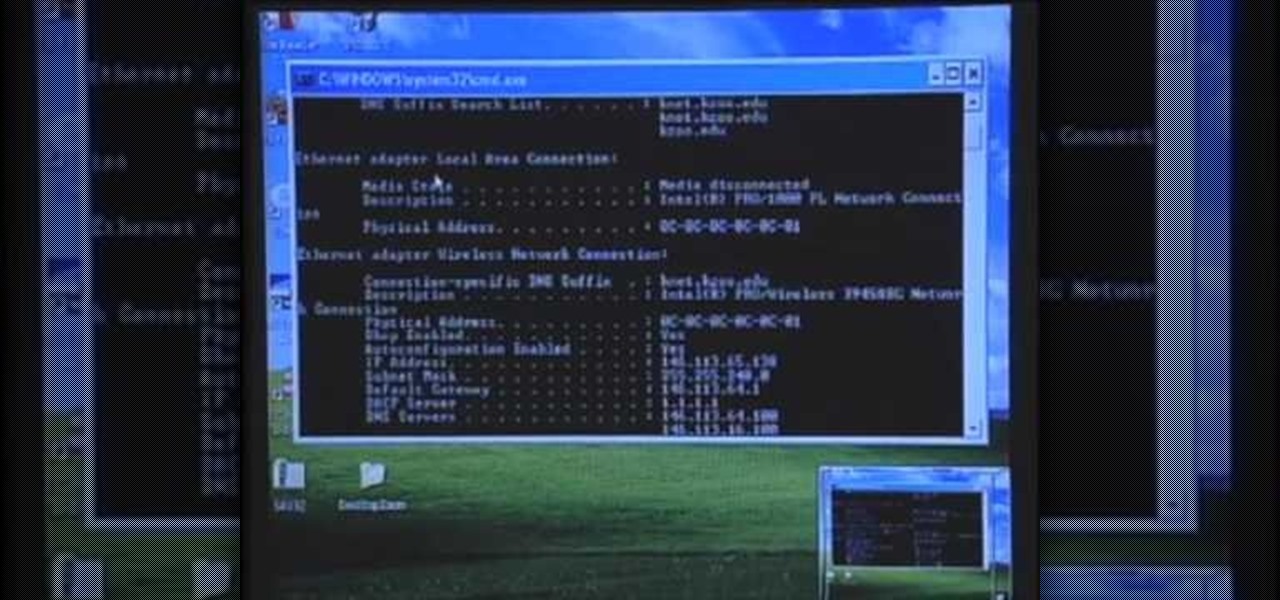
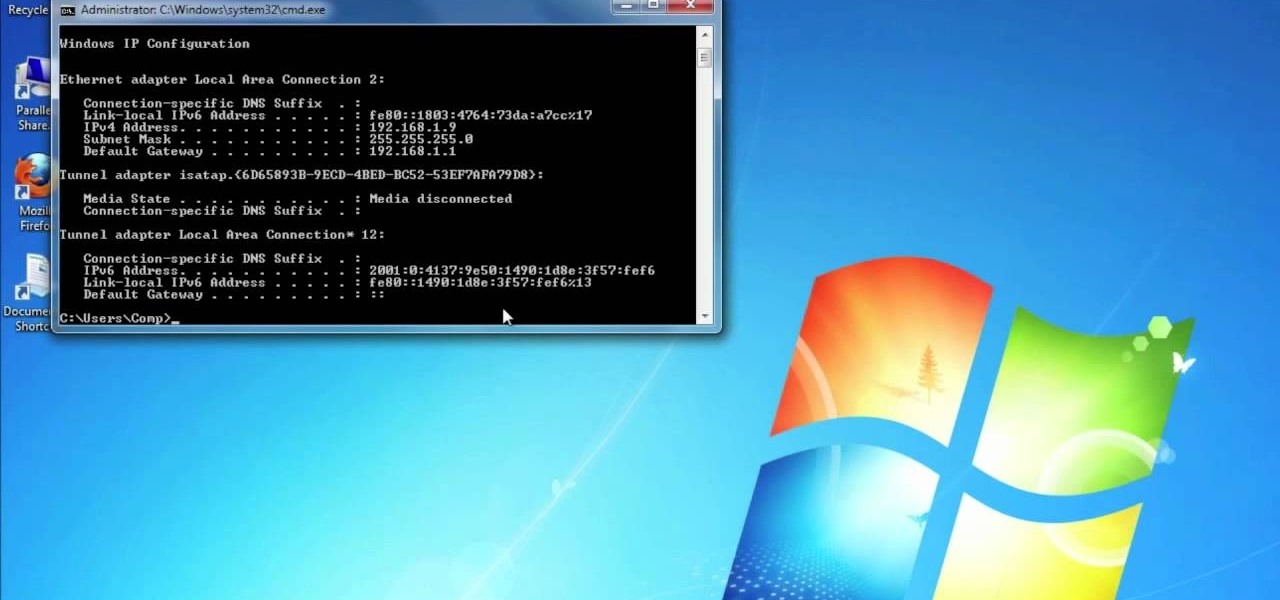
In this video tutorial, viewers learn how to find their I.P address in Windows 7 and Vista. Begin by clicking on the Start menu. Then type "cmd" into the search bar and press Enter. When the command prompt window opens, type in "ipconfig" and press the Enter button. Now search through the list and find a line that says "I.P address" or "IPv4 address". The numbers will be divided by periods. Another way is to open Control Panel and select Network and Sharing Center. Then click on your local ar...

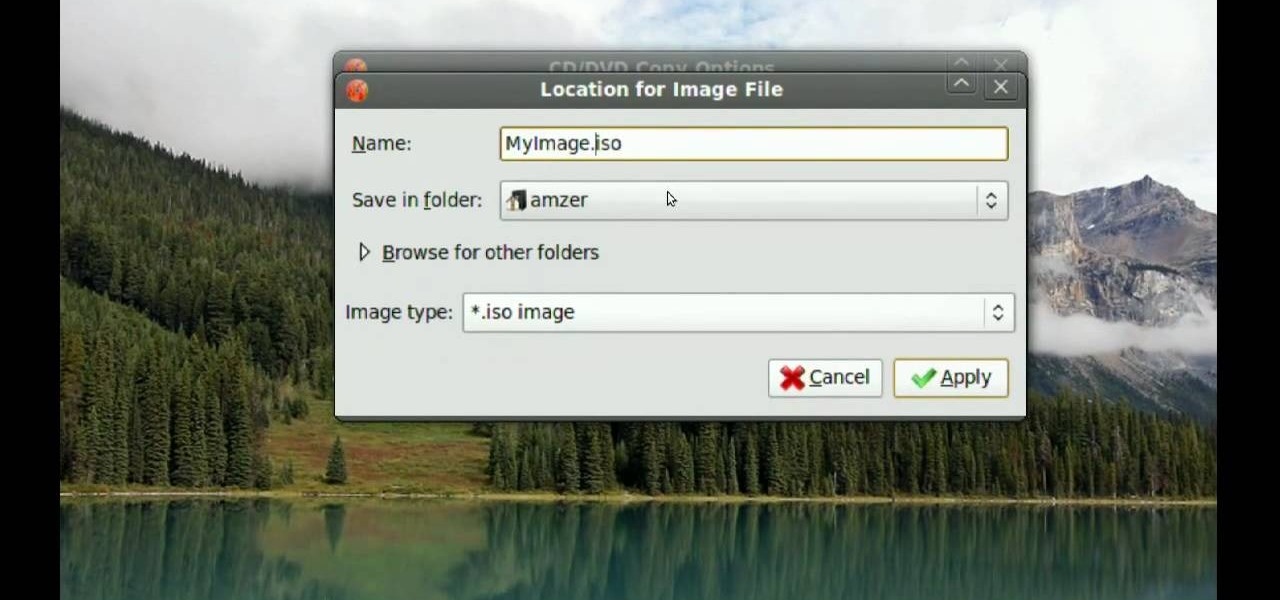
In this video tutorial, viewers learn how to make CD and DVD images in Ubuntu. This task is very easy, fast and simple to do. Begin by right-clicking on the disc icon of the computer and select Copy Disc. When the CD/DVD Options window opens, click on Properties. Now name the disc, select a save folder and choose ISO image for the image type. When finished configuring, click on Apply and wait for the disc to finish copying. This video will benefit those viewers who use a Ubuntu computer, and ...

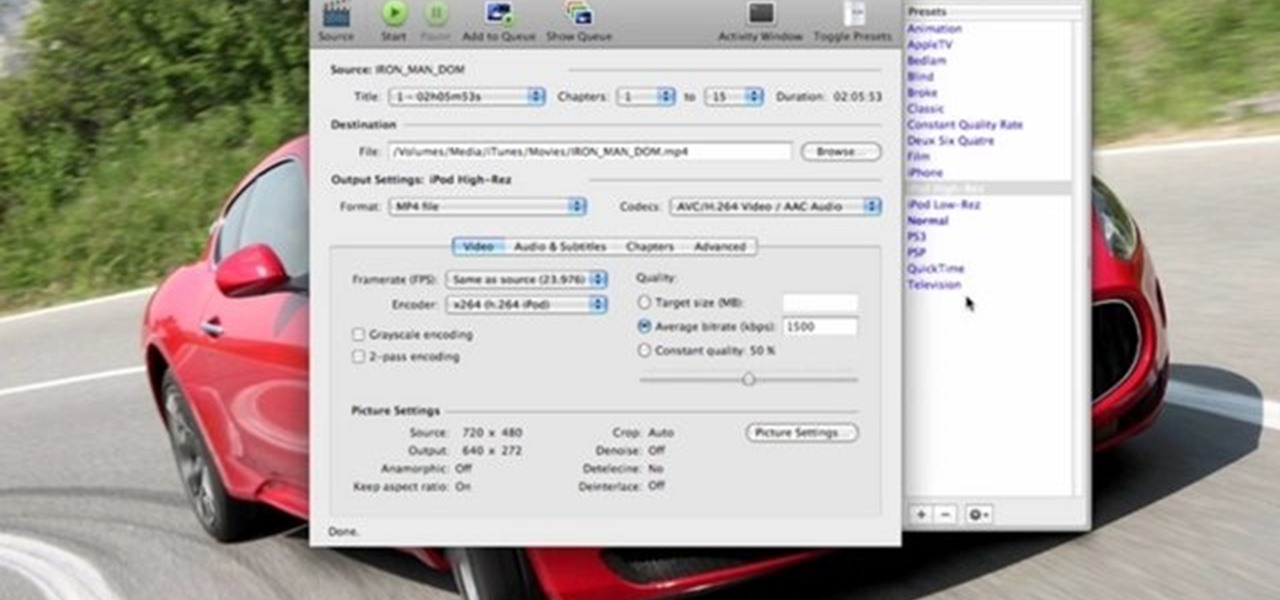
In this video tutorial, viewers learn how to rip a DVD with the program, Handbrake. Begin by opening the video in the program by clicking on Source and locating the DVD drive. Handbrake will start scanning the all the titles of the DVD. When finished, it will automatically select the correct title for the movie. Under Destination, click on Browse to select your saving destination. You are also able to change the name of the file. Now select the video format and aspect ratio. When finished, cl...

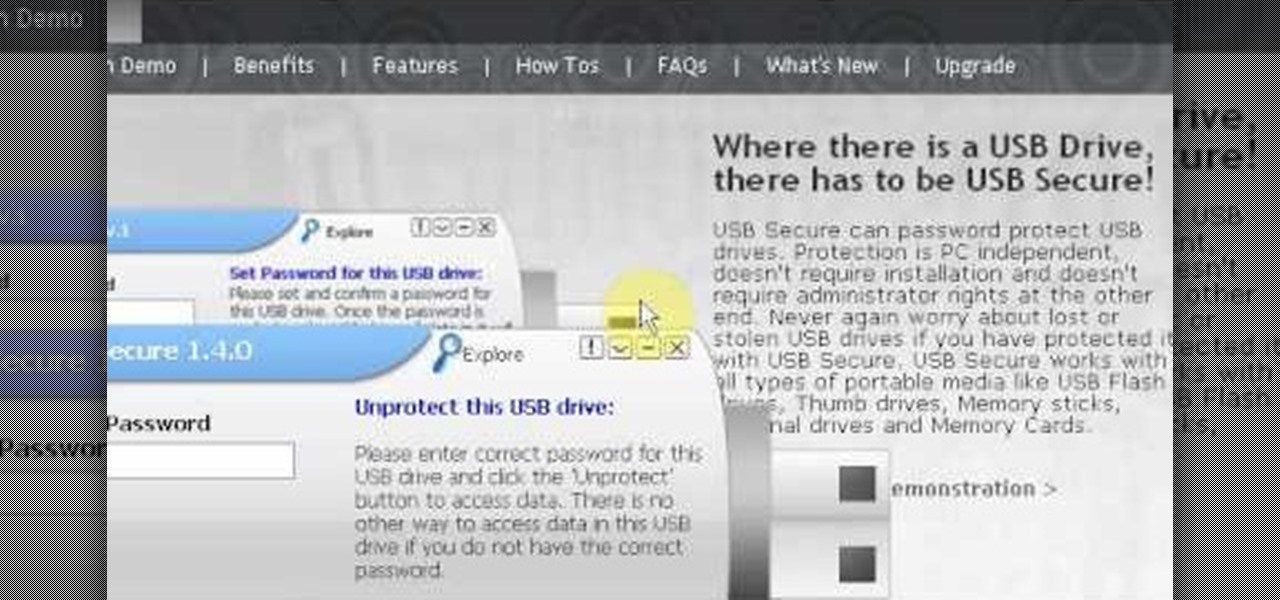
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

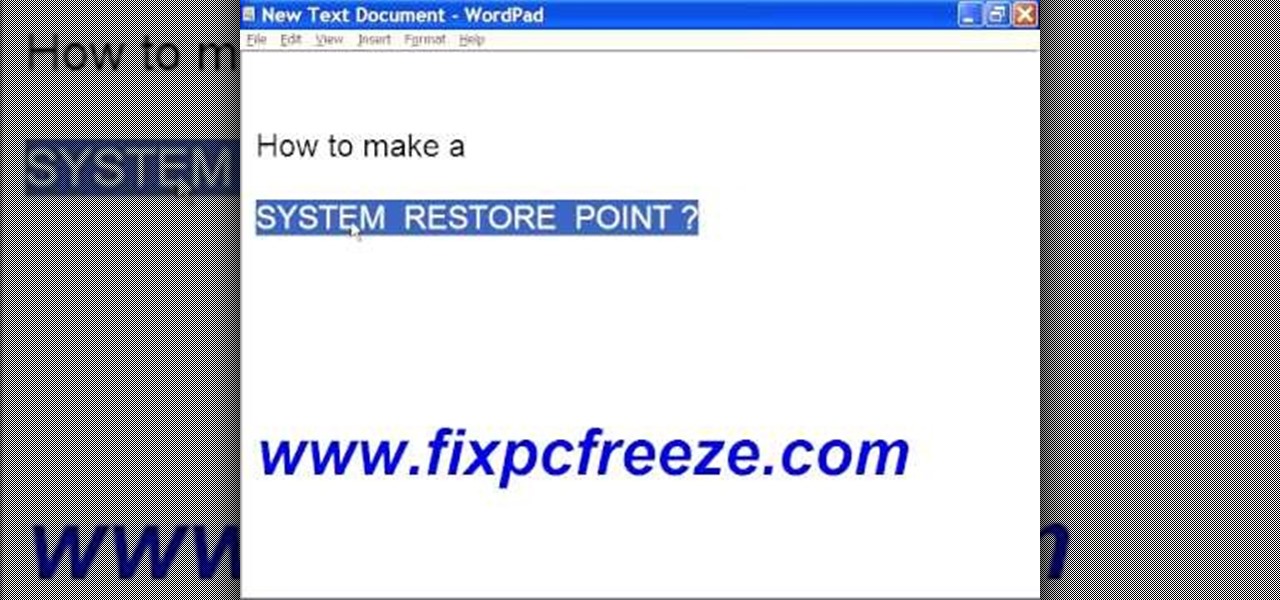
In this video tutorial, viewers learn how to create a System Restore point on a Windows XP computer. Begin by clicking on the Start menu and go to All Programs. Open the Accessories menu and select System Tools. Go down the menu and select System Restore. Check Create a Restoring Point and click Next. Now type in a description for the restoring point and click Create. You will then create a restoring point for you to access whenever you want to restore back to that point. This video will bene...