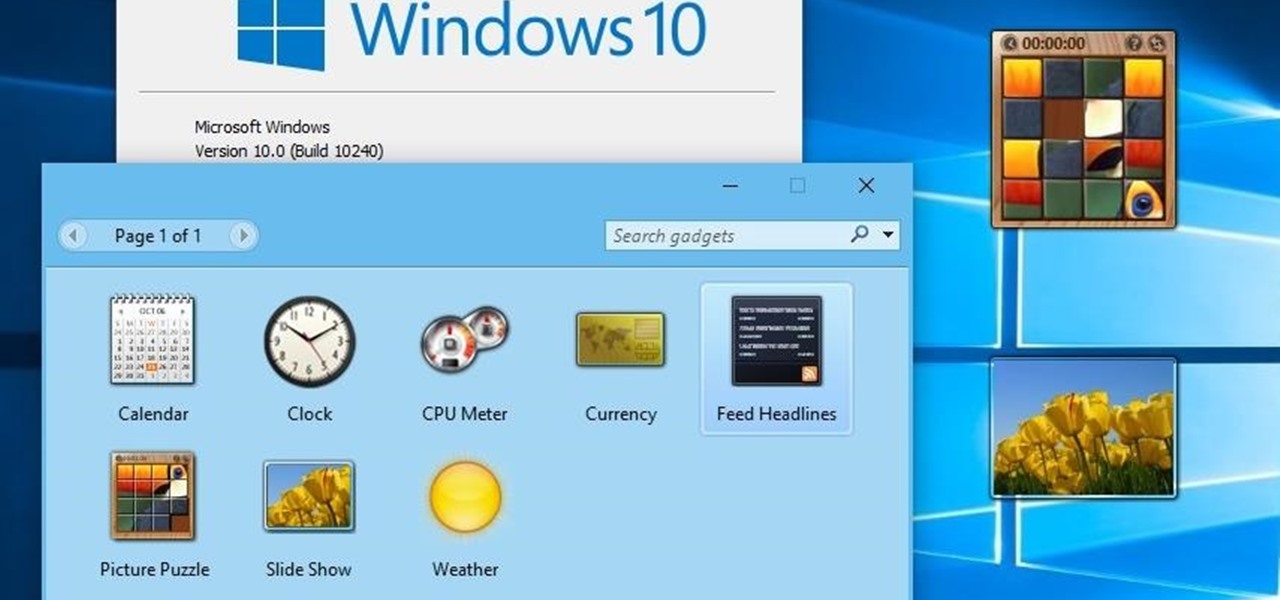
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.
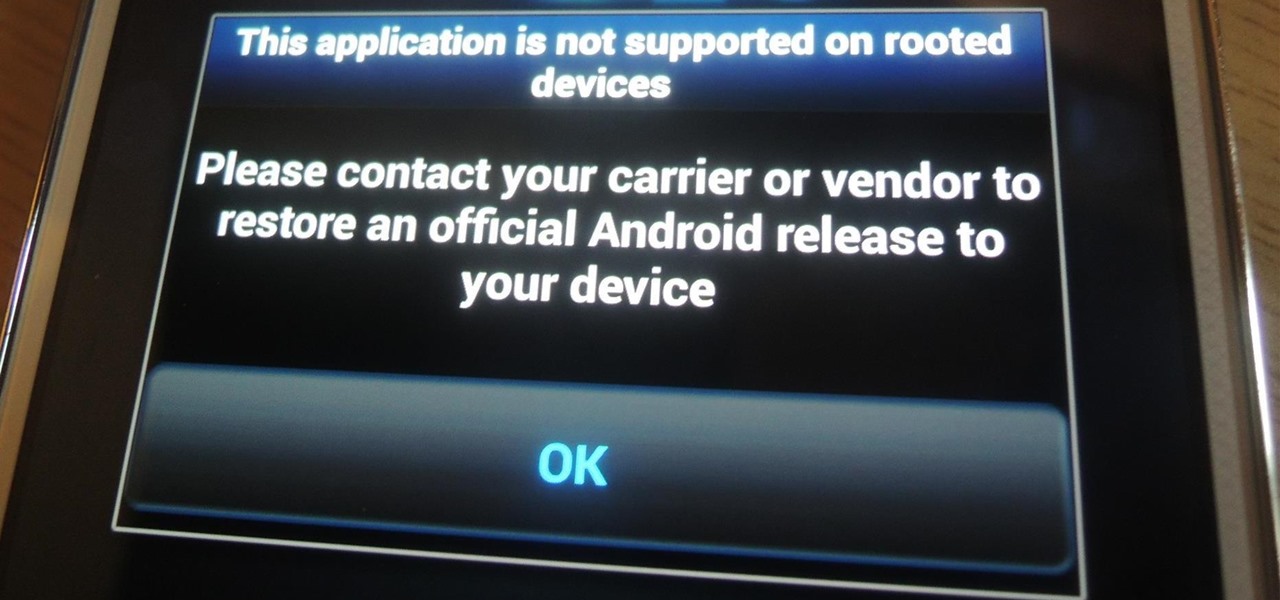
As a preventative measure against exploitation, certain Android applications won't work if your device is rooted. Opening one of these apps that detects root will typically end up with a warning and an inability to access its features, like in the picture below. AS IF!
In this video tutorial, viewers learn how to split their browser. This can only be done on the Mozilla Firefox web browser. Begin by going to the Firefox add-on website and search for "split browser". Then click on "Add to Firefox" to install the add-on. Once installed, users are able to right-click on any tab, go to "Split Tab to" and select the direction (up, down, left or right). Now click on the arrow and it will duplicate the tab in that space. This video will benefit hose viewers who us...
In this video tutorial, viewers learn how to open RAR and ZIP files. This task is very easy, fast and simple to do. Begin by downloading the 7-Zip program. Then open the downloaded file and follow the instructions to install the program. Once installed, right-click on the zipped file, go to 7-Zip and select Open Archive or Extract Files. Once opened or extracted, users will be able to access the zipped content. This video will benefit those viewers who have received or downloaded a zipped fil...

In this how to video, you will learn how to set up Outlook Express for Gmail. This is useful if you want to use the program to access your email. First, log in to your Gmail account and go to settings. Next, go to Forwarding and Pop and select Enable Pop for all Mail. Save this and then go to Forwarding and Pop. From here, select Outlook Express. Click Run the Auto-configuration Tool. From here, you must save a file and open it. Once it is open, type in your account information. Press configu...
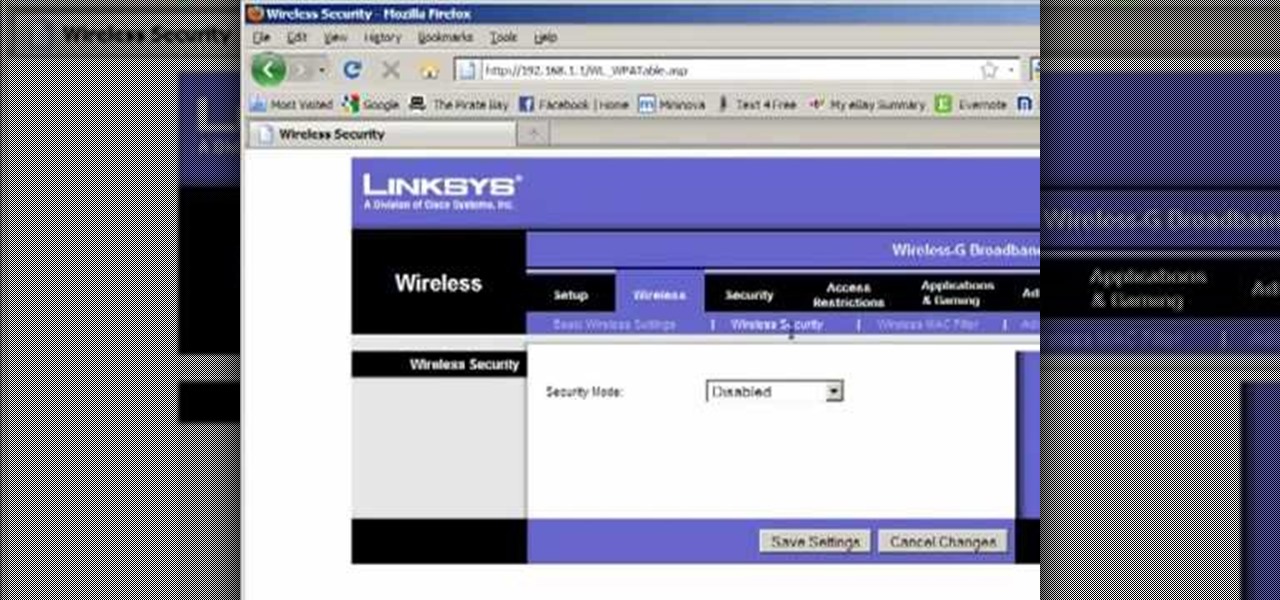
Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...

You might not be alone in having issues running Windows Vista, but you can be alone in knowing how to fix your problems without expensive repair services. With this tutorial, learn exactly how to unlock the hidden administrator account and gain more access to your own computer.

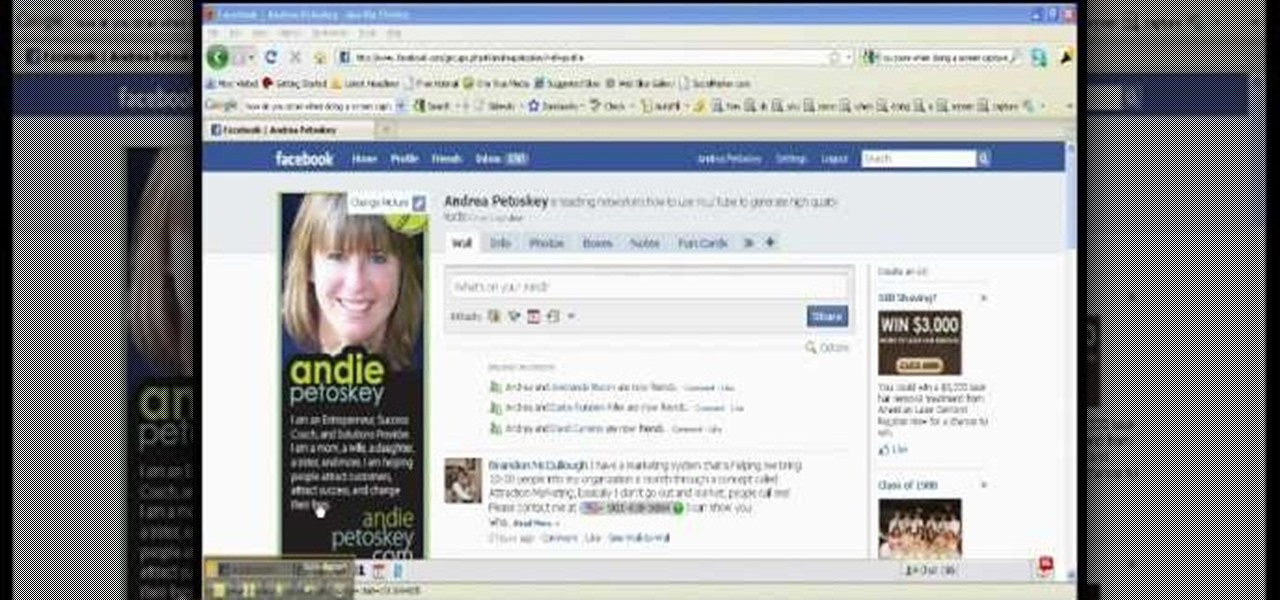
This video is about creating a group on Facebook. Groups on Facebook join friends and people with similar interests. Go to the dialog box and choose groups, create new. You then bring up the form. Choose a name and describe the name. Scroll down and choose the group type. Click create group. You can also add a photo of the group. Scroll down and choose enable photo, video or links. Then you decide who has the responsibility for making changes to the group-members or an administrator. Decide w...

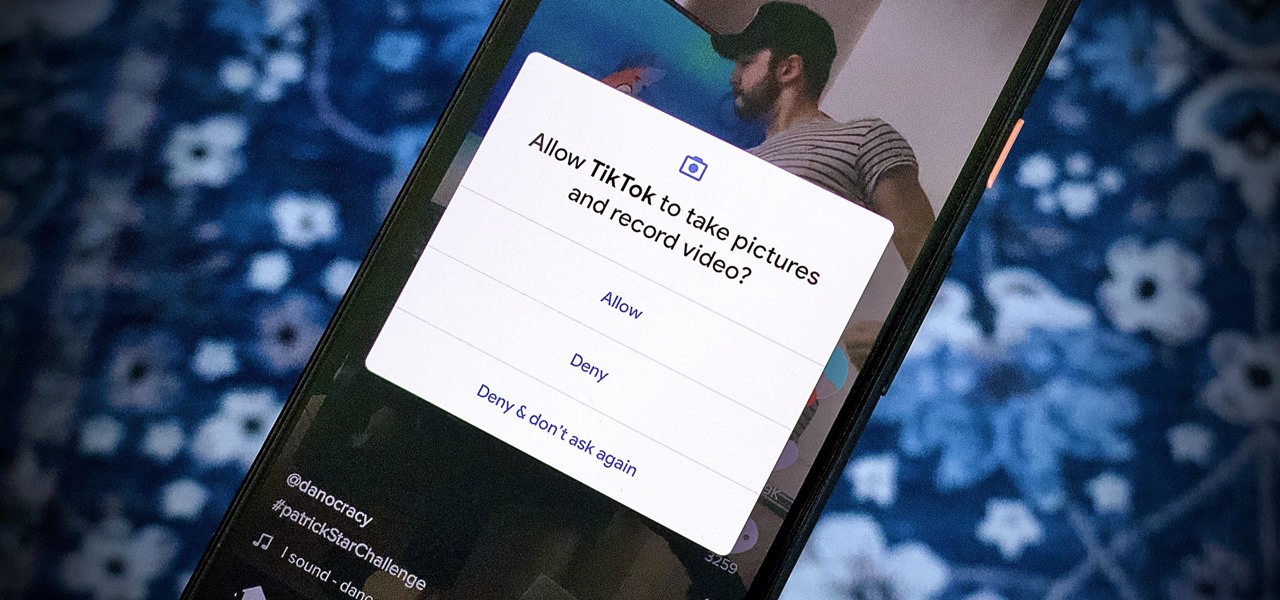
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

Later today, the Olympics are kicking off in London on NBC and its partner stations. However, if you don't have cable or a television with some good reception—or if you'd rather just follow the events on-the-go or at your desk—you're not out of luck. Photo by Locog

Valentine's Day is near, and Judy Topaz has the perfect project for you… a knitted heart. If you want to add a little bit of sweetness to your scarf, sweater or other knitting project, then this knitted heart will surely do the trick. Just make sure to choose a good yarn for good color contrast. Watch all four parts of this comprehensive Valentine's Day knitted heart!

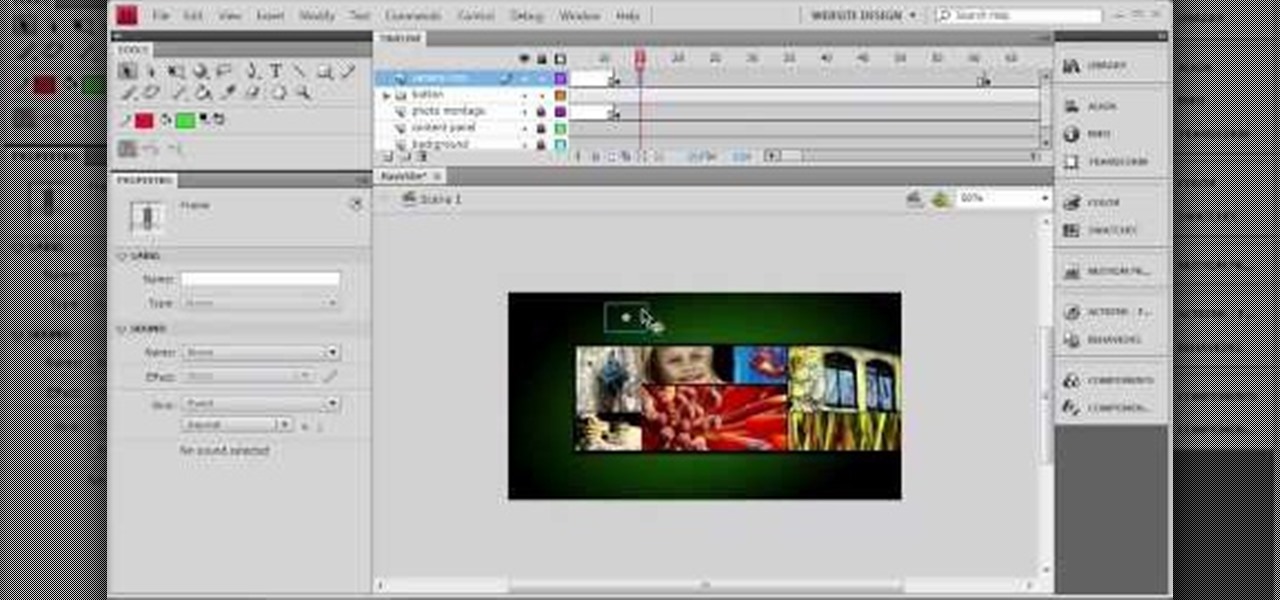
Creating a website using Flash CS4 is one of the most challenging and rewarding ways that you can utilize the internet. This video is chapter 5 of a comprehensive series of videos on designing your own website from scratch using Flash CS4. This chapter covers creating and using motion tweens to improve the animations on your site.

Getting super fast access to your stored contacts on your Android-enabled Motorola DROID mobile device is a easy as two buttons. Yes, 2! Best Buy has the answers. The Best Buy Mobile team explains how simple it is to access contacts quickly via a shortcut on the Motorola DROID mobile phone.

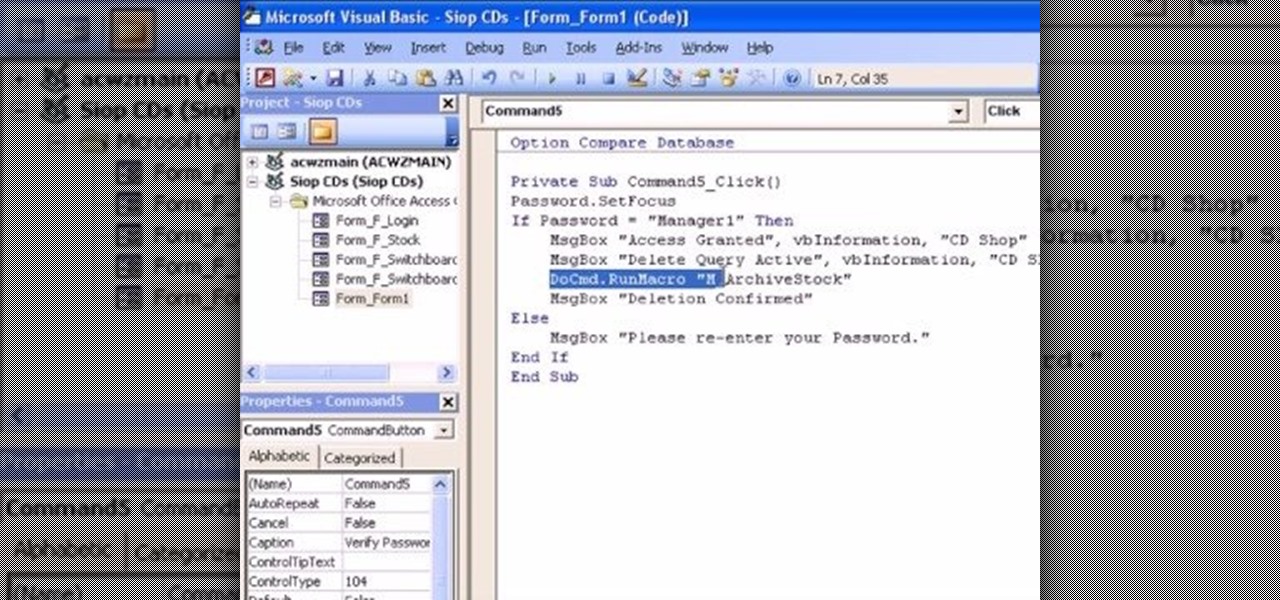
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

"Buy low and sell high" is great advice, but how do you accomplish it? While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader.

Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The newer Graph Search in Facebook can help you find friends in specific cities, photos of a particular subject, restaurants that your friends liked, and a whole lot more. One thing it can't help you with just yet is searching public posts on Facebook, which you could do in the previous search version. Actually, some users do have the option to search public posts with Graph Search, but it's very limited and doesn't include me. If you're like me and don't have access yet, there is a workaroun...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.

This clip over a rehab technique called 90/90 using the Pilates Cadillac exercise device. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

This clip outlines a number of simple Reformer-based Pilates exercises to improve a person's gait. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

This clip demonstrates some rehabilitation exercises that you can use for clients who have suffered from an amputation. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

Learn how to change the themes in Gmail with this video. * Access your Gmail account.

Check out this how-to video to perform three beat weave poi. This poi lesson is for beginners who already know how to spin the two beat weave. The three beat weave poi move is an essential component of your poi twirling move-base. It'll be used a lot, so you should learn how to do it well. Here is a very comprehensive tutorial on how to do so.

This article is a must read for all of you mediocre crossword enthusiasts who can only dream of meeting Will Shortz. (I put myself in this category.)

In this video tutorial, viewers learn 4 different hacks that will make typing easier in Windows. Begin by clicking on the Start button and select Control Panel. Then click on Ease of Access Center and select "Make keyboard easier to use". Now users are able to configure the keyboard options for easier use such as: turning on/off the mouse keys, sticky keys, toggle keys and filter keys. All the features have more specific settings for self-adjusting to the user's liking. This video will benefi...

This video tutorial from TruTricks presents how to setup Google customized alerts.Open your internet browser and search for Google Alerts using Google search engine.Click first result that says Google Alerts.You will need to sign in to use this Google feature.Google or Google mail account will work. If you don't have it you should create one.After you signed in Google Alerts welcome screen will open.Here you can create new Google alerts using Create a Google Alert window.Enter Search Term you...

One of the trickiest parts of auto repair is getting access to the part of the car you actually need to fix. In this video, you'll learn how a new tool called a borescope allows you to inspect and repair sections of your car that were very hard to access before.

If you want to import data or recover files from your AppleTV back to iTunes on your computer, this shows you how. First you are shown how to gently take apart your Apple TV to access the hard drive, then hook it up to a Macintosh, and you can access your files and data structure from there!

One of the coolest features of the new Android phone, HTC EVO 4G is its ability to tether the Internet. In this clip, learn how to access and set up tethering, as well as which apps work best. You will also learn how to use Sprint's 29.99 Hot Spot plan, or bypass the charges by setting up free options. So, follow along and get your phone up and running with the new lightning fast 4G network.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

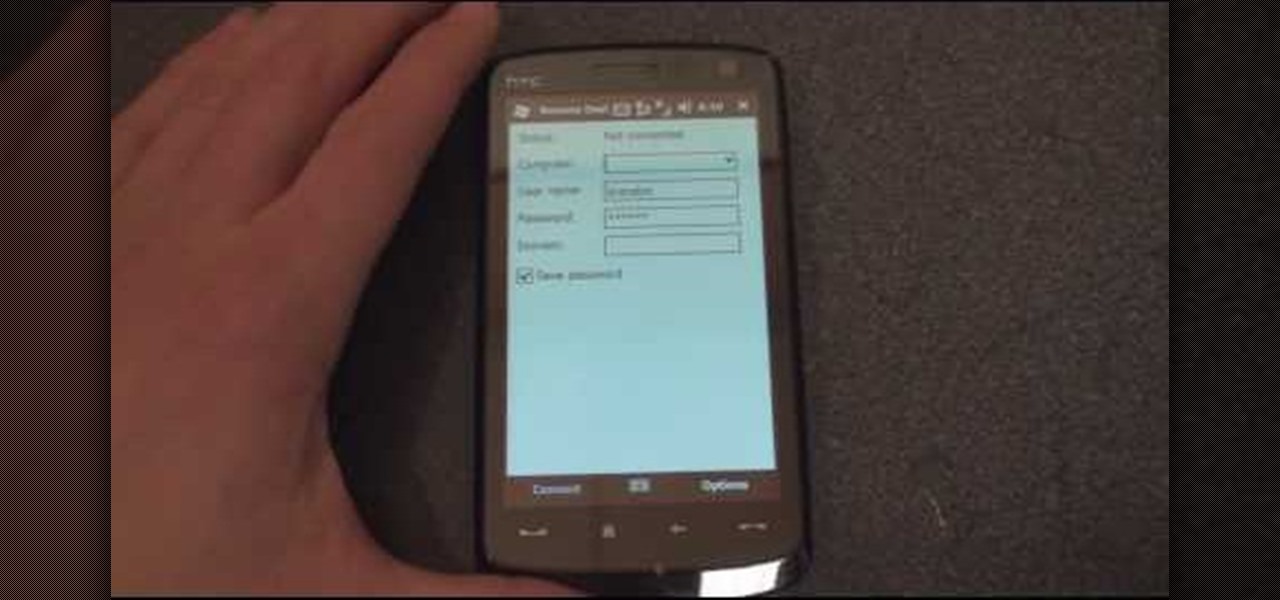
In this tutorial Brandon from Pocketnow.com will show you how to set up and use your remote desktop on a Windows mobile smart phone. Windows mobile remote desktop allows you to remotely access and control your Windows computer from your cellphone device, it is just like controlling your computer but in the palm of your hands. This guide will also show you how to get the Remote desktop software on your cell phone device if you don't already have it. The remote desktop requires for you to have ...

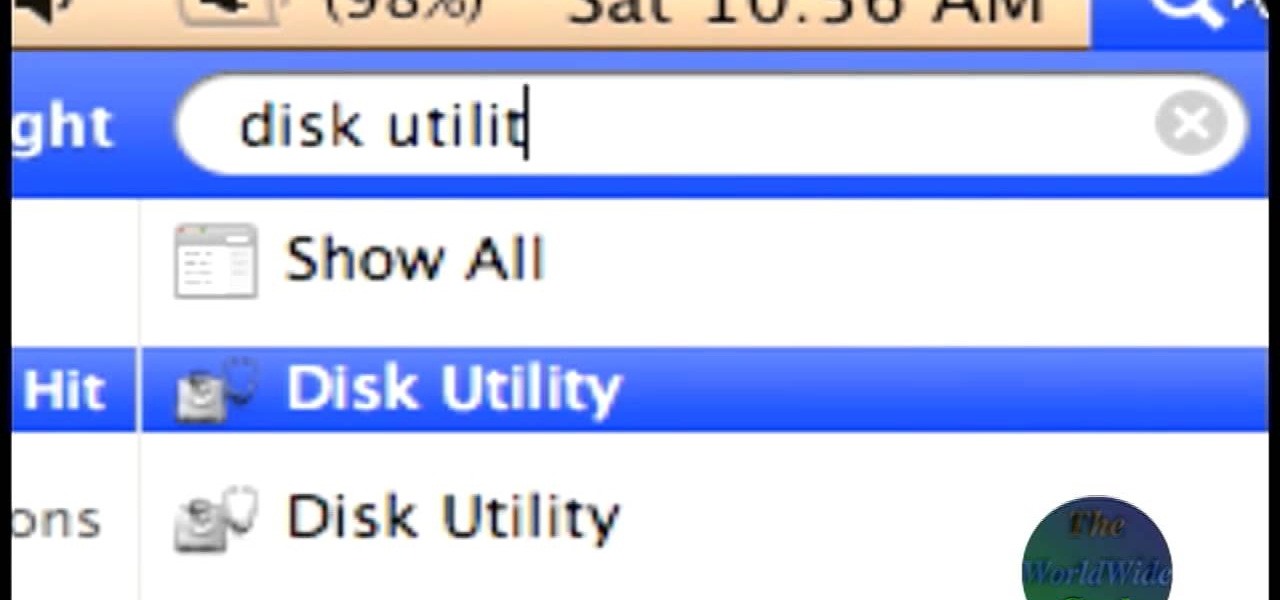
The World Wide Geek demonstrates how to format an external hard drive for Mac OS X. External hard drives are usually formatted for windows. To change the format, you will need to use the disk utility option. Access the disk utility by going to finder and clicking on applications. Next, click on the utilities folder. Then, click on the disk utility option to open it. You can also search for disk utility in spotlight. Select your external hard drive in the options to the left of the disk utilit...

iMovie '08 allows you to directly access your Aperture library to add still photos to your movie.

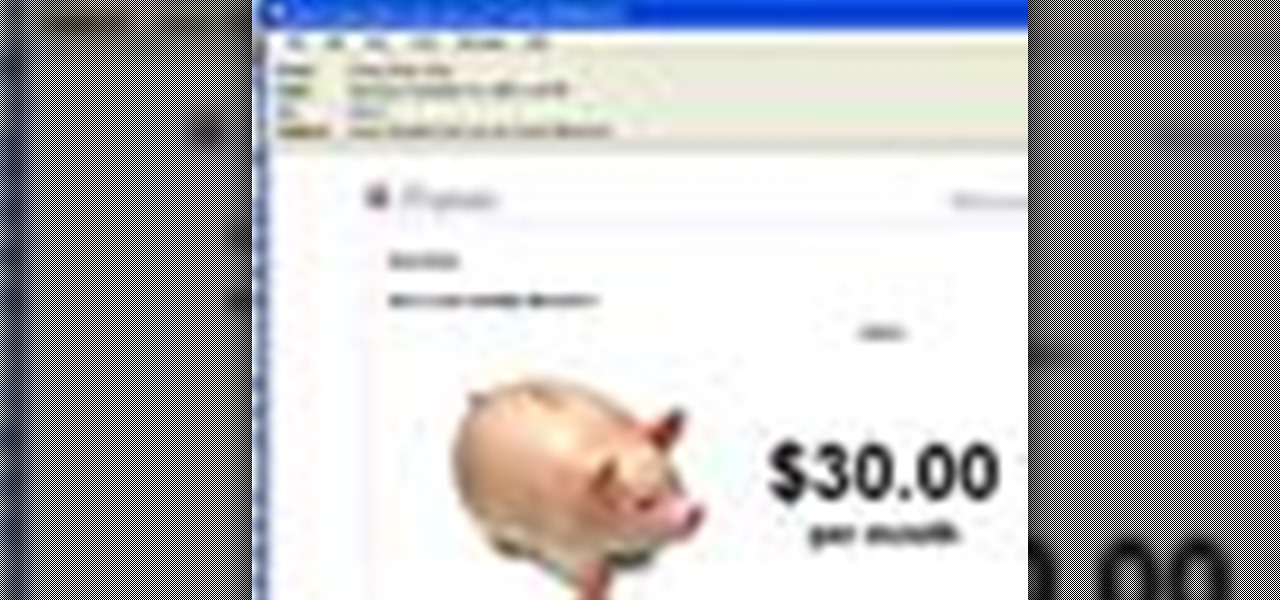
Kids can have fun using the iTunes music store while parents still control the credit card and content their children can access. Parents can restrict access to certain content, set up a shopping cart to review music choices before they're purchased, and give kids a monthly allowance.

No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video.