
How To: Draw a cartoon smiley head in Inkscape
This video shows you how to draw a cartoon smiley head in Inkscape: Open a new page.


This video shows you how to draw a cartoon smiley head in Inkscape: Open a new page.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.
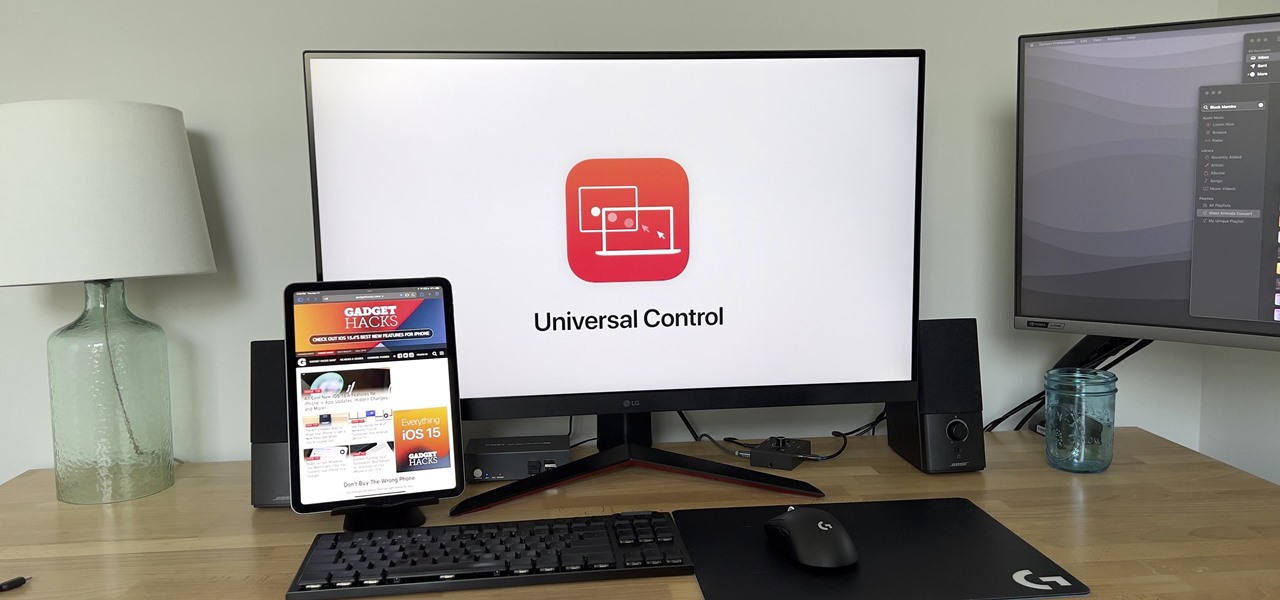
With the release of iOS 15.4, iPadOS 15.4, and macOS 12.3, Apple unleashed a ton of new features. We saw a preview of one of the most anticipated new features way back in June 2021 when it was announced at WWDC, and now it's finally available for everyone with an iPad and Mac.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Today we are going to show you how to make cat face in easy 5 steps. To make a cat face we just need a square paper and a pen. Let's see how to do it.

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.
While Apple's Continuity feature has certainly impressed me, I can't help but feel like it could be used to create a better connection between my iPhone and Mac. Sure, Handoff allows me to pick up where I left off in certain applications between the two devices, and it lets me pick up calls and send text messages on my Mac, but I want even more functionality.
Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

The motor coupling goes between the motor and the transmission. If it fails the washer will not spin or agitate. If the washer fills with water but then does not agitate, but you hear the motor running, the coupler could be the problem. You may hear some clicking noises as the broken pieces spin around. You may also see a pile of black rubber pieces on the floor under the middle of the machine. You can follow the steps in this video to help you do the repair.

The video gives you a step by step tutorial how to replace the steering gear boots of a Volkswagen Passat B3 without dismounting the steering gear.

This video gives you a step by step tutorial how to recover the seats of your car. If you are a little familiar with sewing, this is easier as you imagine. All you need for this repair is new fabrics and a normal sewing machine.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

The video gives you a step by step instruction how to replace the rear shock absorbers on your Audi 100/A6. The replacement is necessary when the absorbers loose their hydraulic fluid, you have problems driving the car, or you find places on the tire where the profile has vanished. Such a tire you'll see in the video.

When your clutch pedal is dropping down and not coming up again, the cause is most probable one of the cylinders in the hydraulic clutch system. The video will give you a step-by-step tutorial on how to replace both, the master and the slave cylinder. In addition, it is a good idea to also replace the pressure hose in-between the cylinders.
This goes out to all of the Tweeters out there looking to get a little more creative with their Twitter accounts. My page has always been extremely basic, because I just never bothered to pretty it up. I just had one of the stock backgrounds and the good ole Sacramento Kings logo for my profile pic. So, if you want to add your own cool photos and backgrounds to your account, the folks over at Twitter made this funny cartoon video just for you. It's not the most complicated of tasks, and every...

You can use iTunes to transfer your old CDs or burn your downloaded MP3s so that you can listen to them on the go. Watch this tutorial for advice and the steps you need to make your own compact discs.

Your iPhone only has a few physical buttons, buttons with a set number of default actions assigned to them, like sleeping your display, controlling volume levels, and even taking pictures. But as much as these buttons can do for you, they can do more. You're not stuck with the out-of-the-box defaults. Every push button on your iPhone can be customized in one way or another.

For all of its many perks — from the best iPhone camera system money can buy, to arguably the best smartphone display on the market — the iPhone 12 Pro Max is undeniably huge. It has the largest iPhone screen to date despite being 0.46 cubic inches smaller than the iPhone 11 Pro Max in overall size. If you're finding it a little too much to handle with one hand, there are ways to make it much easier to use.
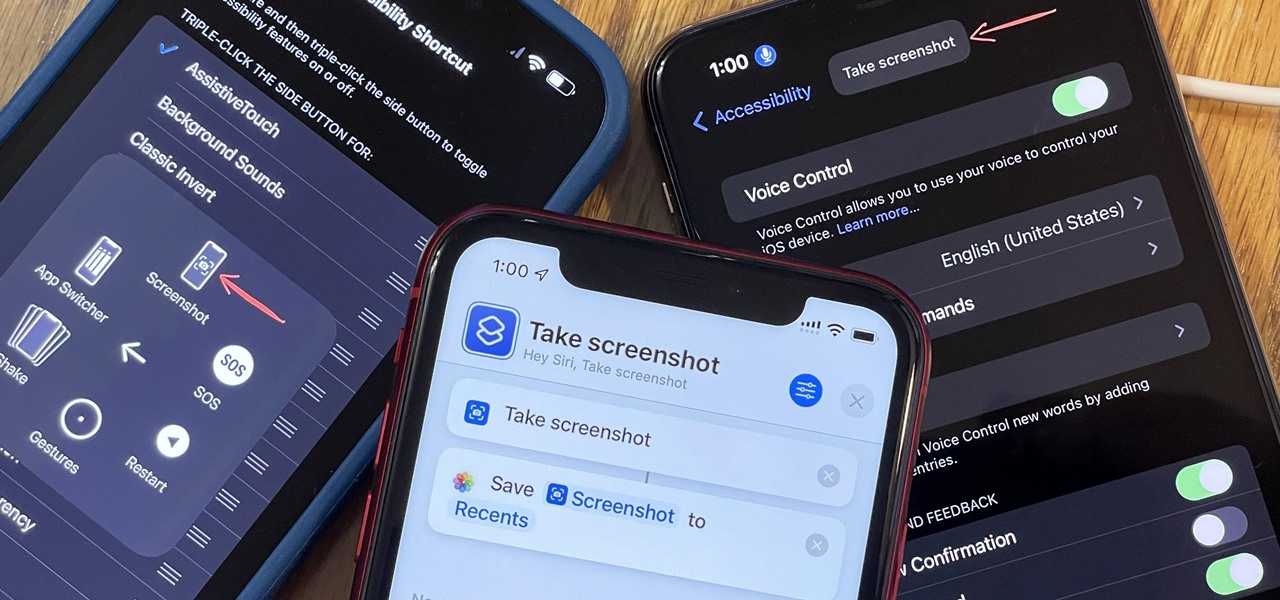
Using an iPhone isn't difficult, but it can be if you're using it for the first time, especially if you switched from an Android phone. That's primarily because of the massive difference in the user interface between the two operating systems. And when it comes to taking screenshots, you have more options than just using the hardware buttons.

The iPhone has included a real-world magnifying glass called "Magnifier" since iOS 10. Still, it remained relatively obscure until iOS 14 when it received significant upgrades such as a new interface, hideable controls, a customizable toolbar, improved filters management, multi-image shooting, and people detection. But one of the best things about the update is that you can open it more easily.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.
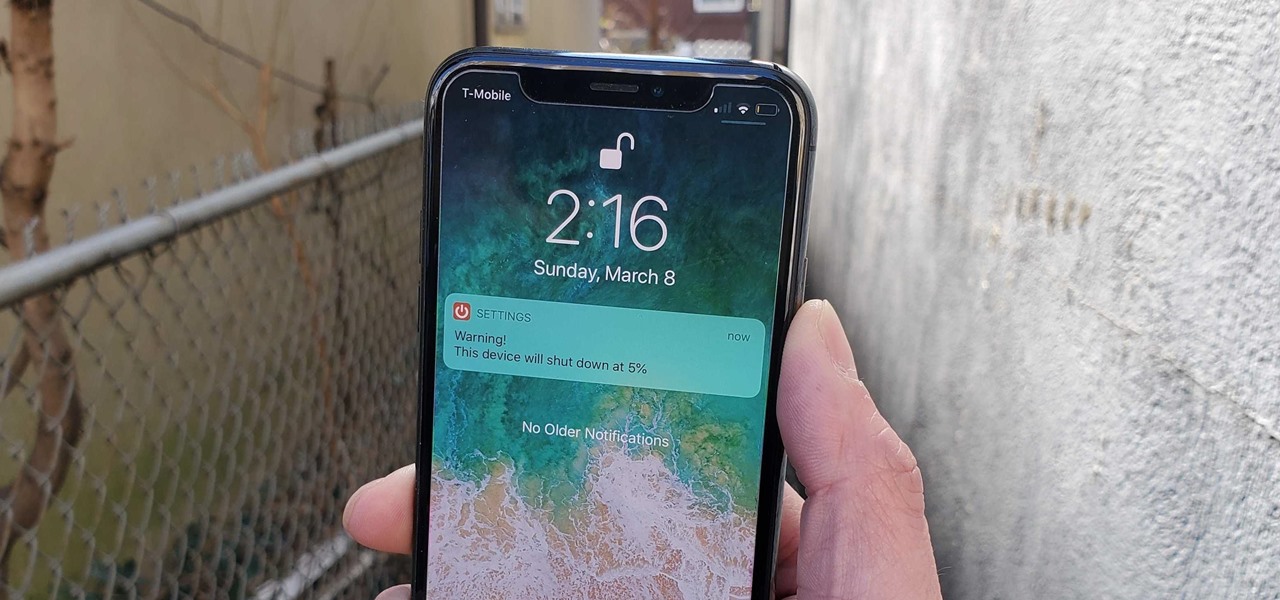
If running out of battery while out and about weren't bad enough, the experience is a lot more painful if your iPhone has a semi-untethered jailbreak. With that kind of jailbreak, when the iPhone dies, all of the mods will be disabled after the device powers back up. Fortunately, instead of restoring your jailbreak and tweaks manually after recovering from a critically low battery, you can avoid it altogether.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

If your iPhone has a Home button, such as either iPhone SE model, old or new, then it has a secret triple-click gesture to activate a suite of shortcuts. These options, dubbed accessibility shortcuts, can work wonders for folks that are hearing impaired, have limited use of their hands, or have vision problems. Still, the shortcuts have plenty of everyday applications that everyone should know.
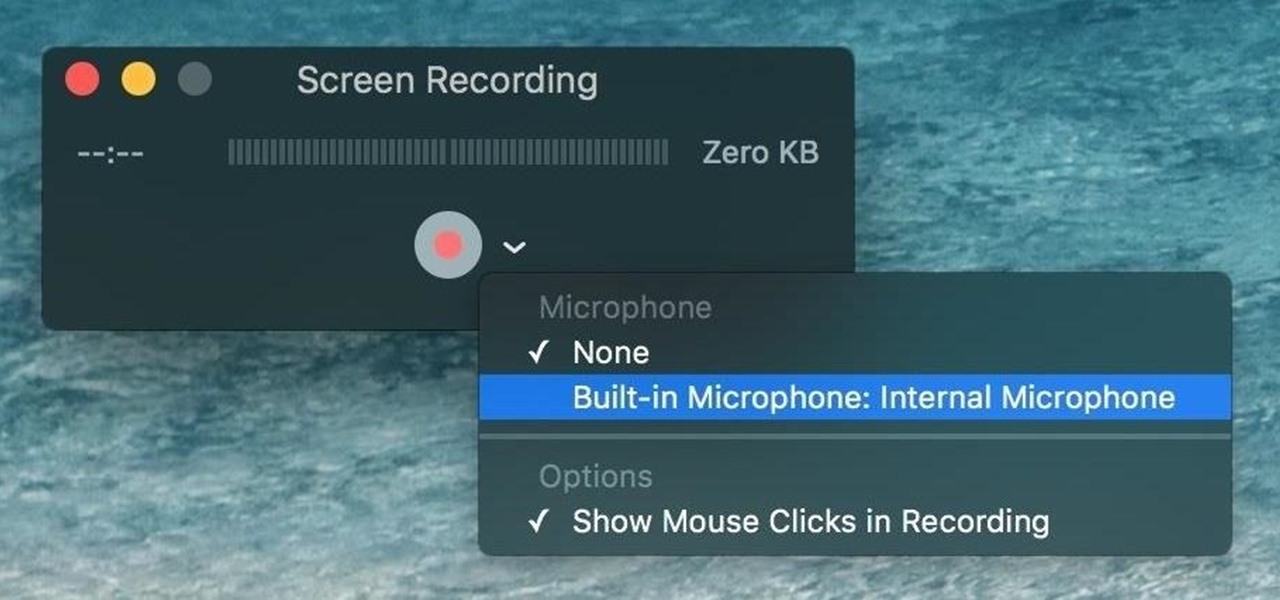
When a friend asks me what screen recording software is best to use, I always say the same thing—you don't need any! Even though it's been around since 2009, many Mac owners do not realize that they have a powerful screen recording software built right into OS X.