
News: Popcorn Time Explained
Part 1: What is Popcorn Time? Part 2: What is a torrent?


Part 1: What is Popcorn Time? Part 2: What is a torrent?

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.
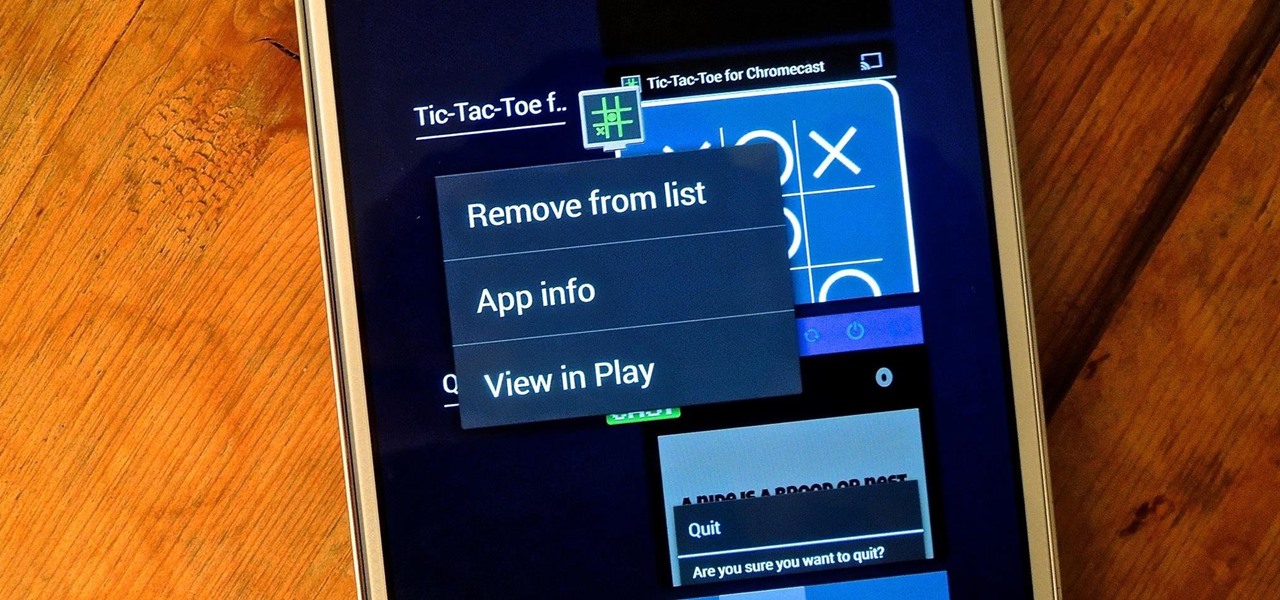
On more than one occasion, I've wanted to check out the Google Play page for an app I was currently using, whether it was to get contact information or read recent reviews to see if others were experiencing issues that I was.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.
Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

Hey dolls, just giving you my review of the Derma roller. The good and the bad! Firstly, let me just say OUCH! This bad boy hurts, it's pain level is very close to Fraxel laser the only difference is, that you're doing it to yourself, instead of being in a clinic. I did get emotional in this video because I just couldn't believe how painful the device was on my skin. Most videos and reviews on the next say it's "pain free" and this just isn't true.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even remember. Now, you could go ahead and uninstall everything that you don't think you need, but then you run the risk of removing something that could really mess up the system. When I open up my Programs folder, I feel like...
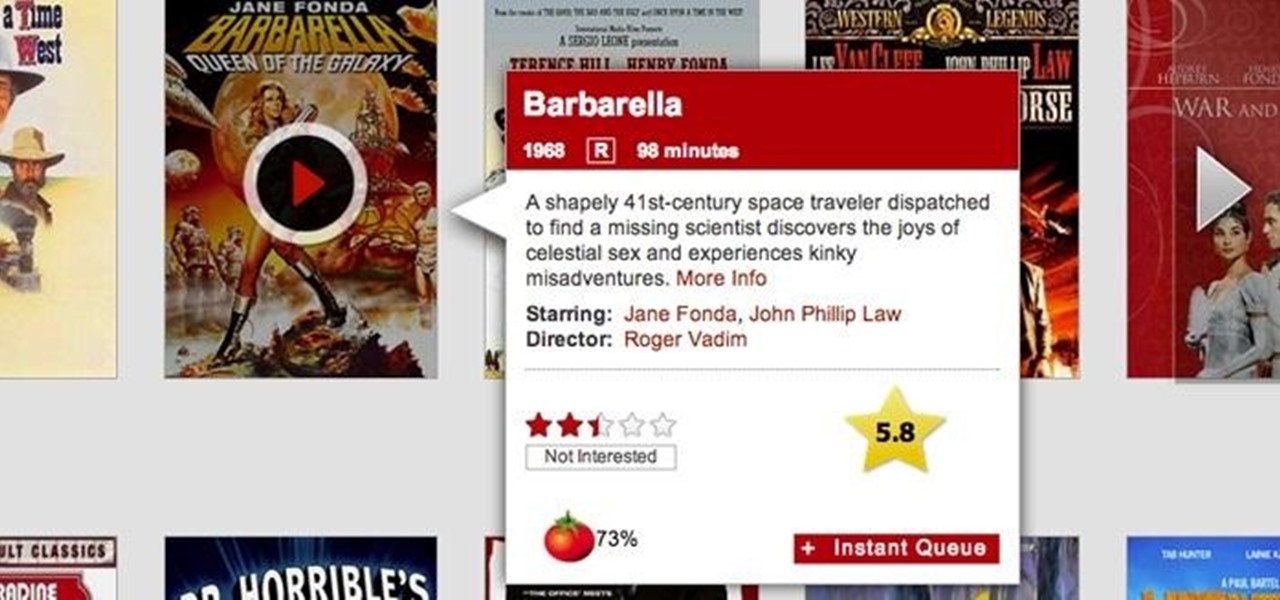
I like to call Netflix my quiet, digital friend. She's been there for me on many many occasions—from when I had to move home for a few months, to when the cable was down for days.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.
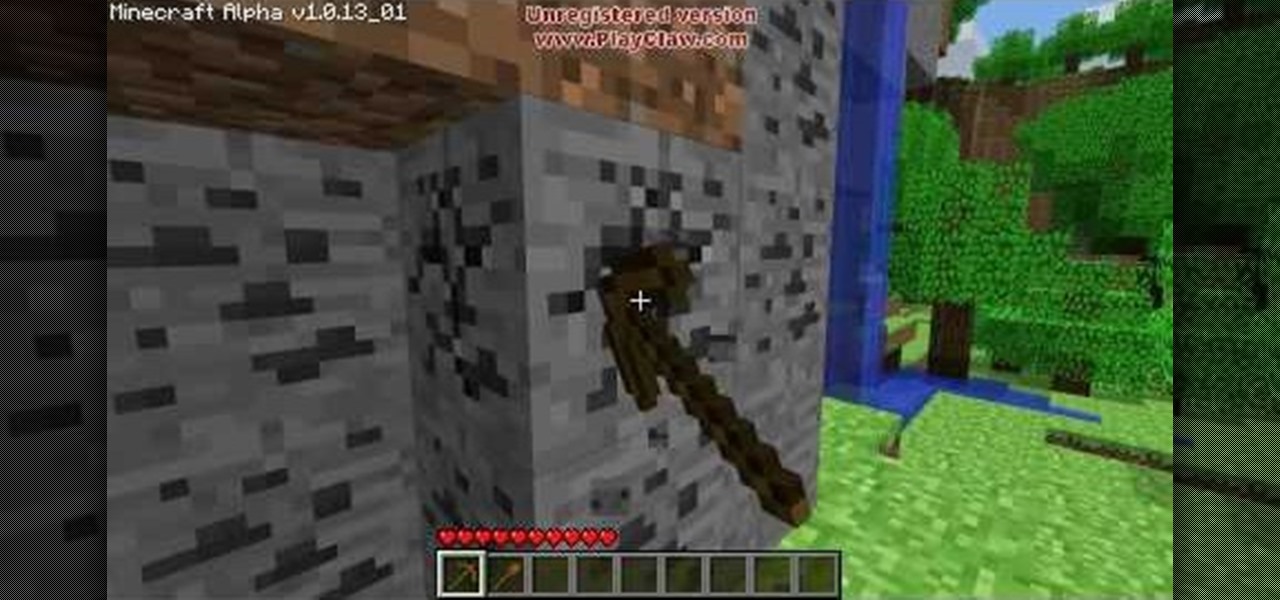
Minecraft is a game that snuck up on the gaming community and set a wild fire bigger than the ones in California! Even though it's not even done and still in Alpha phase, reviewers are already reviewing it, and people are jumping on board. The game itself is based around a basic concept: survive, craft, build, conquer. You play the only man in the world who starts with nothing, during the day, it's safe and you can mine and harvest material, but at night, creatures come out, including Zombies...

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.
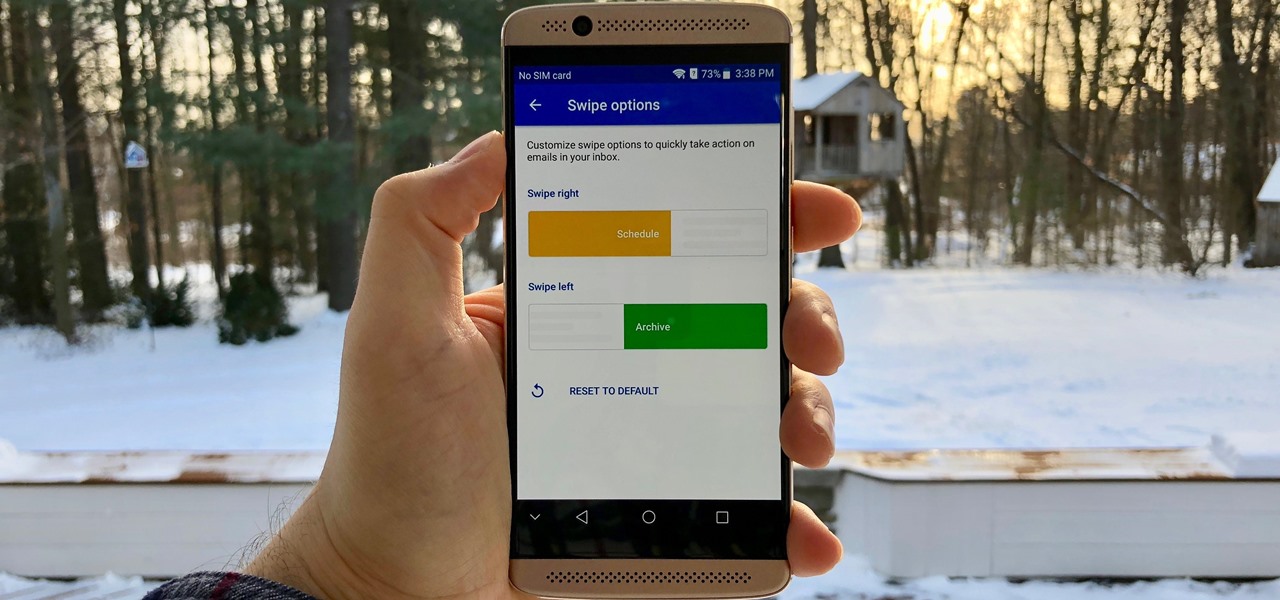
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

If you've been longing since the '90s for the total Clueless experience of virtually trying on clothes, you missed out by not attending London Fashion Week earlier this year.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.
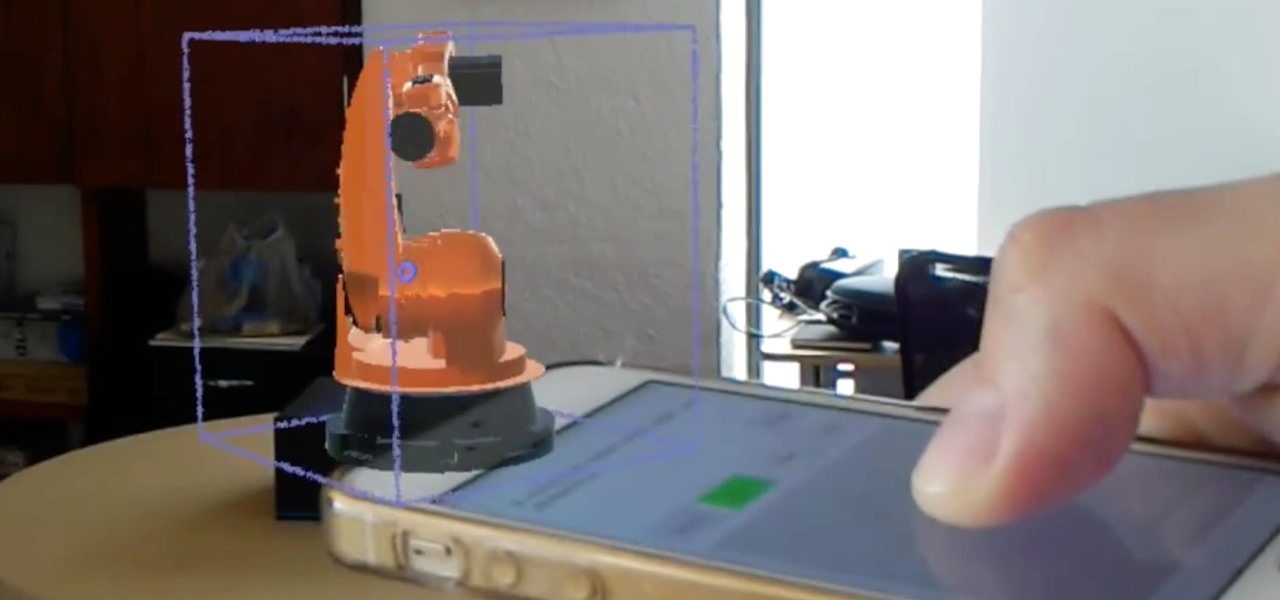
We've highlighted the projects of Wavelength Studios a few times over recent months for their work in the augmented and mixed reality space. Since receiving their HoloLens headsets, they've been hard at work on both development community projects as well as efforts for clients. This brings us to their latest work—a way to control holograms on the HoloLens with our pocket-based modern miracles, also know as smartphones.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

Back for the second part,
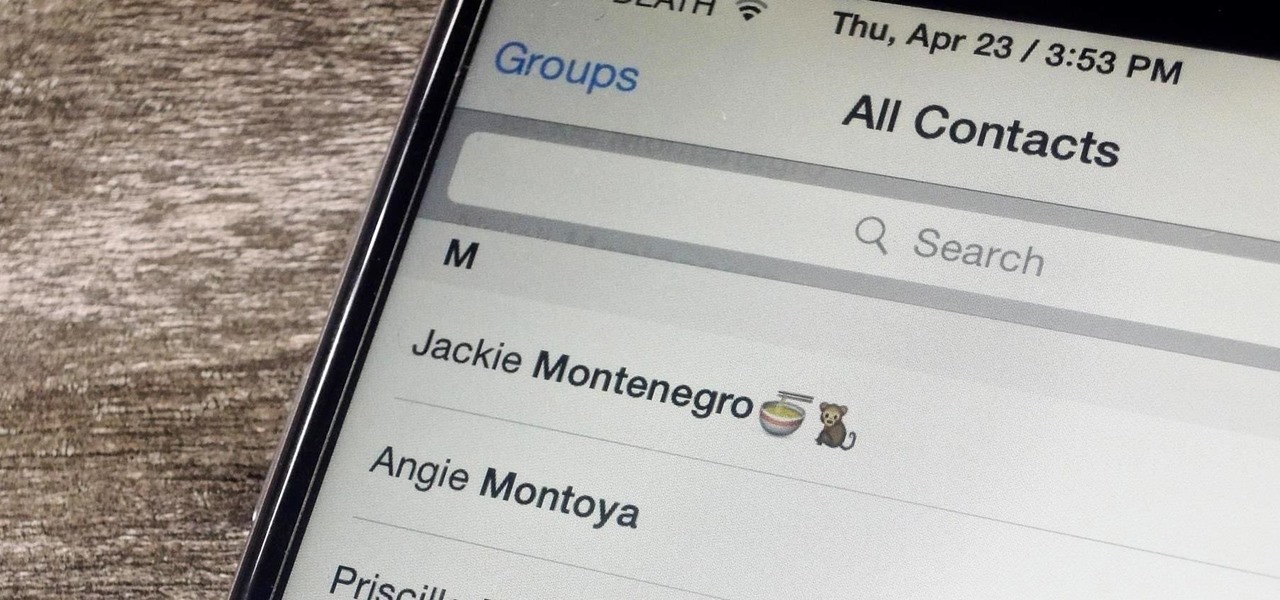
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.
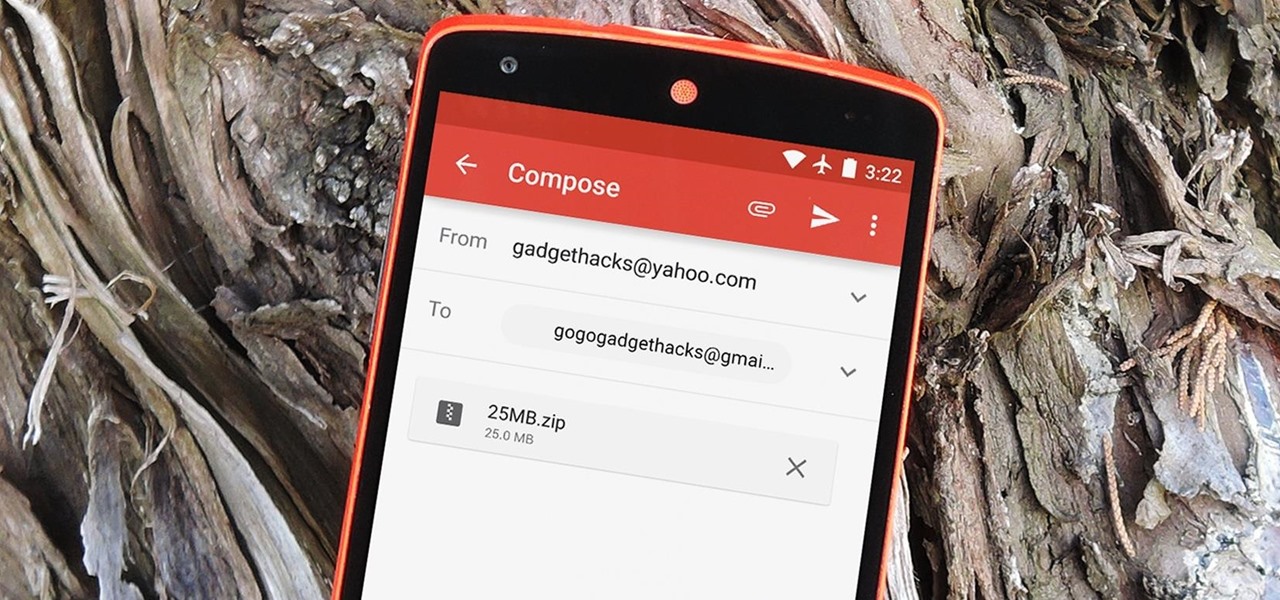
The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you turn your phone into a super-convenient wireless webcam and save some cash.
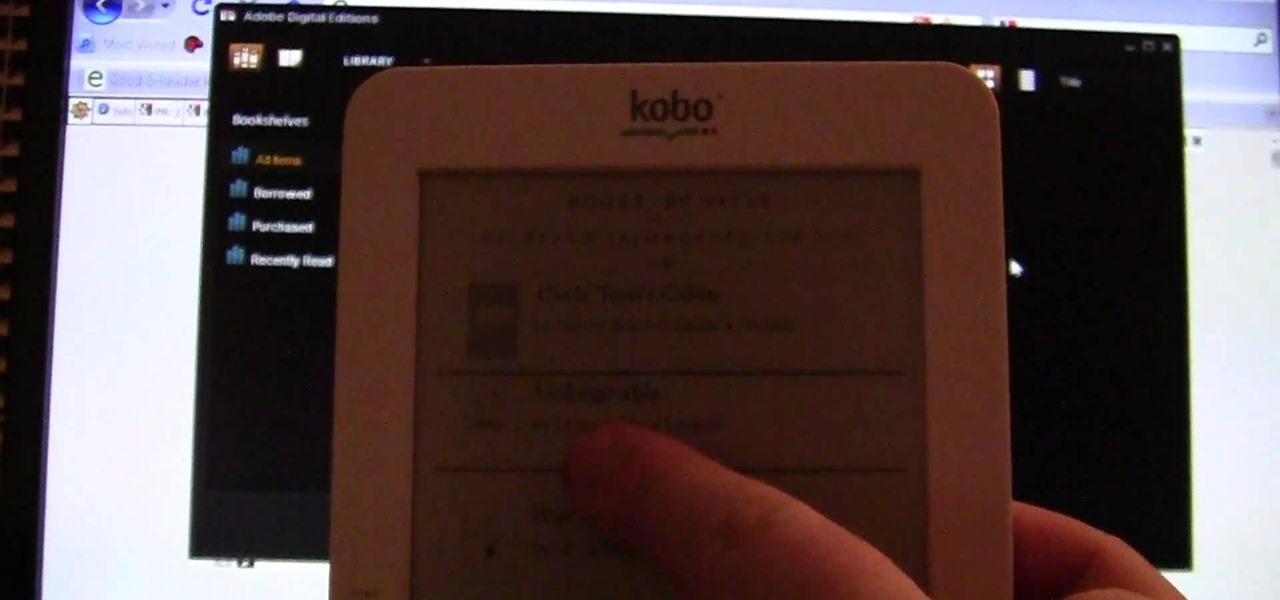
Through Thursday, January 19th, Borders is offering the Kobo Wireless eReader for $99 with coupon—that's $40 off its typical retail price of $139! Though the Kobo Wireless eReader comes preloaded with 100 out-of-copyright classics, new users will nevertheless be interested in filling their new eReaders with their own books.

There are millions of YouTube videos out there about video games. Playthroughs, reviews, commentaries, tutorials. If you want people to see and appreciate your gameplay and takes on it, watch this series of videos. It features a veteran video-game-YouTuber explaining in great detail how he sets up, shoots, and edits his YouTube videos. It covers cameras, lighting, and many other aspects of filming yourself playing a game.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop the App Store on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.
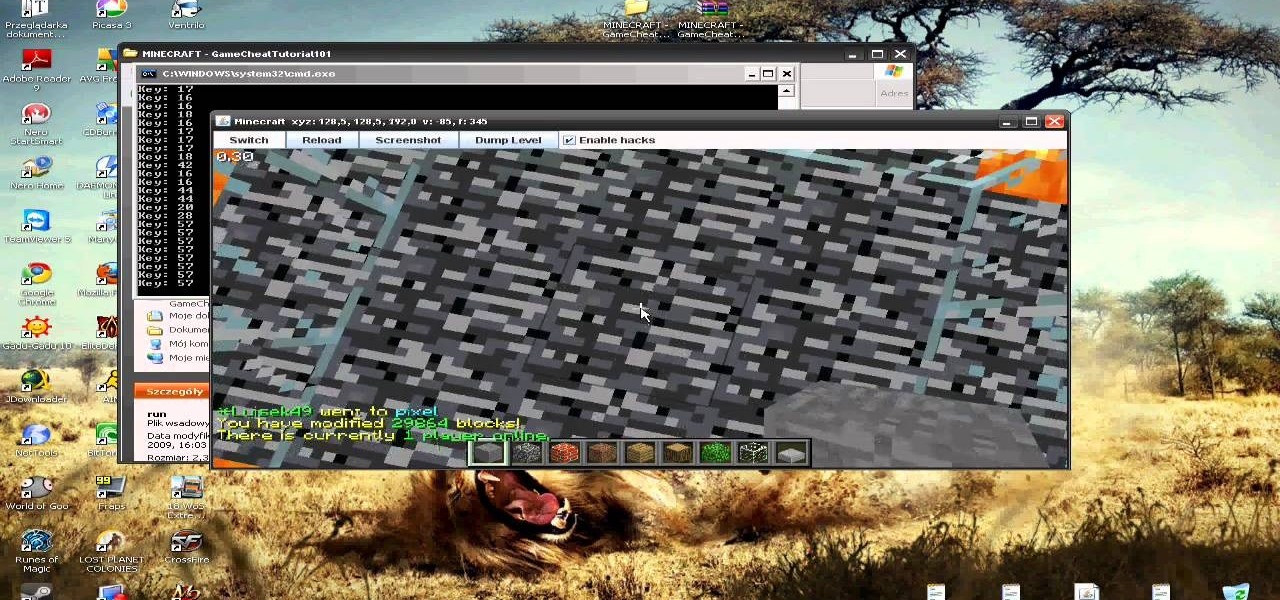
This is a super easy hack that anyone playing Minecraft on a PC can do. Hack a custom client for the game, which will give you access to things like noclip mode and fly jumps. You won't need a broswer loaded to use this, either.