
How To: Do a chair massage for legs and feet
In this video, Massagenerd demonstrates various techniques that can be used to massage the leg and foot regions while the client is sitting on a chair. Watch and learn.


In this video, Massagenerd demonstrates various techniques that can be used to massage the leg and foot regions while the client is sitting on a chair. Watch and learn.

Want to know how to set PDFs up so that they can be digitally signed? In this Adobe acrobat tutorial you'll see how to set up a PDF to accept a digital signature. You all also see how to create your own digital signature for signing and a strategy to work with your clients so that you know who is signing those documents.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?

Since its debut 9 years ago, the iOS App Store has always had roughly the same functionality: Featured apps, categories, top charts, a search function, and a place to update your apps. But starting with iOS 11, that's all changing — drastically.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1
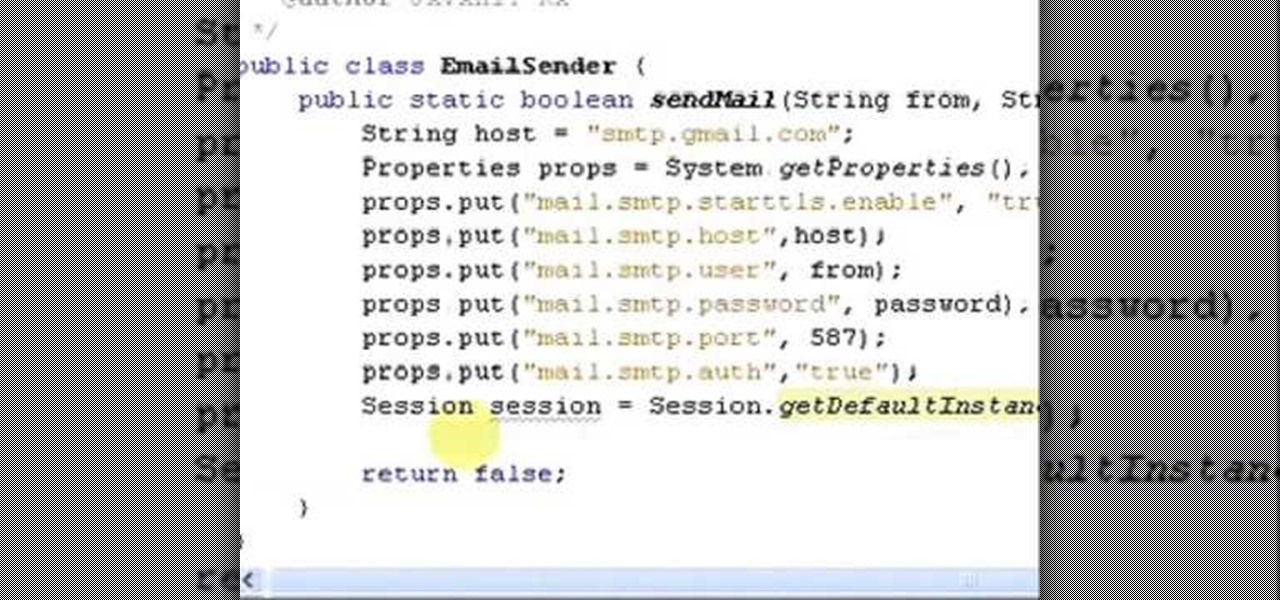
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...
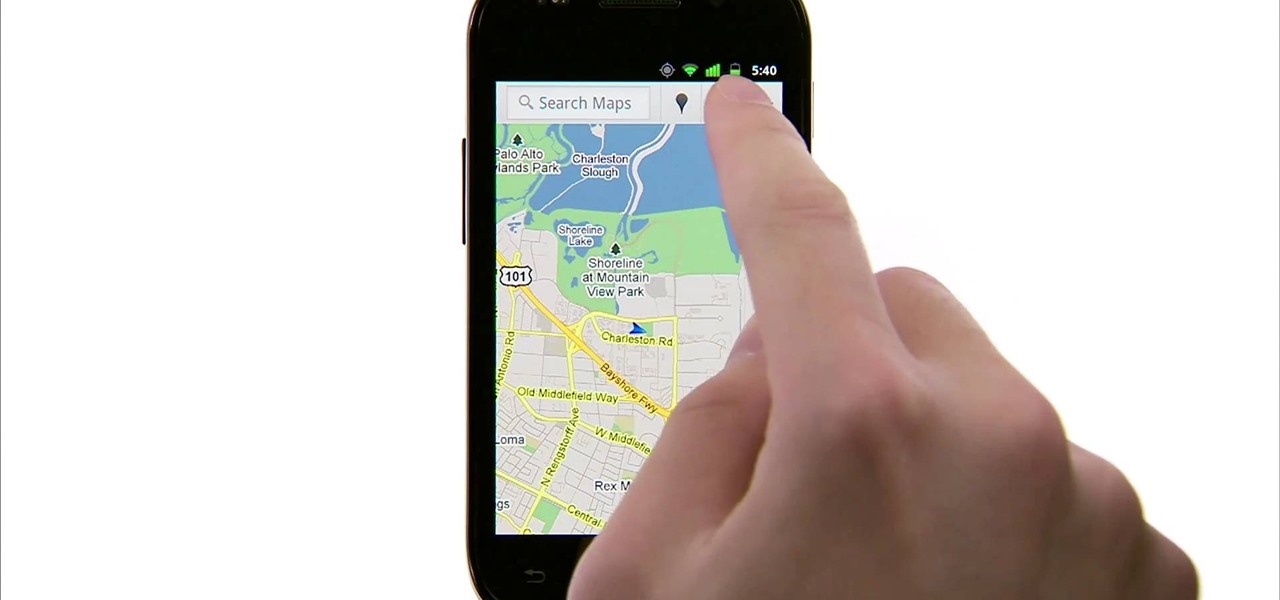
Google Maps is much improved in Android 2.3 (Gingerbread). And even better on the Nexus S. This smartphone can do many things, but the best feature is still Google Maps, which will appear shortly on all Android devices when Gingerbread is officially released.

Tattoo lady and reality TV star Kat Von D is obviously extremely talented with the tattoo needle. Creating interesting designs for clients that include celebrities, Kat Von D exudes a distinctive style that includes looking like a tougher version of a classic pin up.

In this video, we learn how to give a professional hand massage. First, spread oil onto the hand with your hands, which will prevent you from sticking together. After this, open the hand up and interlock your fingers with theirs and start to massage the inside of the hand. Open the hand up and work your fingers into the sensitive muscle areas. Go slowly, but apply enough pressure around the hands to make a difference. After this, work the tendons on the front and work your hands around each o...
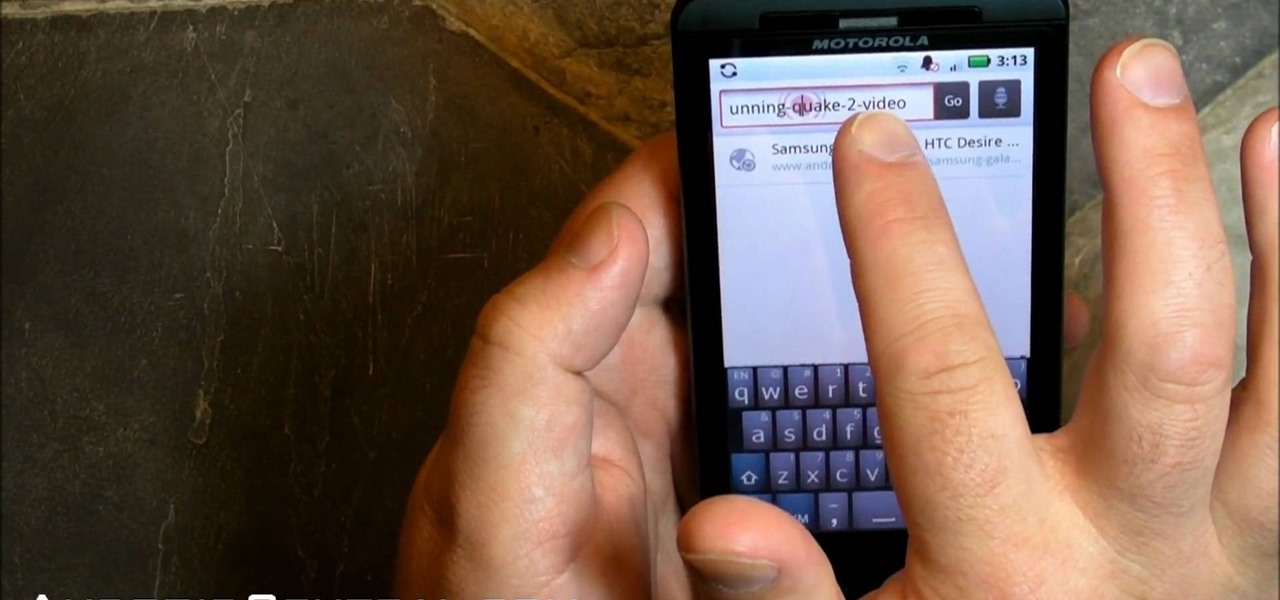
You may be a little confused about all the new functions and features of your new Motorola Droid X cell phone from Verizon Wireless, bud don't worry, help is here. This video will give you a complete walkthrough of the new Droid X mobile device, showing you all the new stuff and how to use it. It's the newest and most sophisticated Verizon Android phone, so don't let it get the best of you — watch and learn what it can do. See a full review at Android Central.

If you're starting to use your digital SLR for the first time, it can be quite confusing to determine what all its functions mean as well as where to find them and how to use them.

Recently purchased a brand new digital SLR? Learn how to use your camera's functions properly by watching this tutorial on how to use your picture control settings on your Nikon digital SLR.

In this video lesson for doctors, you will learn how to do a shoulder examination. First, you'll get a review of the procedures for evaluating any joint, and then jump into the basics of inspection of the shoulder, then learn palpation, and range of motion. This is a very general shoulder examination, meant to serve as a refresher course for those medical doctors or medical students who already know the exam procedure.

Getting text from one area to another is quite simple. You can do so between any text frames. This video will demonstrate exactly how to cut, copy, and paste on your Macintosh.

This video shows you how to draw peter pan step by step. The instructor begins the video by having a preset outline to follow that must be copied to understand how the character will be formed correctly. The face is the first object placed on the outline followed by the shoulders and then legs. After this step the picture will appear completed and colored in leaving the student to have to pause the video and follow the lines carefully with much reflection and reviewing. The coloring for this ...
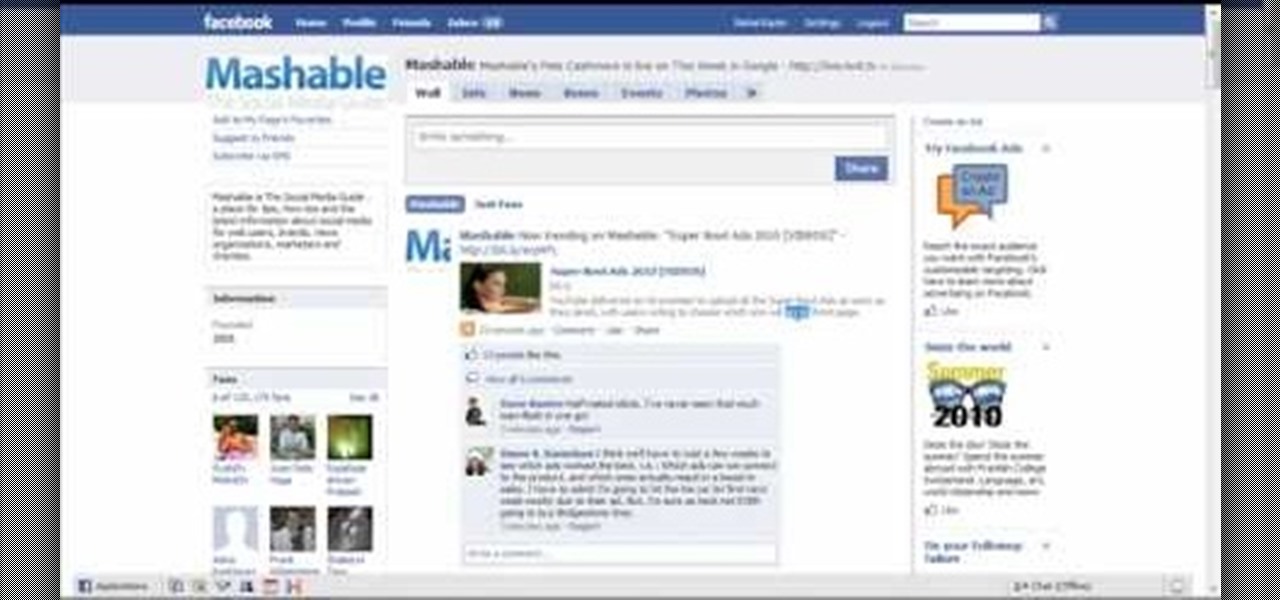
This instructional video Nehal Kazim from Site shows you how to make a complete Facebook fan page. Before creating a fan page evaluate the reasons of making a fan page. A fan page lets you connect with your future clients and fans and keeps them updated and gives them a platform to talk about your organization. To create a fan page go to the bottom of any page and click 'Advertising', select pages and click create a page. Select a suitable category and a suitable name make sure to select it c...
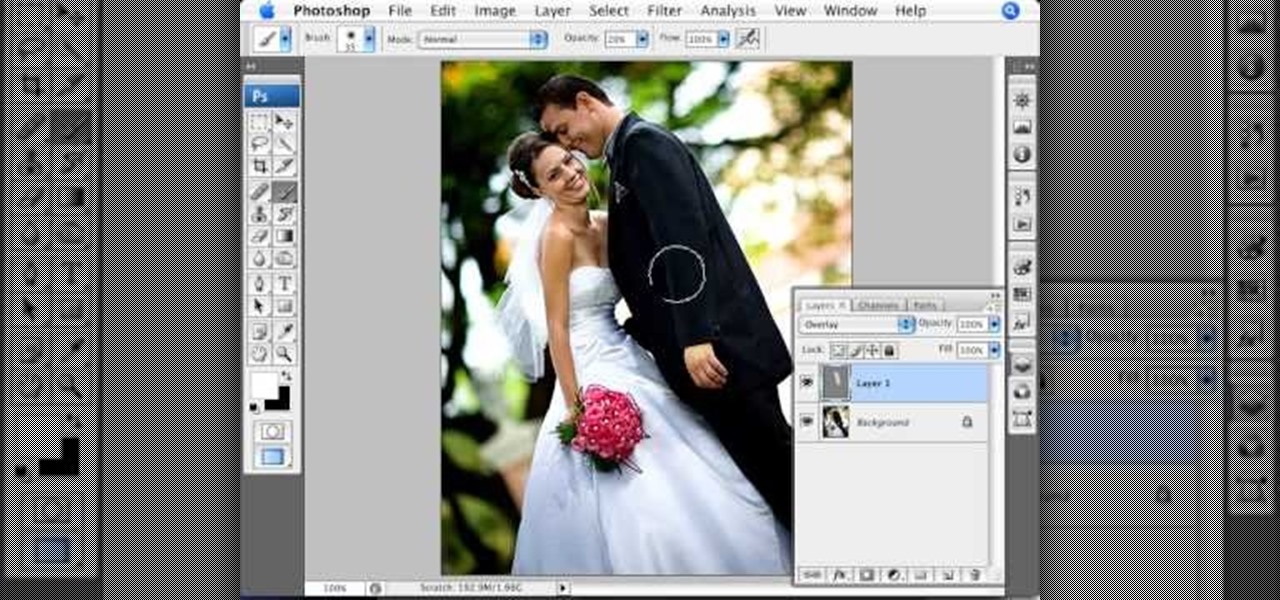
Photoshopuniverse teaches you how to use the Dodge and Burn tools in a non destructive manner, in Adobe Photoshop. Dodge makes things lighter. Burn does the opposite. The problem is that this is destructive operation. Use the Brush tool at 20% opacity. Create a new layer with 50% grey. Change the layer's mode to Overlay. With the black color you will make things darker and with the white lighter. To view the changes, review the overlay layer. To correct a mistake on this layer, use a brush wi...

For a mom, there is always so much to do that your own personal care routine may take a back seat. But in this video, top hair stylist Gary France offers tips on how to style very short hair for the busy mom. France shows us his process on a busy working mom. The client receives a lighter color to brighten up her look, a trim to texturize her hair and styles the hair without using a blow dryer, which is great for saving time. France shows us that just because you have kids to take care of doe...

Matt describes the necessary steps to take before you begin to build your infrastructure. Find business and design requirements.

See a tour of the new fur system in Houdini 9.5! It presents a workflow for adding fur to a character, then dives into implementation of the tools to help build that fur.
Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.
Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

The valve grind process is pretty complicated and each step is covered in a new video. Removing a valve from a cylinder head, review of the cylinder head nomenclature, measurements for valve grind, knurling valve guide, actual grinding procedure,

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.