This clip outlines a number of simple Reformer-based Pilates exercises to improve a person's gait. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

Windows users have looked on with envy at Mac owners wrangling torrents with ease for years. Now, finally, a new Windows torrent client is making downloads easier, safer, and more customizable.
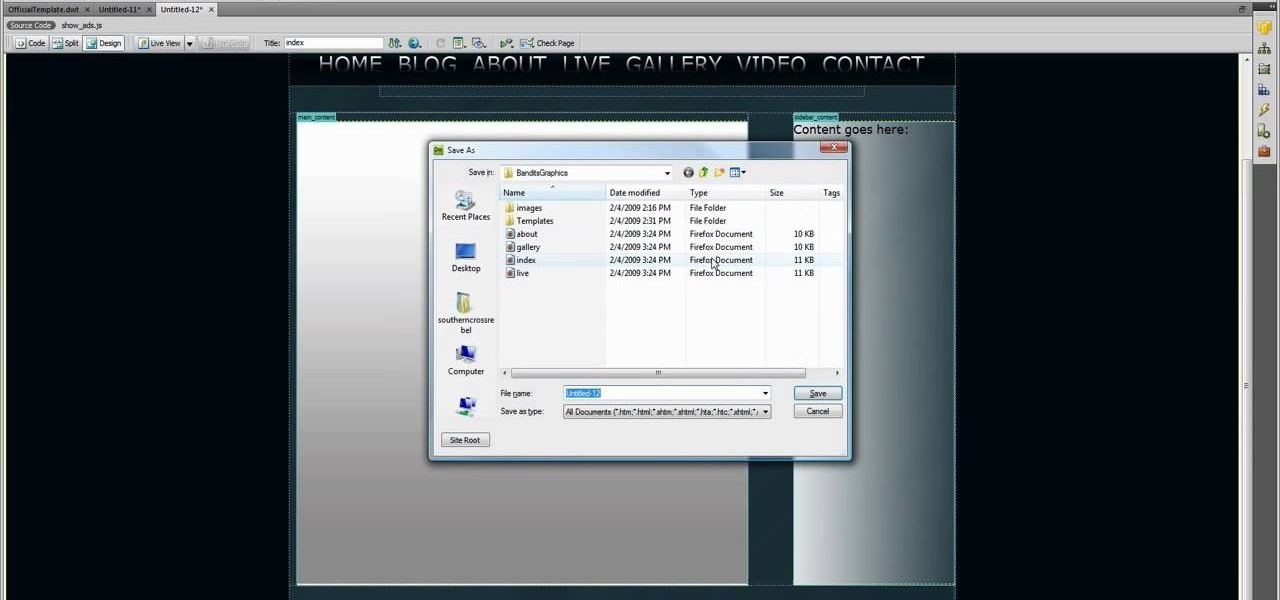
Down, down, down! Yep, what you want is lower on the page and you want to get there faster. SO, why not scroll baby scroll! Ever wanted your website to have a scroll bar? Well, now you can by watch the following video. This how-to will show you how to use Dreamweaver to insert a scroll bar to allow for easy navigation for your or your client's website. It's not too hard, so follow the bouncing ball and learn what to do.

In order to cut a long layer haircut, you will need a good pair of scissors. You must stay in the exact same standing position the entire time. Bring all of the hair together on each side, in order to cut it.

We usually give massages with our finger tips. Try massaging a client's arms with the palms of your hands. Learn the art of giving massage in this health how to video. Using the bottom of palm keeps you from getting tired so quickly and it helps you give a more effective massage.

In this tutorial, we learn how to give a Swedish massage. First, you want to start off by making sure your client is comfortable. Next, you will start to gently rub the body, starting circulation. After this, put cream on your hands and rub them together so it gets warm. Now, rub the client's body with the cream, pushing in the body in the middle of the back. Use smooth strokes, because these will warm the client up. Now, use your elbows and place them along the spine, pushing your body weigh...

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Hot stone massage is the placement of stones in various places on the client's body. This video series will teach you how to give a hot stone massage.

Whether it is a clown costume or a tuxedo, every balloon artist should have a costume or outfit to wear while performing with balloons. Finding a great costume shouldn't be that hard, but when it comes to picking one out it can be frustrating if you don't know what you're looking for. A few things to think about when trying to pick out a costume:

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Nobody could predict the success of Microsoft's Kinect, not even Microsoft themselves. So, it was quite a surprise when it ended up earning a Guinness World Record for fastest-selling consumer electronics device, and an even bigger surprise to see people buying one that didn't even own an Xbox 360.

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.