With Adobe Acrobat 9, creative professionals can take InDesign, Illustrator, Flash, Photoshop iles and more and convert them to PDF or a unified PDF portfolio making it easier to share files with clients and others. This tutorial shows you how you can use Acrobat 9 Pro easily with Adobe CS4 documents and convert them to PDF's or create portfolios. Learn how to review files, brand PDFs, add multimedia, and use print production tools in Acrobat 9 Pro.

Take a look at this instructional video and learn how to control the Mac with either your iPod Touch or the iPhone. This is done by setting up VNC client on your iPhone/iPod touch and your Macbook.
This video shows you how to use the Free Internet Chess server and the BabasChess client for it. This video covers some basics, and hopefully some of you who haven't tried FICS will find it beneficial.

Today's word is "amicable". This is an adjective which means friendly or peaceful.
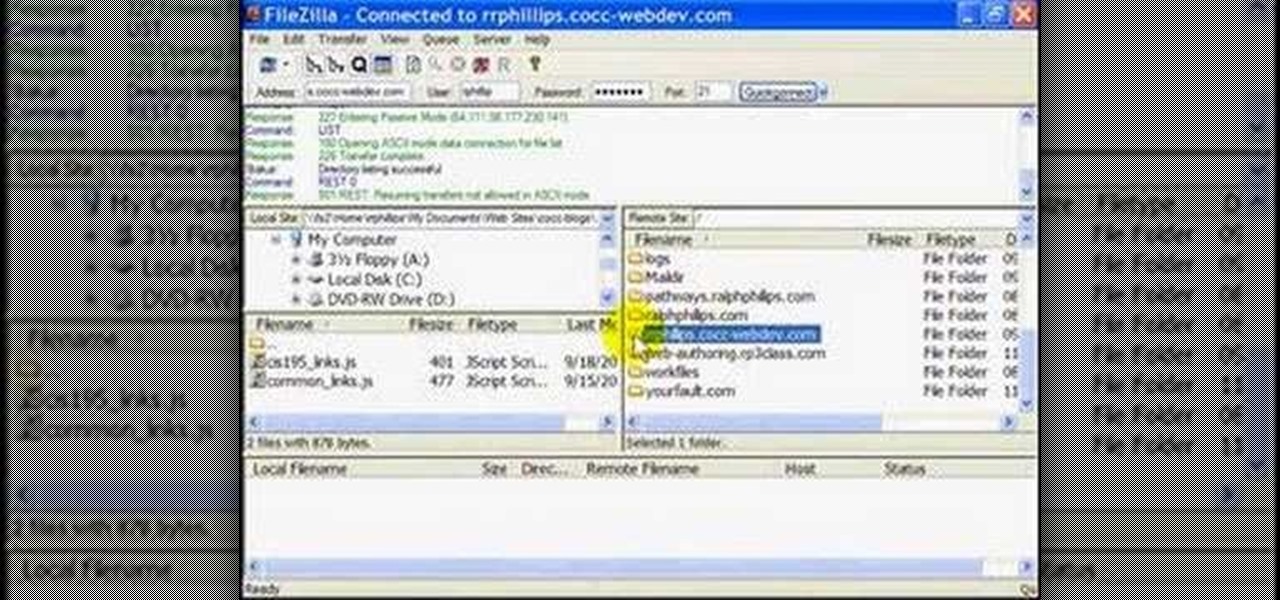
Use the Filezilla FTP client to publish files to your web server.
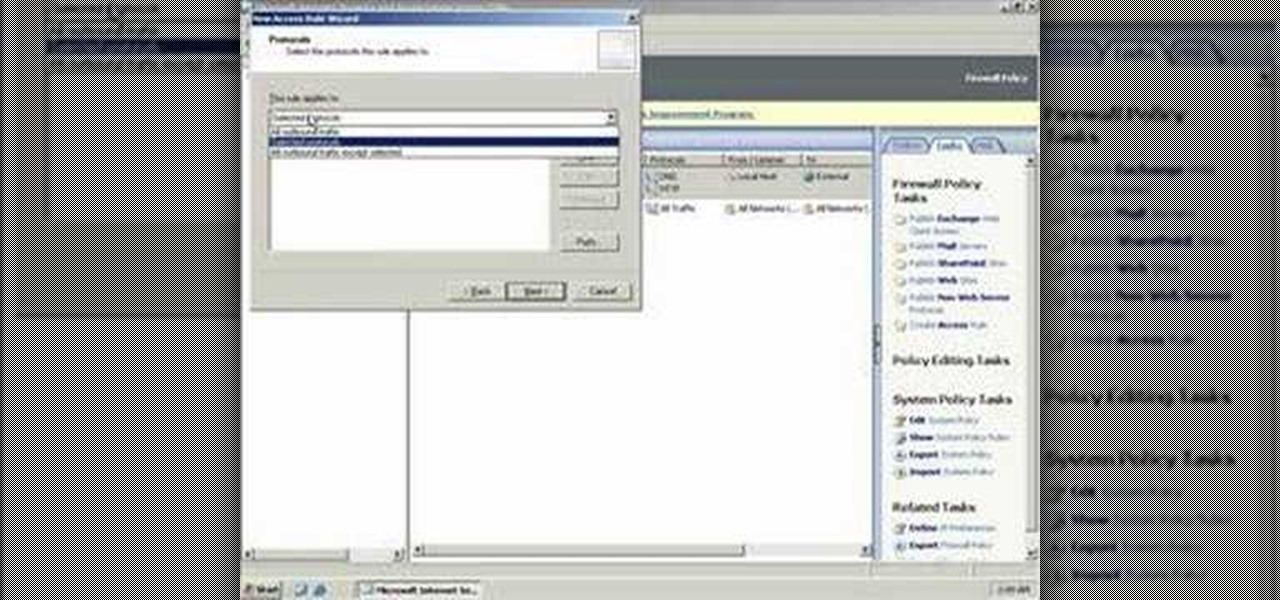
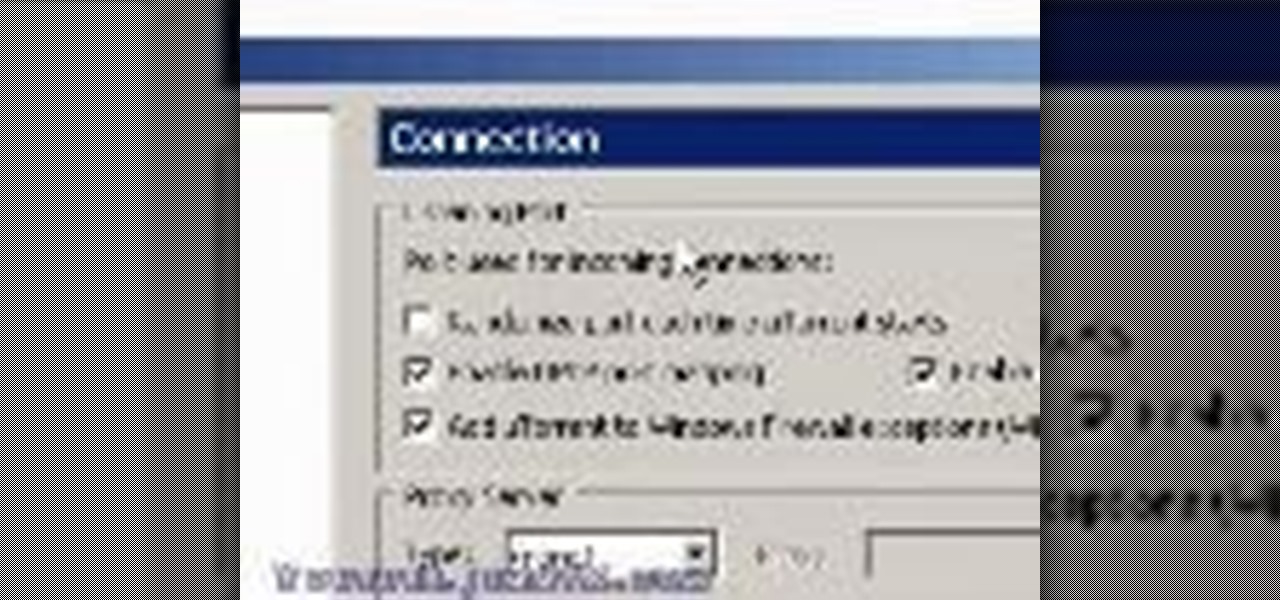
One of the uses of an ISA Server is to act as a proxy server. A proxy server allows your Windows XP and other desktop computers to make requests to the ISA Server and the ISA Server will then go and fetch the results from the internet or, if the ISA Server has cached the page(s), it can serve the pages from cache thus speeding up client browsing.

Bridging movements are some of my favorite Swiss ball exercises. They generally offer a wide progression difficulty. I've used the bent knee bridge with de-conditioned clients in their seventies and challenged young athletes with the advanced variations.

This knot is handy is you are saving on gear. Quite often I will choose to tye in over clipping in with biners. I often tyed clients in because I did not want them unclipping and running away without paying their bill.

A video on the basics of bittorrent technology and how to get started downloading a Bittrorrent client and torrent files.

This video explains how to make your bittorent client download faster. To increase torrent downloads increase your upload capacity to max, enable port forwarding if you have a router hub or firewall that blocks ports, and download torrents with a lot of seeds.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best due to Google's excellent cloud service, feature-rich web-client, and their easy-to-use Android and iOS applications.

In this cardmaking tutorial I use a Anna Griffin rubber stamp to make a repeat pattern in a very easy way, so if you have trouble repeat pattern stamping this could be for you. I make a lace edged card with 2 pretty flowers and a stamped sentiment. Step 1: Items Used

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

Work and School can be boring at times, that's why we do what we can to keep ourselves entertained. So I decided to come up with this funny prank so you can make school or work fun again. You will need a water balloon and someone's clipboard which contains important documents! This is a very mean prank and can definitely get you in trouble so make sure you know what you're doing. Watch the video tutorial provided to get an idea of how to pull this off.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

Video chatting over the Internet is an inexpensive way to keep in touch with your family and friends. This video will show you how to set up web video chat.

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Six Flags is teaming up with Samsung to make riding a roller coaster a little more thrilling, and quite possibly a little more nauseating as well.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

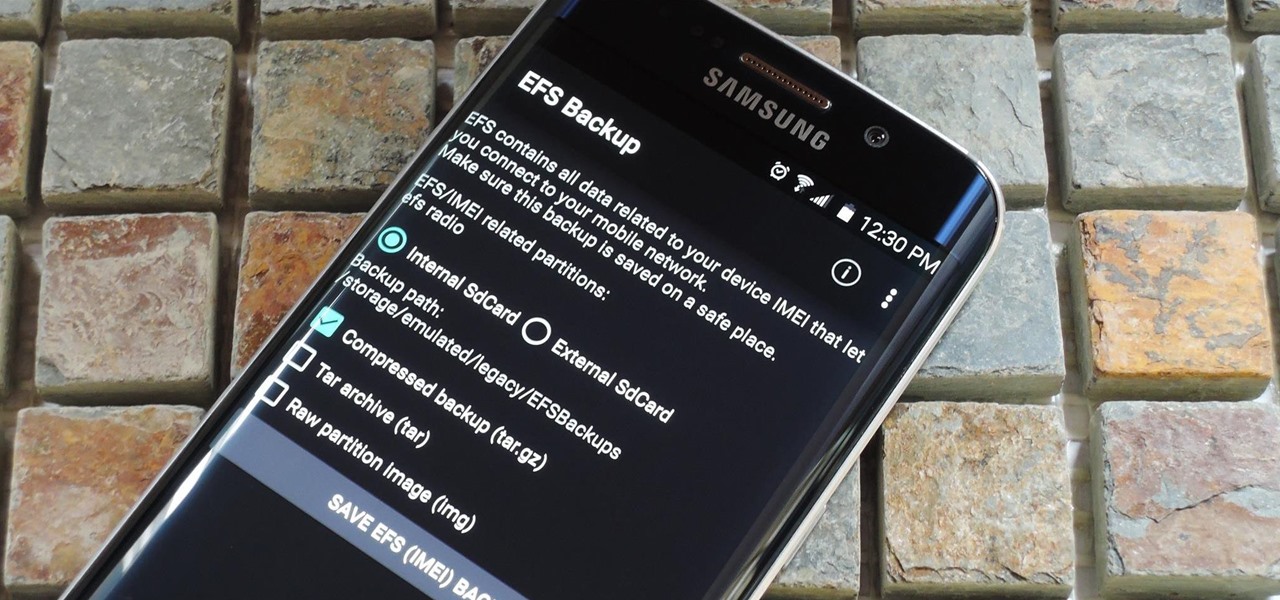
The EFS partition on modern Android phones houses the unique IMEI for your device, which is essentially an identification number that lets you connect to mobile networks. But sometimes, when you're flashing ROMs or restoring backups in custom recovery, the EFS partition can become corrupted, which will prevent your phone from connecting to any type of mobile network.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

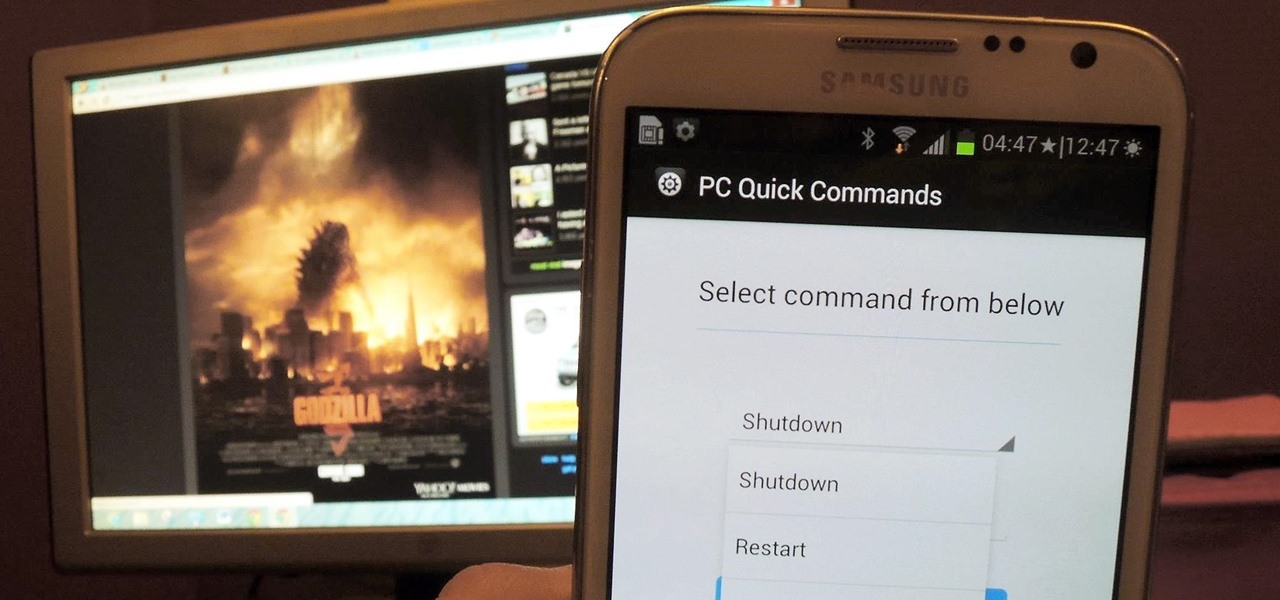
You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Get your numbering straight with Adobe's InDesign and this helpful tutorial, showing you what you need to know. It's essential when creating a project for yourself or a client, to get your numbering right the first time. There is no second chance. So, check out the steps and see how to turn this sometimes tricky task into a much easier one. InDesign offers a lot of options, and if you're going to master all it's tricks, watch this how-to to learn one of the most simple and essential tricks.

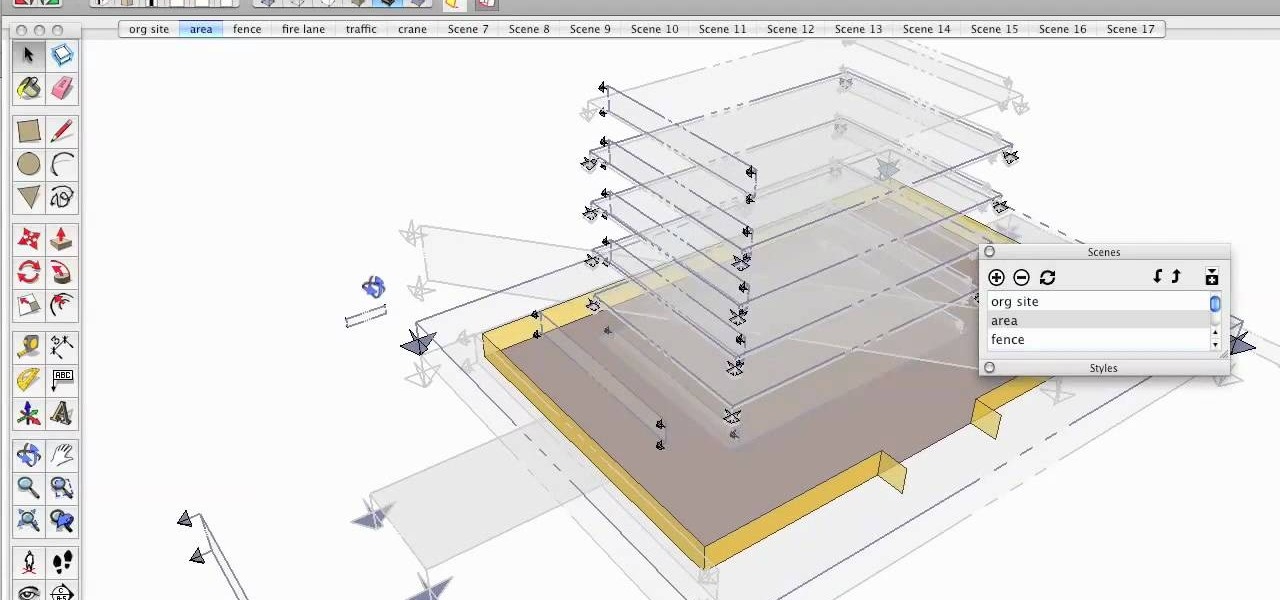
As you already know, Sketchup is a very cool program which allows you to design a myriad of things. But, did you know you can then animate those images? You can, and this tutorial will walk you through the steps to show you how. This is a very valuable thing to know if you're presenting something to a class, or client and want to show them the developmental stages of the project. So check out this video, get designing and put those pictures into motion!

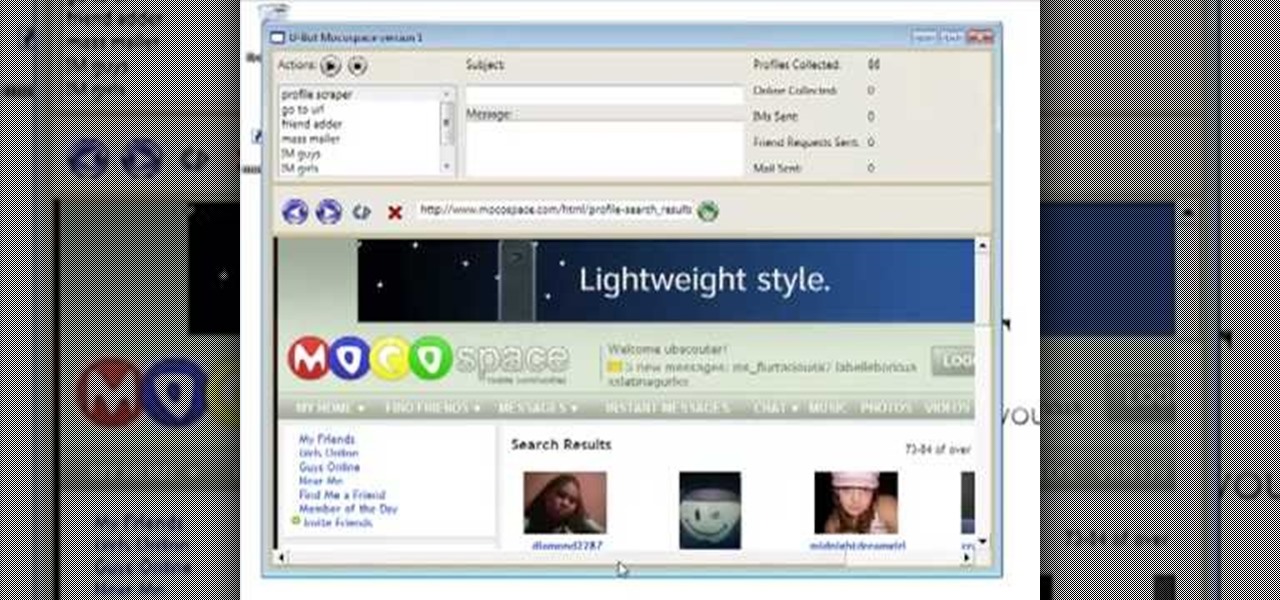
MocoSpace is a newly emerging social network, aimed and designed primarily for users of smartphones and other mobile devices. This tutorial shows you how to use the Ubot software to work with and monitor activity for your clients and customers on MocoSpace.

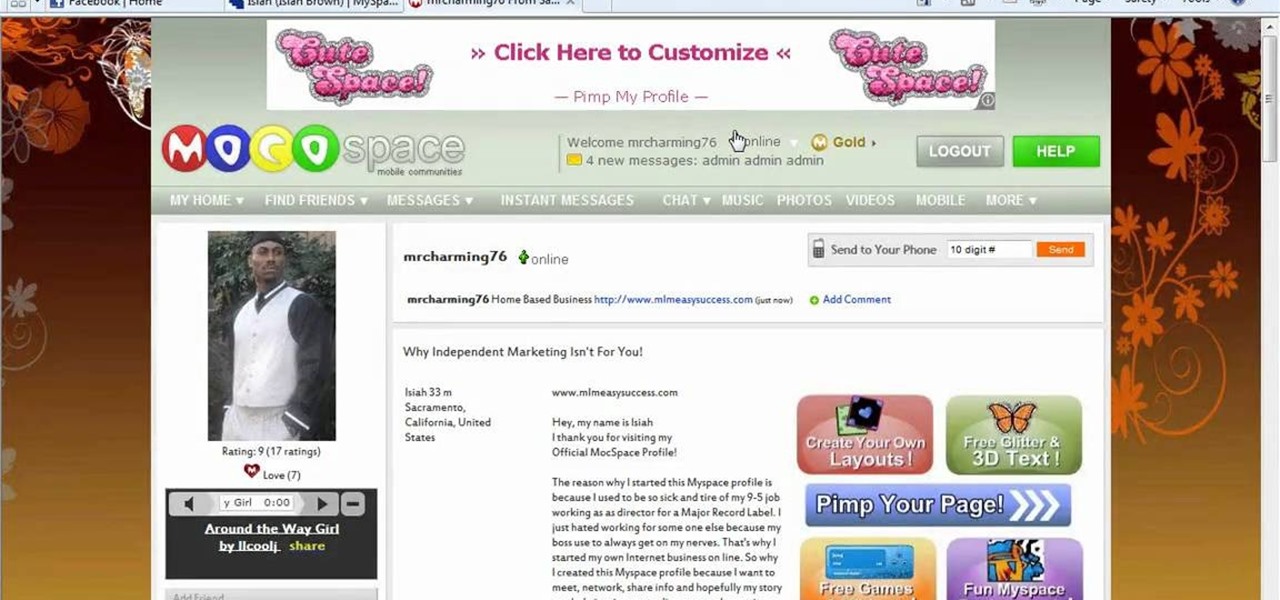
MocoSpace is a relatively young social networking site, primarily designed for people who have mobile phones or smartphones. Make sure you can stay connected to all your prospective customers and clients by using the advertising tools and opportunities that MocoSpace offers!

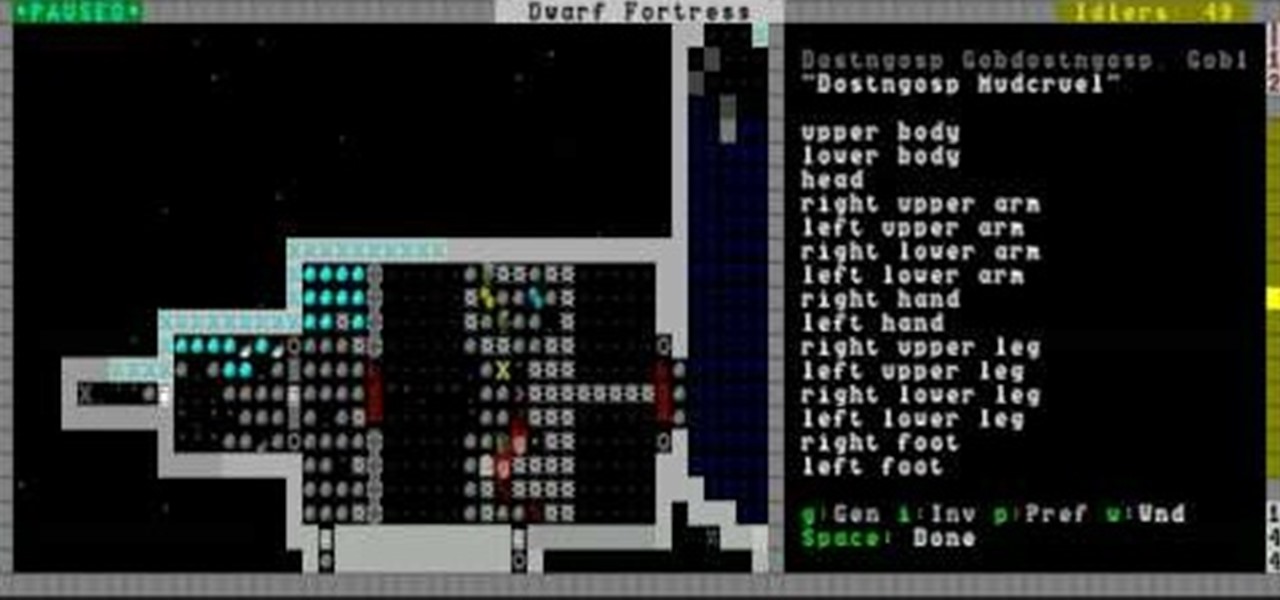
You can capture almost any enemy in Dwarf Fortress, and there are all sorts of creative ways of dealing with them once you have them. This video will show you some cool ways of killing and otherwise killing your captives.

Late in the Dwarf Fortress game building machinery can allow you to pump water around the map and power mill stones to make more advanced food. This video will show you how to build and use machines safely, without destroying your fortress and the lives of your dwarves.

The siege is on! This video will show you how to defend your fortress against a human siege and also explain the most-used and best traps in Dwarf Fortress. The second part is not a how-to, but shows the defense against a human siege playing out so you can understand it better.

If you think about it, your face is just another canvas, with makeup being the paint. You add highlights here to bring parts you want to emphasize forward, bronzer there to create fake shadows, and draw on patches of color (lips) or lines (eyes) to make things either pop or recess.

In this video, we learn how to prepare yourself for a major disaster. If you haven't planned ahead for storing water, you are going to be in big trouble. Your first option is to go purchase liters of water from the grocery store. The recommended quantity to store is 1 gallon per person per day. If you don't want to spend money at the store, you just need to fill up empty bottles with water from the tap and store these after cleaning. You can also fill the water in a large jug, just make sure ...

If you're a graphic designer, you've probably dealt with clients who sent you the wrong files, like JPG and BMP "source" files. You need to the EPS vector files, but they don't know what that is, and they don't care. They want that image or logo they sent you blown up to poster size for a billboard or something.