So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy for this hack. If you follow the instructions in the video, you'll have a completely rooted Motorola Droid X cell phone. Try it out.
Today, BitTorrent Inc. released the SDK for uTorrent Apps, which will allow software developers from around the world to create Apps for uTorrent, the popular bittorrent client. This video will show you how to download the SDK, install it on your computer, make an app, view that app in a browser, and then package the app and view it within uTorrent without compromising uTorrent's famous lightness. This is a big day for bittorrent fans around the world; download the SDK and start making uTorre...

This clip demonstrates some rehabilitation exercises that you can use for clients who have suffered from an amputation. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

This is the ultimate guide to drawing correct human proportions. If you've always had trouble with it in high school art class or in art school, this video condenses all the information into a tight package that's fun and easy to understand. This will uncover all the tricks to human proportions for figure drawings.
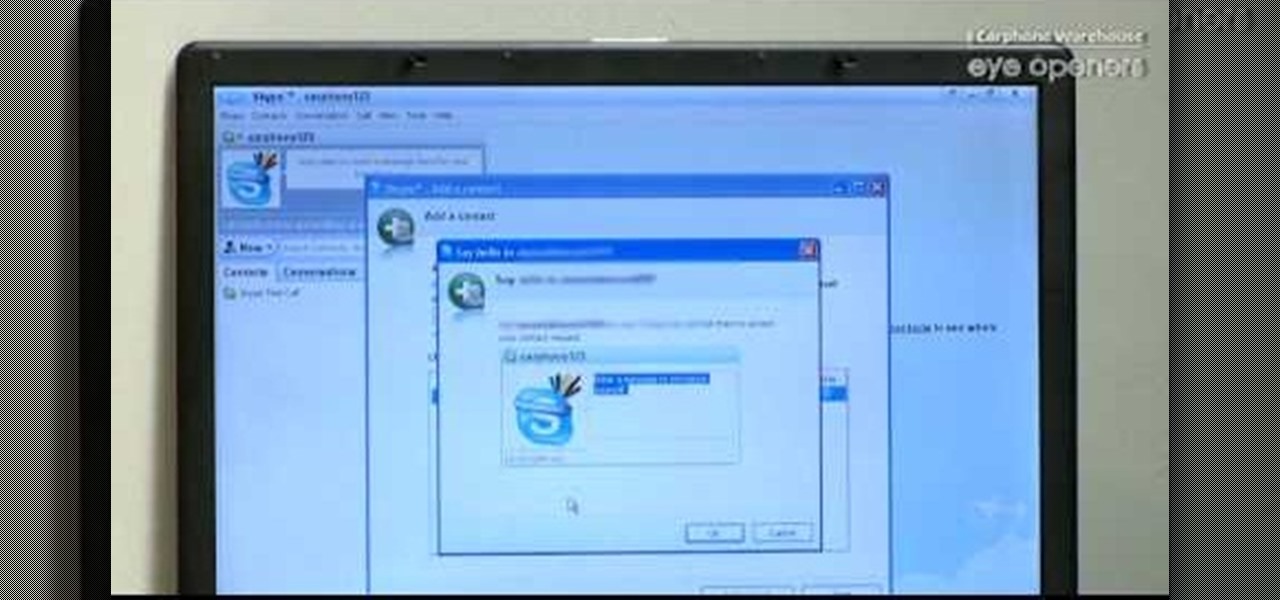
Cellular telephones? So 20th century! With this techy tutorial, you'll learn how to install Skype on your laptop and use it to make phone calls to your friends over the Internet – all without long distance rates! For more information, including step-by-step instructions on how to install the Skype VOIP (Voice Over IP) client on your own computer, watch this free video how-to!

Is your current doorknob sticky, wobbly, or just not cutting it out for you and your family? Well in this video Barbara K will demonstrate exactly how to replace any doorknob in your home.

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...

Paulant Films has some great information on how to download and rip Xbox 360 games. In these four video tutorials, you'll learn how to hotswap, stealth patch, and burn Xbox 360 games.

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

If you're new to Ubuntu Linux and, for whatever reason, not so very keen on Ubuntu's default email client, Evolution, then you might like to try Mozilla Thunderbird. In this tutorial, you'll how learn how to go about setting up an email account in Thunderbird. Take a look.

If you're new to the Mac OS X operating system, one of the first things you might like to do is set up an email client. In this how-to, Gary Rosenzweig looks at how to set up the Apple Mail application to receive and send email from a standard ISP email account.

Watch this software tutorial video to learn how to better install Yahoo Messenger so it will behave how you want it to behave. Yahoo's IM Client can be difficult, but this how-to video offers tips that will help you install it so it won't be.

In this video, Massagenerd demonstrates various techniques that can be used to massage the leg and foot regions while the client is sitting on a chair. Watch and learn.

Want to know how to set PDFs up so that they can be digitally signed? In this Adobe acrobat tutorial you'll see how to set up a PDF to accept a digital signature. You all also see how to create your own digital signature for signing and a strategy to work with your clients so that you know who is signing those documents.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

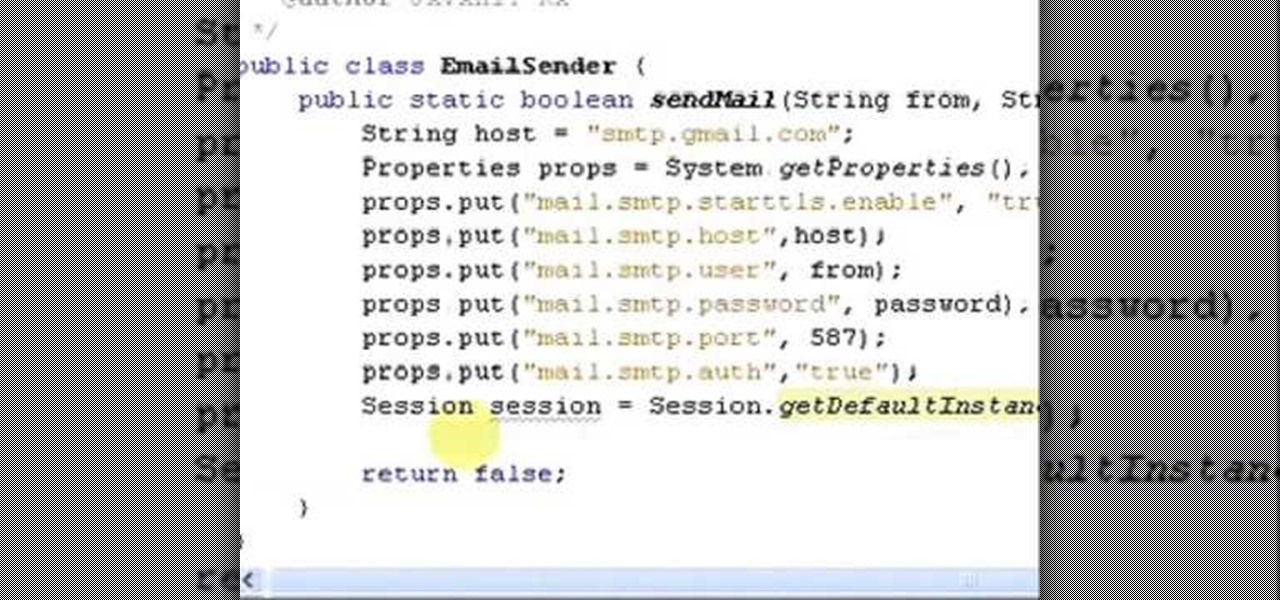
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

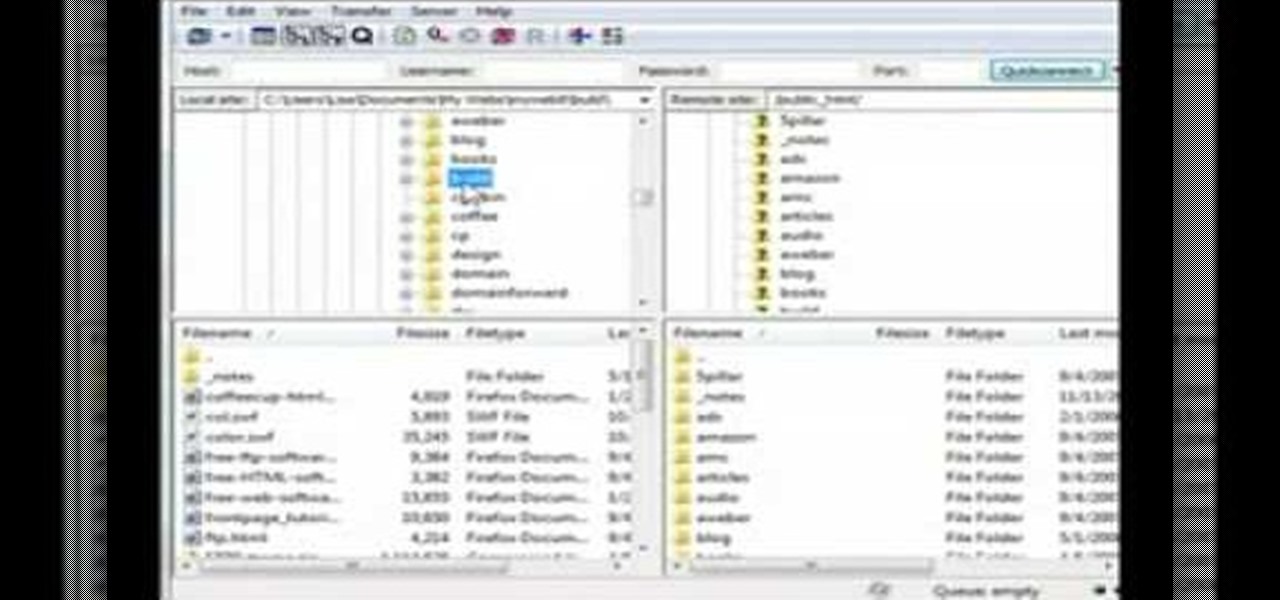
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

In this automotive repair video you will learn how to fix the ABS and speed sensor in a Dodge Dakota truck. Learn how to read diagnostic trouble code to evaluate trouble indicators and fix broken sensors. So if your speed sensor or ABS brake system are on the fritz in your Dodge Dakota truck, watch this video and learn how to check and fix them.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

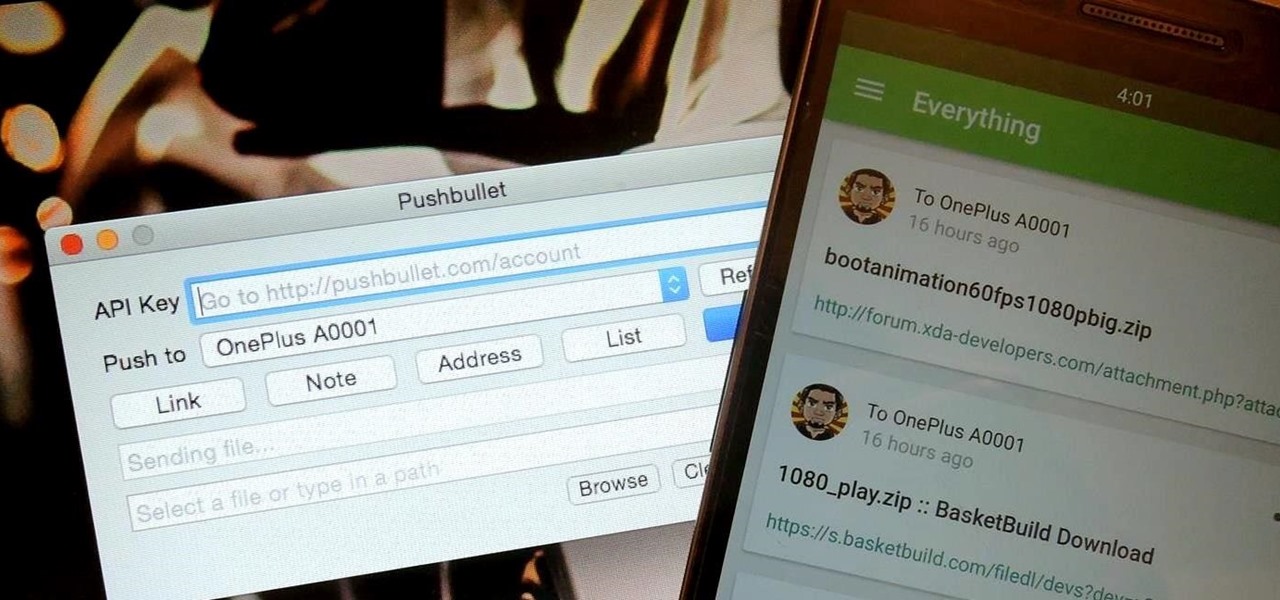
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.