Deleting emails can be a tedious process on the iPhone, especially since the "Trash All" options have been removed ever since iOS 10 first came out. Though likely well-intentioned, this change places an undue burden on all of us iPhone owners who now have to erase emails individually.
Velodyne wants to set the standard for the driverless industry when it comes to LiDAR. To do that, the Silicon Valley-based team just announced its next step — create a low-cost, fixed-laser sensor that can be embedded into a wide range of automotive and autonomous vehicles. That next step is named the Velarray. A sturdy, compact, and affordable LiDAR laser.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

Apple has yet to create a successful social networking app, but that doesn't mean they want to be left out of the social video conversation. Case in point: Today they announced a new video app set to debut for iOS in April called Clips.

Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.
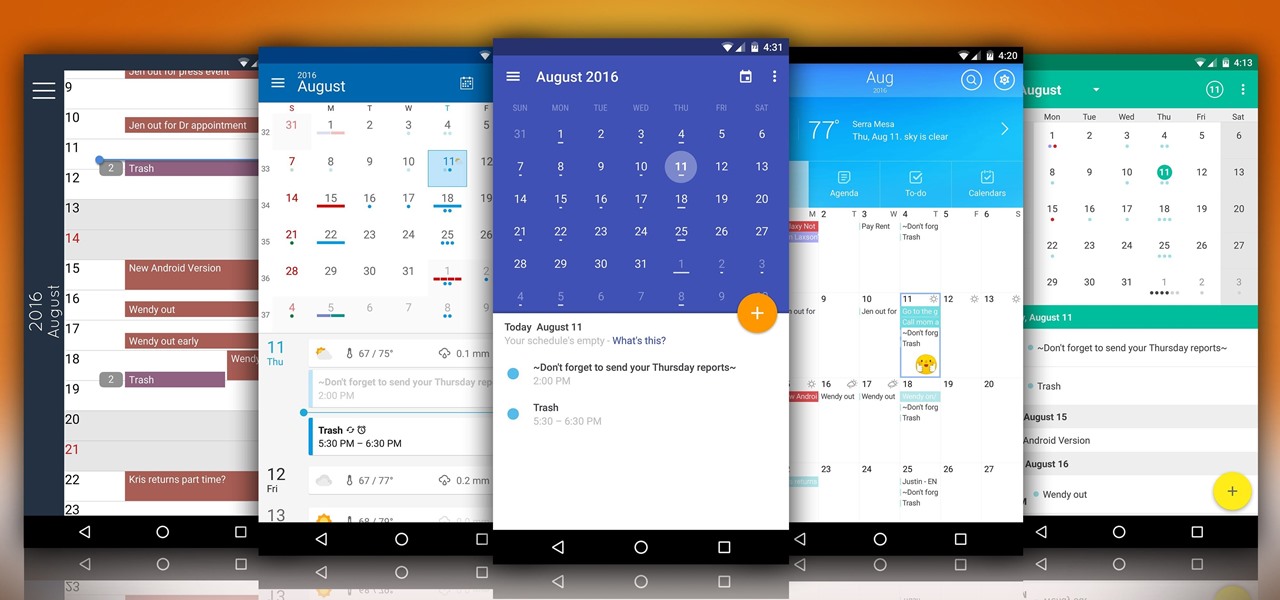
Whether you use Google Calendar, Exchange, iCloud, or any other service, you need a good Android calendar app to keep you organized on the go. For many folks, the obvious answer was always Sunrise Calendar, but Microsoft purchased the company behind this awesome app in a classic acqui-hire move, and now, Sunrise has officially been shut down.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Pickling isn't rocket science. In fact, anyone can make their own speciality pickles using just about any fruit or vegetable. For example, I've pickled everything from lemons, watermelon rinds, and apples to red onions, carrots, radishes, and cucumbers.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Checking the weather ranks among the most mundane but essential tasks you can do on your smartphone. Thankfully, both the iOS App Store and Google Play are loaded with weather apps that add some much needed spice to this daily routine, giving you less of a reason to be caught unaware.

In my opinion (and I suspect in the opinion of the masses), there is no greater snack food than potato chips. They're crunchy, they're salty, they're fried, and they're bite size; what's not to love? But I believe that, like almost all foods, potato chips can get even better. Especially if they're the most basic garden variety type of chip: sea salt.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more unique, and, yes, even more flavorful.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Hops have always been known as the driving force behind beer, but now they're starting to grow their own culinary wings. Slowly but surely, this bizarre and bitter plant is showing up on more and more menus across the country as it catches on as a trendy and up-and-coming ingredient. What Are Hops?

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

It was a chilly but otherwise beautiful night at YouTube Spaces LA—food trucks, ping pong, a photo booth, and the chance to view film school projects created completely with Glass. About a year ago, the Glass Creative Partnership was formed to explore how Glass could be used in filmmaking, with partnerships spanning from the American Film Institute to CalArts and UCLA. On July 16, 2014, the products of that partnership were screened under the Southern California night sky. Three films were sh...

Google's new camera app has a highly innovative and unique feature dubbed Lens Blur, and the most interesting thing about it is not necessarily what it does, so much as how it does it.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

Time-lapse videos are a recent phenomenon to the mainstream audience—in movies, on television shows, and even in commercial ads. These sped-up and blurred images are a microcosm of many of our lives in which we're constantly in a hurry to get somewhere. We like everything fast: our work, our coffee, and our news.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

The holiday season is creeping up fast, and if you're shopping for a Steampunk, it could be almost impossible to find anything for them unless you know exactly where to look. Luckily for you, some of us have done all of the work you'll need. Whether you're Steampunk shopping for Christmas, Hanukkah, Chrismukkah (yes, that's real), Kwanzaa, or Festivus, you're sure to find something for that special lady or gentleman in your life by taking a stroll down this list!

Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...

El Dia de los Muertos, or Day of the Dead, is, despite what its name may imply, not a spooky holiday. The Mexican celebration takes place two days after Halloween, on November 2nd, and involves visiting the graves of your loved ones and communing with them through "shared" food.

Vladimir the Crimson Reaper is the closest thing to a vampire you can bring onto the Fields of Justice. His abilities are focused on taking health from his enemies to build himself up, and this tutorial shows you the best build with spells, runes, abilities and items to take advantage of his unique talents.

In this Games video tutorial you will learn how to play the Pente (Pentagon) marble game. It's a game of skill and strategy played on a 14" square hardwood game board. It can be comfortably played by 2 people or two teams. Teams do not have to be balanced (two against one, three against two, any combination). The board is divided into 3/4" squares. The unique feature of this board is the four holding trays for the playing gems. First decide who will start. The starting player places a gem at ...

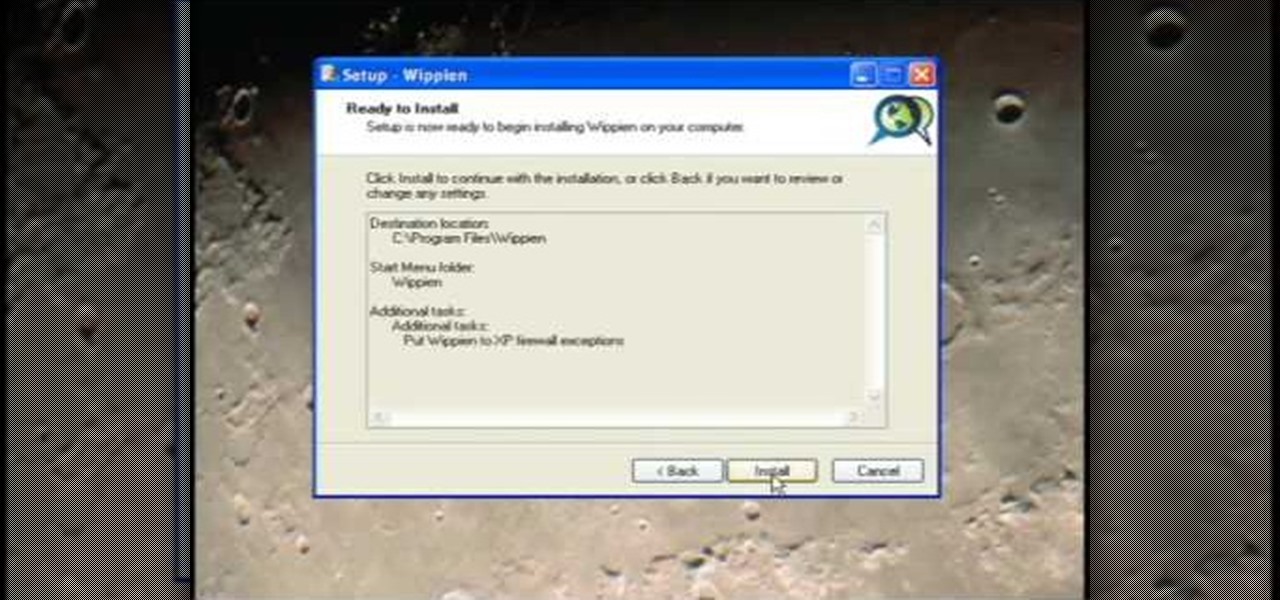
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.