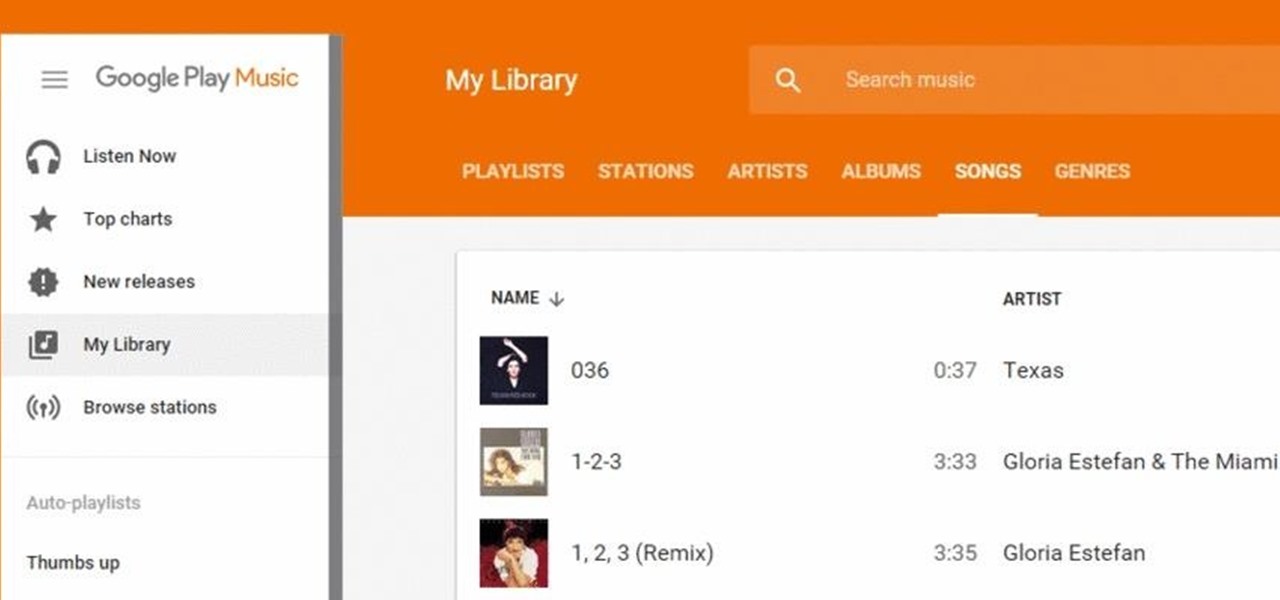
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

According to the American Osteopathic Association, "1 in 5 teens has some form of hearing loss," and some experts believe it's because of an increase in headphones use. While I understand that music, movies, and video games help keep children preoccupied, there's no reason why they can't be entertained at a healthy hearing level.

Hello again, ***UPDATE: Adding links to the other Two articles****
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

If you don't have the time or patience to build a complete Ant-Man suit from scratch, there's another way to make a Ant-Man costume for Halloween. If you're more skilled with brushes and makeup rather than drills and cardboard, this is the Halloween DIY for you—especially if you're a fan of the Marvel universe.

Ant-Man isn't one of the most famous Marvel superheroes. In fact, with the news of his individual movie came great doubt that the comic book legends could succeed in telling the tiny story of an oddball hero on the big screen. Yet with its humor and unique story, Ant-Man has become a hit movie in its own right—and the hero will most certainly make a hit Halloween costume.

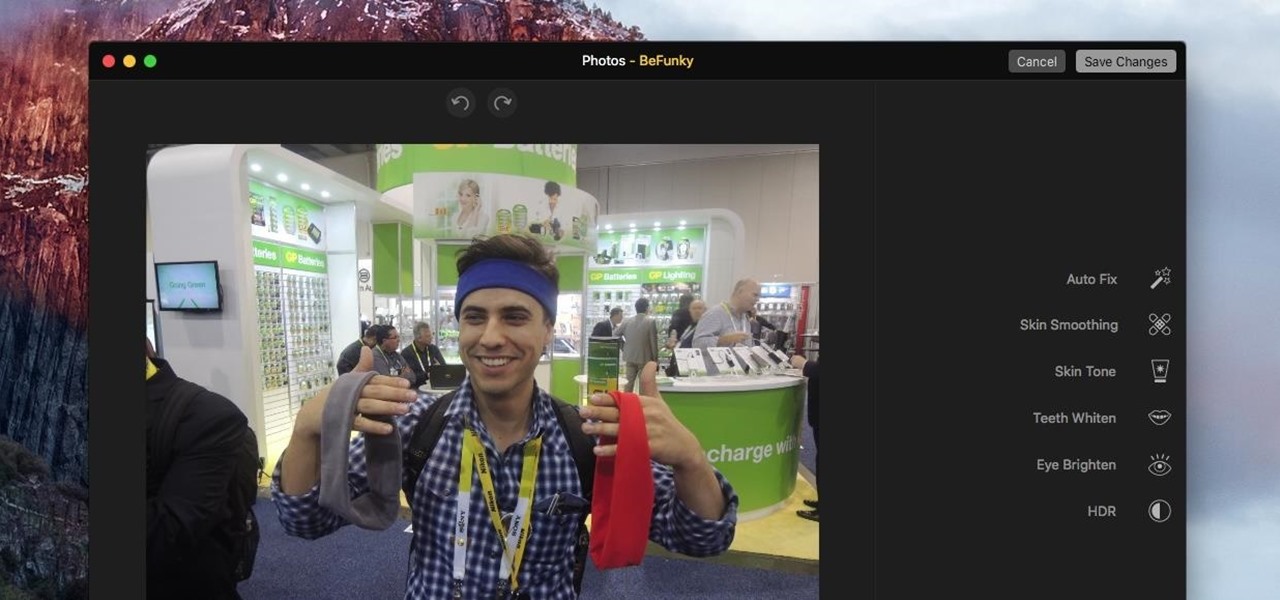
For minor adjustments and color-correction, the Photos app is extremely useful, but its capabilities are limited to just the basics. Now, with Mac OS X El Capitan, Apple is opening the door for third-party extensions, meaning we can utilize additional, unique tools when editing pictures in Photos.

There has been a huge shift over recent years to alternative medicine as people get disillusioned with conventional medicine to overcome anxiety. Natural and herbal supplements are becoming popular as people re-engage with nature. The list of potential side effects from drugs and the rebound effects from withdrawing often make the thought of taking medication unpleasant. Often the promise of how effective the medication can be is exaggerated or it simply does not have the effect it should bec...

One of the biggest gripes I initially had with the LG G3 was the lack of options for the Shortcut keys, which are the volume keys that allow you to launch the camera or the QuickMemo+ app directly from the lock screen. I never use QuickMemo+, so having it as a shortcut was a complete waste of functionality.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

Sometimes just drinking your alcohol can feel a little dull and boring. Eating your alcohol, however, is always a party.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

Whether it's to flaunt your new digital face on Instagram or to show off a unique app to your friends, you'll ultimately need to know how to take a quick screenshot with your shiny new Apple Watch. Turns out, it's not that much different than taking one on your iPhone.

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.

HTC's fitness-tracking application, Fun Fit, has made its way to the Google Play Store for all to enjoy. And while fitness apps are a dime a dozen, Fun Fit offers what its name implies—fun. Like plenty of other fitness apps, Fun Fit is able to track calories burned, steps, distance, active time, walking time, and running time. Where the app differs is in its presentation.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

Some elements of iOS's design, like its minimal color palette, are what make Apple products unique, helping to produce a clean, sleek user experience. But after you jailbreak, that all goes out the window. Once you've tried things like theming your status bar, changing your icons, or applying a new lock screen, you'll never see your iOS device in the same way again.

Reddit is a force to be reckoned with. What started out as link aggregator has become one of the world's most popular websites, with over 170 million unique visitors and 6 billion monthly pageviews. Whether you're into cute animals, crazy conspiracy theories, sports, or Taylor Swift's armpit, Reddit definitely has something for every taste, interest, and morbid curiosity.

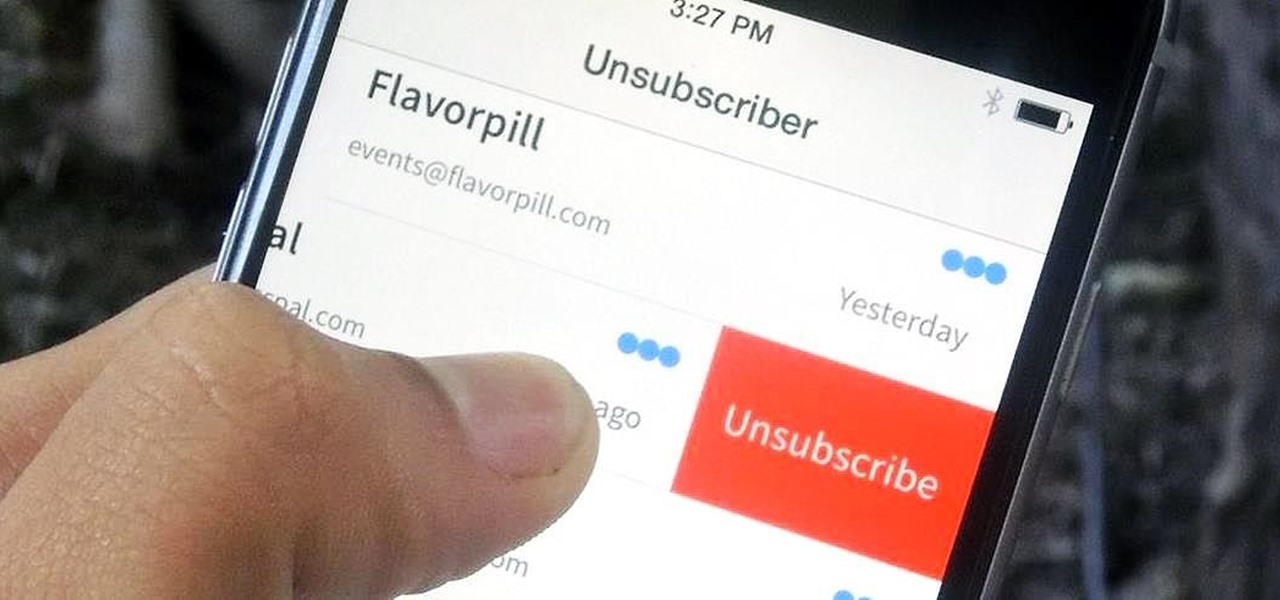
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

Sometimes it's not the look of a product that makes it unique, but the thought that went into it. That's what struck me about TobyRich's SmartPlane—it isn't the most elegant toy on the market, but its simplicity and function make it a winner.

As competition for Spotify and Pandora, Samsung released Milk Music earlier in 2014, a free music streaming service for their Android devices. While Milk was unique to Galaxy owners only, it was popular enough that we showed you ways to get it on non-Galaxy devices as well.

While the new Lollipop wallpapers are great, they'll eventually get stale like all of the others. I've covered a bunch of cool Android wallpaper apps previously, including ones that give you psychedelic and shake-to-change options, but this time I was on the hunt for some geometrical-based ones.

With the Power key located on the back of the device, LG included a convenient "double-tap to sleep" function in their G2 and G3 devices. The function allows users to simply double-tap the display to put their device to sleep instead of picking it up and pressing the Power key.

We've already told you how the Japanese pioneered growing specially shaped watermelons (including square, heart, and Godzilla egg). Now it turns out an organic farmer just north of Los Angeles is doing them one better.

Guardians of the Galaxy wowed moviegoers this summer with its sassy, strong team of intergalactic superheroes. From Groot, the ever-growing tree, to Rocket, the rough-around-the-edges raccoon, the film had an unending supply of unique characters—but no one stood out as much as Gamora.

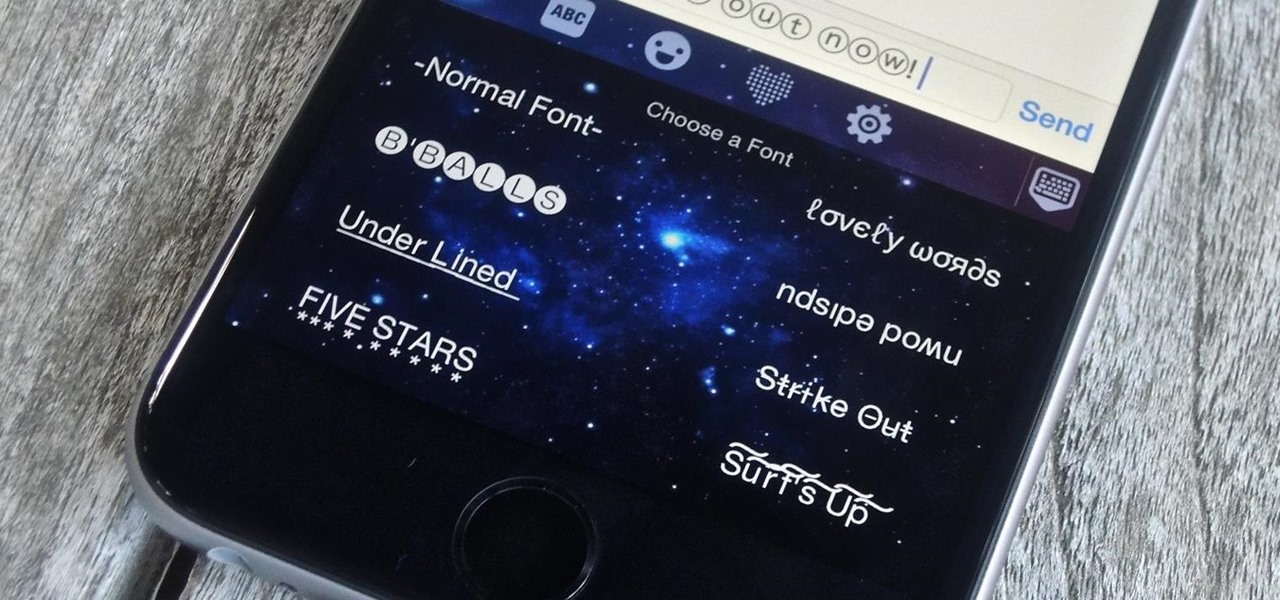
Allowing the use of third-party keyboards on iOS 8 was a great move on Apple's part, providing iPhone users with choices when it came to an often-used and important aspect of their operating system. Unfortunately, as cool as all these keyboards are, they all use the same boring, stock font.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

Sometimes, when it comes to Halloween costumes, the easiest ones to make are the best. They require little effort, but can pack a punch and look even more authentic than complex character replications.

Creating interesting photographs used to be more fun, before we all collectively decided that color filters and rotations qualified as "unique" smartphone pics. Scrolling through my Instagram feed only confirms that these supposedly special, filter-laden photos are actually the norm now.

The camera on the Amazon Fire Phone is simple and easy-to-use, with a 13-megapixel rear shooter with optical image stabilization, but there are a couple of features that makes this camera stand out from others.

With the release of the M8, HTC decided to begin publishing some of its exclusive apps to the Google Play Store. While most of these apps aren't available for download unless you own an HTC device, this practice made it possible for the Taiwanese smartphone manufacturer to issue updates to its users independently of carrier-modified firmware upgrades.

Fact: we live in a world where social media dictates our behaviors and shapes our perceptions. Maybe some of us are addicted more than others, but most of society uses some type of social media, whether it's Twitter, Instagram, Facebook, Snapchat , or something new that I've never heard of.

Starting today, you can experience all the unique feature of Samsung's next flagship device, the Samsung Galaxy S5, right on your Galaxy S3 or other Android device.

Jotting quick notes can be a pain. There have been countless occasions where I've needed a pen and paper to quickly write something down, but either didn't have them near me or was doing something on my phone and neglected to remember.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

It feels like someone just overheard me talking shit about my iPhone. I really hate when I need to edit an email, text, iMessage, or whatever because of the way you have to select words and phrases. You either hold down on the screen where you want to bring up the menu, or double-tap to highlight a word. It's crap.

Winterboard for iOS 7 allowed us to use some pretty great-looking themes. Circulus and Space BlueBerry are both great, but a little too "fun" for me. If you want something serious, yet appealing to the eye, then M'flat is for you.

Long before Windows Phone hit the scene, Windows Mobile was the operating system for Microsoft's older brand of smartphones through the early 2000s. But due to its clunkiness and inability to keep up with modern features, it was scrapped in 2010.