Time is money, and if your job requires sending out hundreds of generic emails—think "Thank You" notes and sales pitches—you could save days of work by creating templates stored within your Gmail called "canned responses."

Prying into people's lives without them putting up their guard can be difficult, unless you can convince them that you already know them very well. Most people don't have many friends they can be honest with, and this can be exploited. Once they're convinced you already know their secrets, they'll start to fill you in on the little details.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

Included in Spotify's new darker, slimmed down redesign is a much needed My Music section, which consolidates all of your starred music, local files, and playlists into a personal collection of songs, albums, and artists, similar to how iTunes organizes your music. This makes me wonder...

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android devices. Quite the opposite really, as we saw from leaks of its new Magazine UX. The new user interface was shown during Samsung's presentation of it's latest Galaxy tablet at this years CES, and as reported to Re/code,...

The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

If you have a group of large files that need to be sent to a client, you might want to compress it into one single file for easy access or even protect its content from outsiders with a password. This video will teach you how to create password-protected zip files with WinRAR. WinRAR provides full RAR and ZIP file support, and can decompress CAB, GZIP, ACE and other archive formats. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so ...

The key to this skit is to get someone incredibly drunk to the point that you can move them without their knowledge. As soon as they pass out, dress them in an orange jumpsuit and take them to a prison or a studio made to look like a prison. The cell-mate (actor) needs to be someone who looks like a big old biker, and is named “Sweetheart,” who makes a lot of references to the victim’s ass hole. When your victim wakes up, they will be in the jail cell completely confused. Sweetheart will say ...

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Outside of plastic surgery disasters or costumes, augmented reality is the closest we can get to morphing our likenesses into those of animals.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Since the internet is becoming more and more important all the time in regards to overall marketing plans for many companies, it’s imperative that the company website be up to the task of attracting visitors and converting them into customers. There are many methods and techniques to do this and for that reason it’s usually preferable to hire a company that focuses on online marketing or search engine optimization (SEO) to do this work.

It may not be your number one spot for finding cool apps for your Android device, but the Amazon Appstore for Android is running a new promotion this week called "Geek Week," where eight of the most popular productivity and utility apps are now on sale for 48 percent off or more.

The augmented reality space is no longer about if but when every company and creator will use some kind of immersive device and software to produce and distribute 3D content.

Videos hosted on Streamable may be fleeting or forever. So when you come across a cool video that you want to watch again later, it's a good idea to download it to your device in case it's one that disappears after a few months. There is no built-in download button in the Streamable player, but that doesn't mean you can't save anything on your iPhone.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

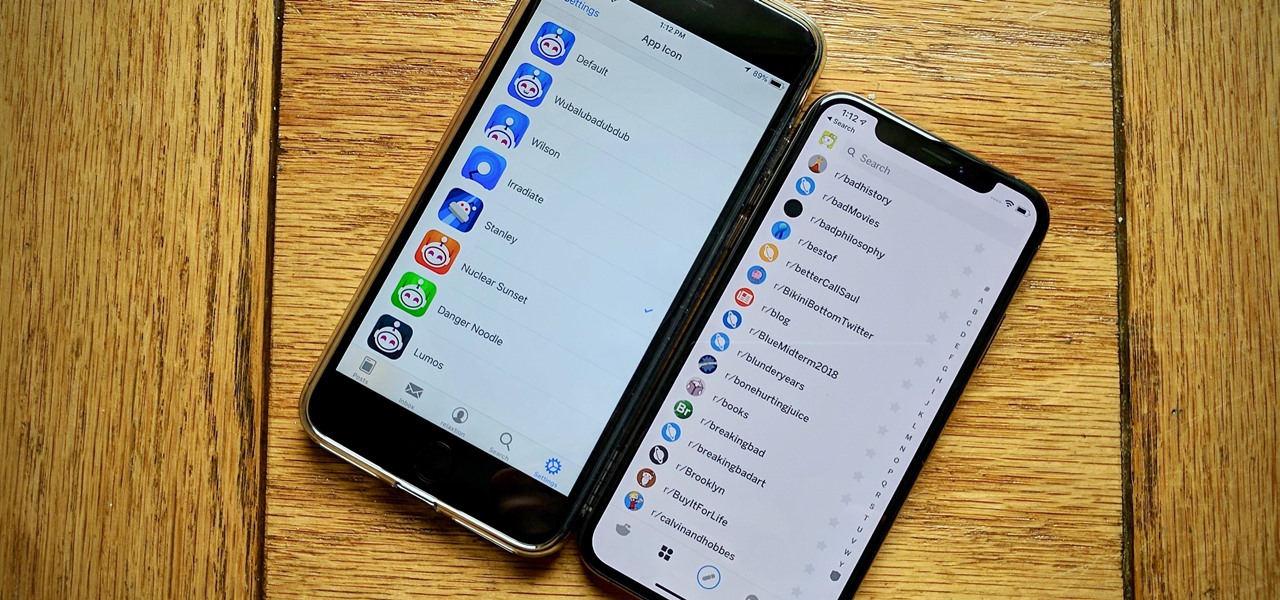
These days, using Reddit on your iPhone is just as good, if not better, than Redditing on a desktop browser. While there's an official Reddit app for iOS, there are plenty of third-party clients that have similar features as well as custom perks to enhance the experience. But figuring out which Reddit client is best for your daily use can be a lot of work — work that we can make easier on you.

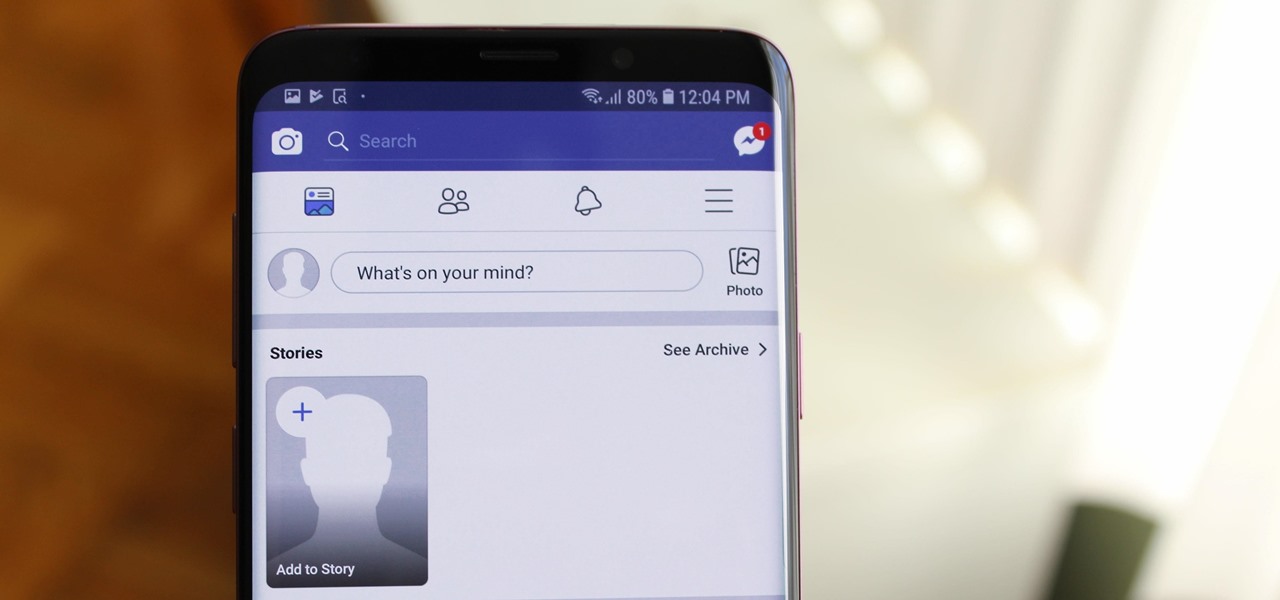
When Facebook introduced Stories in 2017, many users despised the Snapchat-like feature on their main page. However, despite the outcry, Facebook doesn't plan to let you remove it. But you don't have to settle for this. With the help of some third-party apps, you no longer have to deal with Stories.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.