Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

Nobody could predict the success of Microsoft's Kinect, not even Microsoft themselves. So, it was quite a surprise when it ended up earning a Guinness World Record for fastest-selling consumer electronics device, and an even bigger surprise to see people buying one that didn't even own an Xbox 360.

You have two choices for keeping your living room looking fresh: A. constantly update the decor by tripping out on acid—NOT recommended—or B. paint your living room white and get two video projectors. Created by Mr. Beam:

Surfing Magazine staff photographer Nathan Lawrence and Balaram Stack, Oliver Kurtz and Michael Dunphy descend upon Bocas Del Toro and Red Frog Bungalows for a surf trip of a lifetime. Nathan Lawrence is one of the best surf photographers in the world and he summed up the conditions over the week as ,"the best beach breaks I have ever seen in my life". This is saying a lot for someone who is payed to travel the world and snap photos of the best professional surfers in the world. look for the ...

"Freezing Moments" is a great piece of video of different liquids dramatically reaching freezing point, directed by Andrey Muratov. It's cryptically described as "Components of the space. Between existence and 'No!'. Alive - Absorbs." Hmm. Client is also cryptic: GTLK (Gosudarstvennaya Transportnaya Lizingovaya Kompaniya). Appears to be Russian, which would translate to the "State Transport Leasing Company".

THIS IS IN THE PALTALK PC TECH ROOM..

Though only just released, the official Skype client for Android has already been unlocked. Thanks to xeudoxus of DroidForums.net, American Android users may now do what their European counterparts have been able to do all along: make free Skype-to-Skype voice calls over 3G.

In this tutorial, we learn how to track work in progress while using QuickBooks. Start by enter in an estimate and then click on the button to create an invoice. The progress invoice will now appear to track what you want to do with the estimate. You can then choose what you want to fill out, and show either quantity and rate or you can show percentages. You can now change the numbers and figures onto the page, and then click "ok". When finished, you will be brought back to your original page...

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

Indie developers and their games have enjoyed massive success distributing through Steam, notably Zeboyd Games and Carpe Fulgar. While that bodes well for the future of indies on the platform, Steam has to devote a lot of front-page real estate to AAA games and thus can't promote small indies as well as a dedicated indie game distribution service could. IndieCity out of the UK seems like it could be that, but today a consortium of three German game companies launched their attempt at beating ...

Video games were blamed in the death of Chris Staniforth last May, but now things have gotten worse as video games take the blame for a more recent tragedy...

Kizeme This Japanese word, kizeme, means "spirit of attack." It is said of Miyamoto Musashi, the famed Japanese swordsman, that as he grew older he relied more on kizeme to defeat adversaries and, as a result, emerged victorious from challenges without taking the life of his opponent.

What Hand Do I Read - And Why ?This is the first tumbling block for some budding palmists, so let me give you some real begginning tips.

Through Thursday, January 20th, Borders is offering the Kobo Wireless eReader for $99 with coupon—that's $40 off its typical retail price of $139! Though the Kobo comes preloaded with 100 out-of-copyright classics, new users will nevertheless be interested in filling their new eReaders with their own books.

Some people are what is labeled a power user. I am one of these people. No matter how fast I get my system, or how quick of programs I have, it is never good enough. There is always at least one program that I could swap out for a more advanced, text-based counterpart that increases performance just a bit. Luckily, you don't have to use text-based programs without graphical user interfaces to get blazing fast speeds on Linux. There are tons of open source alternatives to the mainstream progra...

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

Installing the Software Download the PC/Mac client from Dropbox for your computer. When installing the software you will also be prompted to create an account. Please do so at this point. This account gives you free access to 2 gigabytes (gb) of cloud storage that can be accessed from any PC/Mac or Dropbox Enabled Device.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

For a professional photographer in the market for good business management software, Canon offers the Studio solutions package. This tutorial series outlines all the various functions and features of Studio Solutions, such as order processing, client files and managing your various photos for each product. Manage your professional photography business using Canon Studio Solutions - Part 1 of 8.

Follow these few step by step instructions to learn how to activate the junk mail filter in Entourage for Mac.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

If you know anything about search engine optimization and online marketing then you know that having as many links going into your site from good sources is very important. And if you’re not really experienced at building links or SEO in general then you might not know the best way to get good links for your site. So please read on and I’ll present to you what I feel is the best way to get good quality links for your site.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

With so many wireless iOS networking apps for the iPhone, iPad, and iPod touch available, there’s very little reason to connect any of these devices to iTunes, except to update the software. Besides, importing and exporting photos using iTunes has never been one of the best features of Apple‘s mobile device process. Let me introduce you to 5 useful apps for importing and exporting photos to and from your iOS device(s).

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

Warning Don't torrent things that you do not have the rights to torrent. Everything I torrent, I have a physical copy of, and just want a copy on my computer without causing wear-and-tear on my DVD drive's laser. Piracy is naughty.

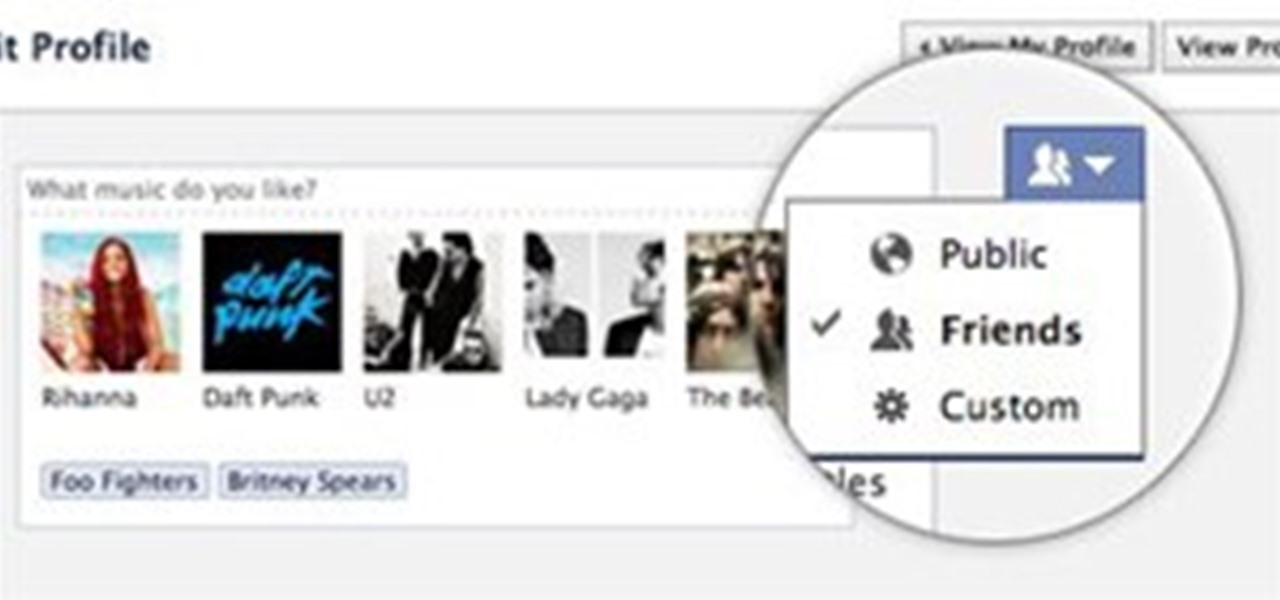
After the launch of Google+ and its ensuing attendant fanfare and rave reviews, Facebook seemed to undergo an identity crisis. On July 6th, Facebook failed to make waves with its "awesome" announcement - the new group chat and video chat features felt lame in comparison to the Google+ hangout and huddle features. Facebook also faced ongoing criticism for its perceived lack of privacy controls. Over on Quora, workers confirmed a lockdown of sorts at Facebook, for employees to work harder on fe...