Today, BitTorrent Inc. released the SDK for uTorrent Apps, which will allow software developers from around the world to create Apps for uTorrent, the popular bittorrent client. This video will show you how to download the SDK, install it on your computer, make an app, view that app in a browser, and then package the app and view it within uTorrent without compromising uTorrent's famous lightness. This is a big day for bittorrent fans around the world; download the SDK and start making uTorre...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...
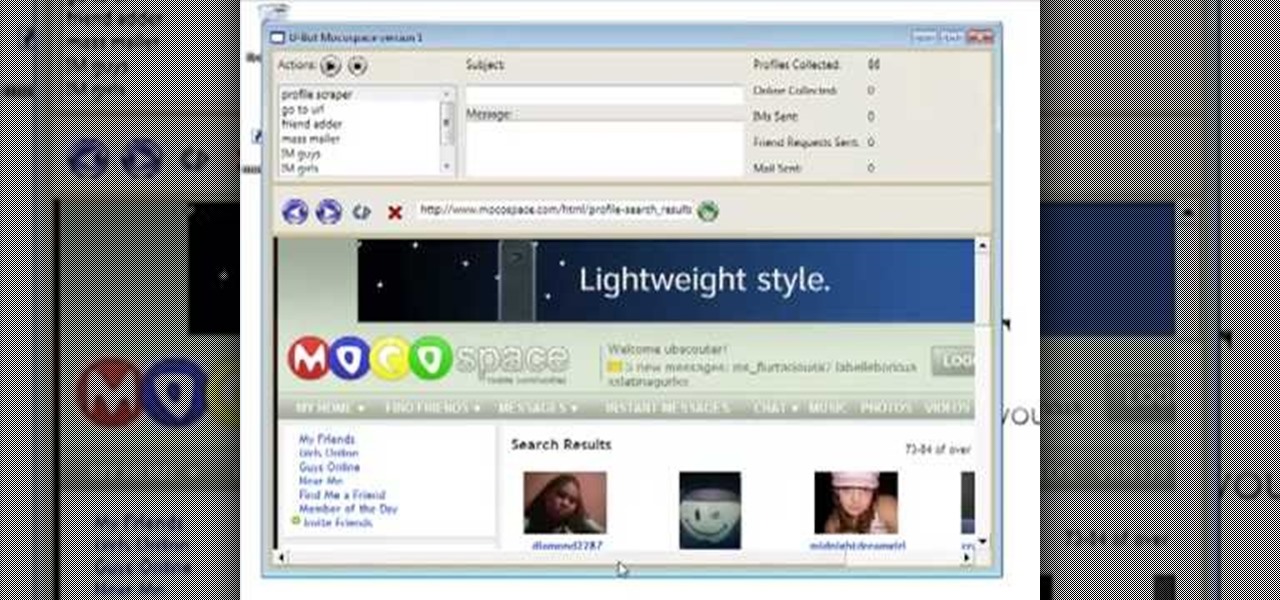
MocoSpace is a newly emerging social network, aimed and designed primarily for users of smartphones and other mobile devices. This tutorial shows you how to use the Ubot software to work with and monitor activity for your clients and customers on MocoSpace.
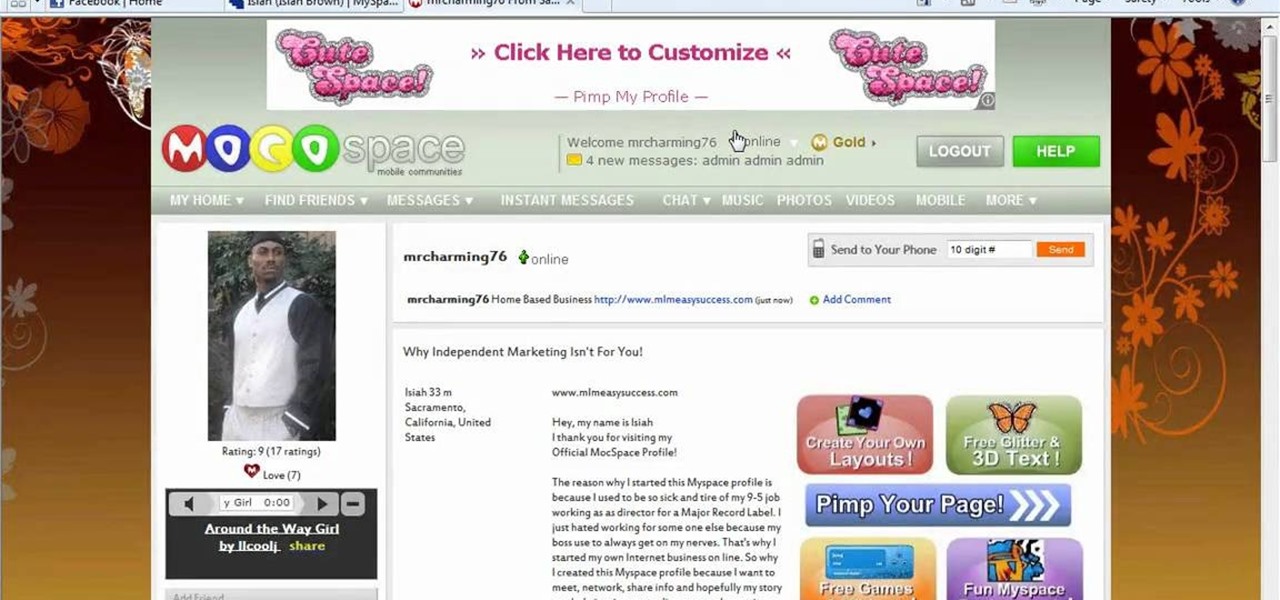
MocoSpace is a relatively young social networking site, primarily designed for people who have mobile phones or smartphones. Make sure you can stay connected to all your prospective customers and clients by using the advertising tools and opportunities that MocoSpace offers!

This clip demonstrates some rehabilitation exercises that you can use for clients who have suffered from an amputation. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

It's a notoriously preconceived notion that a man has to ask the woman out. But why can it not work both ways? It does, and it's the best way to bag the man of your dreams, especially if he's the shy type. If you're tired of waiting for your prince to appear with a Manolo Blahnik in your size, then stop waiting, and start taking control.

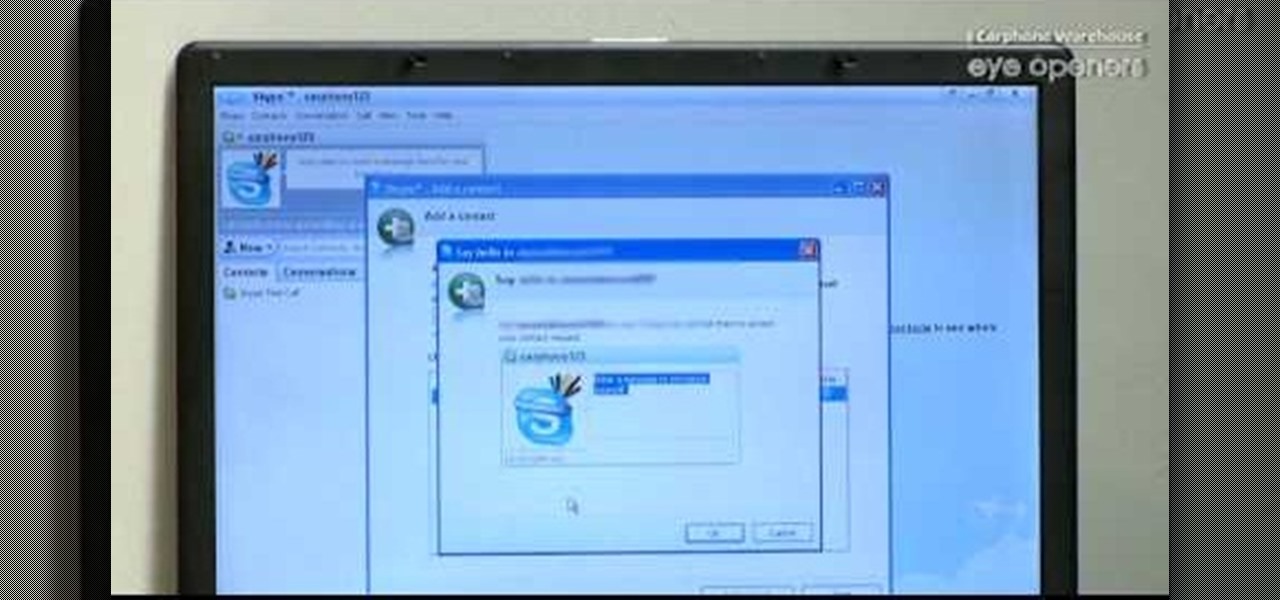
Cellular telephones? So 20th century! With this techy tutorial, you'll learn how to install Skype on your laptop and use it to make phone calls to your friends over the Internet – all without long distance rates! For more information, including step-by-step instructions on how to install the Skype VOIP (Voice Over IP) client on your own computer, watch this free video how-to!

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

If you're new to Ubuntu Linux and, for whatever reason, not so very keen on Ubuntu's default email client, Evolution, then you might like to try Mozilla Thunderbird. In this tutorial, you'll how learn how to go about setting up an email account in Thunderbird. Take a look.

If you're new to the Mac OS X operating system, one of the first things you might like to do is set up an email client. In this how-to, Gary Rosenzweig looks at how to set up the Apple Mail application to receive and send email from a standard ISP email account.

Watch this software tutorial video to learn how to better install Yahoo Messenger so it will behave how you want it to behave. Yahoo's IM Client can be difficult, but this how-to video offers tips that will help you install it so it won't be.

In this video, Massagenerd demonstrates various techniques that can be used to massage the leg and foot regions while the client is sitting on a chair. Watch and learn.

Want to know how to set PDFs up so that they can be digitally signed? In this Adobe acrobat tutorial you'll see how to set up a PDF to accept a digital signature. You all also see how to create your own digital signature for signing and a strategy to work with your clients so that you know who is signing those documents.

Parkinson's disease, a condition that can impair movement and coordination, affects over 10 million people worldwide. And with around 60,000 Americans being diagnosed every year, we're on track to see almost one million Parkinson's afflicted Americans by 2020.

Google caught a lot of flak for the Pixel 2 XL's POLED display issues, regardless of whether the problems were real or perceived. It's too late to contract another screen manufacturer at this point, but Google is doing the next-best thing: Fixing as many user complaints as possible with software updates.

Jay-Z's Tidal streaming service provides Hi-Fi music to a mainstream audience. Even better, Tidal can do this without blowing out your eardrums, because it's easy to enable volume normalization so that one track isn't louder than the next.

Many wonder how driverless cars will ever be able to navigate through any driving condition imaginable — but the point is self-taught machines, in theory, have the innate ability to adapt to chaotic and extreme driving conditions in ways far superior to what humans are capable of.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

Getting caught using your iPhone at school or work (when you're using it for personal reasons) can be a little bit embarrassing. Even worse, it can be detrimental to how you're perceived by your teacher or boss. But sometimes you just have to beat that next level of Candy Crush, view a risqué photo on Snapchat, or send an important WhatsApp message.

Each morning, we spend a significant portion of our time staring into the mirror. From choosing clothes and accessories to perfecting our hair, we try to make ourselves attractive. Yet catching others' attention doesn't have to rely on preening and primping. There's some truth to the maxim of beauty in confidence—all you need to make yourself more attractive is spray on your favorite scent.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

When exercising at a high intensity, you know to expect some level of pain. That can make it difficult to identify when your body gives you a warning sign of injury. If you pay close attention, however, you can tell the good hurt from the bad. I talked to Dr. Brian Parr again, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained which symptoms of exercise are normal and which are bad:

With developments from tech giants Apple and Samsung being shared throughout the interwebs, the term smartwatch has become increasingly popular over the last year. That being said, smartwatches have been around for a while.

Buying and drinking wine can be intimidating. There's so much to know, and so many ways to reveal your ignorance. If you're completely befuddled by wine and how to describe it, don't worry, you're not alone.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

If mainstream media has taught us anything, it's that being beautiful can get you ahead in life. The notion isn't necessarily correct, but it's what the general consensus accepts and it seems to hold quite a bit of weight (no pun intended) in the western world.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

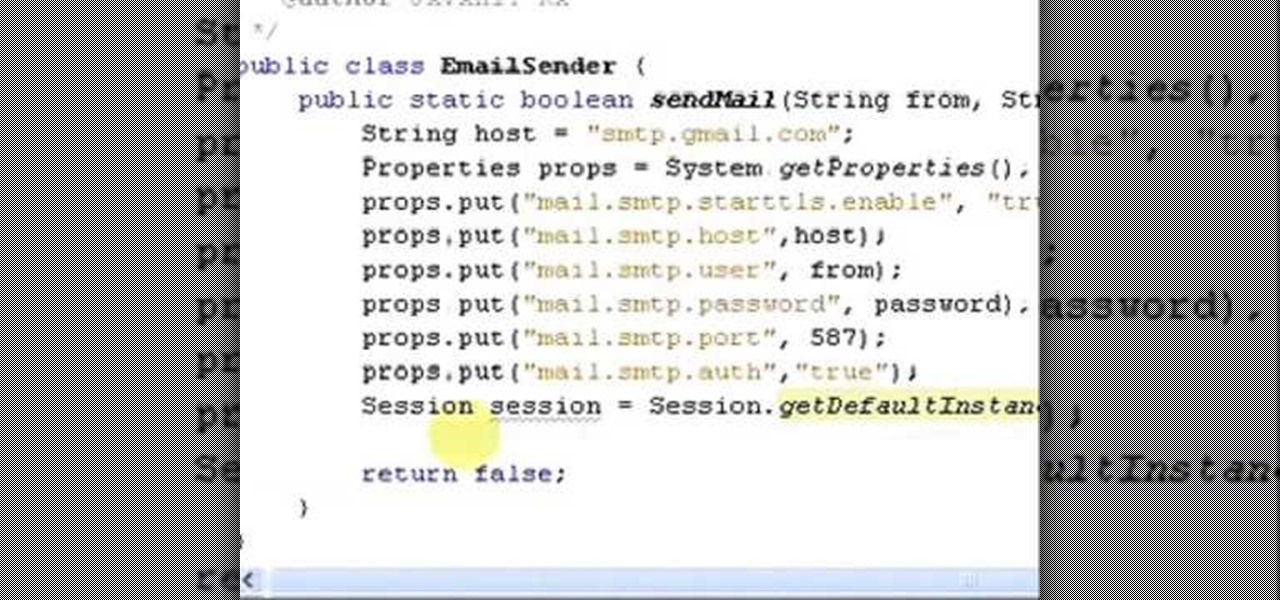
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

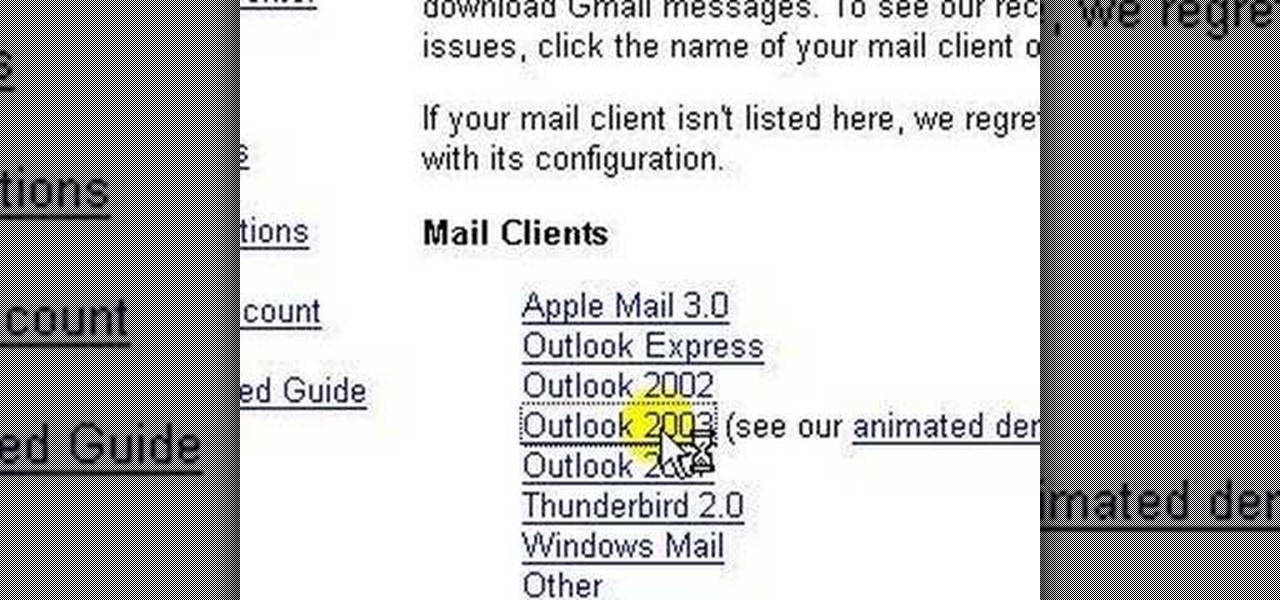
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

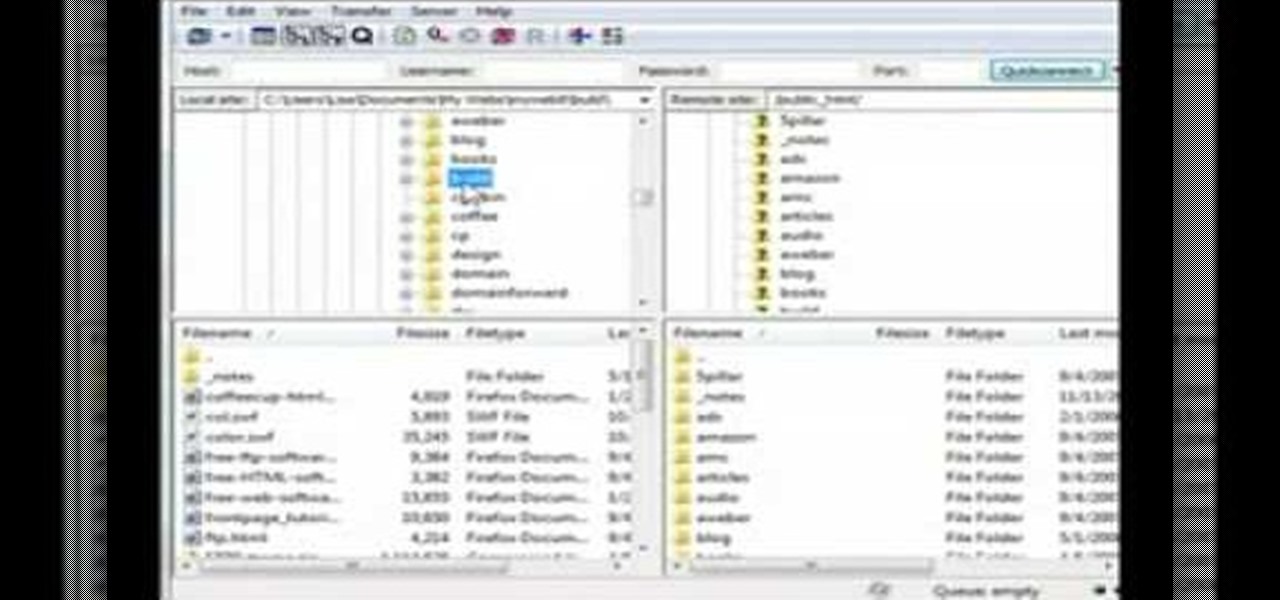
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.