Have you ever wondered how to make a brochure in Microsoft Word? Is your job requiring you to learn how to create a brochure in Microsoft Word? This tutorial will teach you step by step how to find templates online, transfer them into Word, and how to open the blank template in Word. This will enable you to create a successful brochure with a highly professional look to give to your clients. This step-by-step tutorial is guaranteed to tell you everything you need to know about creating brochu...

Are you a makeup artist with a messy makeup station? Many pro makeup artists are looking for the answer to the best set-up to achieve quick turn-over on brushes, specially when working with multiple clients or models. Koren from EnKoreMakeup shows us how he organizes his makeup brush station for hectic gigs with the mission to help!
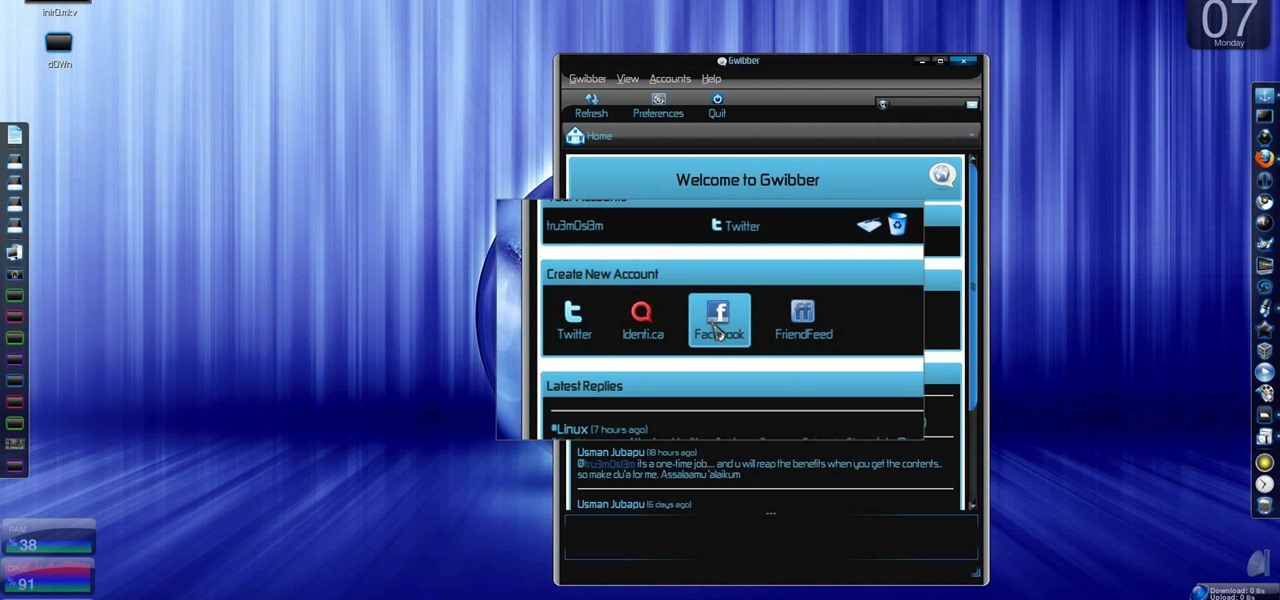
Twitter has consumed the world, so make sure you're up to date on your Tweets. One way to do that is with Gwibber 2.0 on Ubuntu Linux, the computer operating system that could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to retrieve unlimited tweets with Gwibber 2.0 on Ubuntu Linux.

Changing the hold music piped into your company phone is a prank some callers will appreciate—depending on what you replace it with.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to install a Wii homebrew hack using the Twilight Hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Going to school to be a nurse? Then one of the many techniques you will learn is how to irrigate a bladder. In this nursing how-to video our host demonstrates how to do a Nesbitt Young irrigation. This type of bladder irrigation demonstration is not a CBI, continuous bladder irrigation, it is an intermittent irrigation. However it does use a continuous infusion of sterile solution into the bladder, most often, using a three-way irrigation closed system with a triple-lumen catheter. Infrequent...

Massaging the foot benefits the entire body. It is very important to know the proper massage technique and have the right equipment. Learn the art of giving massage in this health how-to video.

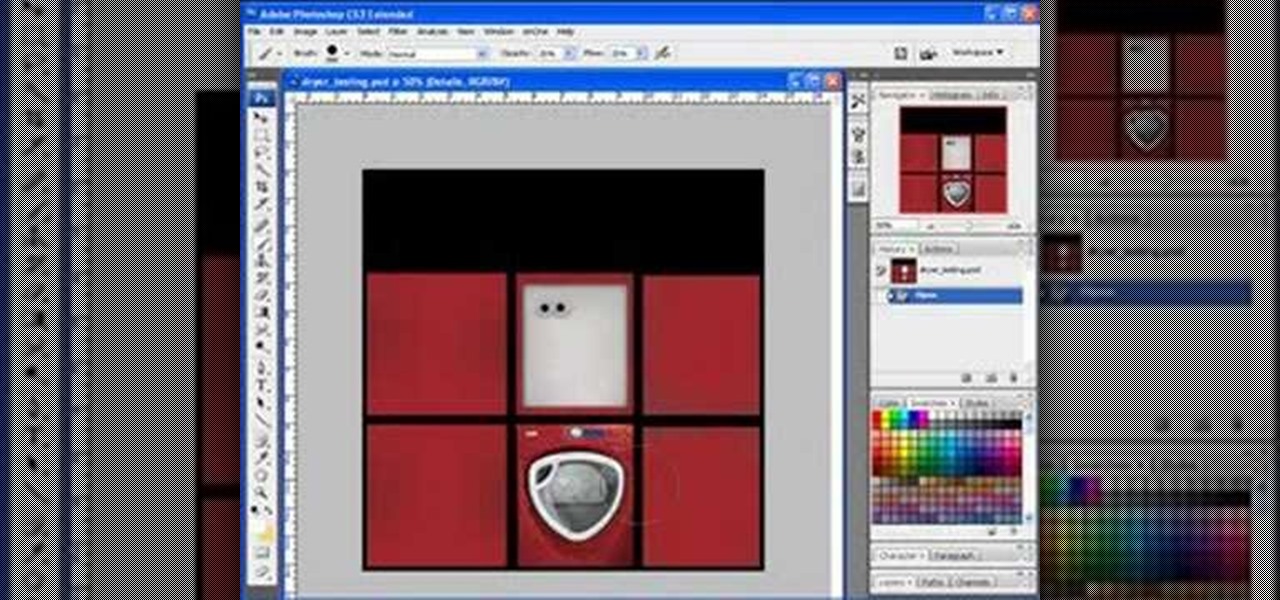
The third dimension has finally arrived to internet browsing! Be sure to catch the wave of innovation with this series of tutorials. Initially, we'll be examining the importance of texturing basic 3D objects. Watch as the almost magical effects of texturing in 3ds Max transform a simple cube into a trendy clothes dryer. Polygons are saved, browsing is made speedier, and clients are bound to be happy. Next stop, bring it into Papervision3D! If you wish to learn about using 3D elements on the i...

The clavicle is a V shaped bone that makes up the shoulder area. Massaging the clavicle, or collar bone, relieves tension in clients. Learn the art of giving massage in this diet and health how to video.

Find yourself going to the same websites or blogs every morning? In this video tutorial, you'll learn how to open them all using a single click. First, view all of your bookmarks. Then, create a new bookmark folder in your bookmarks bar. Add the desired books and check the autoclick box. Whenever you click on the bookmark folder in your bookmarks toolbar, your Safari client will launch all of the websites in separate tabs. For more, watch this OS X video tutorial from Apple.

The Seal is an original pilates exercise that increases core strength and balance while delivering a fun exercise. The goal of clapping the feet like a seal claps its flippers is to stabilize the torso against the movement of the legs and increase the time your suspended on each side of the movement by just a second or two to develop ab strength and balance. The Seal exercise is probably our favorite exercise as it always makes clients smile. Watch this fitness how to video and you will be st...

This pilates how-to video illustrates the Obliques Roll Back exercise. This is a challenging rotational pilates exercise for athletes and advanced clients.

Zune is a digital media players and services sold by Microsoft. It includes portable media players, client software, and the Zune Marketplace Internet music and video store. If you hate the Apple iPods, you probably have one of these MP3 players.

In this video tutorial, Chris Pels will show how to include JavaScript to an ASP.NET page for use on the client page to provide a richer and more robust user experience. First, see how to include JavaScript directly within an ASP.NET page and reference the script from within HTML page elements. Next, see how to abstract the JavaScript to an external JavaScript file which offers the advantage of being cached by the browser and can be used by multiple pages. Lastly, learn how to add JavaScript ...

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

This clip goes over a Pilates arc modification on the Reformer for clients with kyphotic spines. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, give this free exer...

Being in sales is hard work. After all, the only thing more painful than trying to sell a hand cream or knife set to a stubborn client is perhaps pulling out teeth - without novacaine. And God knows how many times we've hung up on telemarketers because, well, they're a little too persistant.

This 4 part video series is a gift from me to all the other singers out there who have shown me such great love and support. It contains a full vocal warmup that will improve tone, expand range, and increase control. This is pretty much the kind of warmup that I might do with a private client, but it's for you guys - free of charge.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

If you're looking for a new Reddit client on your iPhone, look no further than Apollo. Launched with iOS in mind, Apollo is a free app that offers an exceptional Reddit experience, but some of its excellent features — as well as some necessary ones — are hidden behind its "Pro" paywall. Are these extras worth your money?

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Several technologies seek to change the way we perceive our reality, whether that involves entering a virtual world, augmenting an existing one in a realistic and interactive way, or somewhere in-between.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

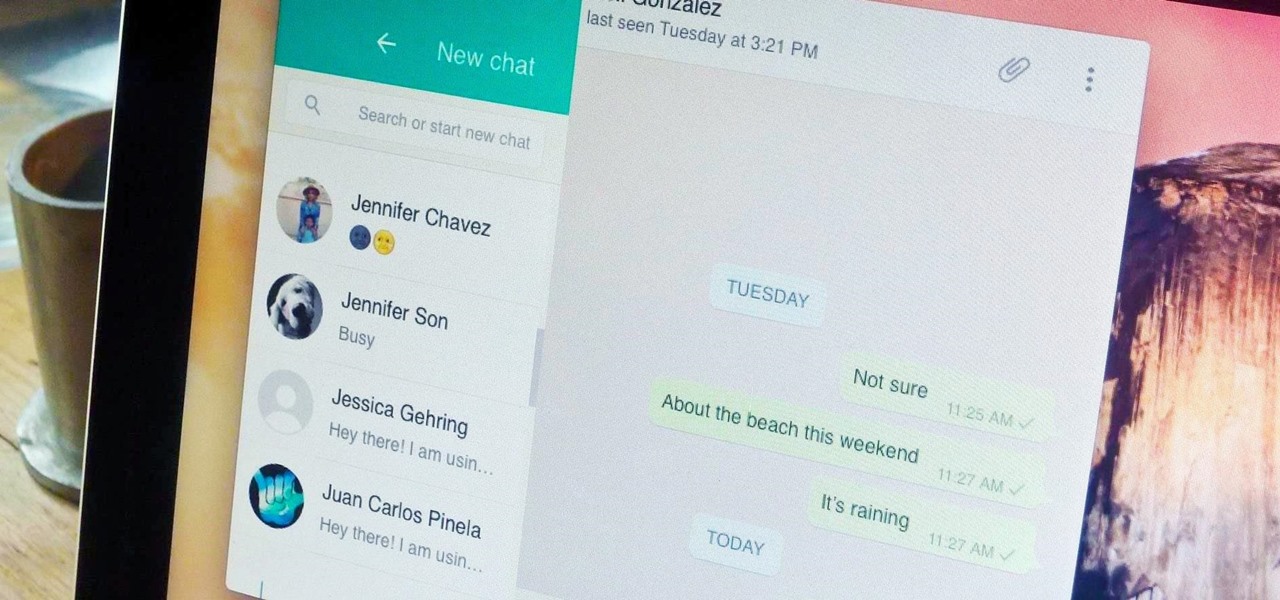
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Video: . How to Stop Shrinkage with Shea Butter & the Banding Method!

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

The Galaxy S9 is an audio powerhouse. It has the first set of stereo speakers on a Samsung flagship, and it even comes standard with a set of AKG-tuned earbuds that would normally cost $99. But if you want to further enhance your audio experience, there's a feature that will customize audio output to your own specific hearing.

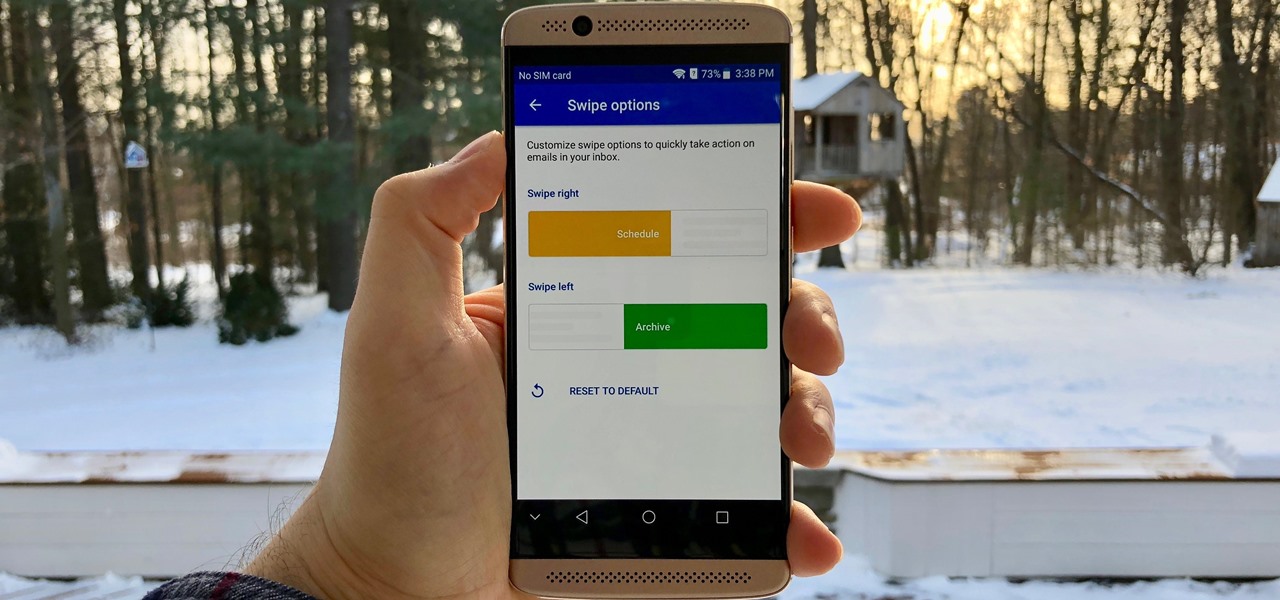
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.