"Ain't No Sunshine" might just be a classic song to you, but for me and my Samsung Galaxy S3, it means so much more. For the most part, my GS3 does a decent job at automatically adjusting the brightness of the screen when I'm in normal lighting, but when I'm in little or no lighting, or there's just way to much, I usually have to switch over to manual to get the right balance. Luckily, we're not stuck with Samsung's built-in auto brightness feature. There are some really good third-party solu...

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

If you have an iPhone, you probably already updated to iOS 6.1, which was released earlier this week. The new release came with some very subtle updates, including LTE support for more carriers, the ability to purchase movie tickets from Fandango via Siri, some security patches, and more.

Streaming video has definitely changed how we watch movies and television shows, but with the constantly growing number of services out there, it can be hard to keep track of who's got what. Who's got Disney now? Starz? Netflix? Who knows. And when you add sites that let you rent or purchase titles, you could spend all evening trying to find something to watch. Here to simplify the process is a service called Can I Stream It?, which lets you search for your favorite movies and TV shows to fin...

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

Duplicating, or "duping" items has been around for as long as PC RPG's, and allows you to use glitches to duplicate your items in the game. This video will teach you how to use the stunningly easy-to-use dup glitch in Dragon Age 2 to duplicate as many of any item you have 2 or more of your want, up to 999. This essentially gives you unlimited money and items.

In this video, we learn how to prepare yourself for a major disaster. If you haven't planned ahead for storing water, you are going to be in big trouble. Your first option is to go purchase liters of water from the grocery store. The recommended quantity to store is 1 gallon per person per day. If you don't want to spend money at the store, you just need to fill up empty bottles with water from the tap and store these after cleaning. You can also fill the water in a large jug, just make sure ...

The Tree of Life Rejuvenation Center has created this instructional video on how to make a diabetic friendly millet breakfast cereal. You will need almonds, cinnamon, shredded coconut, and hemp seed. You can make your own milk out of the almonds, coconut, or hemp or you can purchase almond milk. Place one cup of millet of two cups of water in a pot and heat it up on the stove. It will take about 15 minutes for the millet to cook. To make the almond milk, soak the almonds for 24 hours prior. P...

This video speaks to everyone who has ever bought anything online, or in fact, anyone who has ever bought anything period. How do you know what you're getting is genuine? Is it a fake product? Is it stolen goods? Is it impure?

Make spring rolls like a professional! Use pre-packaged purchased wrappers. Have some egg yolk ready. Apply some egg yolk on the edges of the wrapper, so that it can act like glue. Paint it on all 4 edges. You can use a brush for that. The filling is pre-prepared. It is a mixture of vegetables , cooked pork, and cooked shrimp. We will then add ginger and soy sauce to the filling. Take a small amount of filling, so that the spring rolls are thin, because that is how they are meant to be. Fold ...

This is chemistry at its best! Europium is the chemical element (Eu) which was named after Europe. Dysprosium (Dy) is a rare earth element of a metallic silver luster. Watch this science video tutorial from Nurd Rage on how to make europium and dysprosium nitrate salts with Dr. Lithium.

This automotive video series covers "What to Look Out for" before buying a Volkswagen bug. The first video shows you the first few sections that you should inspect before purchasing a classic VW.

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

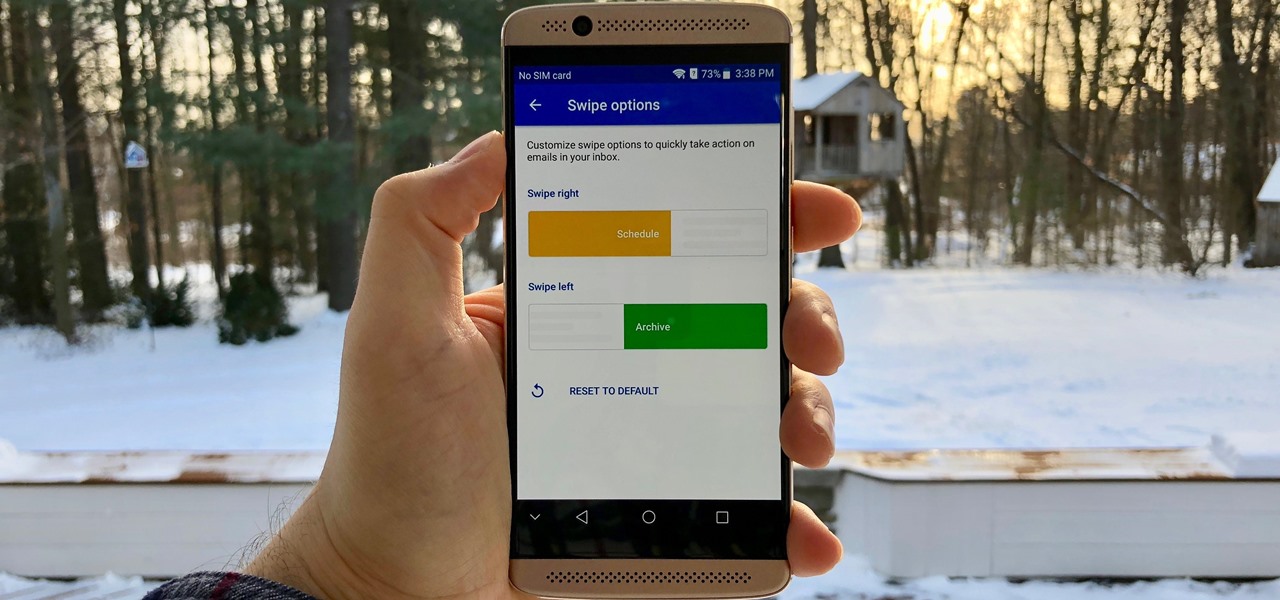
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

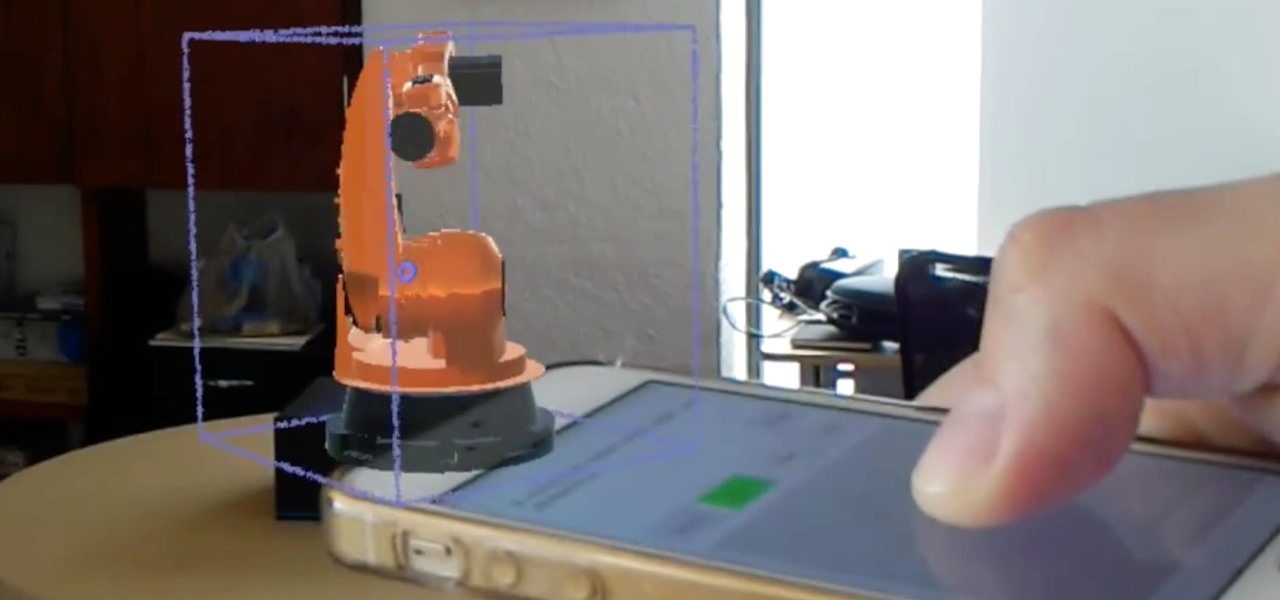
We've highlighted the projects of Wavelength Studios a few times over recent months for their work in the augmented and mixed reality space. Since receiving their HoloLens headsets, they've been hard at work on both development community projects as well as efforts for clients. This brings us to their latest work—a way to control holograms on the HoloLens with our pocket-based modern miracles, also know as smartphones.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you turn your phone into a super-convenient wireless webcam and save some cash.

Through Thursday, January 19th, Borders is offering the Kobo Wireless eReader for $99 with coupon—that's $40 off its typical retail price of $139! Though the Kobo Wireless eReader comes preloaded with 100 out-of-copyright classics, new users will nevertheless be interested in filling their new eReaders with their own books.

In this tutorial, we learn how to dye your hair at home for blondes. First, purchase a couple boxes of hair dye that are the right colors for your hair. After you do this, take all of the products out of the boxes. Now, pour the small bottle into the large container and put the rubber gloves on. You don't need to use both containers, you can just use one if your hair isn't that thick. Snip the top off the container, then start to shake up the container until it's well mixed together. Now, sta...

Scrabble isn't just for playing Scrabble anymore— there's a whole world of uses for the game and its pieces. One particular use is in jewelry— those Scrabble letter tiles are the perfect size for creating DIY pendants!

Wilton Cake Decorating demonstrates how to make and decorate a Making Her Entrance Doll Cake. To make the cream cheese pound cake, cream together some cream cheese, butter and sugar, then add eggs and vanilla. In another bowl mix together the flour, baking powder and salt. Add the dry ingredients into the wet ingredients alternately with the milk, and blend well.

John White, a Doña Ana County Extension Agent, highlights a new section on the show - a monthly checklist for the garden. This time, he talks about what to do in your garden in the month of February. The checklist includes planting dormant plants, pruning with a purpose and applying herbicides and pesticides. He shows us various types of dormant plants that can be purchased from nurseries in February for planting such as potted, bare-root or root-balled plants wrapped in burlap. As for prunin...