In a move that seemingly surprised everyone—including Samsung—Korean carriers have released the Galaxy S5 a full two weeks early to avoid being caught up in an about-to-be-imposed ban.

Been hacked once? Twice? Maybe more? You thought abc123 was the only password that is both 6 characters wide and easy to remember? I have some suggestions in store for you. Just read on...

I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends.

Call Your State's Nurse Aide Registries for School Inquiries

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...
1.) If you do not know something, keep our mouth shut.* No-one, I repeat no-one, is interested in your uneducated guesses about why something is the way it is, or why someone did something a certain way. At best, you will trick them into temporarily thinking you know what you’re talking about. At worst, you will convince them that you are speaking the truth and they will perpetuate your bullsh*t to others. Do not contribute to making the world a more foolish place just because you had to say ...

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Skyrim is a time consuming game. I know I'm not alone in saying I constantly find myself looking for more time in the day. There is never enough time to read the books I want to read, or learn what I want to learn, or play the games that I want to play.

This is the Windows OS counterpart to my tutorial on how to burn the new XDG3 formatted games on Xbox 360. Microsoft invented a new disc format system to trump piracy, it's called XDG3. XDG3's standard is to burn a whole extra gigabyte of data to the disc, to allow more content, but more importantly for stopping piracy. This extra gigabyte of data makes it impossible to burn or rip a game the traditional way. So how on earth can we burn our fully-legal back-ups that we should rightfully be ab...

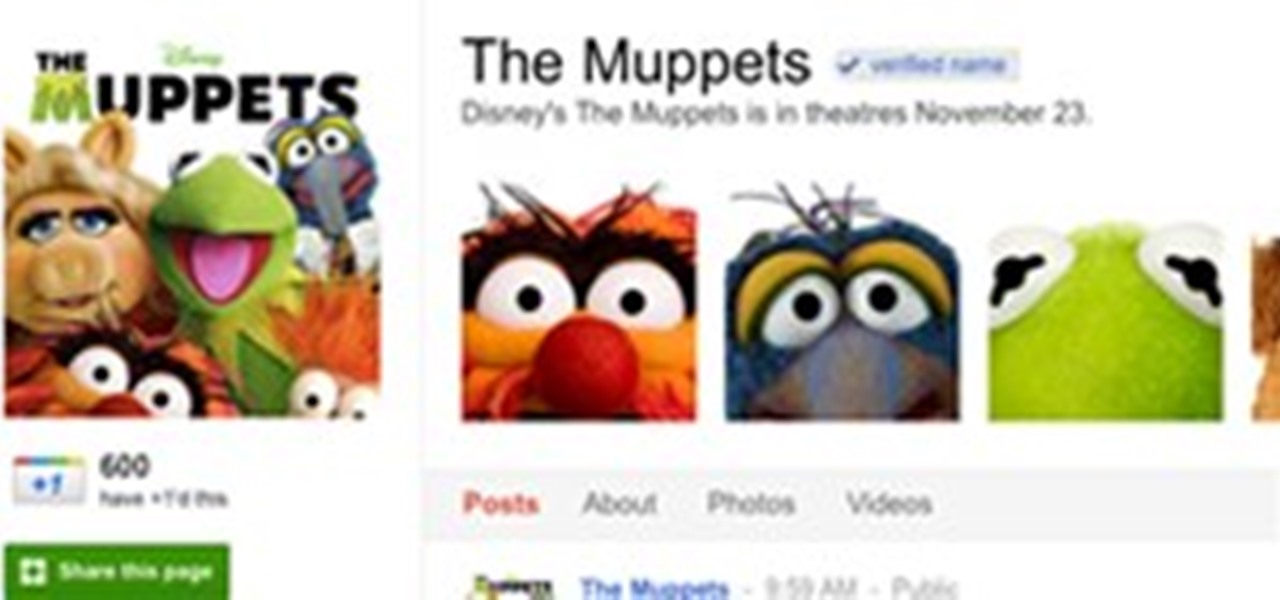
Many companies were disappointed when Google+ rolled out and banned the creation of accounts specifically for businesses and brands. Fortunately, today, Google began rolling out Google+ pages, for them to start connecting with customers and followers. For an example of what a Google+ Page looks like, check out the one for the +The Muppets:

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

Mozilla is scheduled to release their updated Firefox browser on Tuesday, bringing the popular web browser up to version 6. Lately, the Mozilla team has been releasing newer versions of Firefox without a slew of new features, focusing on fixing bugs and getting the improved product out as quickly as possible, in order to compete more rapidly with other browsers like Google Chrome.

Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they aren't so lucky. According to Google+'s community standards, users must "use the name your friends, family, or co-workers usually call you". The purpose of this rule is ostensibly to discourage spammers and people from set...

ARGs have taken the concept of video games to some odd and wonderful real-world places. Socks, Inc. might not be the first ARG, and LittleBigPlanet might have defined the sock-puppet-based game archetype, but it is the first game to combine ARG and sock puppet elements into one package.

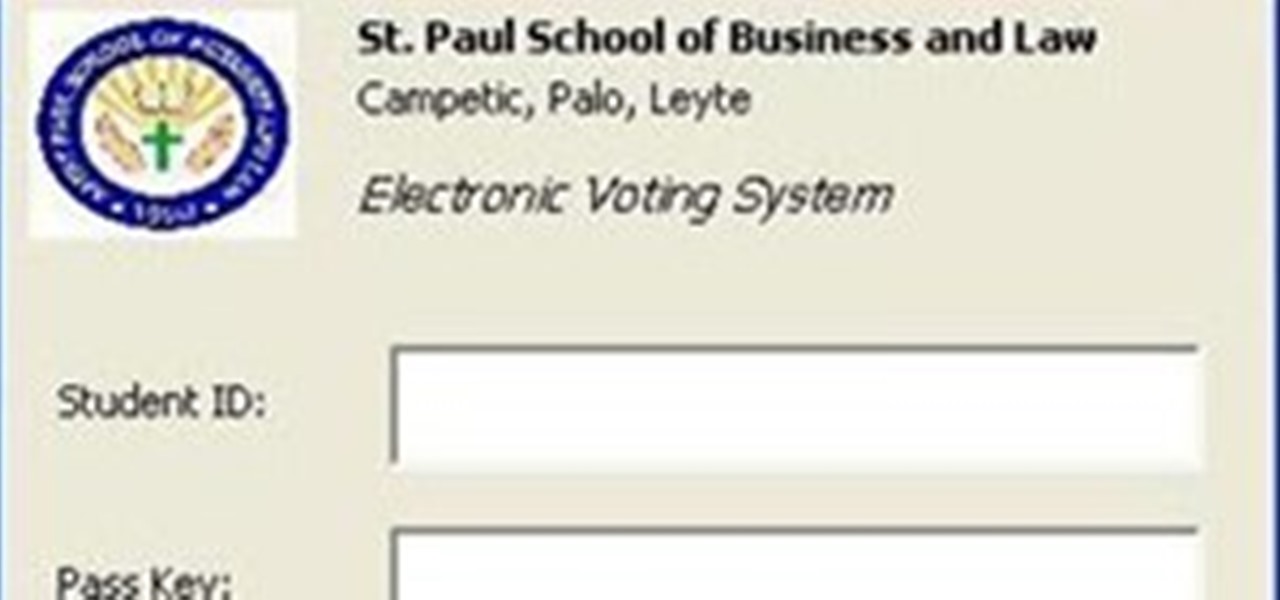
Tomorrow is another day of election (PSG). I have to wake up early to set up the computers on both computer rooms. The election process is computerized, making the counting of votes the responsibility of the computer. What makes this year's election special is that for the first time in 3 years (correct me if I'm wrong), there are competing parties. The result is something to look forward to especially for me who contributed in the creation of the system.

One of the most important marketing tools we should always be developing to help reinforce our brand is our references. Just like many companies use their client list and client references to build credibility and confidence for their products and services, we should also leverage our references to build credibility and confidence in our capabilities and brand. Sometimes reference checks are just a formality, but in most cases potential employers (i.e., potential clients) use reference checks...

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

One of the coolest things about Twitter is the fact that you can get direct access to some of your favorite celebrities, and have one-on-one conversations with them in less than 140 characters. With Google+, you can have the same advantage, but you don't need to feel constricted by the 140 character limit. Although Google+ has been weeding out fake accounts, they do not currently have a system for celebrities to verify whether their accounts are legitimate or not.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

Put simply, SEO = more organic traffic. And more traffic is always good for a web page / website (unless of course, you are an underground drug-dealer selling drugs worldwide via a spooky website whose URLs are as search engine unfriendly as possible, so that no one accidentally discovers your page and informs the police, sending to heaven both an exciting career opportunity and the likely Al Capone's successor).

Moving a 2000 pound safe isn't easy... I was working as manager for a construction company that was performing an up fit on a century old building in downtown Concord, N.C. The owners wanted us to move a two thousand pound (that's a ton!) safe up to the second story so that it could be displayed in their new office. The safe was located between the first and second floors in a small office that was used for accounting purposes in the old days when said building had been a hardware store.

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

On Google+, one of the very first creative projects using the popular hangout feature revolved around cooking. Foodies +Lee Allison and +Eric McKee decided to start their own "G+ Cooking School", which has now expanded into the Social Skillet. Although neither have formal training, they're both quite accomplished cooks and skilled instructors. Using hangouts, they've taught their students how to create dishes like margherita pizzas and chicken marsala.

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for short, is one of them. The idea of MTurk is to hook up programmers with people that do tasks that computers can not, these tasks are called HITs (Human Intelligence Task). These tasks include article creation, creative ...

Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough.

After years of false rumors and abandoned hopes, the day has finally come. Verizon Wireless is finally getting the Apple iPhone!

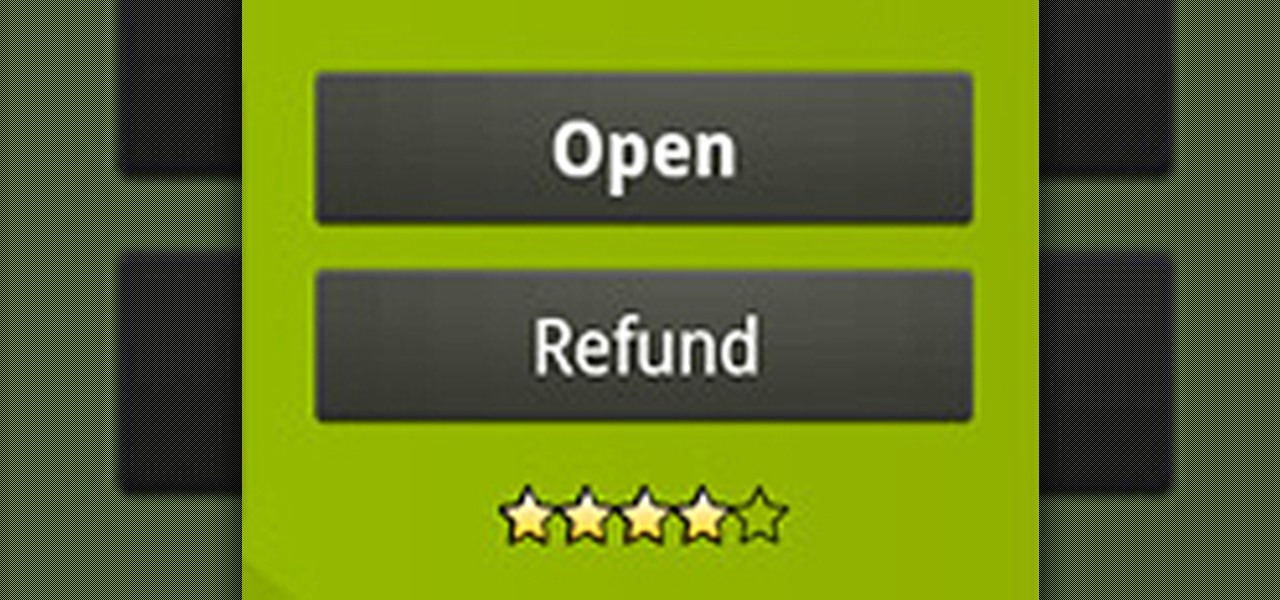
Nowadays, there's a mobile app for just about everything—but that doesn't mean it should be on your smartphone. Not diggin' what SPB Shell 3D did to your home screen? Accidentally purchased Angry Sperms instead of Angry Birds? Want to try out the upcoming Smuggle Truck without committing? You may have to fork out the funds for those paid apps, but by no means should you be willing to just throw your money away. This guide will tell you how to get it back.

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be in total blackout in protest against the proposed legislation in the United States. And that's not all. MoveOn, Reddit, BoingBoing, Mozilla, WordPress, TwitPic and other popular websites are down today in protest.