With over 8 million active users, CyanogenMod is definitely the most popular ROM for Android devices, which explains why venture capitalists invested $7 million last month for future development.

While Siri came up on the scene with hardly any competition back in 2011, Google Now has not only caught up to Apple's intelligent personal assistant, but also excelled in certain areas—with its ability to quickly answer questions, give recommendation, and even deliver information that it predicts a user will want.

The high limit thermostat can be found in gas and electric dryers and serves as a safety feature that helps to prevent the dryer from becoming too hot when it’s running. The thermostat is designed to shut off power to the dryer’s heater when the dryer vent is blocked or clogged. The high limit thermostat on your dryer is something that does need to be replaced from time to time. Fortunately, it is a job that you can do on your own with basic tools.

Ringing and vibrating alerts on your smartphone can be a bit distracting when you're at work or school, but silent alerts can be a little too subtle if you want to know when you get a notification. Even the tiny LED alerts can be easily missed. So, is there's something in-between loud and almost-not-there alerts? In today's softModder tutorial, I'm going to show you how to get flash alerts on your Samsung Galaxy Note 2 and other Android devices. That way, whenever you receive a call or text m...

Probably the most favorite custom ROM among softModders is CyanogenMod, a theme-friendly take on stock Android that not only makes it easier to customize your device, but also increases performance using a variety of system tweaks and enhancements.

While there's still no set date, Jelly Bean 4.3 is rumored to be released on the Samsung Galaxy S4 and other TouchWiz devices within the next couple of weeks (or months), presumably sometime after the upcoming Samsung Unpacked event.

The new Moto X is still a couple of weeks from being released here in the United States, but that doesn't mean we can't play around with a few of its cool features.

The new Android 4.3 Jelly Bean has been out for a while already, and most of you already have it installed on your Nexus 7 tablets. Many of you softModders have also probably rooted your tablet so you can take advantage of some of the more popular root-only softMods, like speeding up performance, installing WhatsApp, increasing internet speeds, getting Beats Audio, etc.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

There are a lot of programs which allow opening archives. Alas, most of them are rather complicated to use. The process of opening of the archive often takes much time. Hopefully, there are some applications which are simpler to use for regular uers.

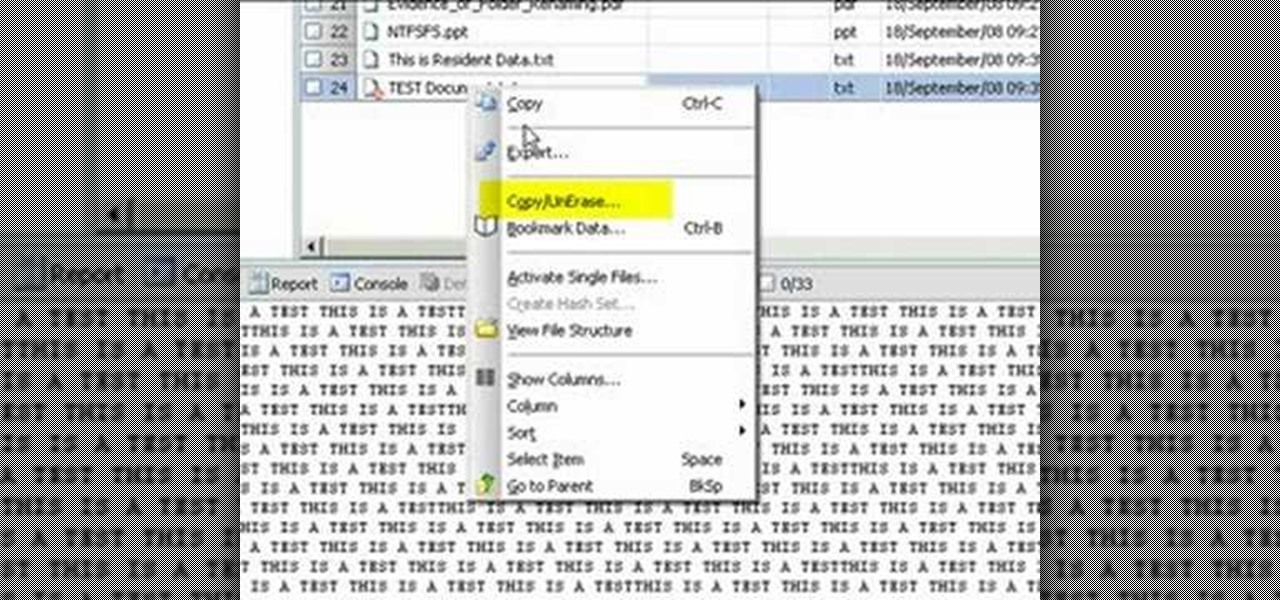
Use Encase to open the drive after the document has been deleted. The deleted file will show up in the program and will have a red circle with a line through it showing that it was previously deleted. The window on the bottom of the screen will show the document context so you can verify that it is the correct one. Right click on the file and click 'copy/unerase' to restore the document. Down in the bottom right hand corner you will see the progression of the copying to the chosen file destin...

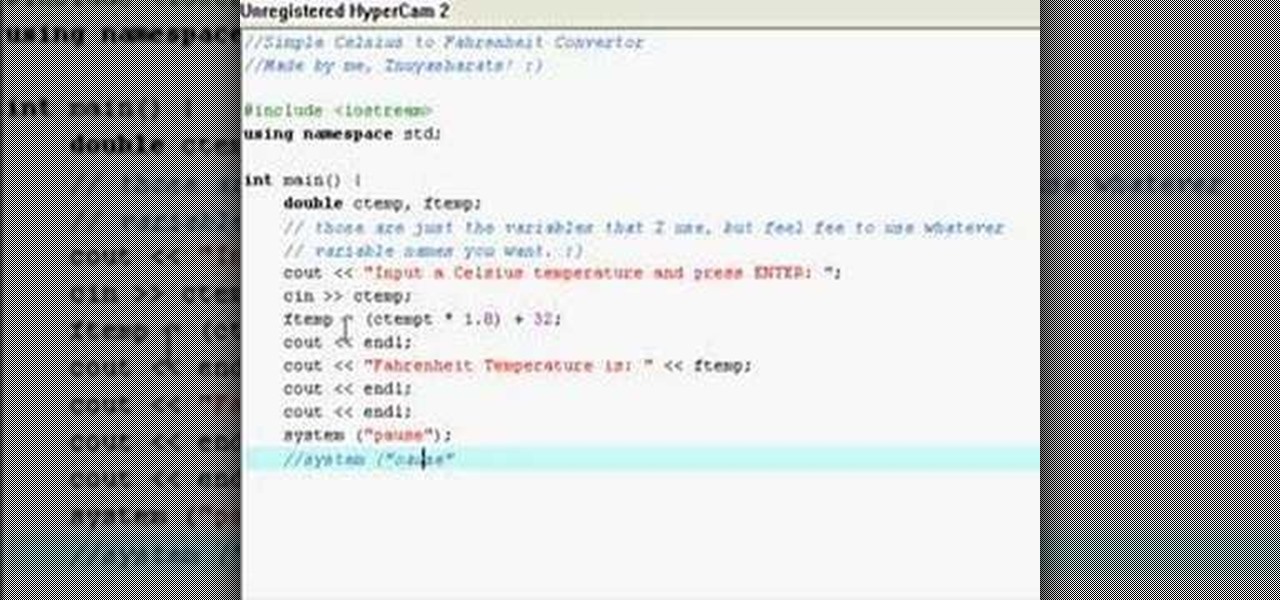
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

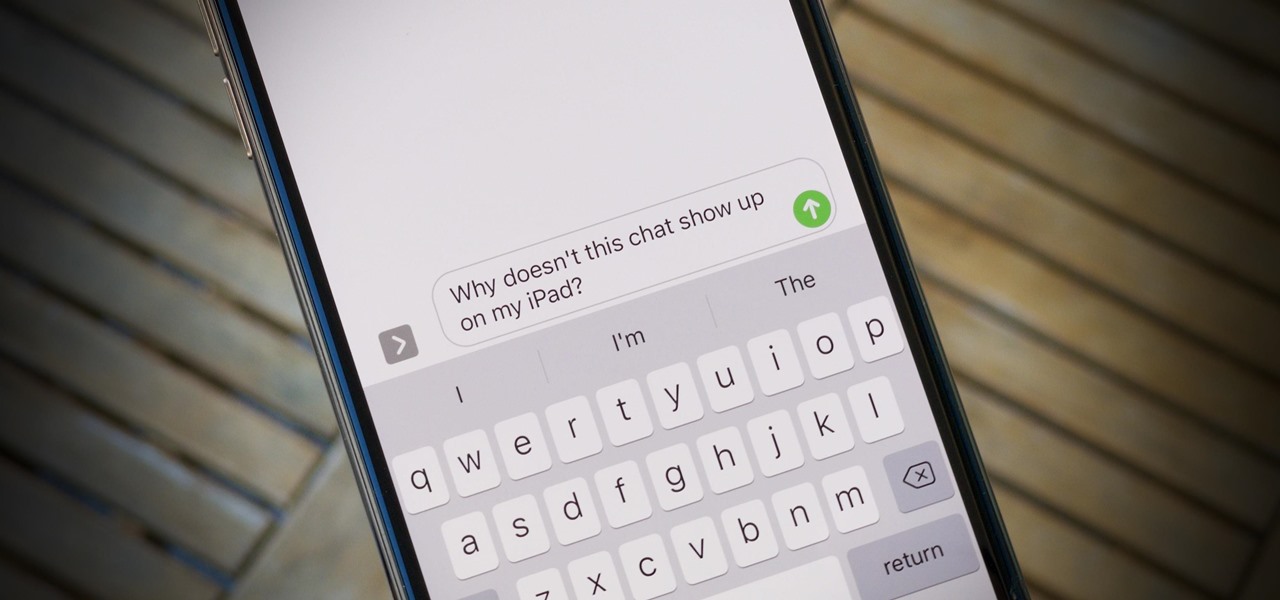
One of the best reasons to enter Apple's ecosystem is iMessage, where you can communicate more securely with other Apple users and send and receive chats across all of your connected iPhone, iPad, iPod touch, and Mac devices. While those blue bubble conversations sync across devices, the green bubbles — SMS and MMS texts — remain on your iPhone alone unless you change a setting manually.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can provide you with a ton of new features you didn't know you were missing.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

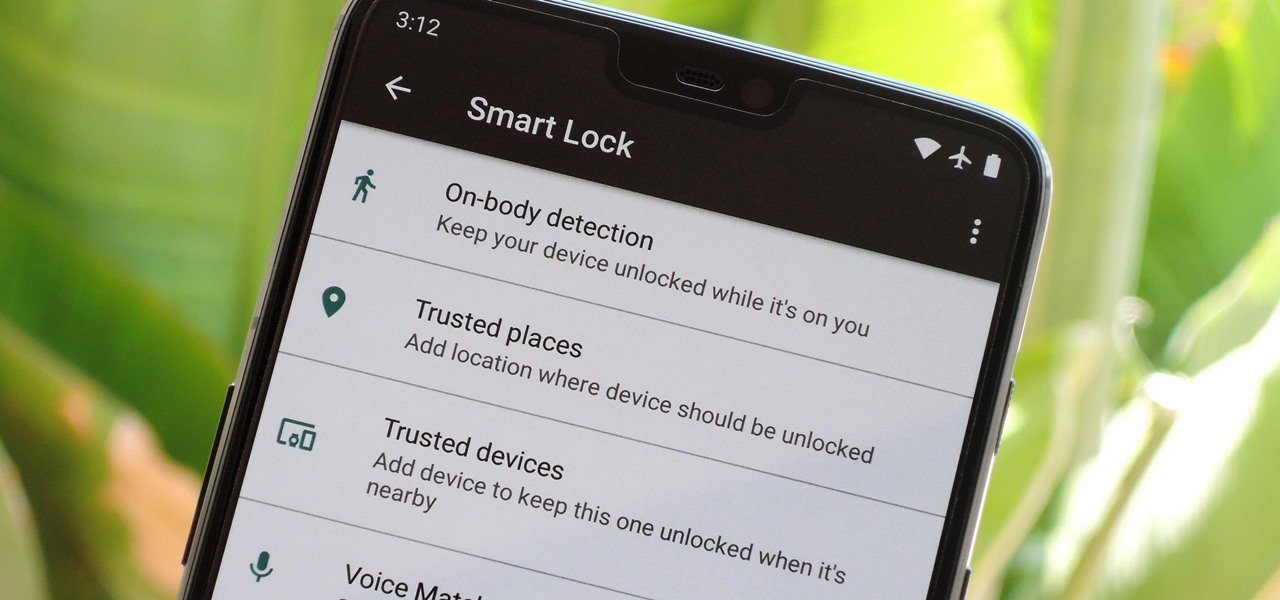
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.