Here is the final part in Null Byte's series on mastering the skills in The Elder Scrolls V: Skyrim. We have already covered the slick and brutal methods to raise our Spellcasting and Combative skills. Skyrim's intelligent new leveling system has trumped the former methods of spamming repeated moves to raise levels quickly. Rather than casting a spell, or jumping up and down constantly, the new system requires that we use our skills in practice to get experience for them. This causes leveling...

What if your fridge knew your food and expiration dates? What if your fridge could tell you which ingredients are missing and where you can get them the cheapest?
In a recent announcement, Hewlett-Packard announced that they're considering spinning off their PC hardware business, but even more recent was the decision to completely off webOS devices. Though they aren't eradicating the once popular Palm platform altogether, they are liquidating all of their HP branded smartphones and tablets in a fire sale, including the Pixi, Pre and Veer phones and TouchPad tablet, which is less than two months old.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.
Johnny Knoxville and the Jackass boys have finally returned from their whirlwind world tour promoting Jackass 3D. Along with their return comes the long-awaited Honorable Mentions for the Jackass 3D Prank Contest. So, straight from the source, a note from Knoxville:

It’s a game, it involves numbers, it’s fun, it’s KenKen! Understanding the goals and rules of this fun, numbers puzzle will give you the skills you need to win. Have fun working your brain and passing the time with KenKen.

This series will teach you the basics of sewing machine operation. Our expert will identify the parts of the sewing machine for you, as well as explain some of the general functions and abilities of the machine. Tips include how to thread a sewing machine, winding and installing the bobbin, selecting the proper foot, and turning the fabric.

A miter saw used to refer either to a large unpowered backsaw or metal frame saw with replaceable blades suspended on rollers in a metal guide that allowed making accurate crosscuts and miter cuts. These types of miter saws are still sold, the Nobex brand being notable. Today, they are generally used in picture framing but have largely been displaced by the power tool in carpentry and joinery operations.

It's currently 2011, but when you fire up your game console, put your hands on the controller and play the new Dead Space 2 video game, you're warped into the future— into the year 2511— just 3 years after the events that took place in the first Dead Space. And it's sure to be a beautiful, frightening, futuristic experience.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

The iPhone 15, iPhone 15 Plus, iPhone 15 Pro, and iPhone 15 Pro Max are Apple's most powerful iPhones to date with features like USB-C connectivity, improved camera capabilities, and faster CPUs. But no matter how impressive these phones are, they can still freeze, become unresponsive, or get stuck when powering on — and a force restart is how you get things working again.

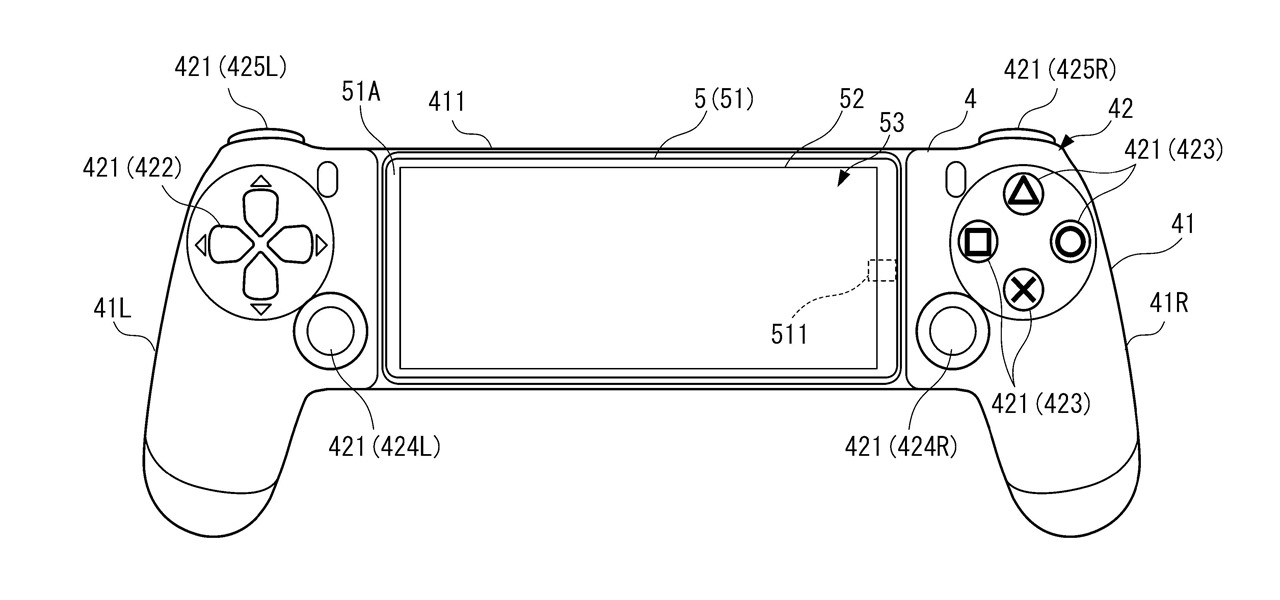
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

If it's always been your dream to work for a large company as an app developer, there's never been a better time to consider the field than right now — especially with companies like Apple staffing up in this department. It feels like everywhere you turn, companies are starting to move in this forward-thinking direction.

The year 2021 is already promising to yield a number of major shifts in the augmented reality landscape, and Snap is signaling that it has every intention of being an aggressive part of that narrative.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try.

Every state has begun reopening in some capacity. While there are important steps for everyone to get back to work and begin socializing, precautions will be in place for some time, especially with an expected second wave coming this fall. The virus is not over.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars.

Chances are, your favorite websites run on ads. That means the sites rely on those ads to fund their operations. Without ads, your laughs, news, and guides don't happen. That's why it's helpful to disable content blockers (often called whitelisting) for sites you support. In the past, it wasn't possible directly in Safari, but in-app whitelisting becomes a reality with iOS 13.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

As Magic Leap prepares to ship the Magic Leap One later this year, the company is putting its focus on mentoring developers and creators to build a content ecosystem for the spatial computing platform.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.

If you've running iOS 11.1 through iOS 11.1.2, whether you have an iPhone X or an iPhone 5S, you'll notice that Apple's Calculator app can't keep up with your calculations. That's a because a bug has seriously slowed it down so that operation buttons won't always trigger when you press them. Luckily, there's something you can do about it.