
How To: Password Protect Google Chrome with Rohos Mini Drive
Get Google Chrome Download and install Google Chrome.


Get Google Chrome Download and install Google Chrome.

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song

In these music studio recording and production videos, learn how to use a 4-track reel to reel tape recorder to capture your vocals, guitar parts, drums, record songs, or even make a demo CD. Our expert will walk you through the operation of a fairly simple reel to reel machine in several steps, including the basic and advanced functions, rear components, using mics and connecting to other mixing boards, recording on four different tracks, mixdown, bouncing tracks, and final tips for masterin...

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. This series is a grea...

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert, Bill Macpherson, will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. Thi...

In this video clip series, our expert will demonstrate the ways in which you prepare a welding machine, manage voltage and energy levels as well as techniques for the different modes of operation and equipment. Learn how to use the weld supplies, tig, wig and arc welds and more. Techniques such as the “Push and Pull” are explained and demonstrated, as well as basic information such as setting up the welding machine and an introduction to the gases used for welding are included.
Cap Holes is a great modifier for modeling as well as making images in 3ds Max. The 3D Studio Max Cap Holes modifier builds faces in the holes in a mesh object. A hole is defined as a loop of edges, each of which has only one face. For example, one or more missing faces from a sphere would produce one or more holes. The modifier works best on reconstructing planar holes, but can do a reasonable job on non-planar holes as well. See how to use it in conjunction with a slice modifier, it’s a goo...

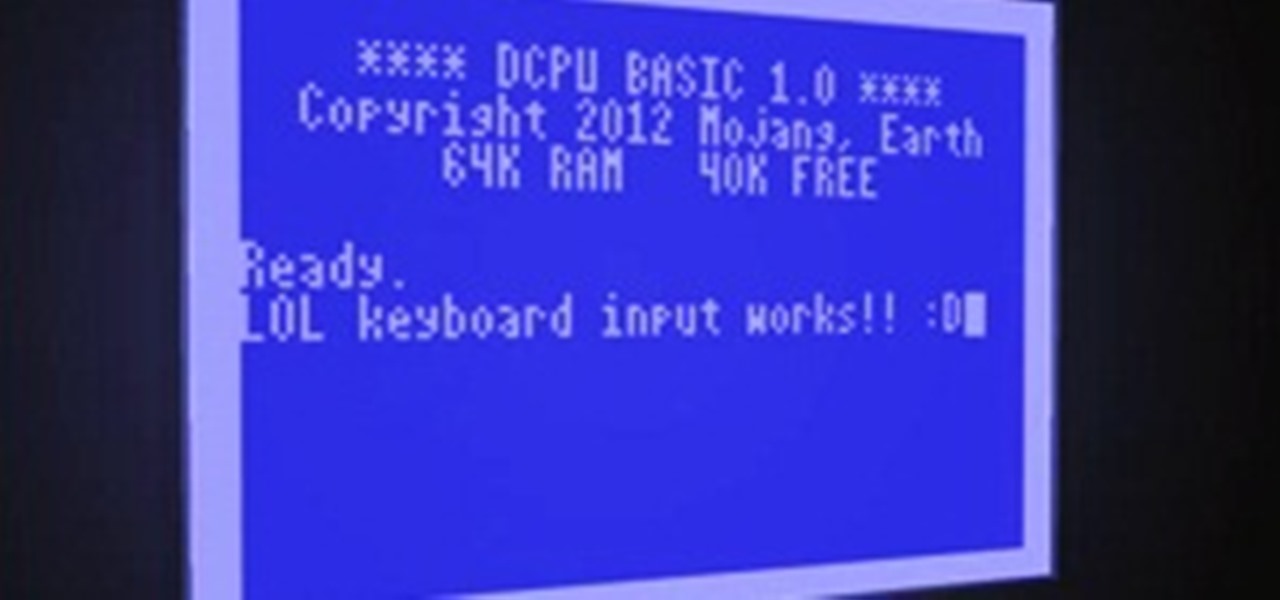
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.
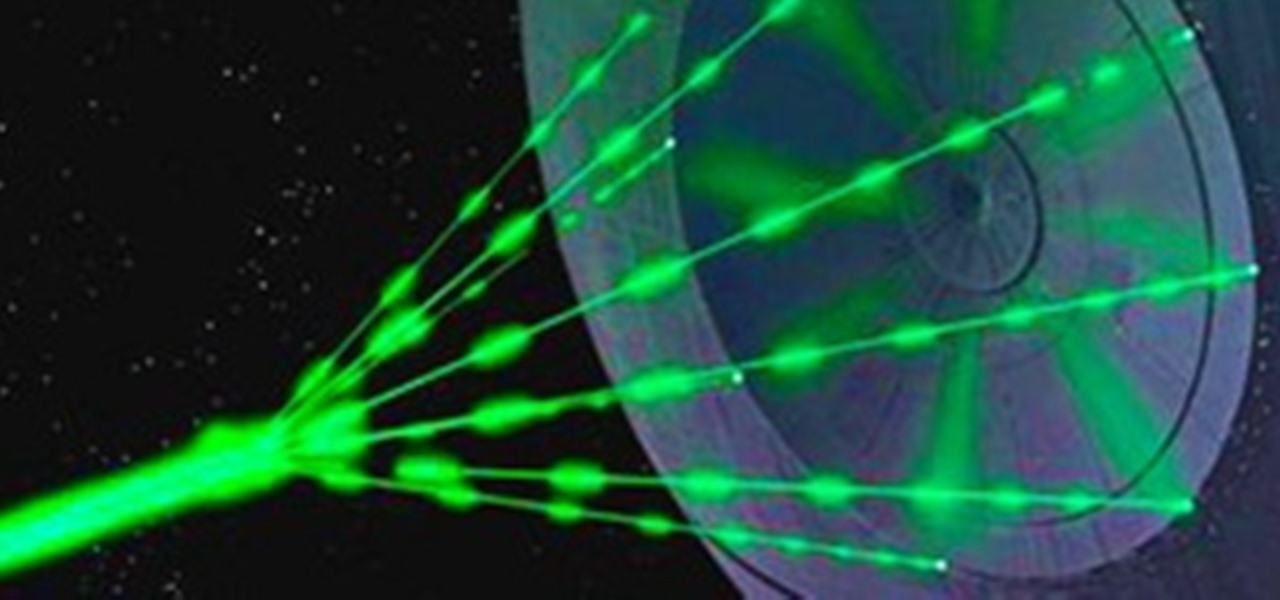
In this series on weaponized lasers, I'll be exploring the function, operation, strength and building instructions for three basic laser weapons; CO2, Diode, and Flashlamp. These laser types are just a few of many, selected because of their simplicity and basic construction (depending on your experience).

In this article, I'll show you how to built a Wireless Transfer of Energy Transmitter. Simply put, this device will send electricity to a florescent light bulb and light it up, from up to three feet. The idea originally (at least, prominently) came from Nikola Tesla (read more about this amazing inventor here), who used his Tesla coils to transfer wireless energy to light bulbs in demonstrations (photo below). However, the circuit described in this article consists of a flyback transformer, n...

If you haven't noticed yet, I've started dishing out some "Scrabble Bingo of the Day" articles that showcase interesting and somewhat unusual seven-letter words (or longer) that could give you an extra 50-point bonus on the board, as long as you empty your rack. So, for this week's Scrabble Challenge you'll have to get your brain in gear, because it's a tough one based of high-scoring bingo plays.

A century ago there wasn't much life available for quadriplegic people. Handicap accessibility was barely even a concept, and lacking medical technology kept any semblance of independence out of reach. Today those unfortunate enough to be paralyzed from the neck down have brighter prospects, but are still unable to participate in many activities. Video games are a great option for those who do not have the use of their legs, but for quadriplegics, the use of a standard controller is not an op...

Yes. That's right. The 2010 National SCRABBLE Championship (NSC) is almost here. In fact, it starts in less than 2 weeks! And if you were lucky enough to register for the competitions, you could win a first place prize of $10,000!

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

If you're a normal, non-corporate video conferencing user, you may not have heard of BlueJeans, but in the corporate world, the software has long been a major staple when it comes to remote meetings.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

The iPhone 11, 11 Pro, and 11 Pro Max introduced a new rear camera system to the iOS ecosystem. Each model has a new ultra-wide lens in addition to the wide one, and the Pros have a telephoto lens. Both have improved selfie cams too. With so many lenses, it can be challenging to choose which to film with, but why pick when you could shoot with two at once?

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

There are many reasons to use Filmic Pro if you're a mobile videographer. Chief among them is its automated controls, called "pull-to-point" sliders. These pull-to-point controls not only allow you to manually adjust focus, zoom, exposure, ISO, and shutter speed before and during the action, they also let you set start and end points to automate each function, leaving you free to focus on filming.

The week of the annual Consumer Electronics Show is supposed to be filled with good news for the augmented reality industry as AR headset and smartglasses makers show off their new wares.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Get Out absolutely tore up the record books this year. And the wildest thing about it? It did so with the most ordinary looking characters and props ever (hence the shoestring $4.5 million budget). Which makes it a godsend for the time- and cash-strapped come Halloween. With Get Out, Jordan Peele is the first (and only) African-American writer-director with a $100-million film debut under his belt. The film is also the _all-time highest domestic grossing debut based on an original screenplay ...

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

The OnePlus 5 just made its official debut, so we now have all of the juicy details. From the announcement, this device definitely sounds like it's going to be another flagship killer, following in the footsteps of its predecessors.

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.
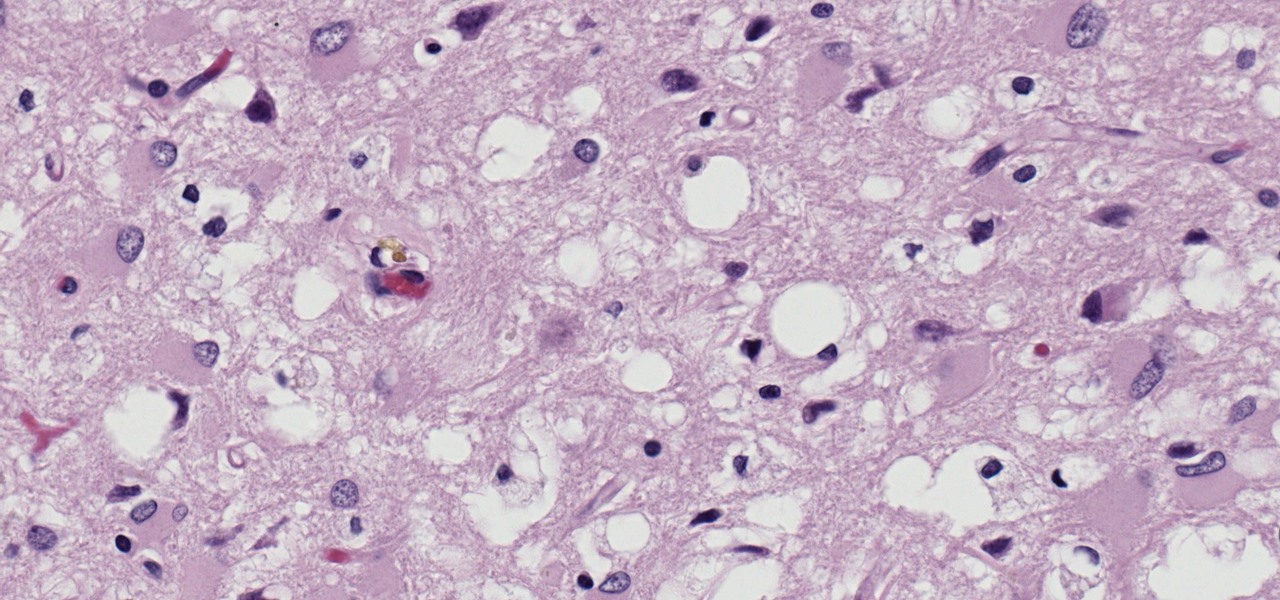
Prion diseases are a group of infectious brain diseases that causes extensive tissue damage, resulting in sponge-like spaces in brain tissue. Prions include Creutzfeldt-Jakob disease in humans, bovine spongiform encephalopathy (often called mad cow disease), and chronic wasting disease in hoofed ruminant mammals.