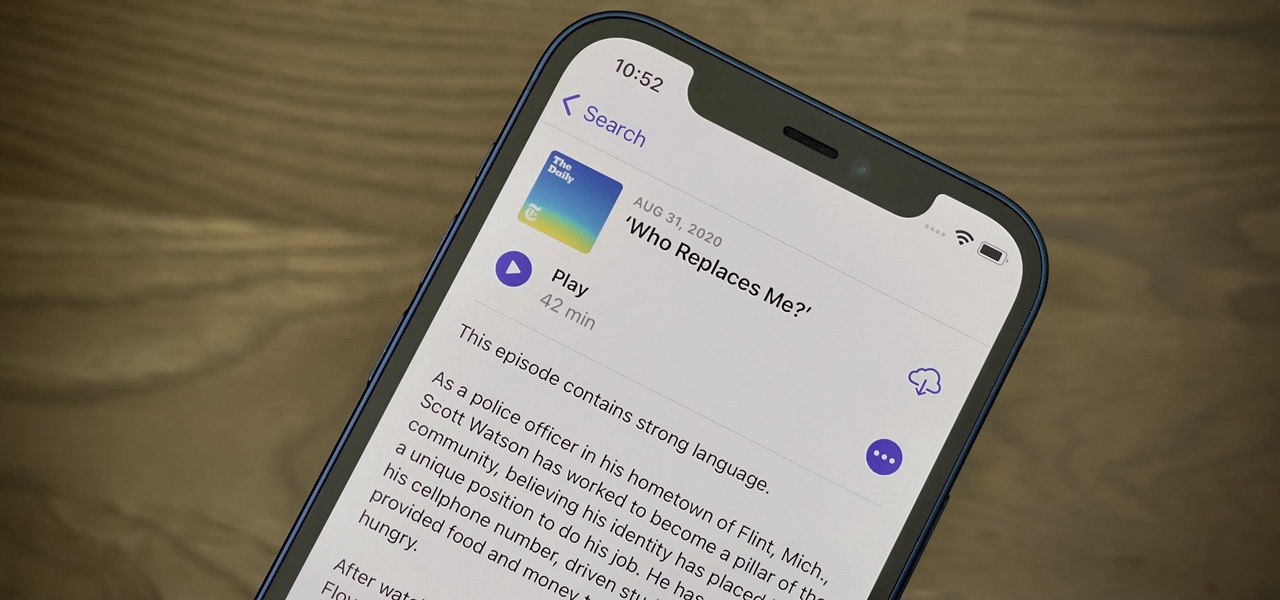
Many podcasts you come across will tell you to check out the episode notes for information and links about whatever that show's topic is. Easy enough, unless you're using Apple Podcasts, where these episode notes don't appear to be anywhere at all. Luckily, they're just hiding in plain sight.

In response to Sony unveiling its own holographic display back in October, Looking Glass Factory CEO Shawn Frayne quickly penned a letter welcoming the electronics mainstay to the field, with a post-script teasing the reveal of their own for December of 2020.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

So the new iPhones have arrived. Like last year, Apple released three iPhones in three different sizes that vary in price and specs. There's the base model iPhone 11, and then there are the real deal, premium models, the iPhone 11 Pro and Pro Max.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

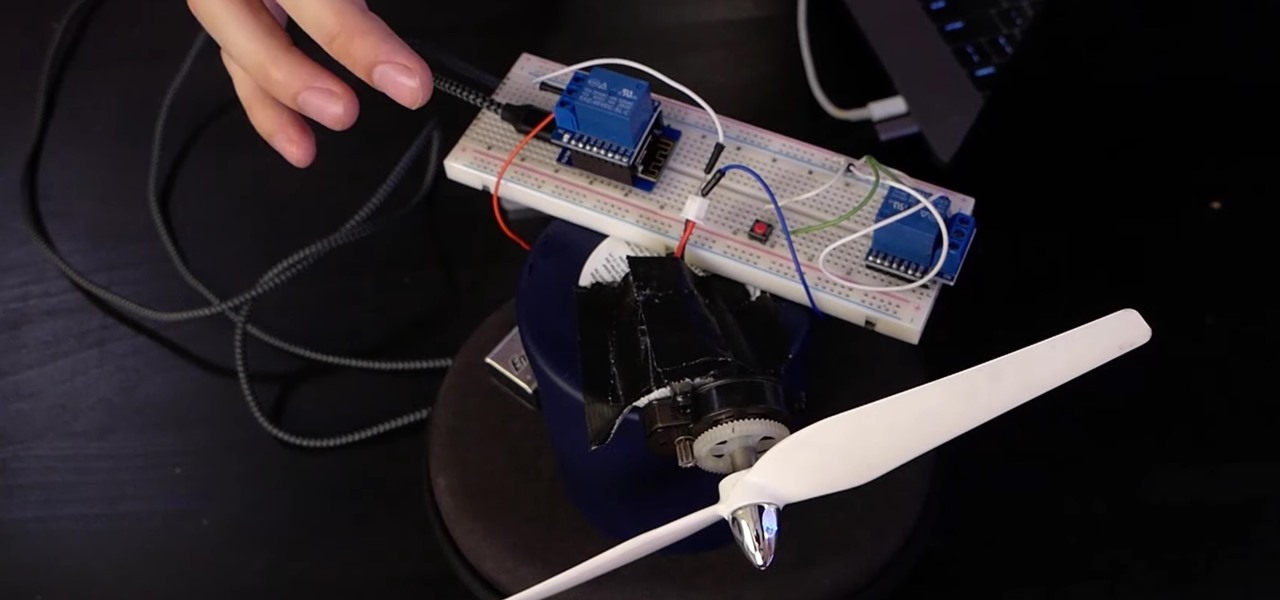
A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Unlike the realm of virtual reality, augmented reality is less about losing yourself in some fantasy environment, and more about getting things done in the real world. So while we've seen some great games that capture the imagination on devices like the Magic Leap One and the HoloLens, when it comes to real-world usage, the biggest developments coming for AR apps that are the more practical ones.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

After poor sales of the Pixel 3 and Pixel 3 XL, Google needs to reinvigorate its Pixel lineup, devices it's been pushing heavily over the last couple years. On May 7, Google had the eyes and ears of the technology industry at its Google I/O keynote, making it the perfect time to announce new devices that would attract a different crowd of users. Meet the Pixel 3a and 3a XL.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

There are countless methods and cleaners aimed at eliminating stubborn stains from everything to clothing, carpet, and furniture. But completely removing every last trace of a stain doesn't require an arsenal of chemical cleaners and repeated cycles in the washing machine. Most stains can disappear in a matter of minutes with a dose of alcohol.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

Stephany is going to take you through the process of sewing a mens shirt. She is going to use a pattern and talk to you first about choosing a pattern and knowing what the package means before you start. This is a very long video series, but sewing a shirt has many components to it, so be patient you'll finish the shirt eventually!

Visit a webpage on your iPhone, iPad, or Mac, and there's a good chance you'll be bombarded with distractions such as ads, fullscreen pop-ups, cookie consents, log-in requests, notifications, email signups, sticky videos, and calls to action. If you're using Safari and content blockers, "Block Pop-ups," and Reader mode can't hide the elements you need, Apple's got a new tool you should be excited about.

With iOS 17, Apple News integrates more deeply with Apple Podcasts and Apple Stocks and has become a bit more fun thanks to new crossword puzzles. But that's not all that appears in the updated News app.

It was a long time coming, but Android finally has built-in scrolling screenshots, and they come courtesy of Android 12.

We're still basking in the afterglow of the HUGE Snap Partner Summit last week, where Snap made Snapchat a much stronger augmented reality platform while also unveiling the AR smartglasses version of Spectacles. This week, we got a peek at how Spectacles AR started and got our hands on Lenses from Lego and Disney featured during the keynote.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety.

If there is one constant in currently available AR headsets, it's that, for a quality experience, they'll carry a high price tag. Price is one of the reasons these devices are mostly marketed towards enterprise customers for now.

In the realm of social media, all roads lead to one destination: cracking the code of continuous partial attention dopamine hits. We learned this back in the days of Vine, before Twitter foolishly killed it. And I pointed my lens at the emerging trend back in 2016 when I highlighted Musical.ly for Mashable, just before it was snapped up by China's Bytedance for $1 billion and merged into what is now TikTok.

If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.