Check out how to read a binary clock in this how to video. You'll see how to read the BCD (binary-coded decimal) format like so many can't. Just watch this if you have trouble determining the hours, minutes, or seconds on your binary clock. You can read it in standard or military time if you'd like.
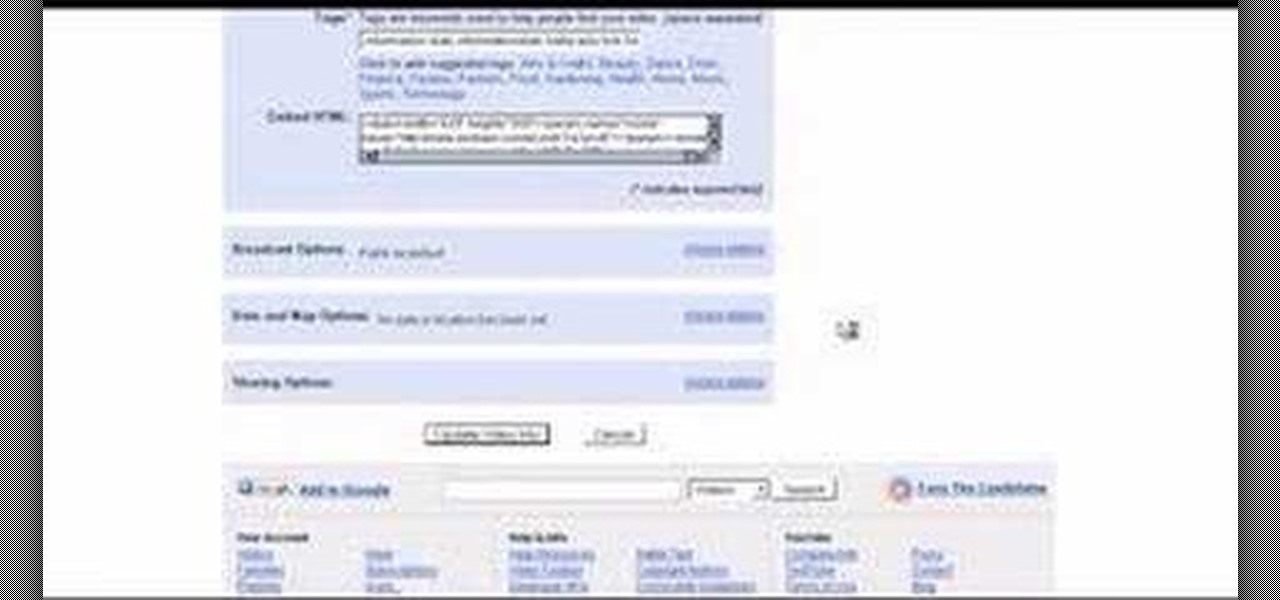
This shows how to bypass youtubes block on certain characters in video descriptions.. something thats very annoying, especially in How-to/DIU videos that require some codes in the description using nothing more but some simple HTML.

This video explains how to read a tape measure. Discover how tape measures are divided into different fractions. Color coding is also used to help with spacing things 16 inches on center.

Ask the Builder host, Tim Carter, shares a quick lesson to help you out of a tough spot when working with plumbing vent pipe. If you're installing a sink, and need to follow the codes, then just work around it with this trick.

Watch this video to get set up with C++. The video covers creating a project, what to do with the console window, hello world code, and the debugging process.
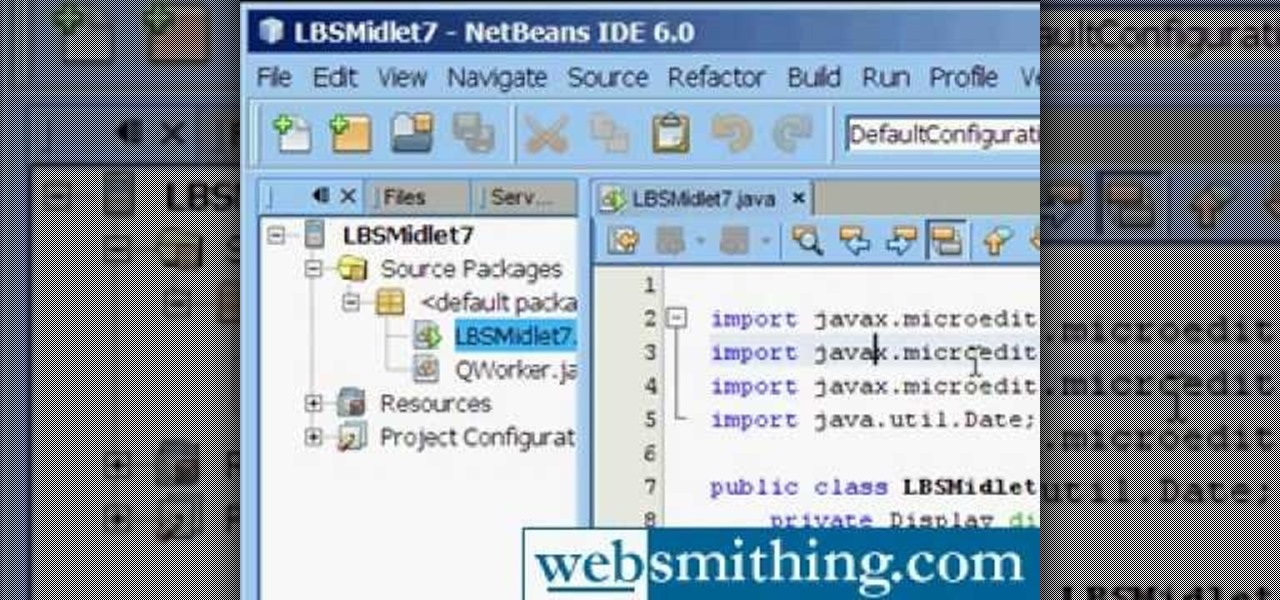
This tutorial explains how to setup the gps cell phone app. Go to http://www.websmithing.com for the full explanation and source code, you'll find it on the programming menu tab.

Members of the Chicago area gang the Latin Kings explaining their language of symbols and codes expressed through graffiti.

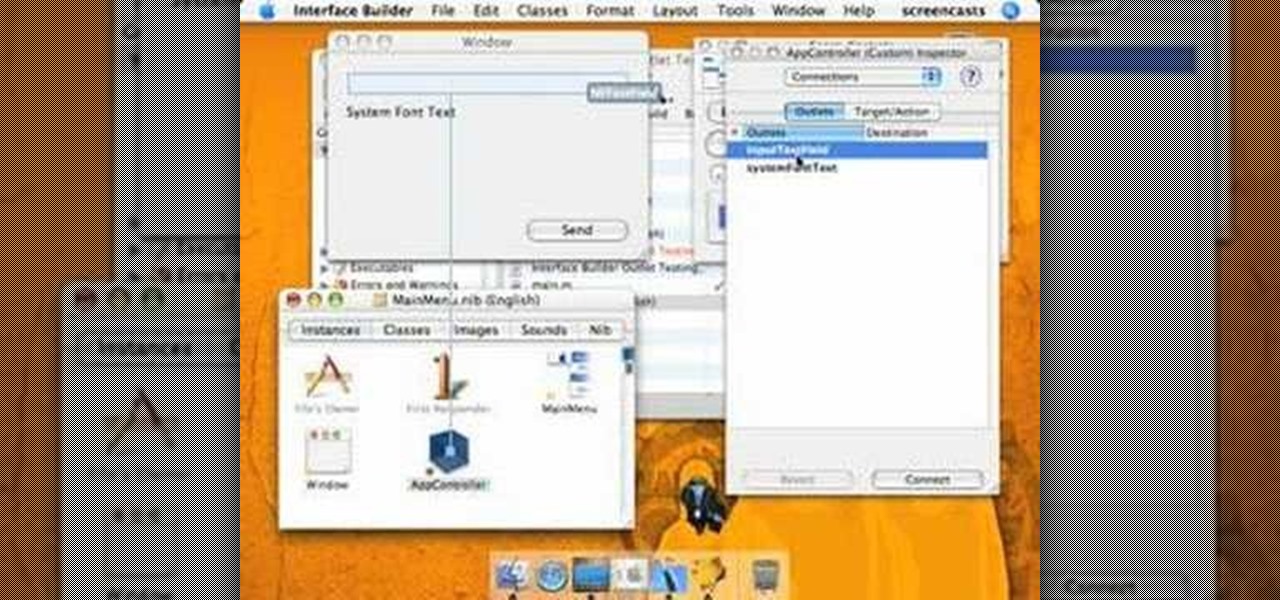
This Xcode video tutorial will help beginners learn how to use Interface Builder to use Objective-C code to interact with UI elements implemented in their Mac OS X applications.

Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.

Austin Chau does a short tutorial about how to use the JavaScript Client Library with the Google Calendar Data API.

This is Anthony Caporale's version of the bloody mary, made in honor of the Da Vinci Code fans. You'll need pepper vodka, citrus vodka, tomato juice, salt, pepper, Worcestershire sauce, olive juice, a squeeze of lime, and garlic stuffed olives for garnish.

In the embed code for a video, you can change certain numbers for the width and height of your video in HTML.

Get closer to God with a hot chick.

Make a getaway from the cops, with a hot chick by your side.

Try some gender bending in Elder Scrolls IV (4): Oblivion and flip the sex of your character. To do so, enter the code ~sexchange.

This sexy chick has all the right moves in Tiger Woods PGA Tour 08 for the Nintendo Wii. Learn a cheat code to unlock all of the clubs in the game.

This busty beauty shows you how to bust out a tiny skater in Tony Hawk's Proving Ground using a code.

To get the girl, you need a hot ride. So here's a cheat code to up your ride in Juiced 2: Hot Import Nights.

Learn how to write a simple prank program that will make someone think that their hard drive is being formatted and completely erased.

Send a little dose of system shutdown to your friends or foes using these codes!

This tutorial will teach you how to make a simple Flash app that uses the microphon using the ActionScript code:

Following the proper electrical code for installing electrical outlets will be shown in this video.

In this video you'll learn how to play "Mr. Jones" by Counting Crows. It's a good song for blending open chords with your bar code F.

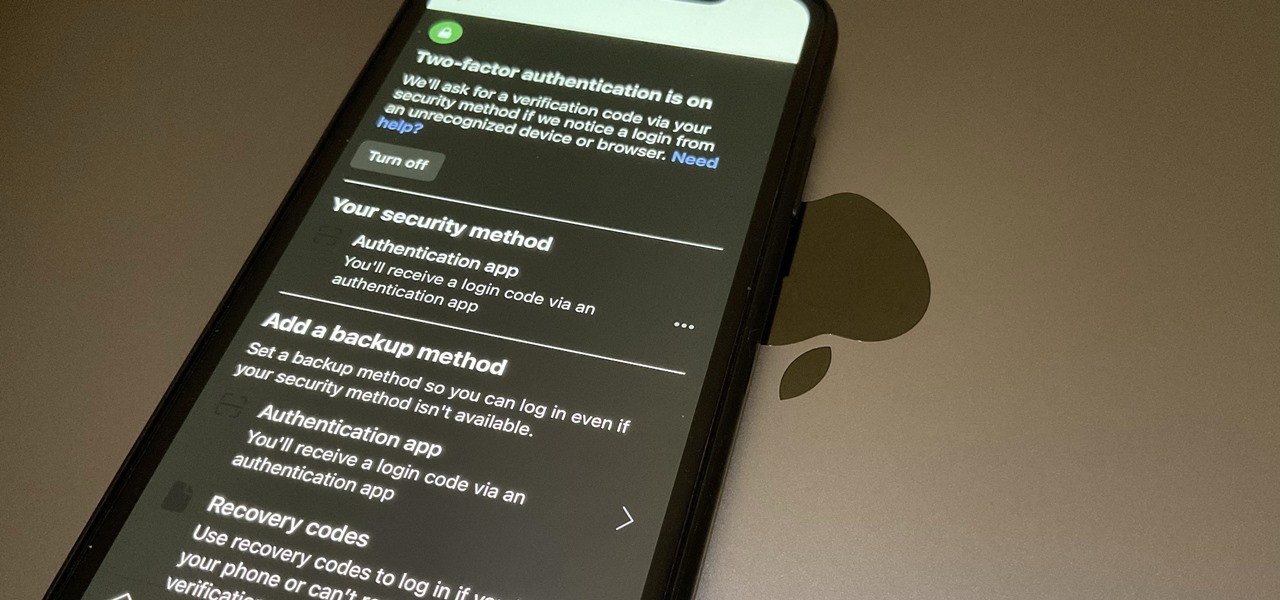
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

The global gaming market is expected to generate $160 billion in 2020. With emerging markets in the Middle East and Africa, the planet's 2.5 billion gamers are always looking for the next great adventure.

PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

How much screen time is too much for a child? Should you let your children have a smartphone or tablet? What age is appropriate to introduce them to technology?

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Apple's first AR wearable might not arrive until 2022, but we may have an early preview of what it will be like to wear a pair of its smartglasses via iOS 14.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.