Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Another entrant into the do-it-yourself AR content creation market has emerged, as Zappar has updated its ZapWorks Studio software to include features for development newbies.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

If you or someone you know has younger kids and you're looking for an augmented reality toy, Pai Technology has just the educational option for you.

Typos are a constant annoyance that we all deal with thanks to the cramped touchscreen keyboards on smartphones. For many, nothing beats the feel of a good old physical keyboard when it comes to typing fast with minimal errors. Fortunately, WhatsApp has an awesome feature which lets you use their messaging service right on your computer.

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

Google announced today that it's offering rewards to Android Pay users, and taking advantage of these deals could land you a free 2nd Generation Chromecast, among other prizes. The Tap 10 promotion is pretty self-explanatory: Tap to use Android Pay 10 times before February 29, 2016, and Google will give you a code to redeem a free Chromecast, free music, or both. You'll also be rewarded for Taps 1 through 9 as well. You'll receive a code for one music track from the Google Play Store for ever...

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

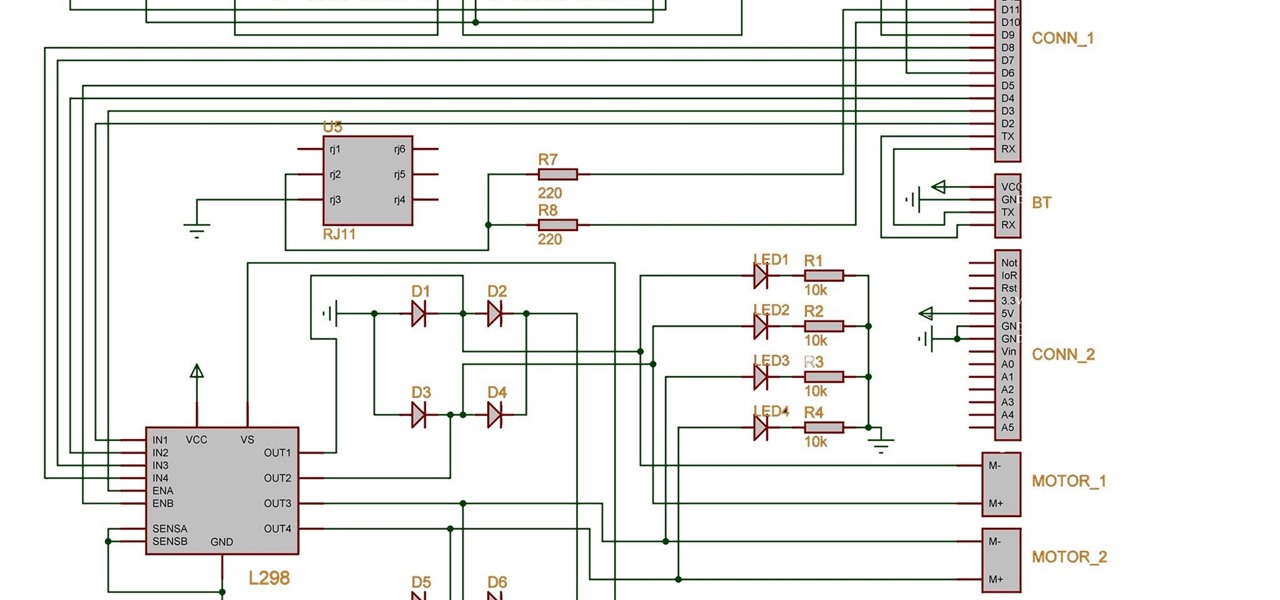
Two years ago, driven by a good friend of mine i decided to give it a try on timelapse photography. I had a DSLR camera but didn't had an intervalometer, so i assembled a small electronic circuit on top of an Arduino Uno, made some basic code and did my first timelapse movie. The result was awful, but for some reason I was hooked.

Google I/O, the national developer conference for the Mountain View giant, has come and gone. We saw the preview for Android L (which you can get right now on your Nexus 5 or Nexus 7), Android Wear, and Android Car and TV.

This is an easy step by step tutorial how to lock your jewels in a hotel room or in a public safe. Be aware that in a public safe it is more secure to use the second method of locking by a magnetic card, not by a PIN code that can be easily seen by someone nearby.

In old-school Konami fashion, there's an Easter egg lurking inside your Samsung Galaxy S3, and I'm not talking about gingerbread men, robots, or jelly beans. In fact, it's actually an achievement, like those you would unlock in Black Ops on your Xbox 360, and it's pretty easy to find.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

Last week, the whole world ushered in the new year, celebrating the start of 2013 with family and friends, and of course, that little thing we like to call alcohol. But just because New Years Day is over doesn't mean the party is. And surely, there will be some assholes out there that will drink and drive this year. It happens. So, how can you make sure you're not one of those assholes?

'Tis the season... for cheap (and free!) video games. THQ's Humble Bundle lets you get 7 games for any price you want, and now they're making it even better by offering fans a free Steam copy of Metro 2033 just for liking Metro on Facebook, which is gearing up for the latest Metro: Last Night release.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

If you're new to DreamCoder for Oracle, one of the very first features with which you'll want to acquaint yourself is the data table browser, which will permit you to display entries in a given Oracle database. For a detailed walkthrough of this feature, take a look at this video tutorial.

If you're new to DreamCoder for Oracle, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your Oracle databases with ease. For step by step instructions, consult this how-to.

The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— go to College Board and get your SAT test results now!

This video shows you how to fix a Windows "Blue Screen of Death". You should know what to look for when you get the BSOD. You should look for the error code first and then the stock code. You should hit the F8 button upon start up to go to the last known good configuration and it will boot your computer to the last time it booted correctly. You can also start in safe mode. You will need to do a system restore. If that doesn't work do a Google search for the file name that is causing the probl...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Game design is among the fastest-growing industries in tech. What once was a passing hobby or niche job has become a thriving industry with a huge variety of work. If you are interested in learning game design, either as a hobby or a profession, then The 2021 Complete Learn to Code by Making Games in Unity Bundle will hold some interest for you — and it's on sale for $39.99.