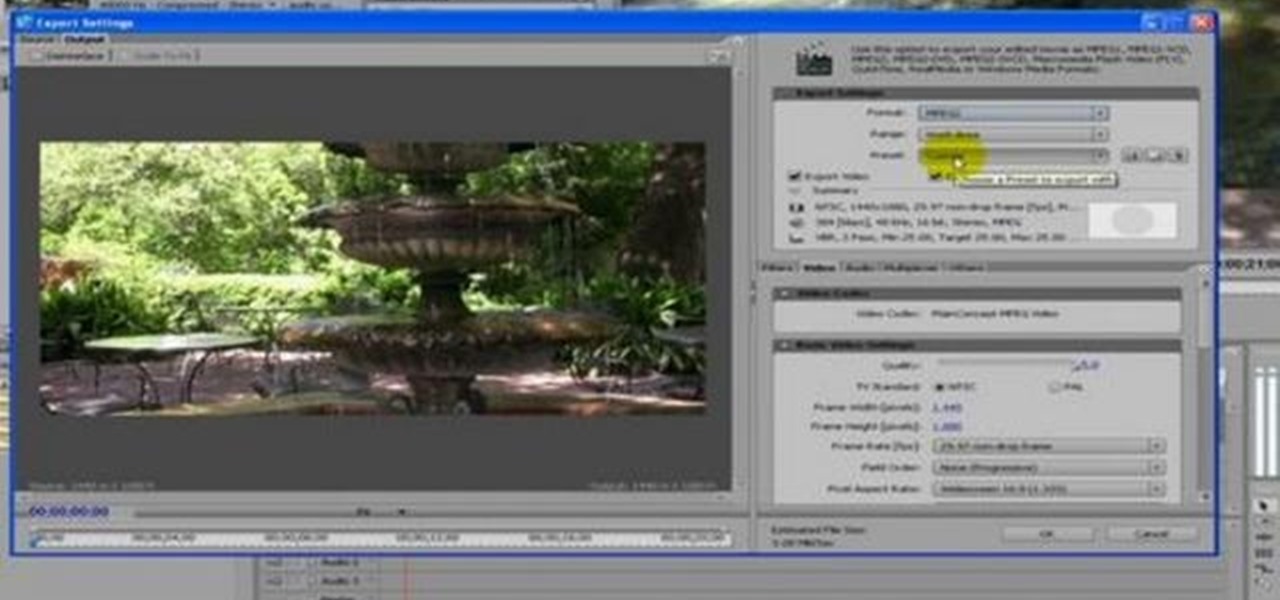
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to organize your desktop with Microsoft Scalable Fabrics.
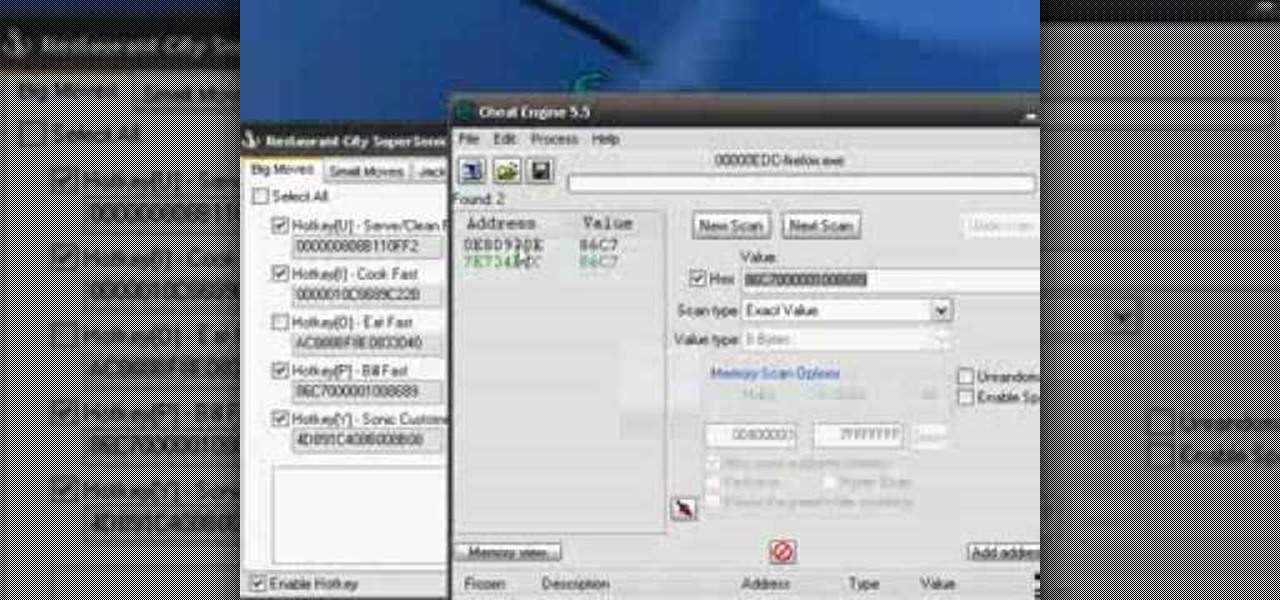
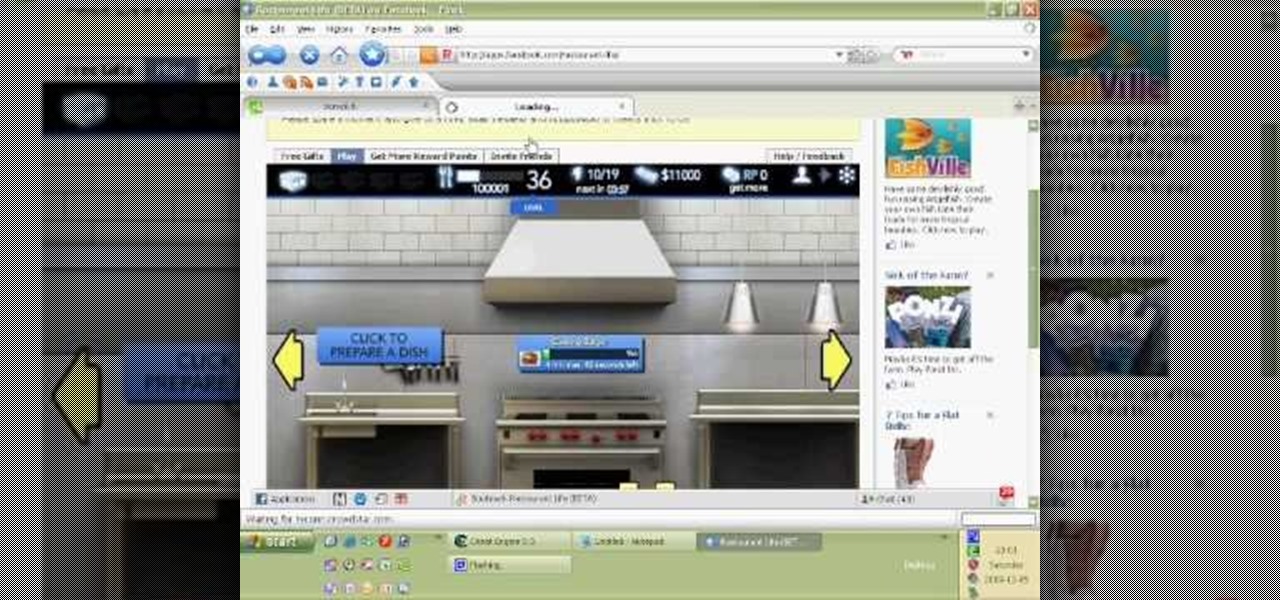
Hack Restaurant City (06/02/09): Waiters serve faster
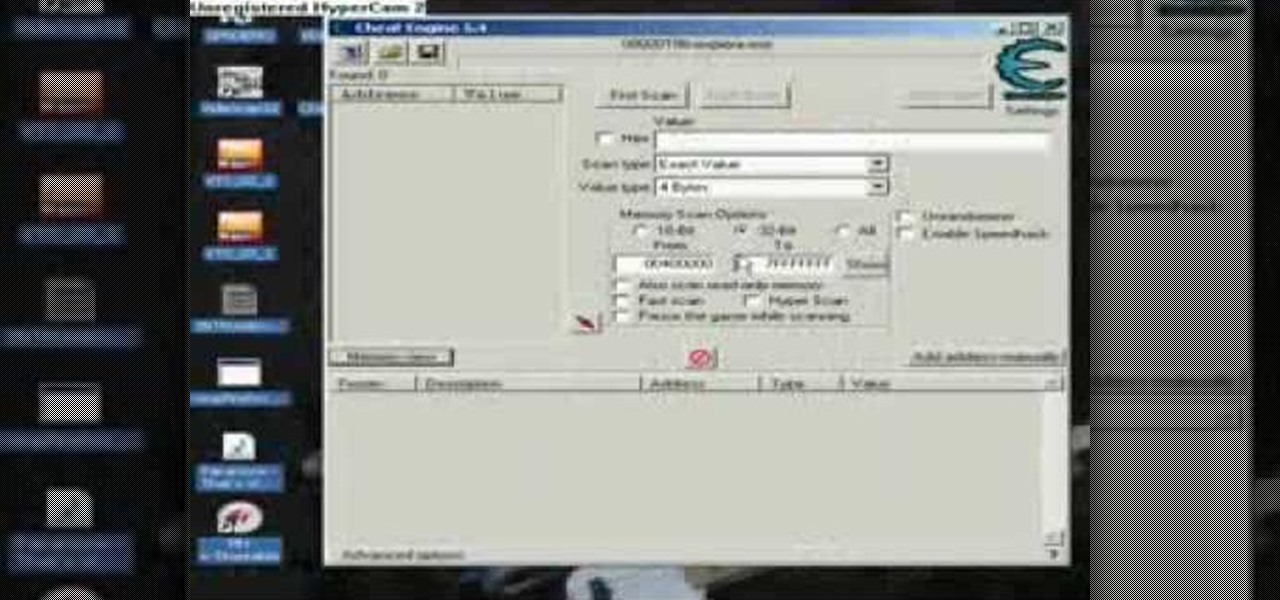
Hey, world! This is a tutorial on how to use cheat engine(version 5.4 or 5.5) to get money on the Facebook application "Pet Society".

Video of cheats to unlock costumes in the action game Star Wars: The Force Unleashed for XBOX 360! This video gives cheat codes that enable you to get all the costumes unlocked. Very cool for a Star Wars game.
This shows you how to install an app for the Apple iPhone that records video. You have the capability to record video. The hardware is there. It's simply a deficit of software. Both the iPhone 3G and regular iPhone can record video with the right iPhone App. Here's what you need to get video captured with your phone.

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

A detailed look at how to unlock the Secret Survival mode in Mortal Kombat Shaolin Monks.

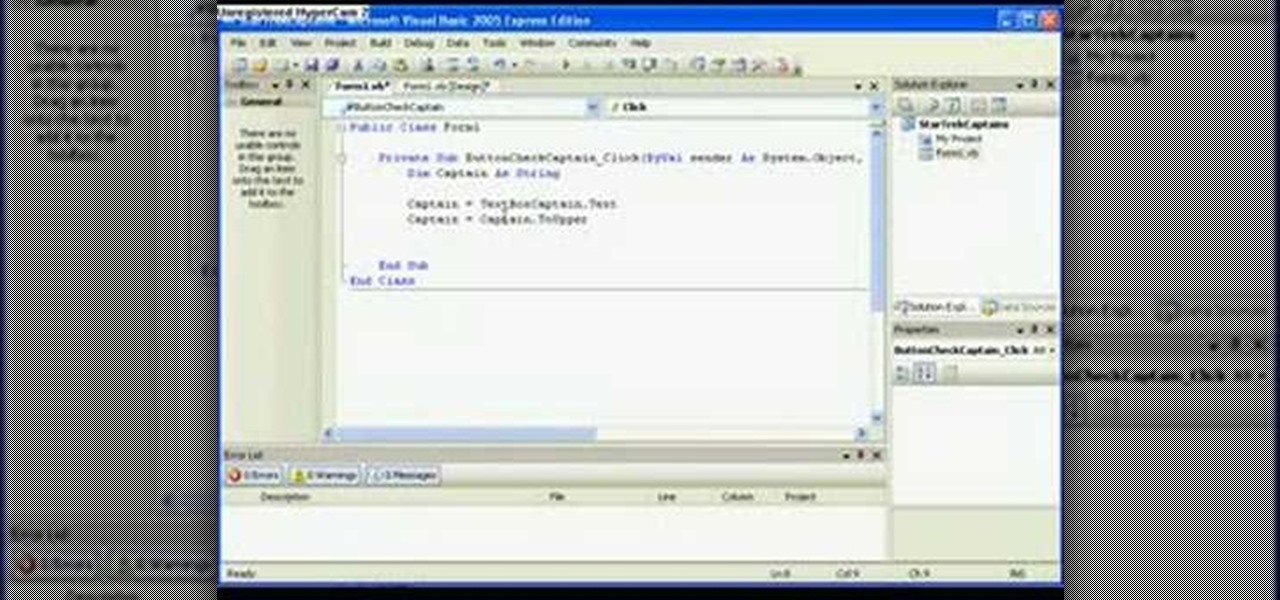
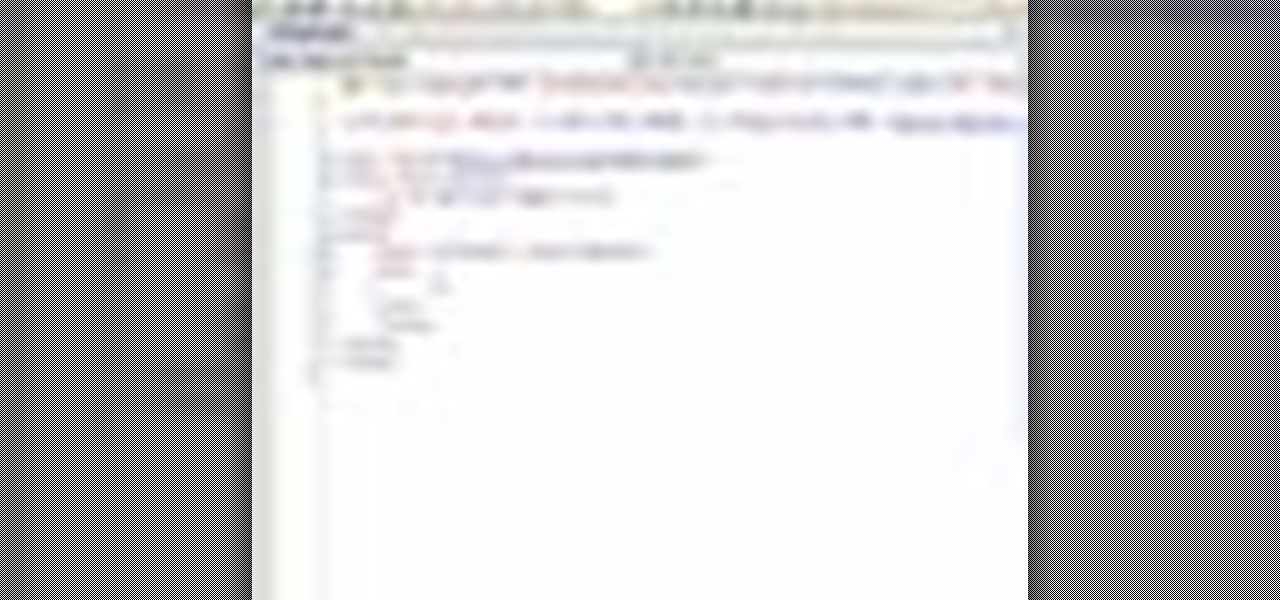
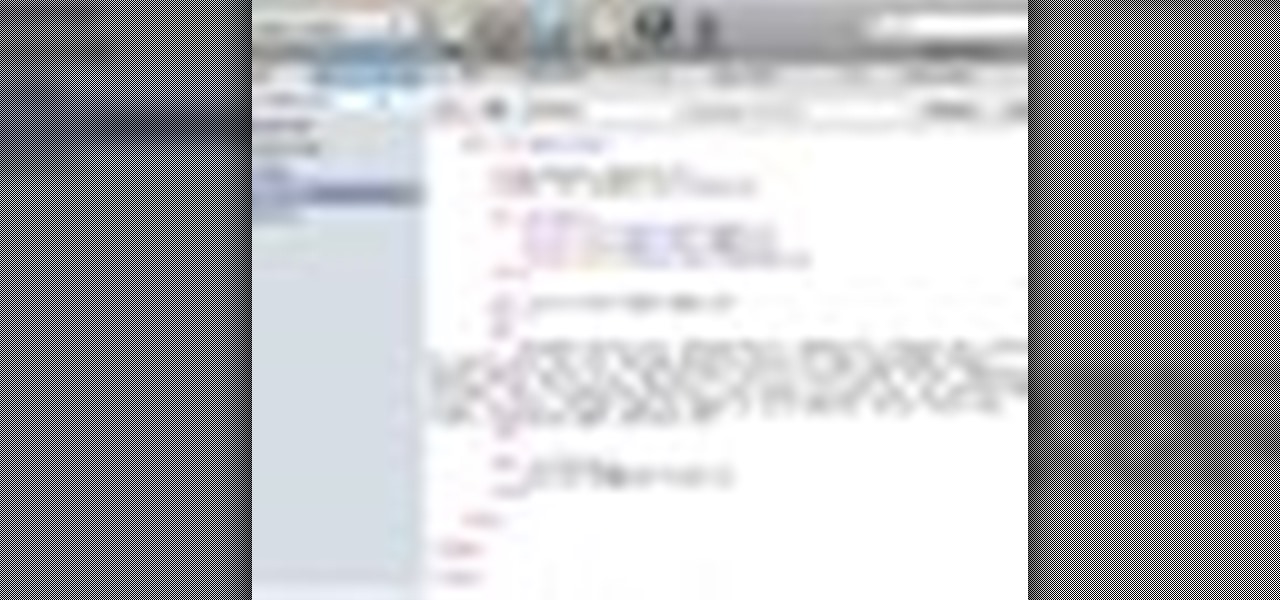
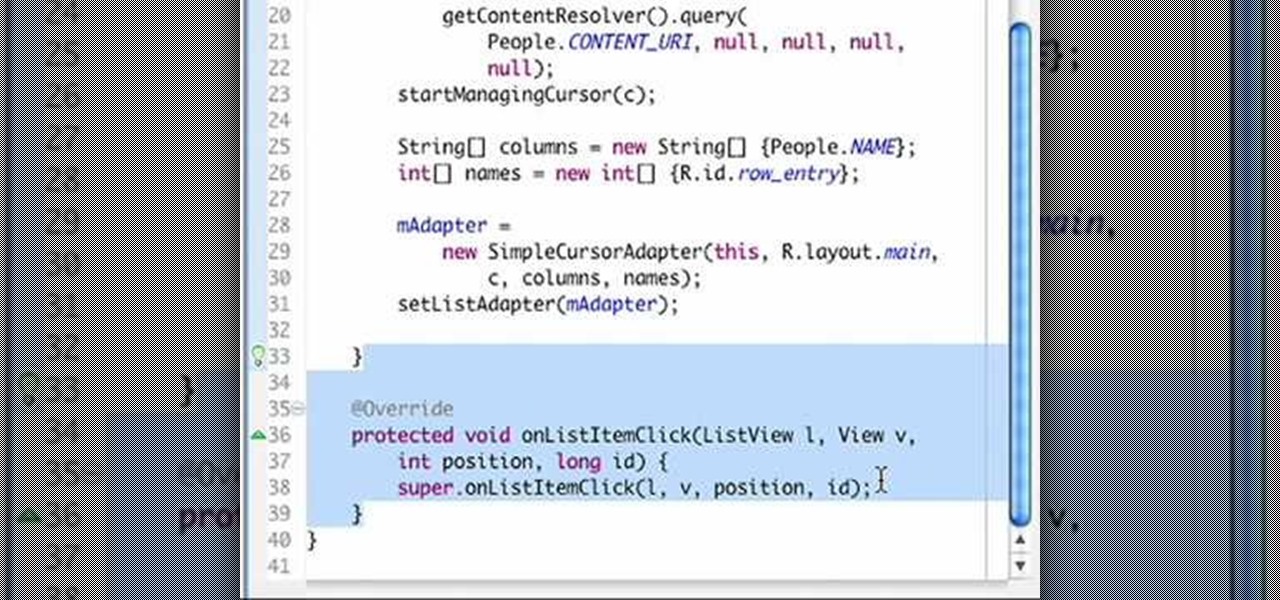
In this Visual Basic tutorial, you'll learn to use conditional statements for the push-button validation of a designated text string. The code used in this example is as follows:

There are some really helpful people in the Rails community, but you'd be hard-pressed to find anyone who helps bunny and green coders more than Ryan Bates. While this tutorial is geared towards intermediate Rails users, beginners are certain to walk away with something as well. In this video tutorial, Ryan and Miles K. Forrest provide a walkthrough of scaffold_resource. If you're even a little bit interested in learning more about Ruby on Rails, you'd be well served to take a look!

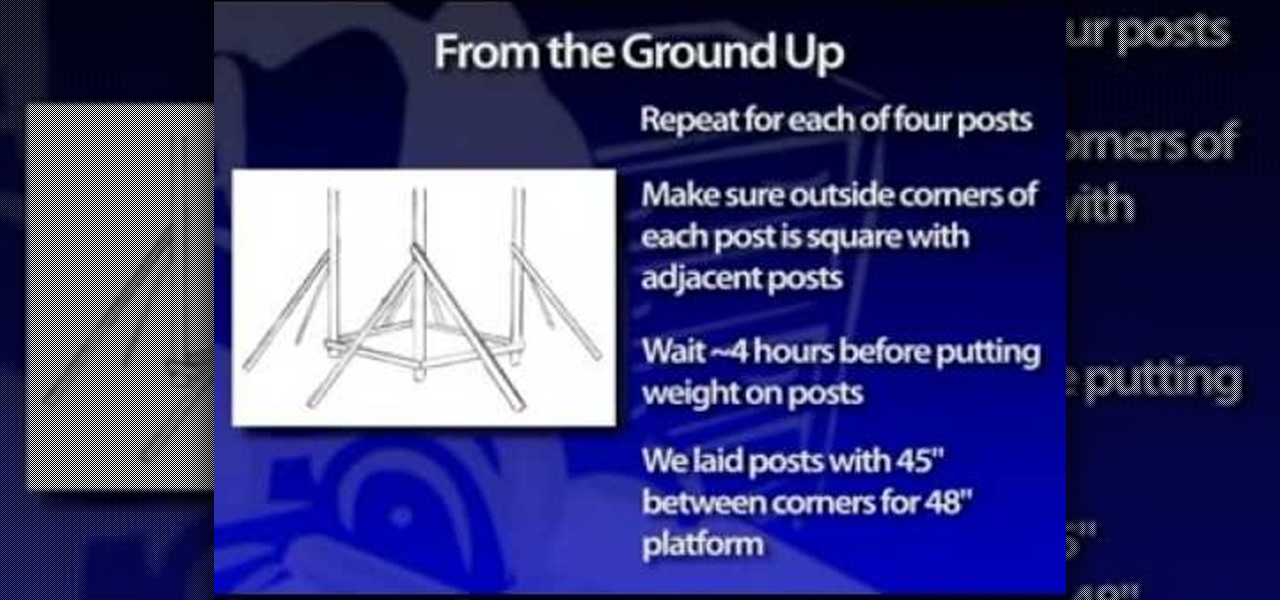
In this video tutorial, you'll find instructions for building a standard joist design playground slide, supported by 3-by-4 posts and secured with galvanized fasteners. All fasteners exposed to the outdoors must be weather-resistant, galvanized, zinc-coated brass or stainless steel. Standard homeowner tools are all you'll need to complete your slide—a tape measure, post-hole digger, circular saw, sawhorses and a level. A good drill/driver is a great tool if using decking screws as fasteners. ...

Core Data is a powerful data-management framework introduced with Mac OS X v10.4 Tiger. When you take advantage of Core Data, it slashes the amount of custom code you need to write in order to manage application data. Opening, saving and undo management can all be handled by Core Data, freeing you to concentrate on creating unique features for your application. This video tutorial, which presents a general introduction to using Core Data, will walk you through the process of building a simple...

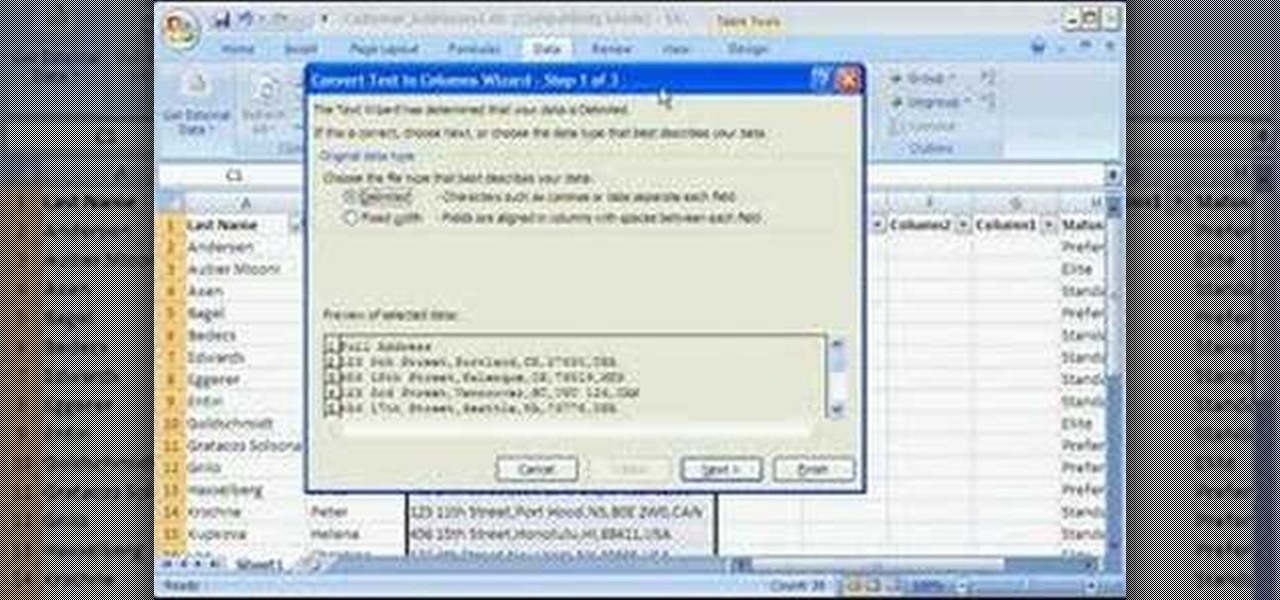
Storing information, such as a full address, in one column can limit what you can do with that information. For example, you can't easily filter or sort by part of the address, such as country/region or city. However, if you break up the address into its parts — street address, city, state/province, postal code, country/region — one for each column, you can remove those limits. Watch this instructional video to see how to use the Convert Text to Columns Wizard to automatically break up a sing...

It's difficult to learn programming in the abstract. By building something I need and care about I can learn piecemeal, asking just the questions I need to solve the next step.

In this video tutorial, Chris Pels will show how to use a control adaptor to provide different renderings for an ASP.NET server control without actually changing the control itself. In this video, an ASP.NET BulletList control will be adapted to display each list item horizontally using div elements instead of the traditional ul elements. First, see how to create a class that inherits WebControlAdaptor and then implements the code to render the new list format. Next, learn how to map the new ...

Many sites do not use any fancy Content Managment System (CMS) to generate their pages, they are just just good ol' static HTML content. A site for your grandmothers pie baking business probably only has a few pages, perhaps a homepage, about page, and contact page. Each of these pages has different main content, but much of it stays exactly the same, like the header, navigation, and footer. Think of these sections as "modules" that you can easily use PHP to insert into the page. This way, ma...

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

Just happen to have some video footage in AVCHD format? That would be "Advanced Video Coding High Definition"—you know—HD video files. If you've got some of those MTS files (like from a Canon HG10 camcorder) you want to open in a program that doesn't support them, like QuickTime or Premiere Pro, then you're going to have to convert them to a different format. Here's a way to convert them without losing the quality. You'll be converting the MTS files into HD WMVs at 4,000 kbps with a program c...

In this ShowMeDo John Montgomery demonstrates how to create a project in Eclipse, then write and run a simple "Hello World" Java application. He also demonstrates the code-completion features of Eclipse, how to use the find and replace functioning and use the CVS version control system.

Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

Have an old bike combination lock that you can't remember the code for? If it's a simply four-digit cable lock, you can easily figure out the combination with a quick peck-and-go method. Best of all, this technique doesn't require any tools or special know-how, and let's you reuse the cable lock again versus just damaging it with bolt cutters. All you need is a bit of patience and you'll have your figure out your combo in no time.

Once in a great while something comes along on the internet that’s so unbelievably simple and yet works so well. Twitter is one of them. On the video conferencing side, now we have MeBeam. MeBeam, which requires no software or drivers to be installed, is a web application that will permit you and up to 15 of your closest friends to hold a video/audio conference (provided you and said friends all have webcams or, at the very least, microphones). For further details consult this simple how-to!

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

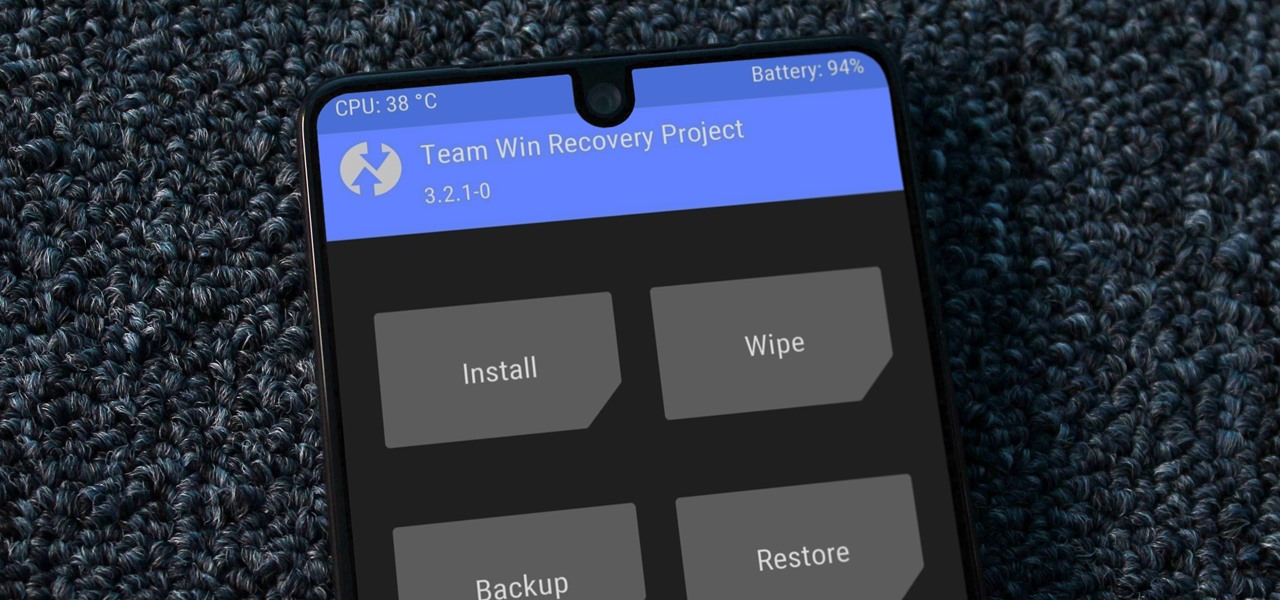
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

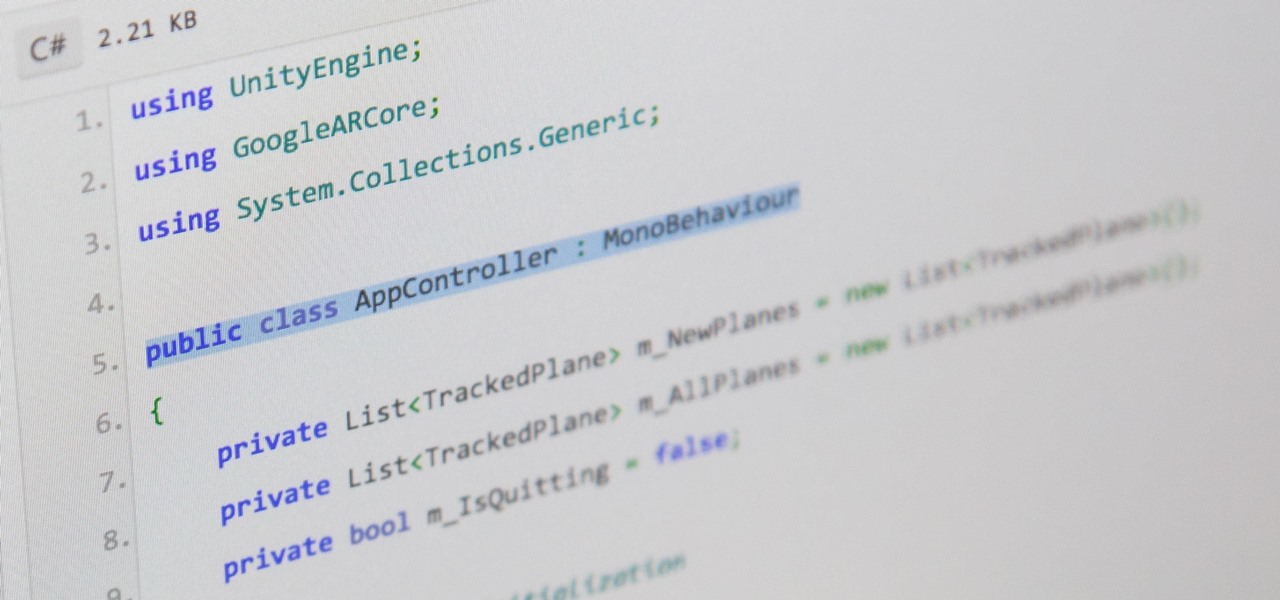
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.