For developers and makers getting started with augmented reality, Intel is lowering the barrier to entry for its RealSense line of sensors.

Sometimes, you encounter words in a non-native tongue while using your Android device. The Google Translate app has an awesome feature where it will translate any text you highlight. An overlay will appear, and on this overlay, there will be the translation of the foreign word. This can help you if you need a translation quick fix or if you are learning a new language.

It's no secret that the enterprise sector is hot for augmented reality, but the move into the enterprise AR software market by one of the biggest names in industrial engineering announces the technology's arrival loud and clear.

Months ago, we showed you some of the powers of Spatial, the HoloLens app that allows groups of workers to collaborate in augmented reality using 3D avatars.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world.

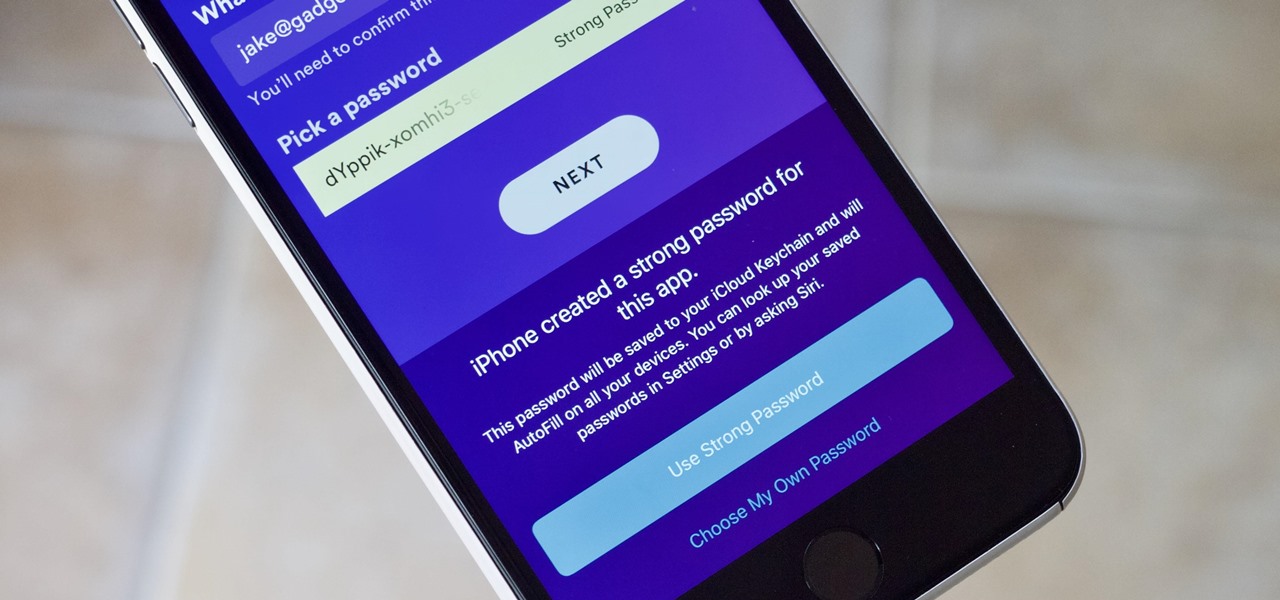
Maybe you prefer writing passwords in a notebook. Maybe you like creating your passwords yourself. Whatever the case, you don't like iOS 12's new automatic password generator, and you don't need it to pop up every time you enter a new password in Safari or a third-party app. Lucky for you, iOS 12 lets you disable the feature altogether. Unfortunately, that perk comes with a catch.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Instagram is no stranger to stealing features from Snapchat. Stories, originally a Snapchat invention, feels more at home with Instagram today. Now, Instagram is attempting to repeat this feat with nametags, a way to quickly add new friends akin to Snapchat's Snapcodes.

Some phones have a feature that turns your screen white for a second when you're taking a selfie in dim lighting. This does a great job of illuminating your face in a pinch, but there are two problems with it: First, not all phones have the feature, and second, it doesn't work in third-party camera apps like Snapchat and Instagram.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the iPhone X's announcement, another phone was revealed, and almost everyone seems to have forgotten about it. We didn't.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

Now that the cutting-edge iPhone X is up for preorder, everyone is excited to see how the new device will compare to offerings from Apple's competitors. Namely the Galaxy Note 8, which is a beast of a phone in its own right.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

Waymo revealed more clues about its future business model after it said yesterday it plans to kill its Firefly pod-like car project and focus more closely on offering driverless systems for commercially available car and truck models.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

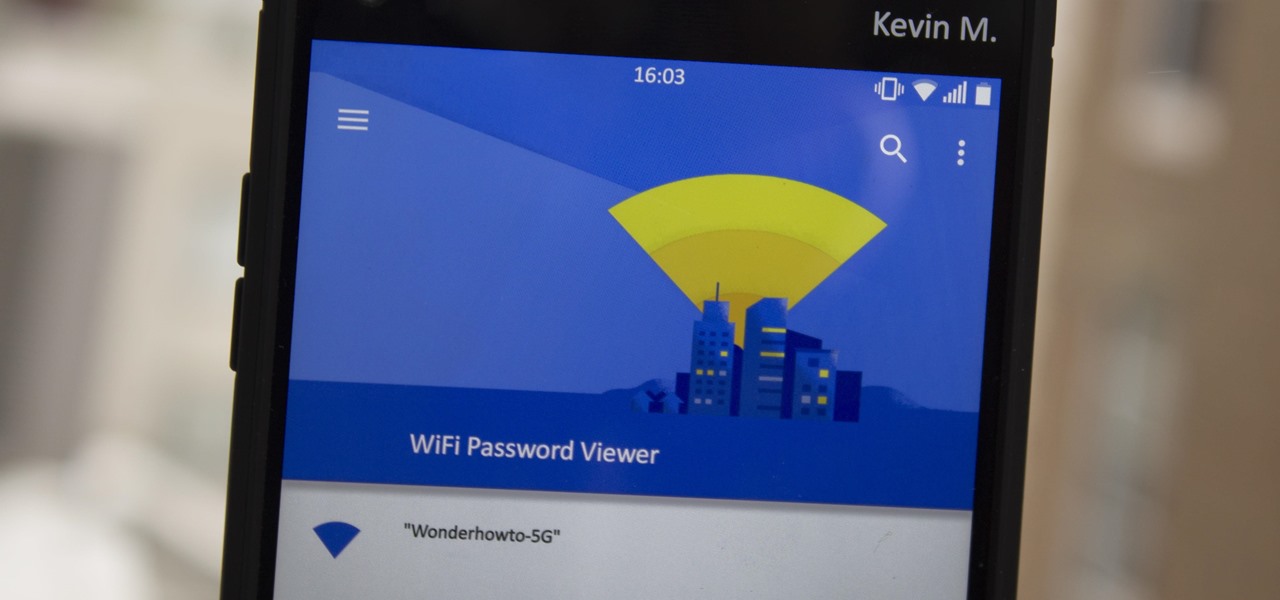
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

Recent launches of YouTube TV and YouTube Go created a bit of excitement on the web. Though the latter allows downloading, it doesn't allow background playback, as that would require a YouTube Red subscription for $10 a month. However, there's still a way to get both of these features without paying a dime.

Chinese search engine giant, Baidu, has just announced its own autonomous car platform which is intended to speed up the development of driverless vehicles.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Some manufacturers, like Samsung and LG, have had split-screen multitasking on their custom versions of Android for years. But starting with Android Nougat, Google added this functionality to AOSP, which means that all phones and tablets running Android 7.0 or higher will now have a new multi-window mode.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

A little less than a year after announcing "Project Astoria," Microsoft announced Thursday, February 25th, that it will end the "Bridge," which would have brought Android apps to the Windows Store.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.