
How To: Use BeEF and JavaScript for Reconnaissance
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.


Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .
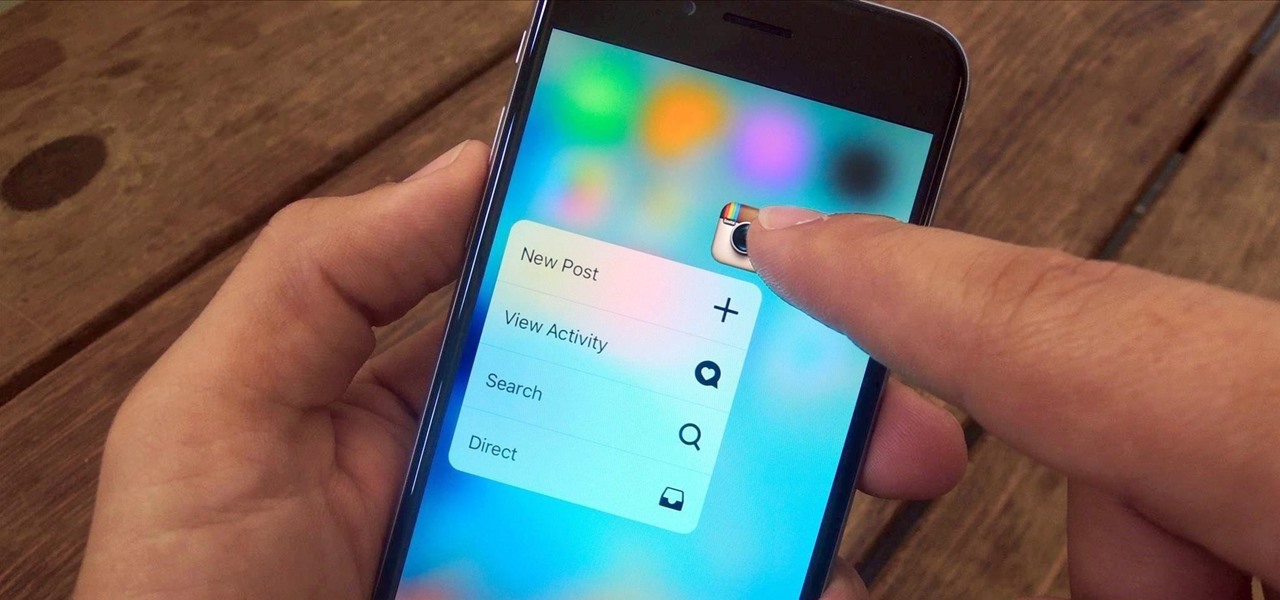
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Video: . Project Overview

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.
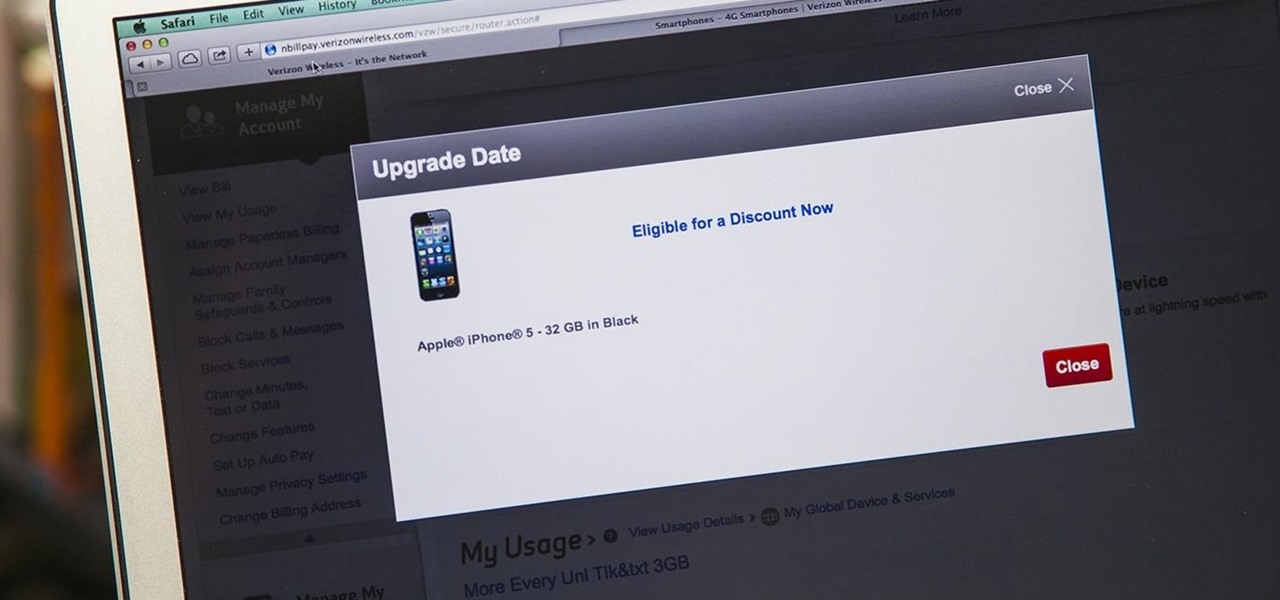
iPhone 6 pre-orders begin on September 12th, with the devices set for sale on the 19th. If you're ready to pick one up—no matter if you're a loyal iPhone user or an Android user about to make the switch—now is the time to check your upgrade eligibility.
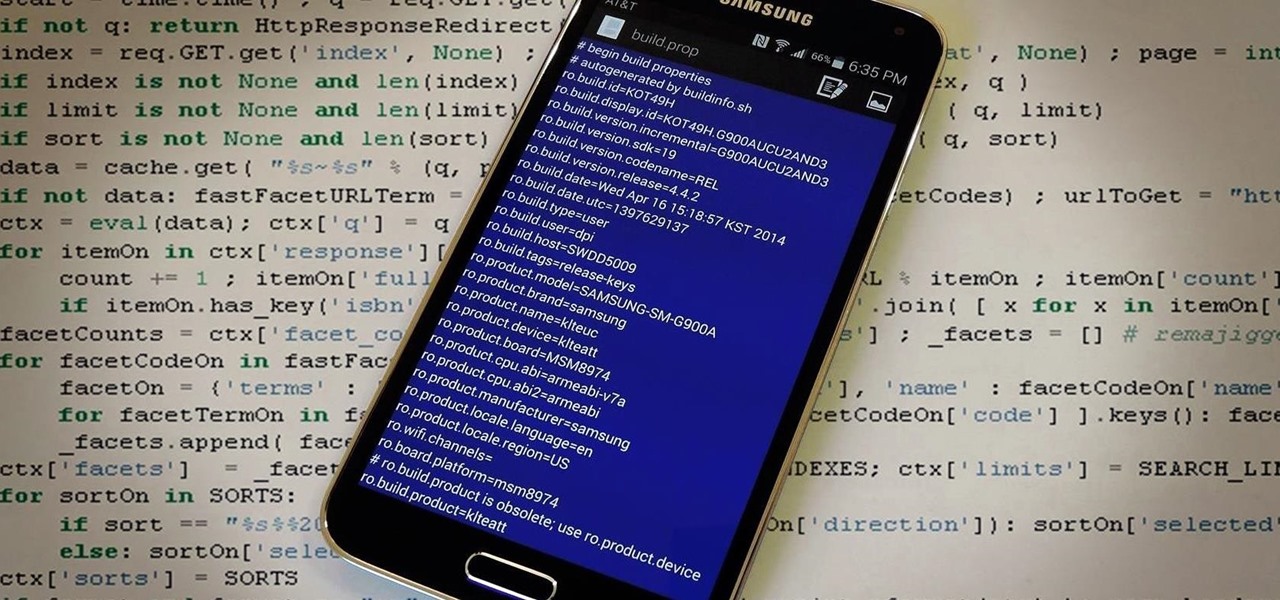
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker wannabees!

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.
To test how fast your internet speed is an intermediate level skill. Start by picking an internet speed test. You can use Google or another search engine to find one. A service that is recommended in the video is DSLreports. This site does not require you to know a lot of information about your service. To test your speed start by picking a city that is near to you. Then shut down all tabs and every application that you have running. It's important to do this on every computer on your home ne...
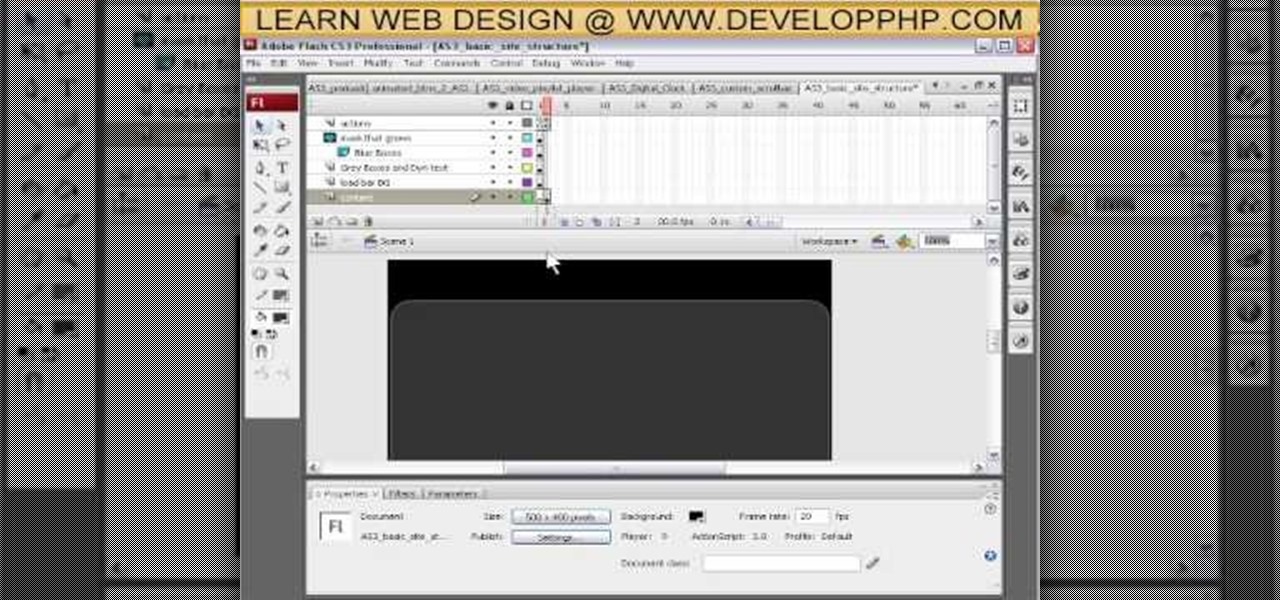
This tutorial is for anyone who wants to create their own Flash-based website, even those with little to no coding experience. You're shown how to incorporate animations, loader bars, and other interactive content into your website; as well as how to manage it all from the admin side.

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

Roofing is pretty dangerous work, maybe one of the most dangerous is residential construction. But if you're following all of the necessary safety guidelines, the chances of getting injured on the worksite are minimal. Working safe doesn't take long, and you don't have to sacrifice safety to do quality work and make a profit.

This video is dedicated to the residential construction workforce and focuses on how to safely install siding. It's intent is to help provide employees and employers with the tools to make the residential workplace productive and safe. It outlines a number of code requirements and will show how to work safely and how to meet all of the safety requirements during the siding phase of residential construction. The areas discussed in this safety video are job preparation, walk-around safety inspe...

Looking for a way to generate an unlimited amount of Pet Society coins? Look no further. This hacker's how-to will show you how to hack Pet Society's frisbee & ball games to generate more digital cash money than you could ever spend.
Want to generate experience and level up your Pet Society character the easy way? Watch this cheater's guide, which will show you how to hack Pet Society for all the EXP you could ever want.

If you have never dealt with wire color-coding then Old64goat takes you through a very elementary tutorial that will give you the helpful aid needed to deal with common household wires. The first cord that is reviewed is the three pronged cord. The color wires contained within it is the green wire which is the ground prong, the white wire which is neutral, and the black wire which is the heat. Old64goat then demonstrates where the wires are connected to on the prong. He even gives out helpful...
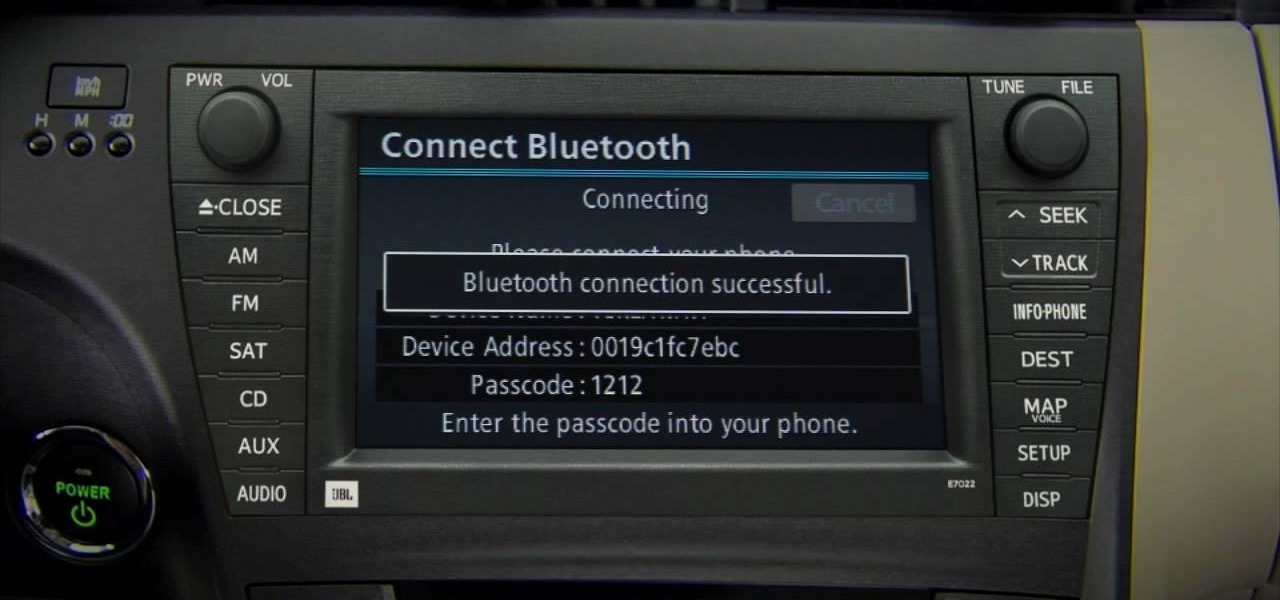
Learn how to pair a phone through Bluetooth with a 2010 Prius in simple steps. 1. You can connect your phone to the vehicle through Bluetooth without using any wires. 2. Press the 'Info Phone' button on the right side of the display screen, press 'Phone' now and press 'Yes' when prompted. 3. Now enter the pass code when prompted on your phone to pair it successfully. 4. You can pair more than a single phone by using the same process but you can use only one at a time. 5. You can also transfer...

Watch this video to learn how to cheat on a test with help from your iPod. Ask a trusted friend for their notes/answers the night before. Then at your computer, just type up their notes/answers, or the important parts, and then save it in your computer as "How to make Grandma's Secret Fudge Brownies.txt" . Now plug your iPod into your computer and click Start- My Computer- (someone's iPod- Notes. Now you will need a separate window. Click Start- My Computer. Now find "How to make Grandma's Se...

1. Shallow Bow You bump into someone in passing

Shown here is another video tutorial made possible through TutVid. In this video, you are learning the basics of Action Scripting in Flash. This lesson is titled "Action Scripting:101." Action scripting is one of the coolest thing about flash. The thing that makes flash special is the ability to make simple actions interactive. Flash possibilities are endless!

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

!!! READ THIS FIRST !!! - 4 april 2009 -

If you would like to use Google AdSense on your website, in order to make money from your site, you will need to get a Google account. Click "sign in" on the Google home page: www.Google.com. Next, scroll down to the bottom of the page and click on "create an account now. Fill it out. It will send you an email to verify your account. You'll need to open your email to confirm.
This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

Syncing your bluetooth earpiece to your BlackBerry device can be tricky. But pairing your bluetooth enables BlackBerry with your earpiece is actually quite easy. Best Buy has answers. The Best Buy Mobile team explains how to connect a Bluetooth earpiece to your mobile device. See how to access connections set-up on your Blackberry and also see how to wear a Bluetooth headset.
This six-part video tutorial, goes over how to make beats in Adobe Director. The six different videos go over the following: