With the prestige appeal of its original programming and relatively low subscription price, Apple TV+ is one of the more appealing streaming options out there — and you don't need an Apple device to subscribe and watch movies, TV shows, sports, and other Apple TV+ content.

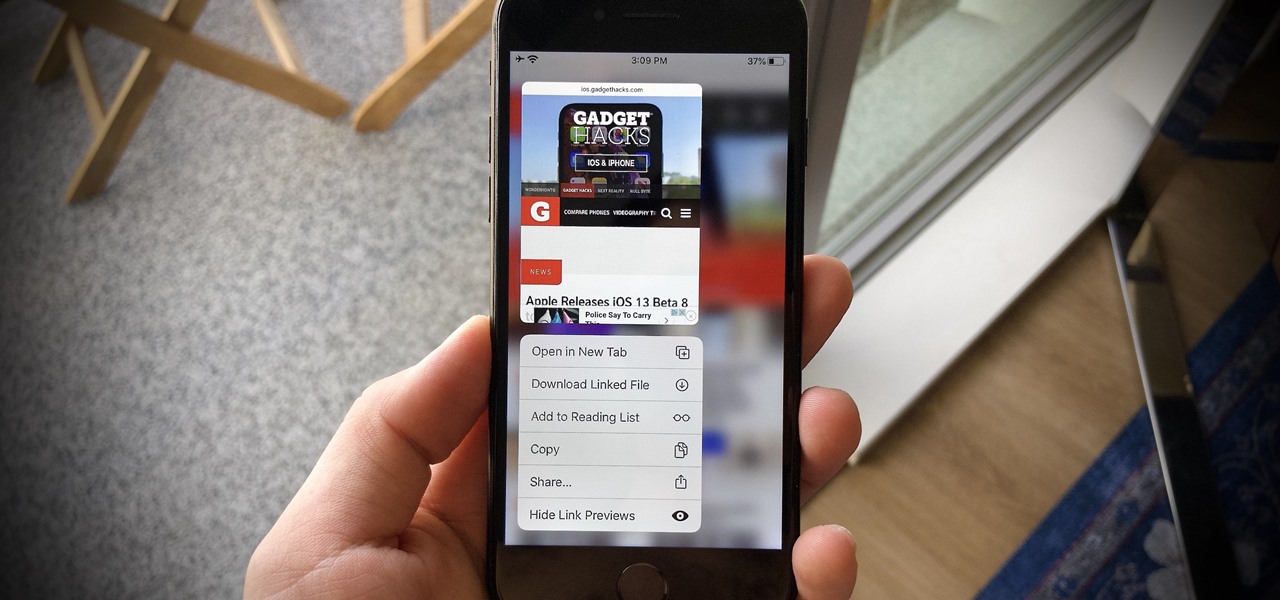
Apple's Wallet app lets you store boarding passes, concert tickets, gym memberships, vaccination cards, movie stubs, rewards cards, insurance info, student IDs, and more in one place on your iPhone, and you just double-click the Home or Side button to access them. Unfortunately, many cards and passes are not officially supported — but that doesn't mean you can't add them.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.
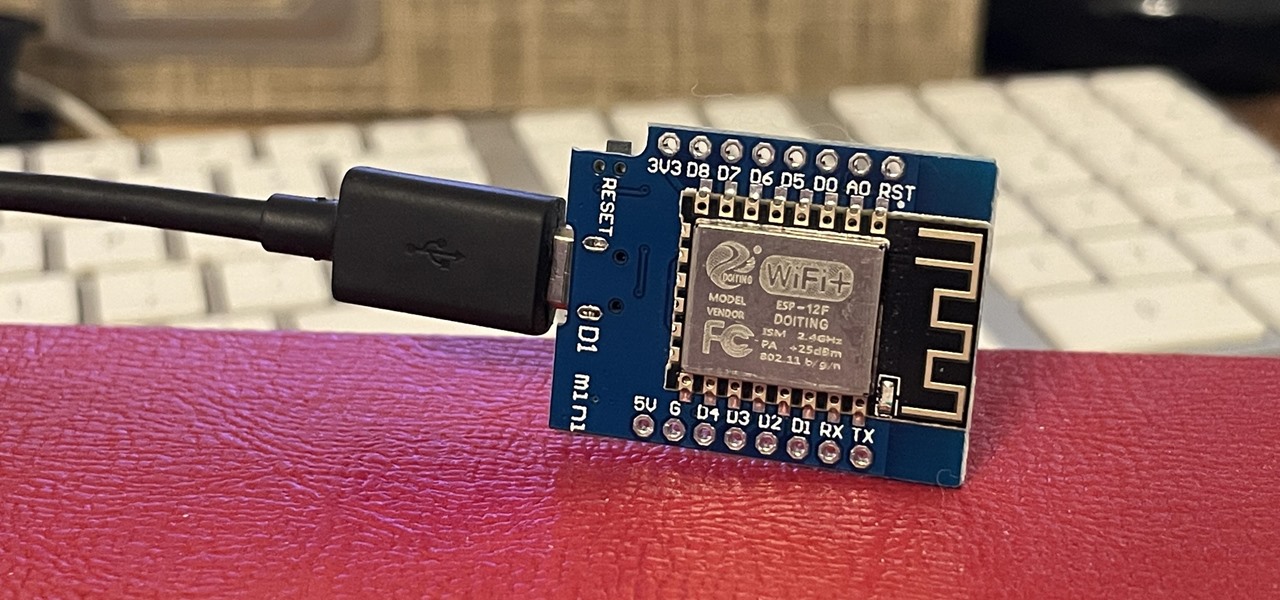
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

MicroPython is an exciting language to use on ESP8266 boards and ESP32-based microcontrollers, but it doesn't always include all of the libraries you'll need for a specific project. This issue is less of a problem, thanks to the upip package manager.

Get your holiday shopping done early with these deals on software, e-learning classes, and gadgets. These Cyber Monday goodies include something for everyone at a can't-miss additional 20–70% off sale prices.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

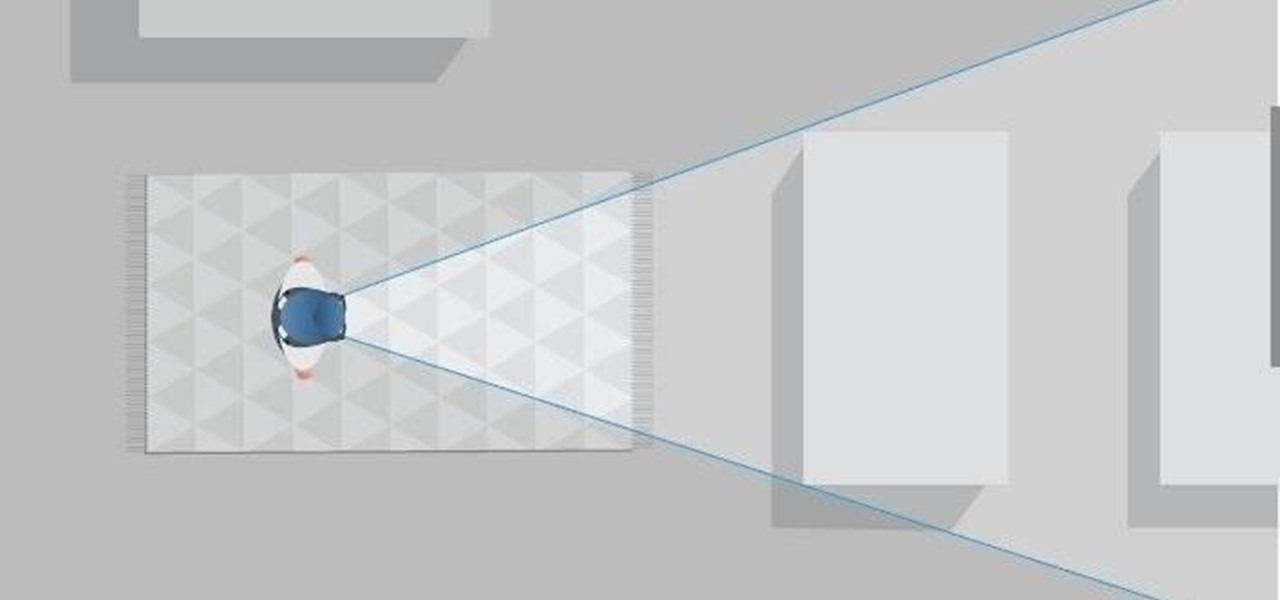
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

From the iPhone X onward, the Side button has taken on many of the functions associated with the Home button, such as summoning Siri, pulling up the AssistiveTouch shortcut, and more. So if you've finally ditched your Home button iPhone for the latest iPhone 11, the process of shutting down and restarting is something you'll need to learn all over.

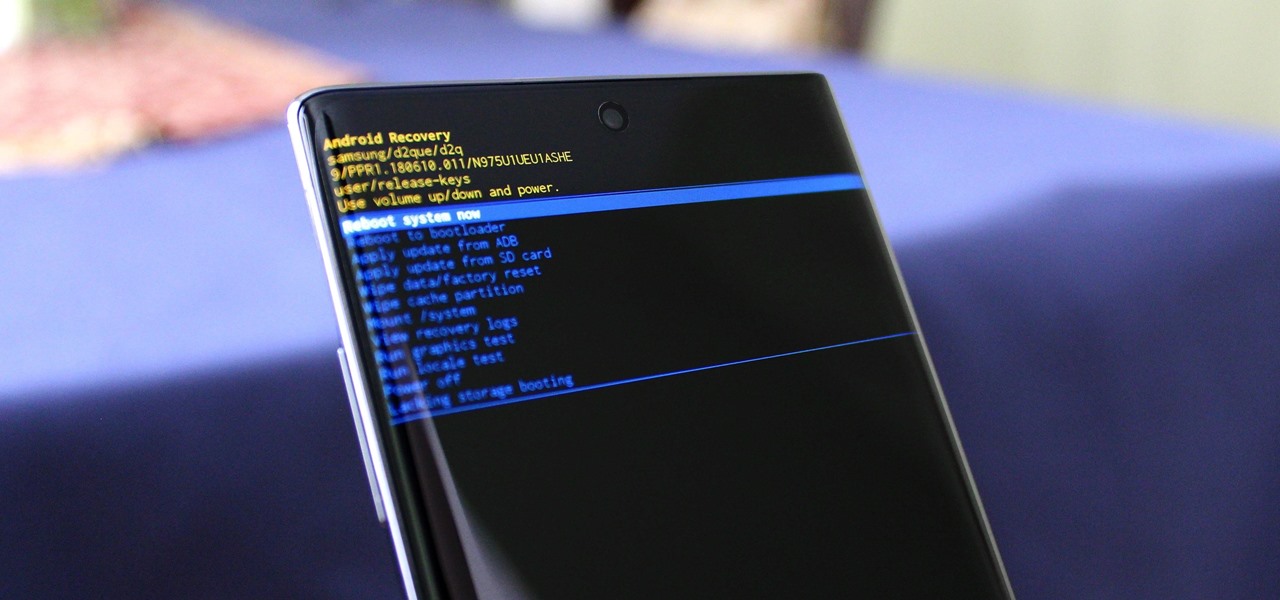
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.

Apple's iOS 13 is nearly here. After four months of beta testing, the latest iPhone software update promises over 200 brand new features, like system-wide dark mode and an overhauled Reminders app. That said, it'll be shortlived, as Apple plans to release iOS 13.1 as a supplemental update just 11 days later. In fact, the company just seeded developers the fourth beta for iOS 13.1 today, Sept. 18.

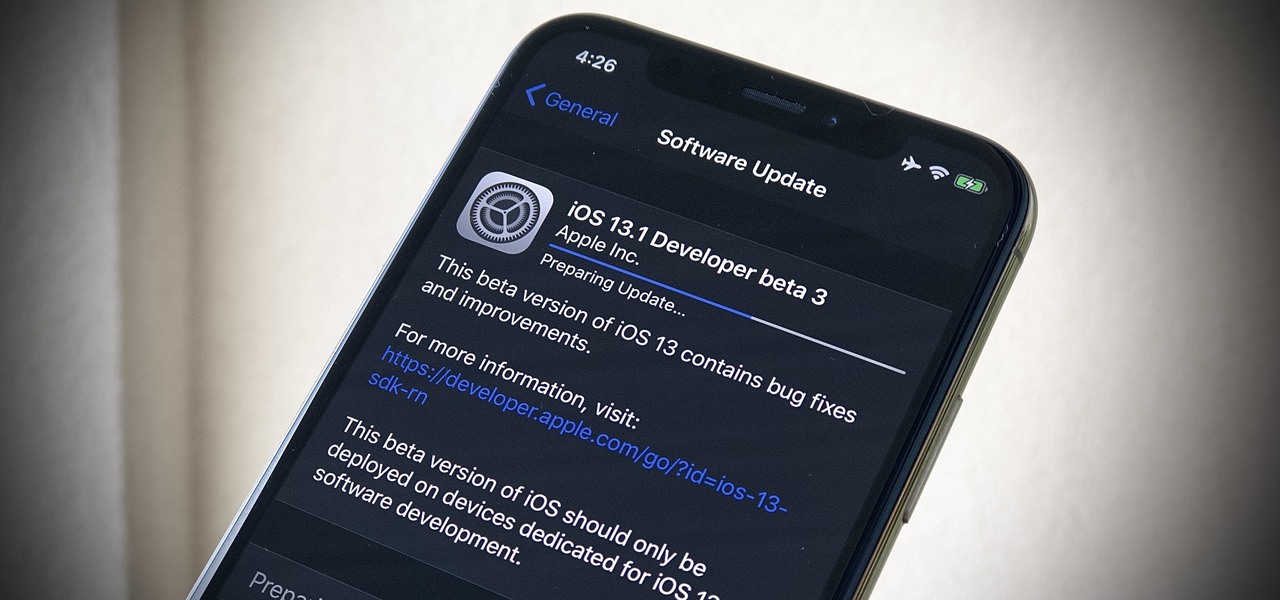
Yesterday showed us our first look at the iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. But it wasn't all about hardware. Apple also released the iOS 13 Golden Master, making iOS 13.1 the main focus for us beta testers. Now, Apple just seeded the third public beta, following yesterday's release of 13.1 dev beta 3.

It's a big day for Apple. First, the company announced its new suite of phones: iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. Then, we get the iOS 13 Golden Master, the beta version of iOS 13 that will eventually release to the general public on Sept. 19. Now, it seems the company has dropped the third developer beta for iOS 13.1, set to release to all compatible iPhones on Sept. 30.

Apple has pulled quite the headscratcher in anticipation of its big iPhone unveiling next week. Its latest iPhone update, iOS 13.0, is just on the horizon, going through eight beta versions so far. And yet, before that software's official release, the company has started beta testing iOS 13.1, with no explanation why. And the second public beta for iOS 13.1 is now out, so let's see what's new.

When Apple takes the stage next week, we have no idea what version of iOS it will release. For months it seemed like a given that we would, of course, see iOS 13 seeded to our iPhones. Now, we aren't sure if Apple will tout iOS 13 or iOS 13.1, since the latter is now the focus of its beta testing. In fact, 13.1's second developer beta is now available to download and install.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

When it comes to building luxury cars, Bentley certainly knows what it's doing. However, when it comes to building an AR app, Bentley is looking less Continental GT and more Geo Metro.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

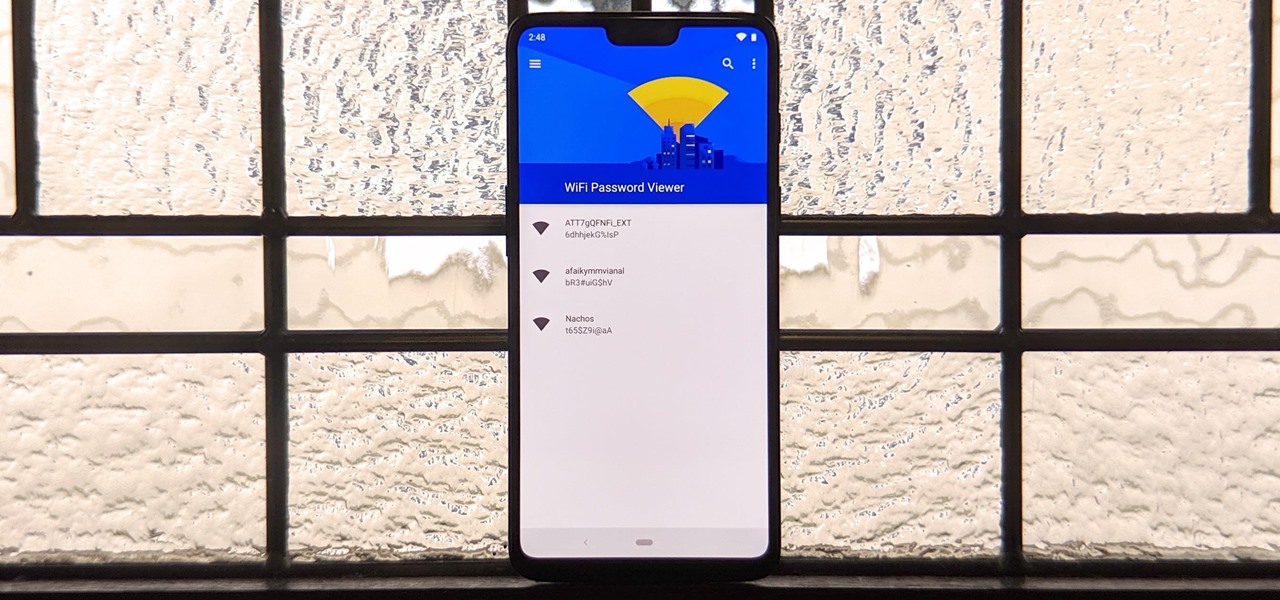
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

Last week at Mobile World Congress 2019, Google put an augmented reality twist on its annual Android Partner Walk via its ARCore toolkit.

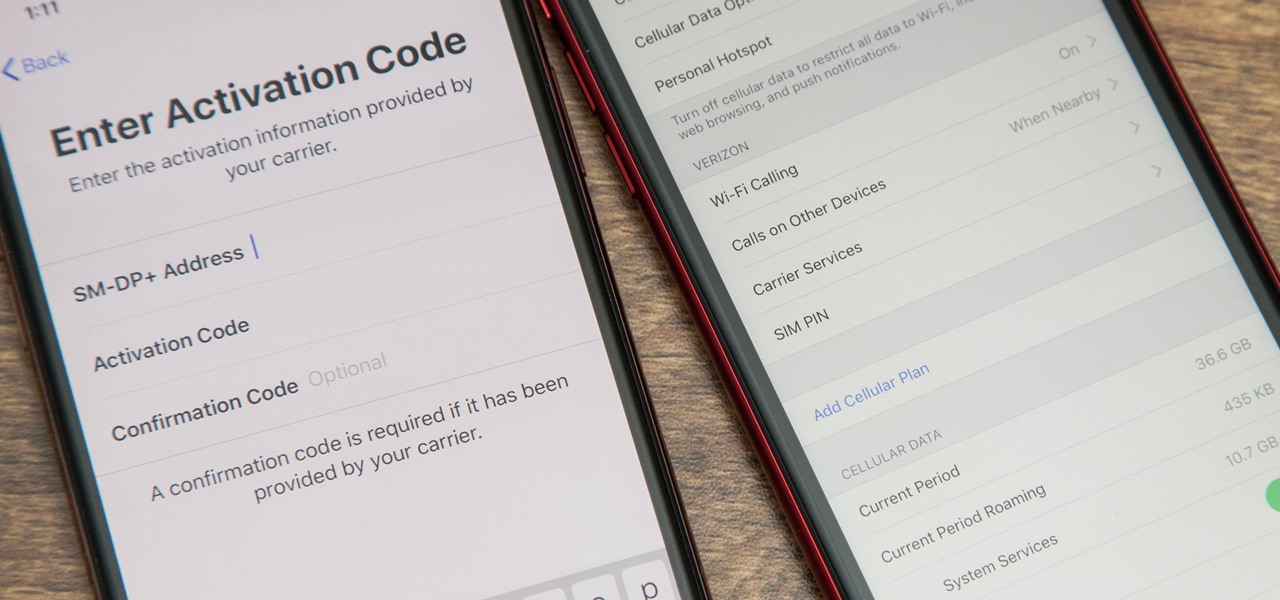
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

Augmented reality experiences for consumers, for the most part, are relegated to mobile devices at present, but creation and development of those experiences is still a province of desktop computers.

The arrival of Magic Leap One is tantalizingly close and, although the company has been saving the last details for launch day, a few of the more important details were found this week hiding deep in the code on Magic Leap's website.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to enjoy this feature.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

In late-2017, Snapchat debuted Lens Studio, a way for anyone to create their own augmented reality "world lenses" that can be shared to anyone with a Snapchat account. If you don't mind spending money, you can even create custom face lenses and basic overlay filters for special events. And while making lenses and filters have gotten pretty easy, distributing them is another matter entirely.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

With the big reveal of the Magic Leap One: Creator Edition in December 2017, and now the update on Feb. 13, 2018, we no longer have to speculate as to what the augmented reality headset will look like or when (in general) it will be available.