Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Google has been working on its voice recognition technology ever since the days when you had to call a phone number with a Silicon Valley area code to dictate your query. As you can imagine, things have come a long way in the decade or so that has passed, to the point where we talk to our phones as if they were a person nowadays.
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

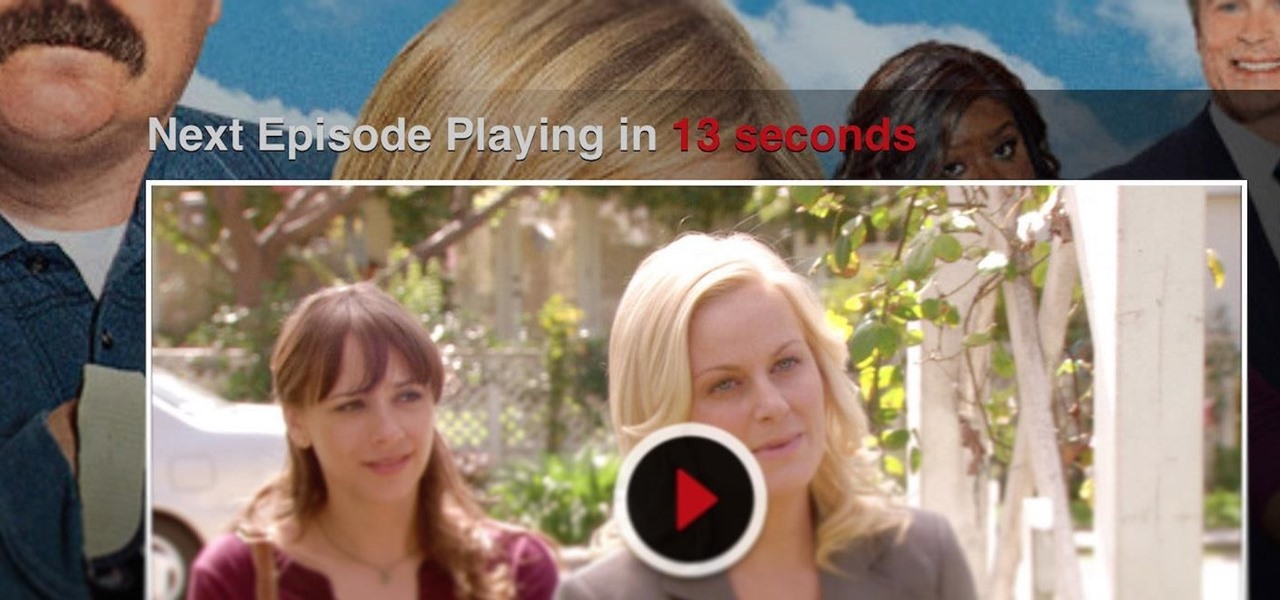
Cord cutters are changing everything about TV—the more of us that sever ties with cable, the more changes we start to see. In fact, viewing habits have already changed so drastically that waiting a week to see the next episode in a series is no longer acceptable, as binge watching has completely eclipsed this old-fashioned format.

Waking up can be a real struggle for some people. Alarms help, but most of them are so easy to turn off that you can shut them off while you're still half asleep and go back to bed, only to wake up in a panic as your realize you've severely overslept. Microsoft Garage wants to make you at least work for your lethargy with its new Mimicker Alarm.

Hello there Nullbyte users! This will be my first article here.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room for more useful functionality.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

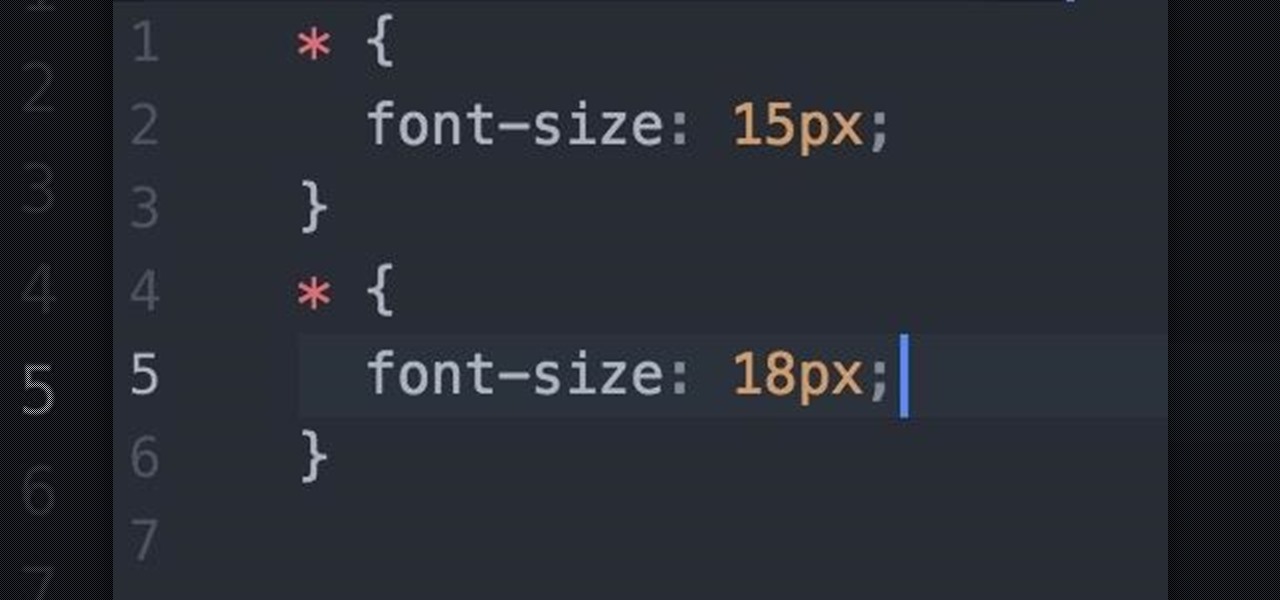
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

What's up guys! It's time to discuss strings in more detail. Review

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

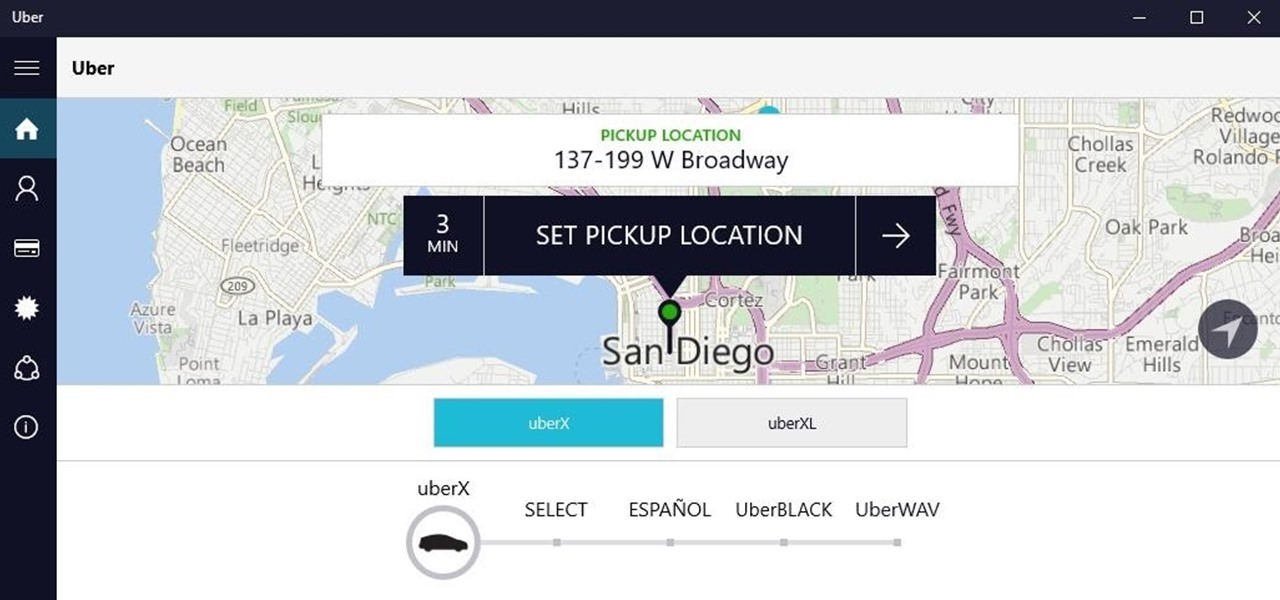
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

Cauliflower has become trendy again, and it's mostly thanks to the low-carb crowd who use its mild flavor and soft texture as a replacement for things like rice and pizza dough.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

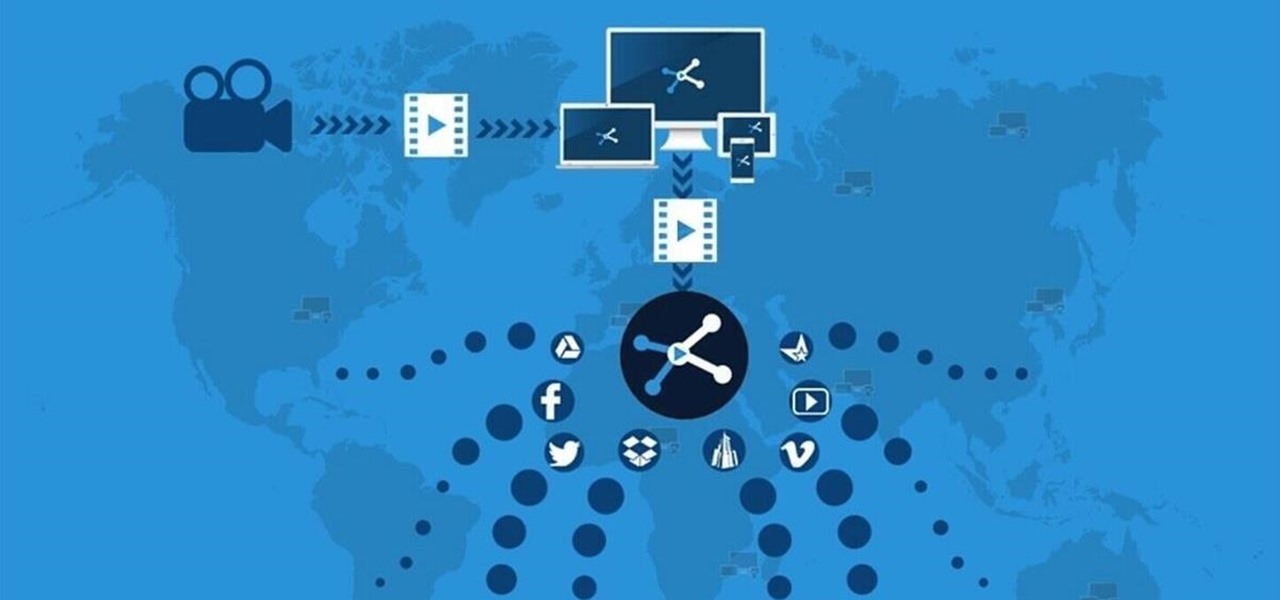
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.