
How To: Hook Web Browsers with MITMf and BeEF
Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!


Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

Believe it or not, not every Apple lover is willing to make the commitment and fork over $350+ for the Apple Watch. Like many others, I'm not willing to put that much faith into Apple's first attempt at wearable tech.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.
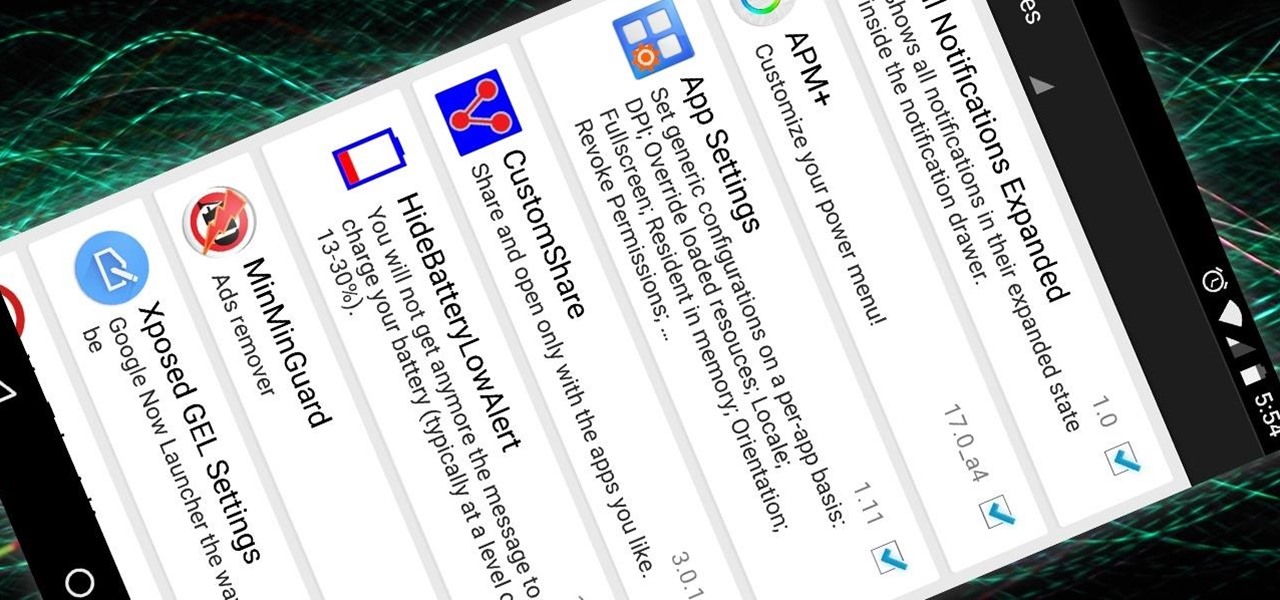
Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.
Most custom ROMs are built from the freely-available source code of AOSP, so they share a lot of common ground with stock Android. The difference, though, is the fact that Google adds many minor tweaks and finishing touches to AOSP while creating the version of Android that ultimately comes pre-installed on Nexus devices.

While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast way to capture and send photos without having to waste time unlocking your device.
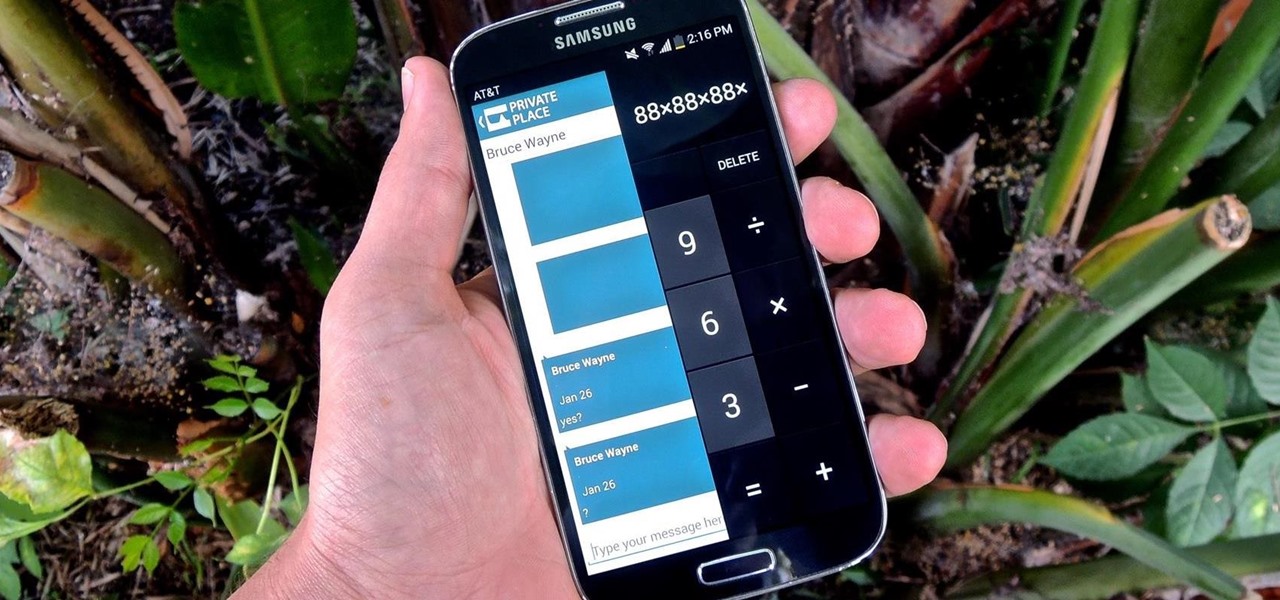
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.
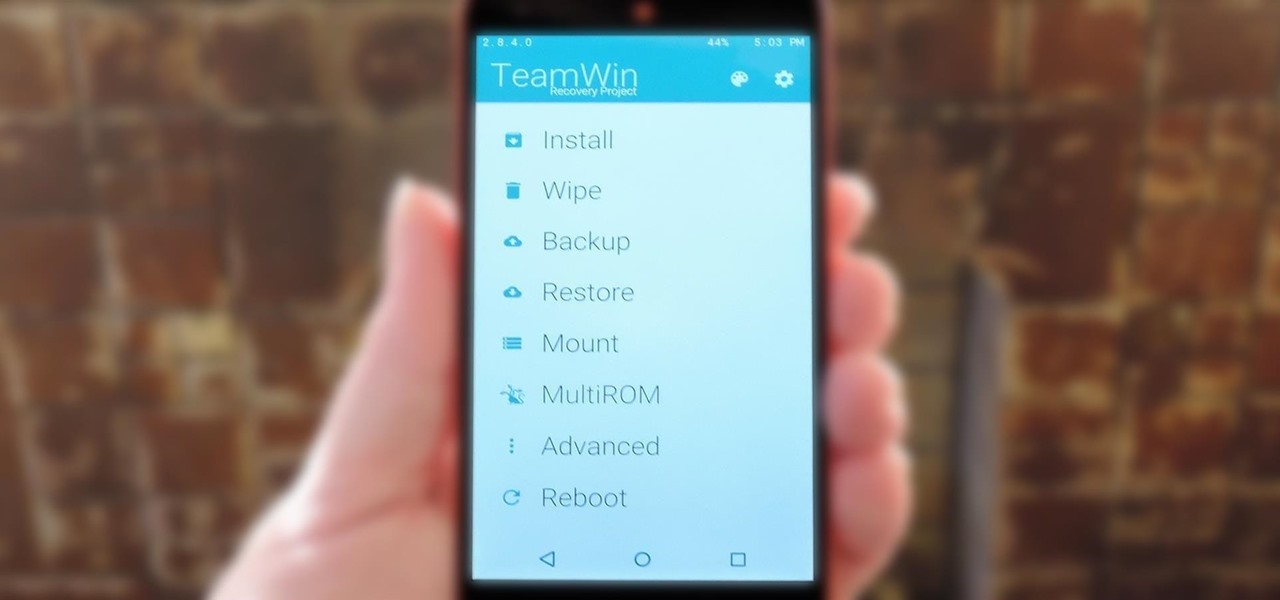
TWRP is hands-down the best custom recovery out there. Its interface, on the other hand, is... well, let's just call it utilitarian. The guys over at Team Win made sure that their product was robust, functional, and easy-to-use, but they didn't put a tremendous amount of effort into polishing the looks.
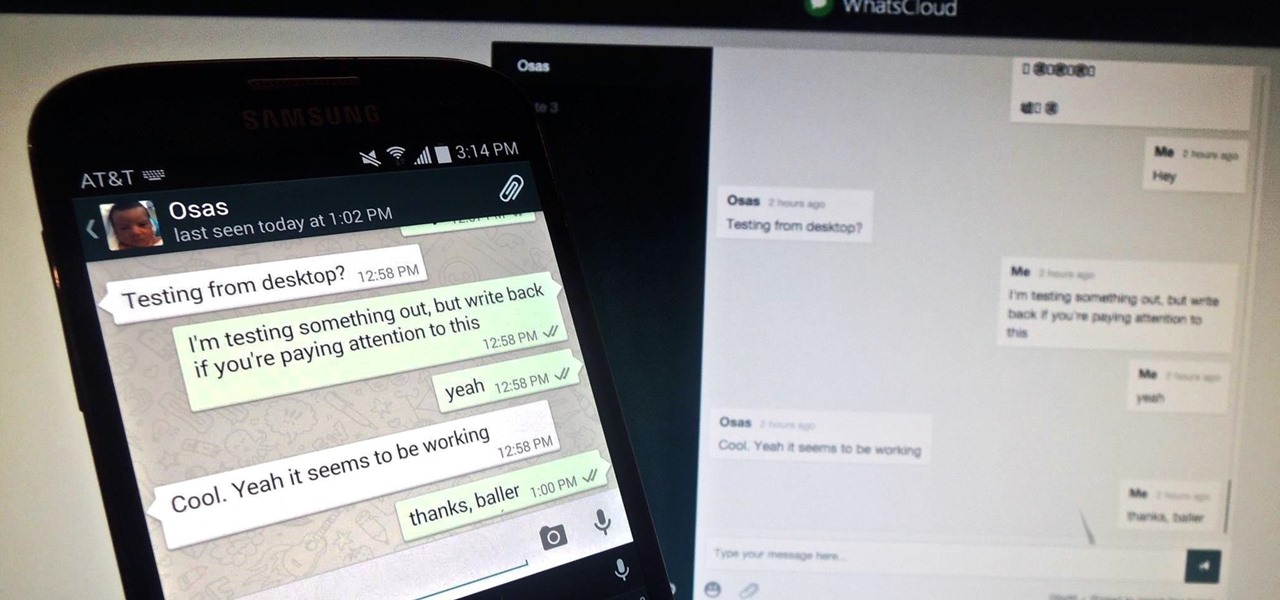
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.
Revised Version, Gallery pictures of the Ambassabank have been removed since XCL 2.0 has been released.
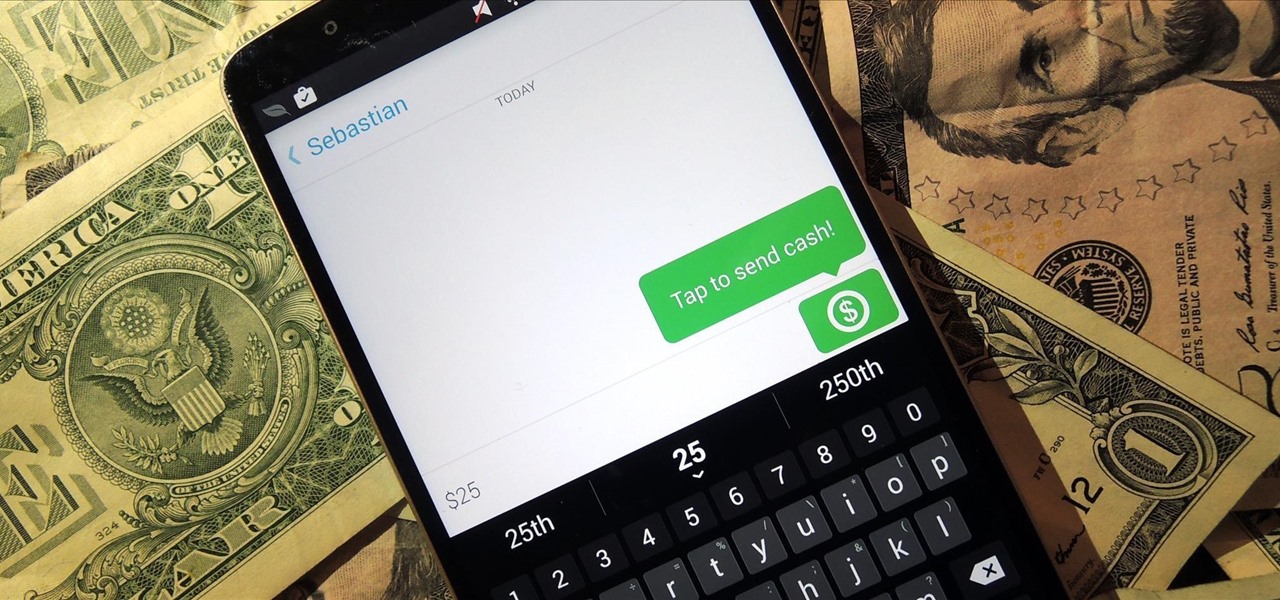
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.
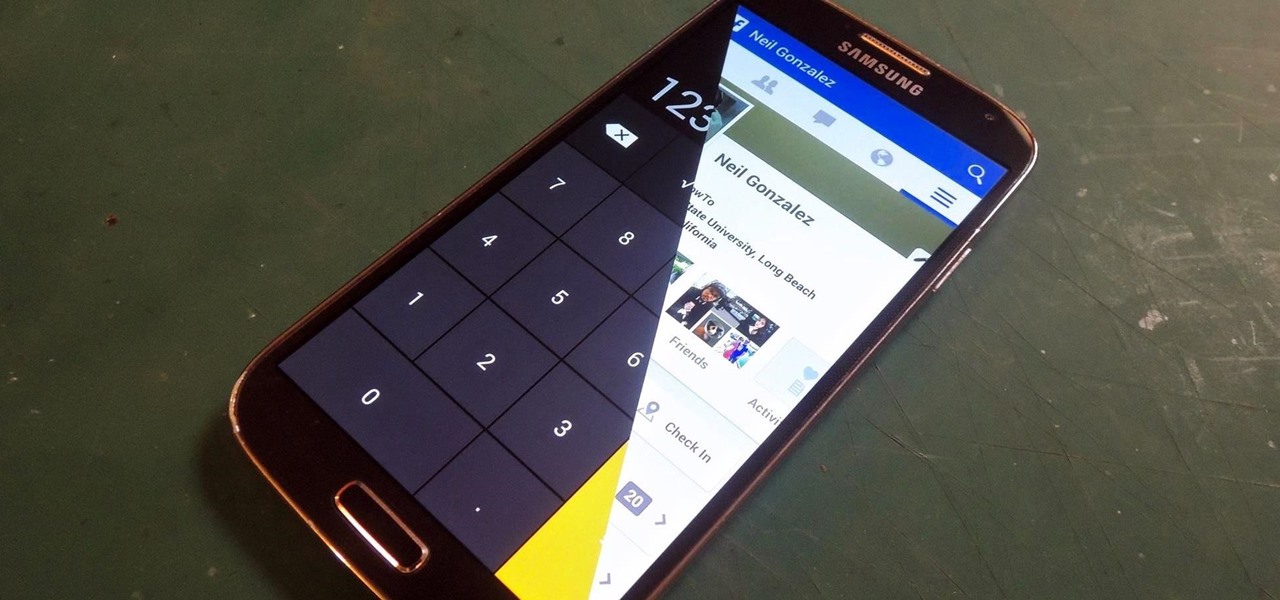
Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.
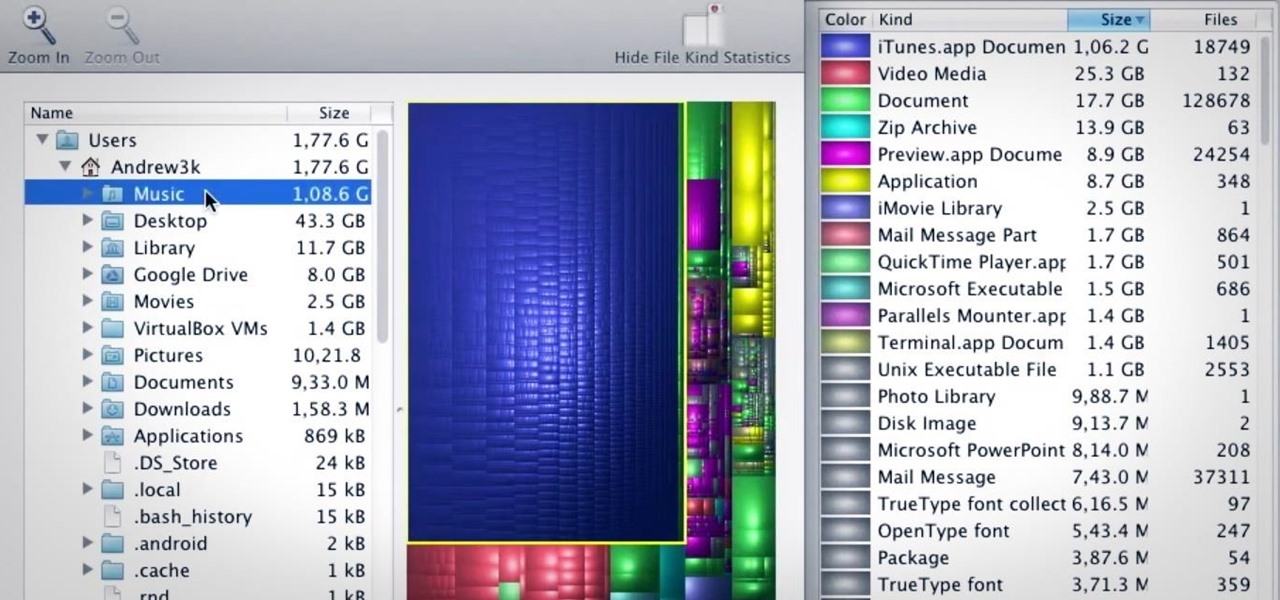
I love my MacBook Air, but the fact that it runs on only 128 GB of flash storage causes me to move most of my files to the cloud. I don't mind having to be connected to the internet in order to access my files, but it's definitely a hassle trying to figure out which files I should move in order to save the most space. Usually, I don't even bother even trying until I see the dreaded "Your startup disk if almost full" warning. Currently, the only real way to find your biggest files in Mac OS X ...
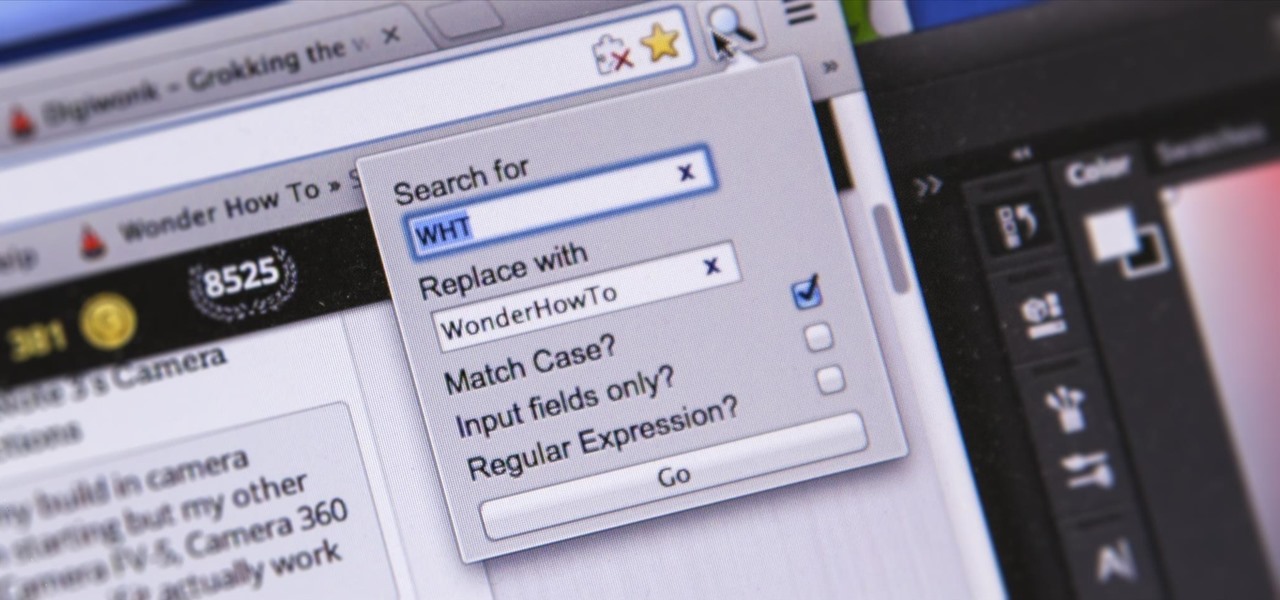
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

Unless you're waiting in line for your iPhone 6 or iPhone 6 Plus, it's a sure bet that you'll be sitting by at home for your new device to get delivered today.

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Buried deep in the code of many Google apps is a set of debugging options. These options, which are designed for developers to help test the way their apps interact with Google's own, are normally hidden from view.

Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.
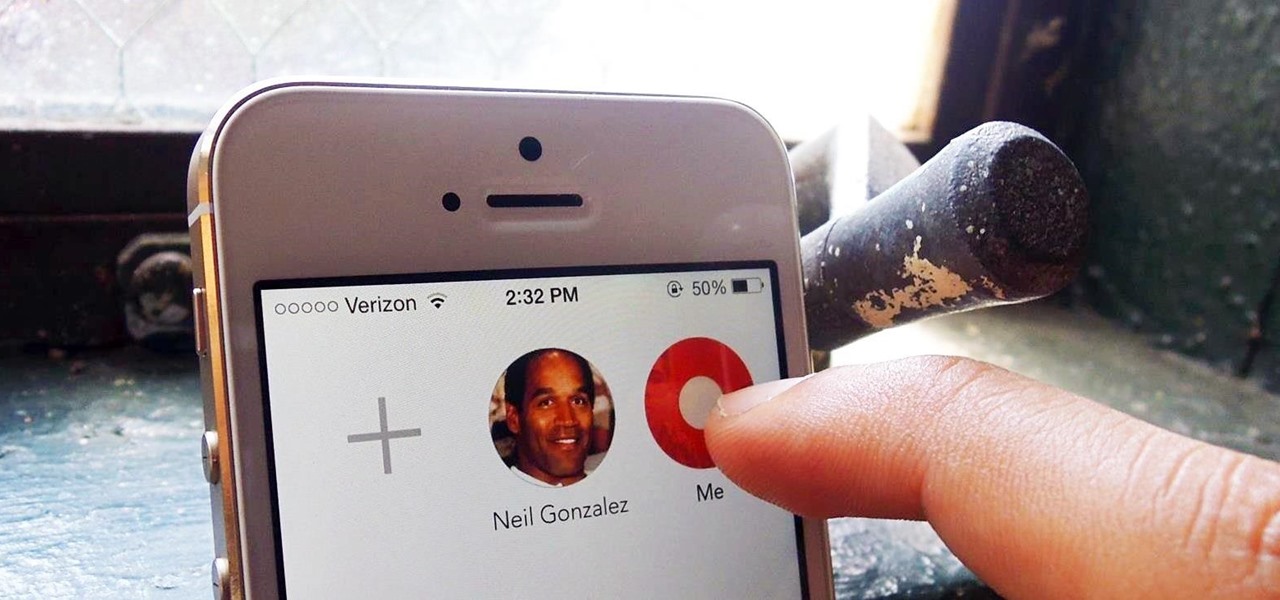
Apple is bringing one of the biggest updates ever to its Messages app, including a feature that will allow users to send audio messages back and forth with the press of a button. Goodbye, voicemail.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.
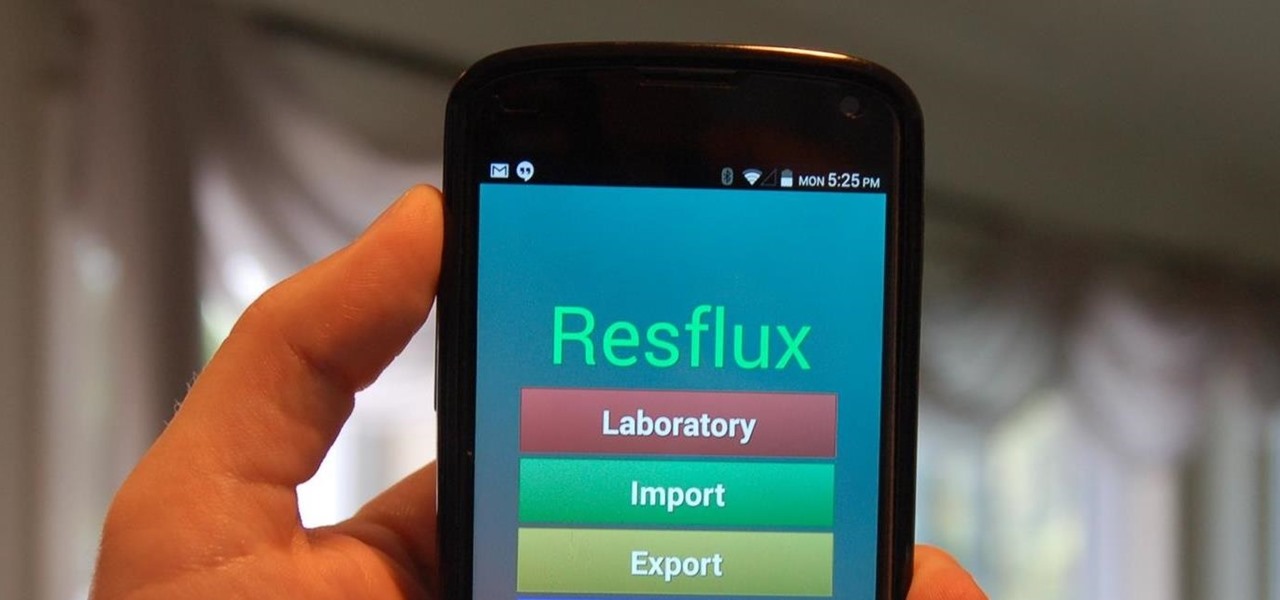
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.
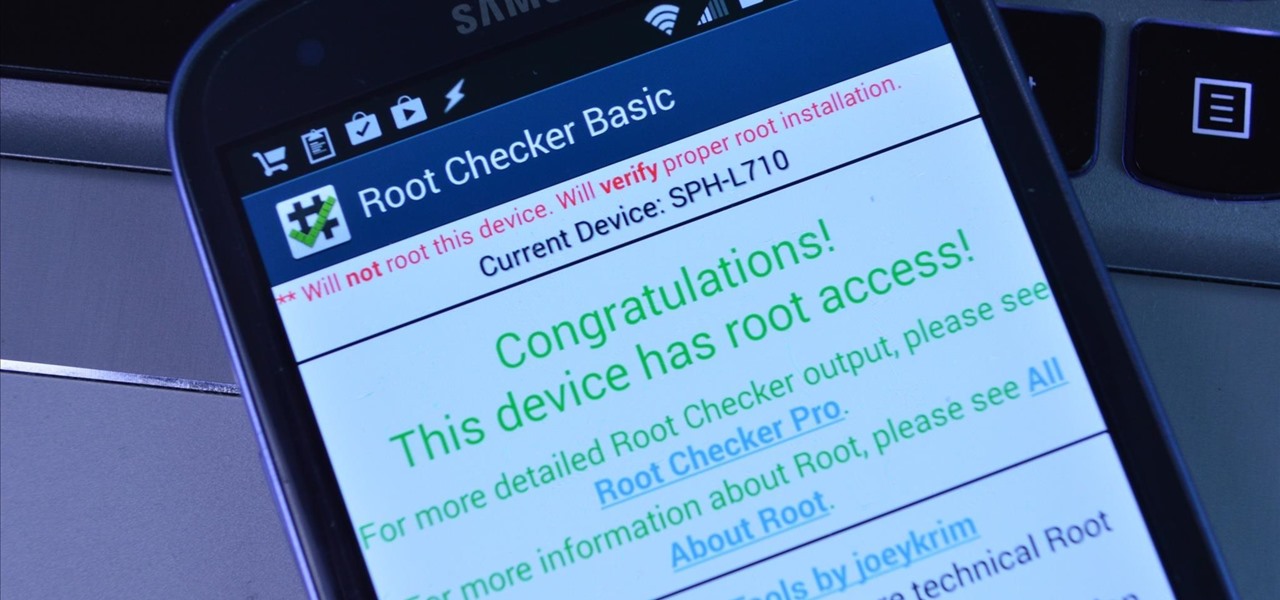
Rooting an Android device used to be a nightmarish labyrinth of .zip files and command prompts, confusing seasoned modding veterans and newbies alike. Thankfully, the process has gotten simpler over the years, with various "one-click" rooting tool kits surfacing and working for nearly every major Android flagship on the market.

Last week, I showed you a peek at the not-yet-released Galaxy S5 Active, the more rugged version of Samsung's current flagship. The man behind those leaks, TK Tech News, has now brought another goodie from the device, and it's one we can have on the Galaxy Note 3.

If you have Android KitKat, you're fortunate enough to be able to use the new Google Camera, which has tons of great features, including Photo Sphere, Tiny Planet, Panorama, and Fisheye. With so many photo options and no additional hardware needed, it's hard to not to like this camera.

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.