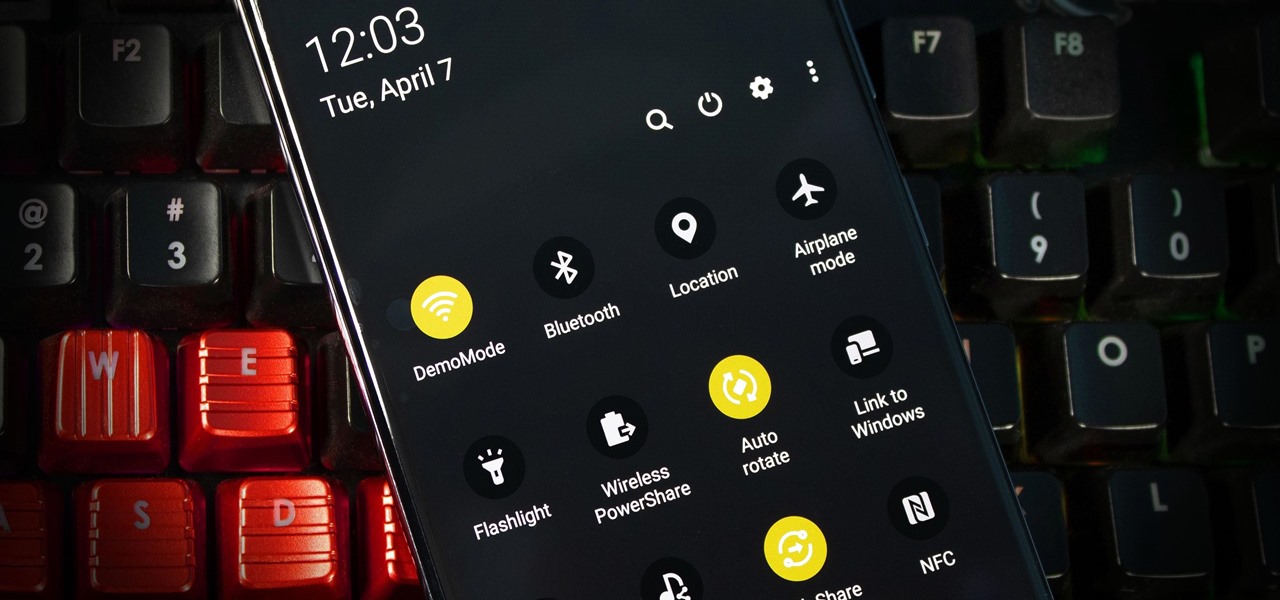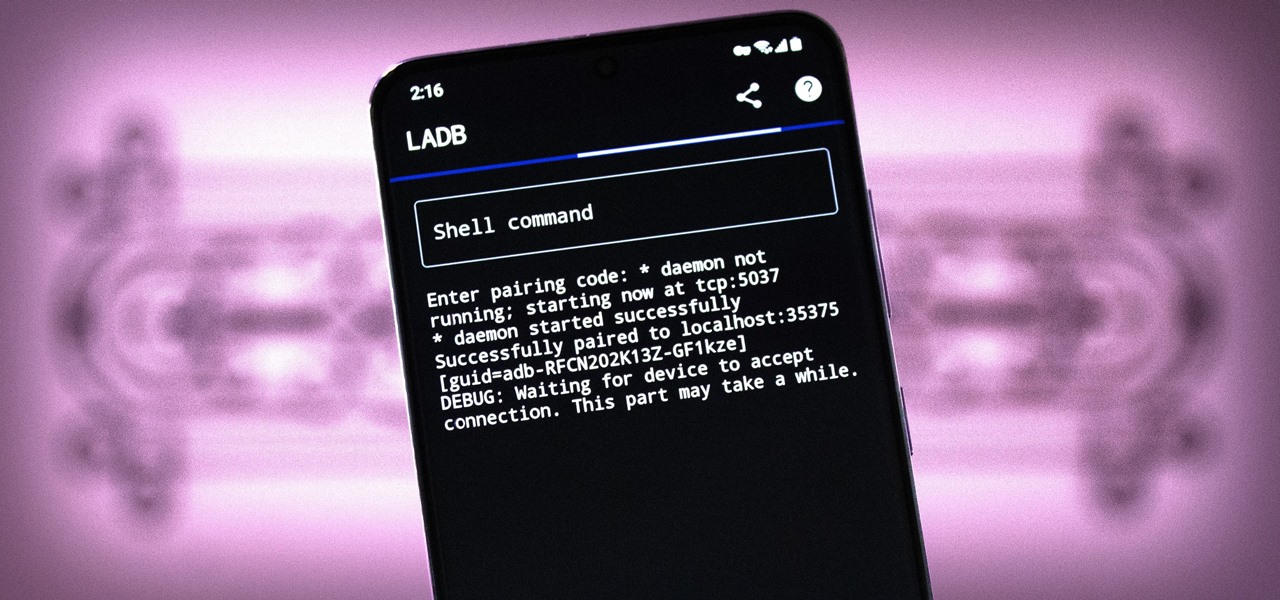
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

This holiday season, give yourself a gift that will keep on giving: a new web development skill. Whether it's to secure lucrative freelance work in the new year, bolster your résumé, or have fun with some frankly outrageous discounts on online course bundles right now (up to 99% off), there's nothing better you can do with your free time. Your future (pro coder) self will thank you.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

The gesture navigation introduced with Android 10 worked wonders by giving you more of your screen and less tapping. Android 11 offers the option to fine-tune the back gesture sensitivity for your screen's left and right sides. However, the issue still stands for people who like to use the left swipe menu within apps to open hamburger style menus.

After teasing the feature in Android 10, Google finally added proper native screen recording to Android 11. But when you start a capture, you'll see a small red indicator in your status bar as long as recording is ongoing, which can really distract from your video. Thankfully, it can be removed with a little ingenuity.

One of the biggest bummers about Netflix is the inability to create different lists for your favorite movies and TV shows. Instead, you're only able to lump titles into the single default "My List," and that can be impossible to browse. It doesn't separate titles into categories or genres, and titles are arranged for you automatically, so there's not much room for customization.

Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

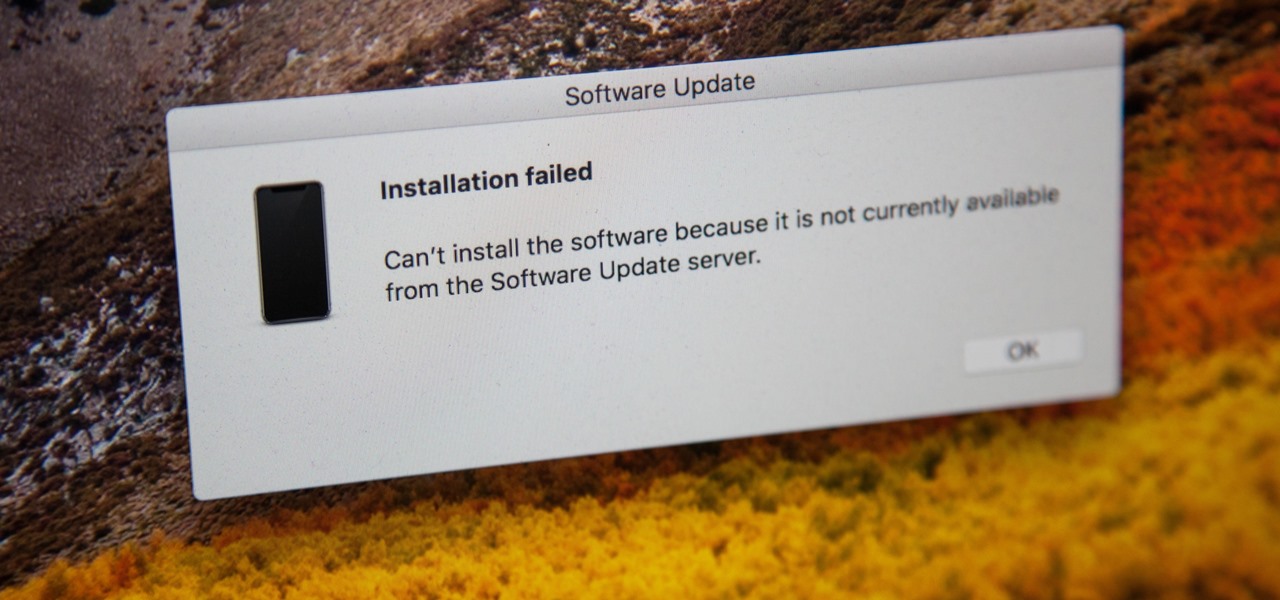
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

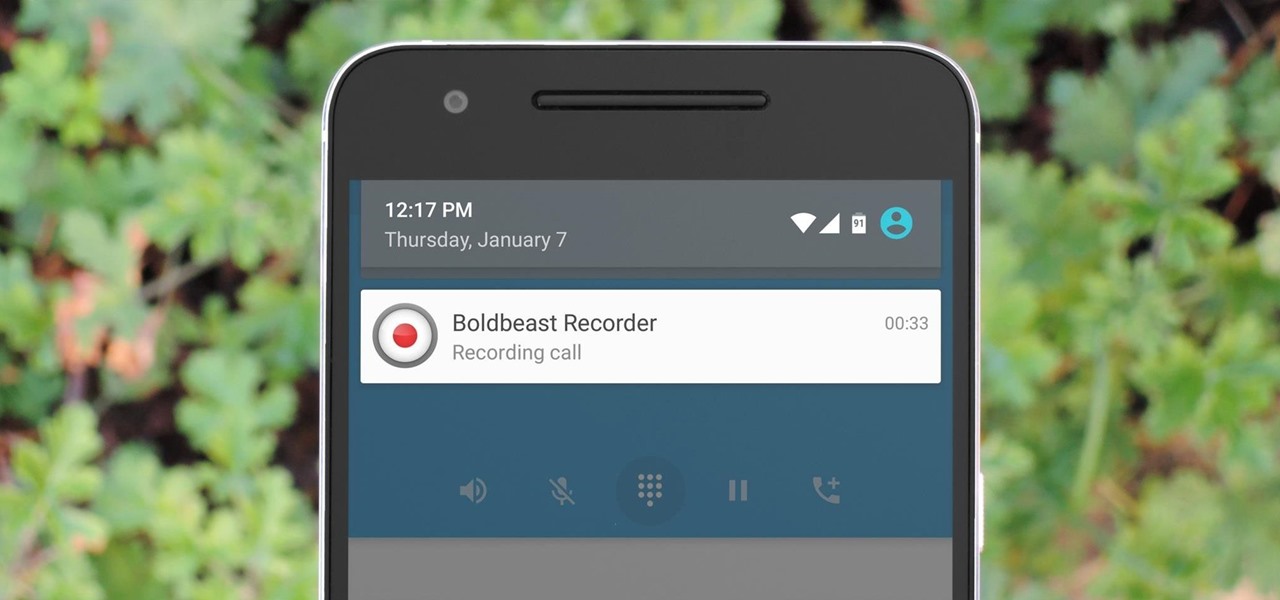
There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

A vending machine is an invaluable yet totally frustrating piece of equipment. It's a godsend whenever your tummy's growling or you need an ice-cold drink on a hot summer day. But when something gets stuck inside or the machine flat-out malfunctions, it quickly becomes your archenemy. And when you're broke, it's basically just one big tease.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

In this tutorial, we learn how to take apart an Xbox 360 wireless controller for repair. First, grab your controller and grab a few different sizes of screwdrivers. After this, turn your controller over and start to remove all the different screws from their spots and place them onto a table where they won't fall. now, take the bar code off and take off the final screw that is on the inside. After this, you will be able to take apart your controller and fix whatever issue you are having with ...

In this how-to video, you will learn how to use placemark visuals to make a perfect landing in Flight Simulator X. Along each runway, there are lights that range from red to yellow depending on your range. 2 reds and 2 yellows or 2 yellows and 2 reds mean that you are on the correct glide path. The lights will change according to your height while approaching the runway. Try and maintain the correct color code as you start to land. Keep on trying until you get it perfectly. Viewing this video...

To take apart the controller you will need a Torx t8 screwdriver and a Philips head screw driver. There are 6 obvious screws on the back of the controller and there is one hidden and one behind the bar-code in the battery compartment on the back. Remove all of the screws, push down on the right and left triggers and pull the controller apart. Pull the board apart and don't worry you won't break anything unless you are really rough. Remove the rest of the buttons, they come out just by pulling...

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Get a crash course on HScript Expressions, Variables, and Attributes in Houdini 10. If you don't even know what this means, then you probably need to check this video tutorial series out. Understanding how to massage data in Houdini is key to giving yourself the creative edge and allowing you to unleash mind-blowing visual effects. This 18-part video series covers a variety of simple yet essential weapons in your arsenal including Global, Standard and Custom Variables to Math and String Modif...

Want to do some web designing in Flash? This tutorial will walk you through the basics of creating a button in Flash CS4 (though this tutorial will work in earlier versions of Flash as well). They will first walk you through the basics of converting text to a button symbol and then go more in depth by showing how to link the button through the more advanced action tools. This tutorial then takes you into the basics of coding in flash that will result in a working button that will link to an o...

This scorpion toy was constructed by Make Magazine with a Twitchie Robot Kit. If you're afraid of real life scorpions this friendly toy might help you get used to them. His plush body is made from some fabric aiming to make him look like an Arizona bark scorpion, which are tan/yellowish/translucent. Twitchie is Arduino powered and comes pre-programmed, so it's an excellent kit for beginners in robotics, because no programming is required! You can download and modify the code if you want, and ...

Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

If you've ever used your iPhone's hidden Field Test mode to view your signal strength in decibel-milliwatts, locate the tower you're connected to, or find out the radio frequency in use, you no longer have to dig through all of the confusing-looking data every time you need to check. Apple updated Field Test's interface in iOS 15, and one improvement gives you more control of the Dashboard.

Consumers who haven't already delved into the interactive wonders of augmented reality are about to be pushed into the immersive waters by market forces.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

Safety means something different to everyone, but everyone wants to feel safe. For many, the best way to feel safe is to have something external that offers that sense of security, whether it's an alarm system, a friend on standby, or just something that helps you feel in control.

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.

Apple released the fourth public beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes three hours after the fourth 14.5 developer beta, and includes references in its code to a new "City Charts" playlist feature in Apple Music.

As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality?

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.