
How To: Tie a retraced figure eight knot
How to tie a retraced figure eight knot is shown in this video.


How to tie a retraced figure eight knot is shown in this video.

Learn how to tie dye a shirt. This is a fun activity for kids and adults.

This video shows you how to tie eight useful knots including the figure 8, rolling hitch, clove hitch, bowline, square knot and a few more.

This is a video of how to make a surgeons' knot when tying a quilt.

This video demonstrates how to import XML code from the Internet into Movie Maker. The video shows you how to find the XML code on the Internet, how to download it, and how to import it into Movie Maker.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.
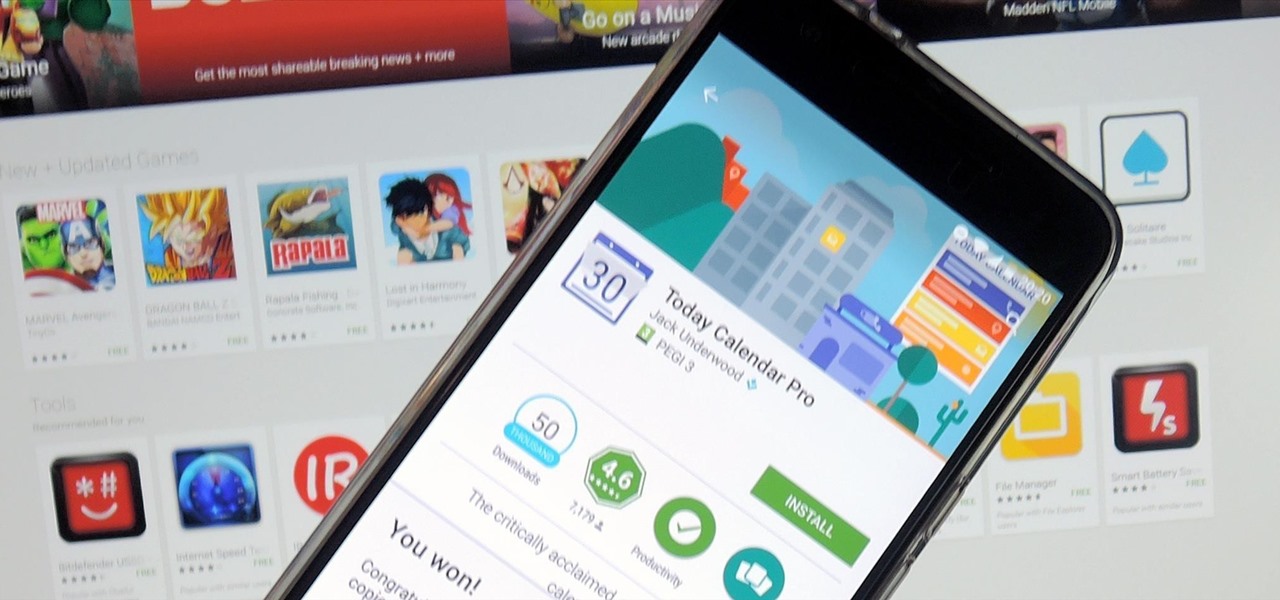
If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

This video tutorial demonstrates how to tie a figure eight knot. You can use this knot as an alternative to the overhand knot for starting and ending your hemp jewelry pieces such as necklaces, bracelets, chokers, and anklets.

A step by step video tutorial on how to tie a vertical larks head knot.

A video tutorial on how to tie a square knot to make hemp macrame jewelry.

A video tutorial on how to tie a switch knot and make hemp jewelry. This knot can be used to make various pieces such as necklaces, chokers, bracelets, and anklets.

A step by step video tutorial that teaches how to tie an alternating Larks Head knot with loops.

A step by step video tutorial on how to tie a continuous half hitch spiral knot. You can use this knot to make various types of hemp macramé jewelry such as necklaces, bracelets, chokers, and anklets.

A video tutorial on how to tie a pretzel knot AKA Josephine knot for hemp jewelry. Easy step by step instructions.

A video tutorial that shows how to tie a half square knot AKA spiral knot. You can use this knot to make various types of hemp jewelry.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Video: . This is how is replaced the outer tie rods on a 2008 Pontiac Grand Prix. Most late model GM vehicles will be similar to this Grand Prix. 97-03 Grand Prix, 04-08 Grand Prix, 00-05 Monte Carlo and Impala, 97-03 Regal

The '90s bigger than ever, a day-to-party outfit is, once again, a tie-dye tee with a choker. If you want to make it modern, then just pair it with a Rainbow Loom band. But before you do, sit back, relax, because here's the first installment of Debrief DIY: how to make a tie-dye T-shirt.
If you want to embed a video on your website and customize the player so it doesn't look like crap, you've come to the right place:

A sophisticated knot invented by the one and only Elliot Truelove. Difficulty level 5/5. This knot isn't for little boys, it's for lady killers.

How to tie the intricate and multi-layered Fishbone knot for your necktie. Easy to follow animated video shows you how.

Here's and animated video showing you how to tie the amazing and stunning Trinity knot for your necktie.
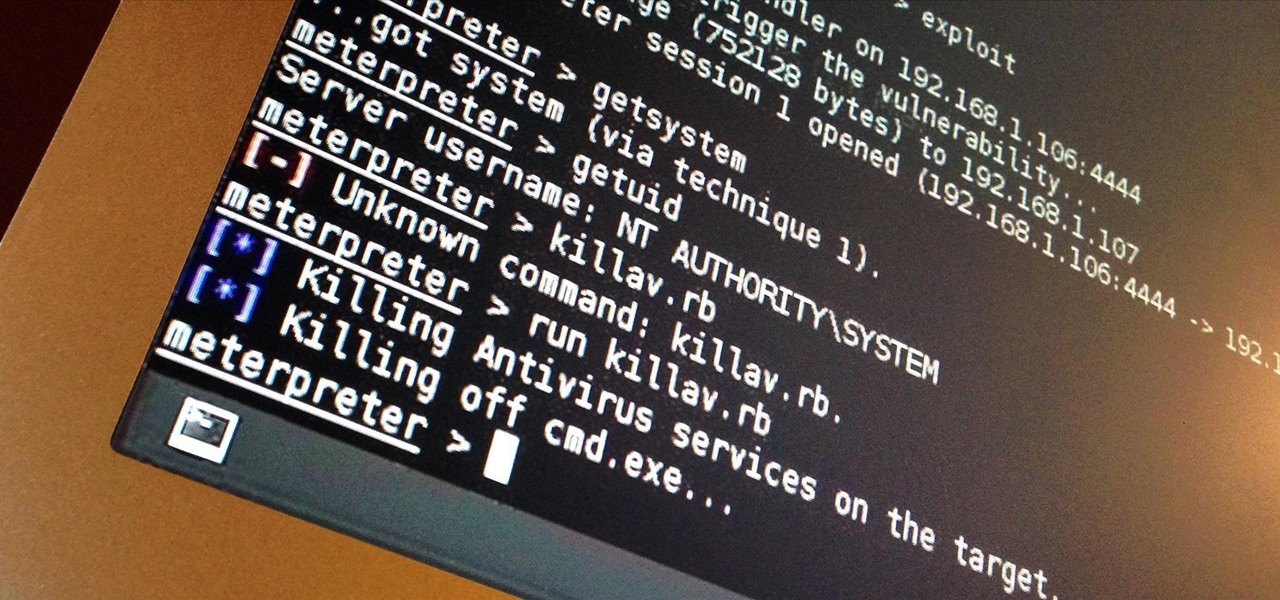
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

In this video we will show you how to replace the inner steering tie rod linkage on a 00-07 Chevy Silverado; this process is also the same on a 00-07 GMC Sierra.

Step 1: Tie a Ponytail Use clear elastic to tie a ponytail and divide the ponytail into 2 segments.
How to draw Lelouch from Code Geass. Follow step by step tutorial of Lelouch from Code Geass. Lelouch's trademarks are his ebony hair, and violet eyes, which he inherited from his mother, and father respectively. Hope you enjoy watching this tutorial! For the full tutorial with step by step & speed control visit: how to draw.
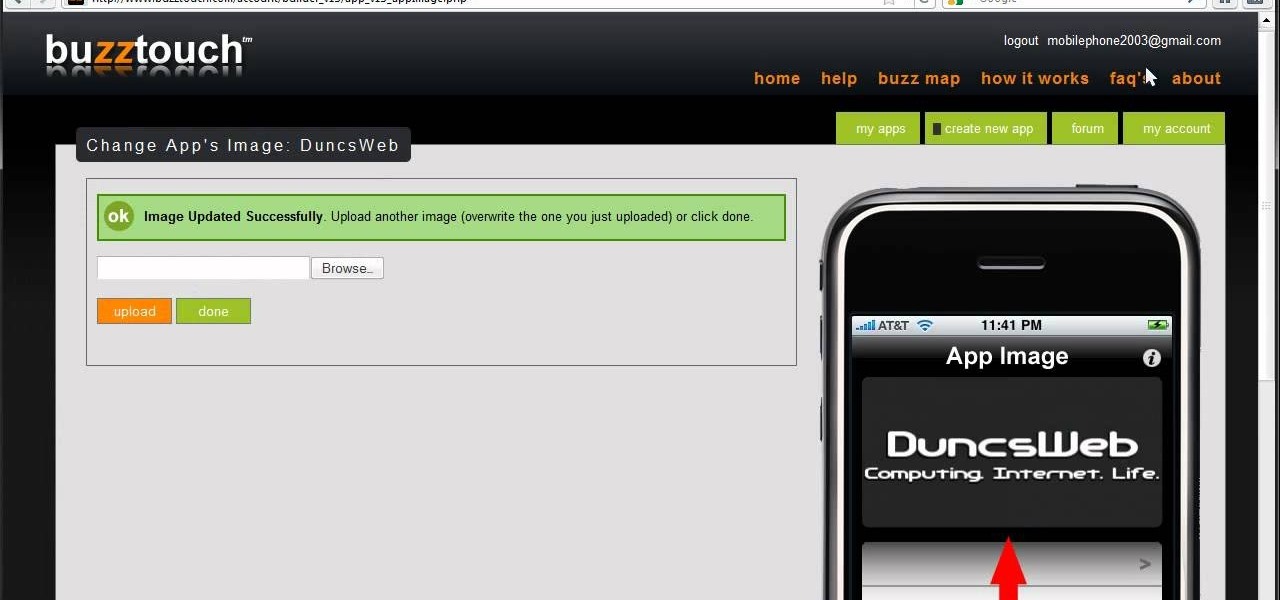
You need an app to be competitive, but you don't know any code. Don't let that stop you. Watch this video and learn about buzztouch a website that will make your app for you. Expand your presence with an app in the App Store or Android Market.
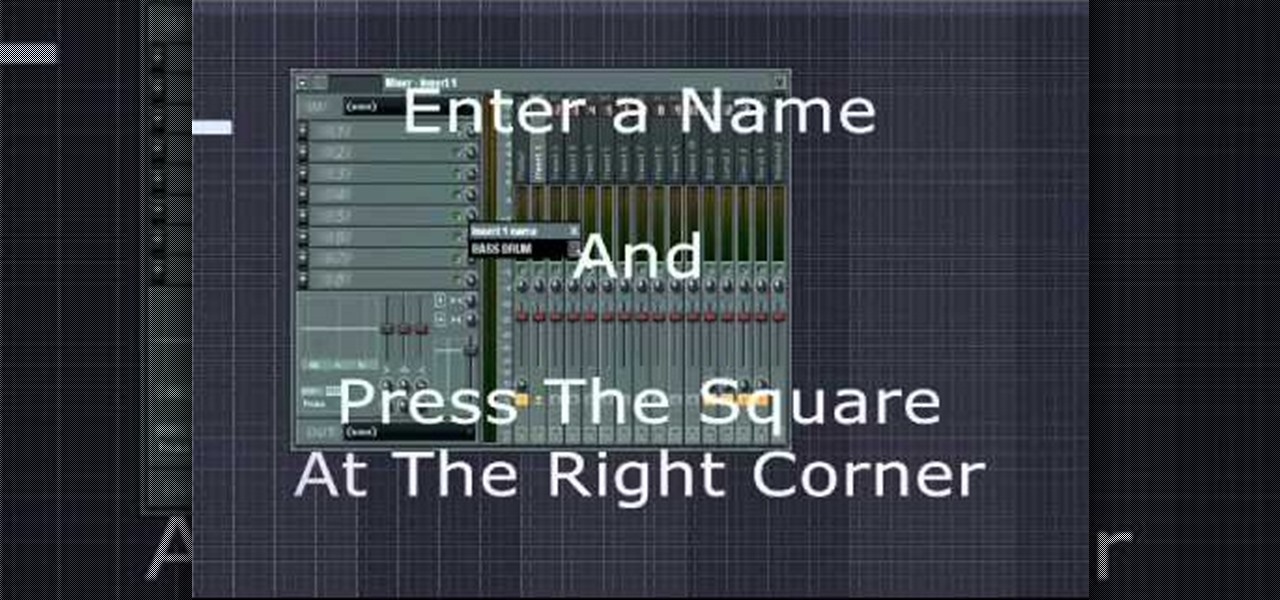
Keep your tracks organized by color coding the mixer channels when using FL studio. You'll have a much easier time making beats in FL studio with color coded mixer channels. You've got the tools, make sure you know how to use them properly.