The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all you'll need is ARKit!

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.

For some of you, whether or not to delete Facebook is a daily struggle. One reason you might not have pulled the trigger on your Facebook account yet could be because of Messenger, which provides millions of people with different devices an easy way to communicate with each other. But here's a secret you might not know: you don't need to have a Facebook account to use Facebook's popular chat app.

Samsung Internet offers excellent features that enhance the mobile web browsing experience, often through its extensions. A QR code scanner, ad blockers, tracker blockers, and more work directly in the browser, so you can do exactly what you want to do on the web.

A loop knot can be used to attach most fishing lures and all hooks and flies. A loop allows greater action of the lure or fly and always ensures the line will pull straight down the shaft. With knots that cinch tight agains the eye of the hook, the may move off to one side causing it not to pull straight.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

If you don't like watching YouTube videos on your computer with your hand glued to your mouse, the next best thing is using keyboard shortcuts. They may not seem any easier than clicking, but once you get them down it's a whole other story. Plus, there are some features you might not otherwise use (I'm looking at you, speed control) unless the shortcuts existed.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

How to make Super fast and Easy friendship bracelet: This bracelet can make each person. Tie 3 strings together creating a loop. Put your beads in each string. Tie the ends of each string so that your beads dont slide off. Start making a braid and braid at least 2-3 inches before you start adding the beads. Add your beads on the outside string and braid till you get your desired lenght. You can also use different color beads or cords and make more colorful bracelets. This will allow you to qu...

If you ride your bike or motorcycle a lot, especially in a large city, you've probably had a few close calls. No matter how safely you're driving, you never know what other people are going to do, and being on a smaller vehicle makes you difficult to see.

The video gives you a step by step tutorial how to replace the steering gear boots of a Volkswagen Passat B3 without dismounting the steering gear.

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

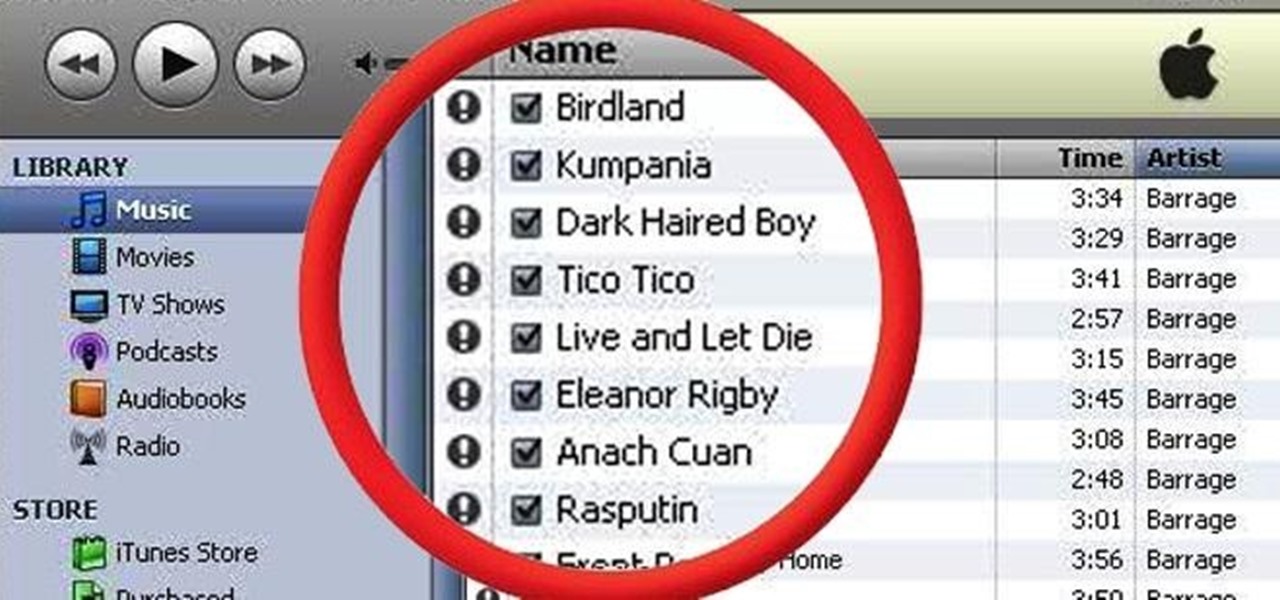
If you've ever mistakenly moved your music files around without relinking them in iTunes, you might now be noticing that you have a long list of tracks asking you to relink them. You could go through them one by one, redirect them to the new file location, then delete any copies. Or you could try to track them all down and delete the old references. But come on, who wants to spend that much time when you can clean up your library using this clever method using only Notepad on your Windows com...

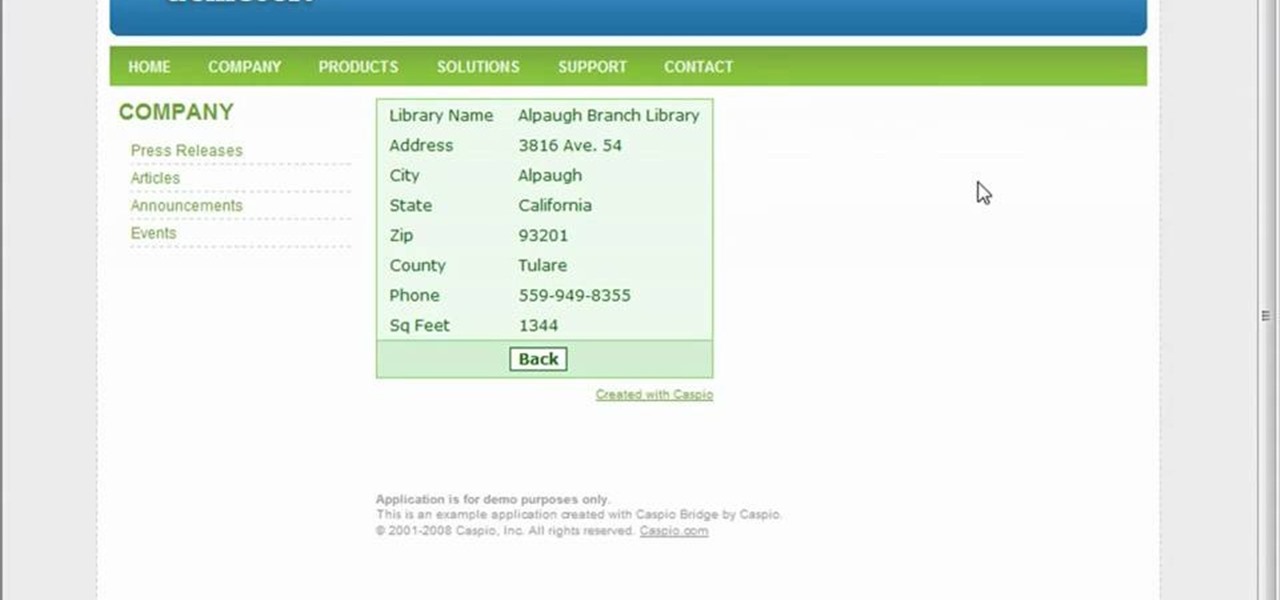
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...

This is a great level hack for Pet Society, using, none other than, Cheat Engine. Try this out for yourself and see your levels rise like tides during a full moon close to an equinox.

Read This Must Need flash player 9!!

You can get push alerts to your iPhone from lots of things online like Facebook and Foursquare, but now here's a way to get push alerts sent to your phone from everyday household objects like the mailbox or the refrigerator. In this Arduino project, a mailbox is wired so that a push alert is sent to the iPod when mail is delivered.

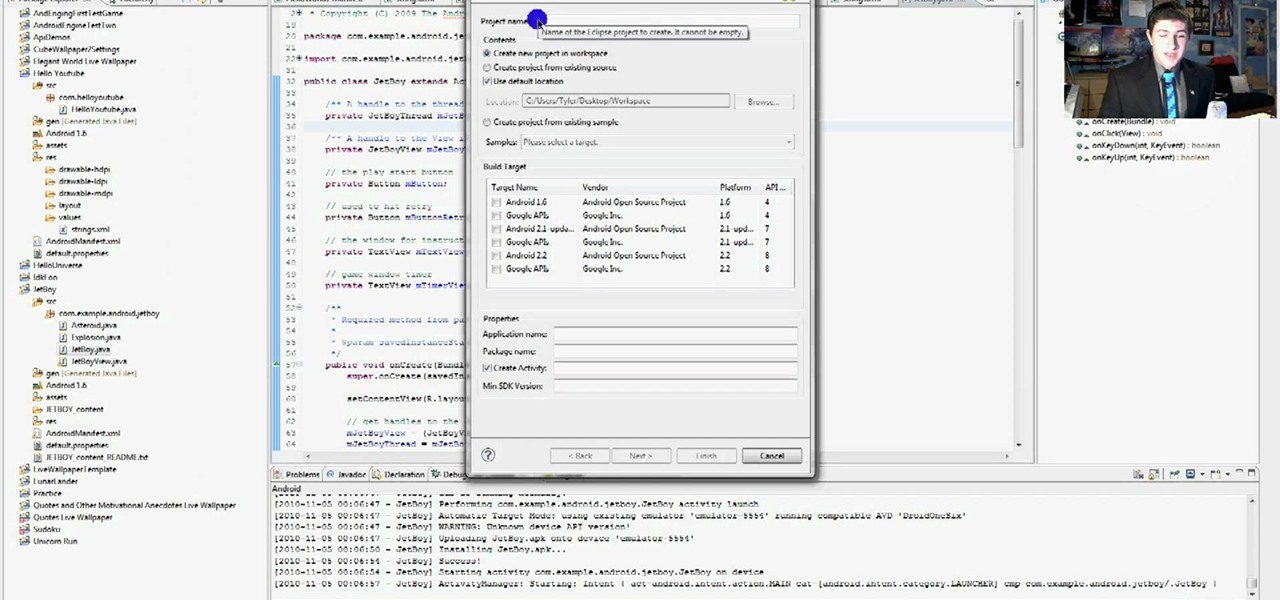
Develop your own Android app by following along this informative video. After installing the Eclipse IDE and the Android development environment, the walkthrough shows you the steps of compiling prewritten code into an Android app and viewing it on an emulator. Next, a step-by-step process to creating a simple "Hello World" app is demonstrated and explained.

So are you a Windows or a Mac? Well, some days you may be one, and other days you may be the other, SO, this handle little how-to will show you how to use Quicksilver to boot up into either OS whenever you want.