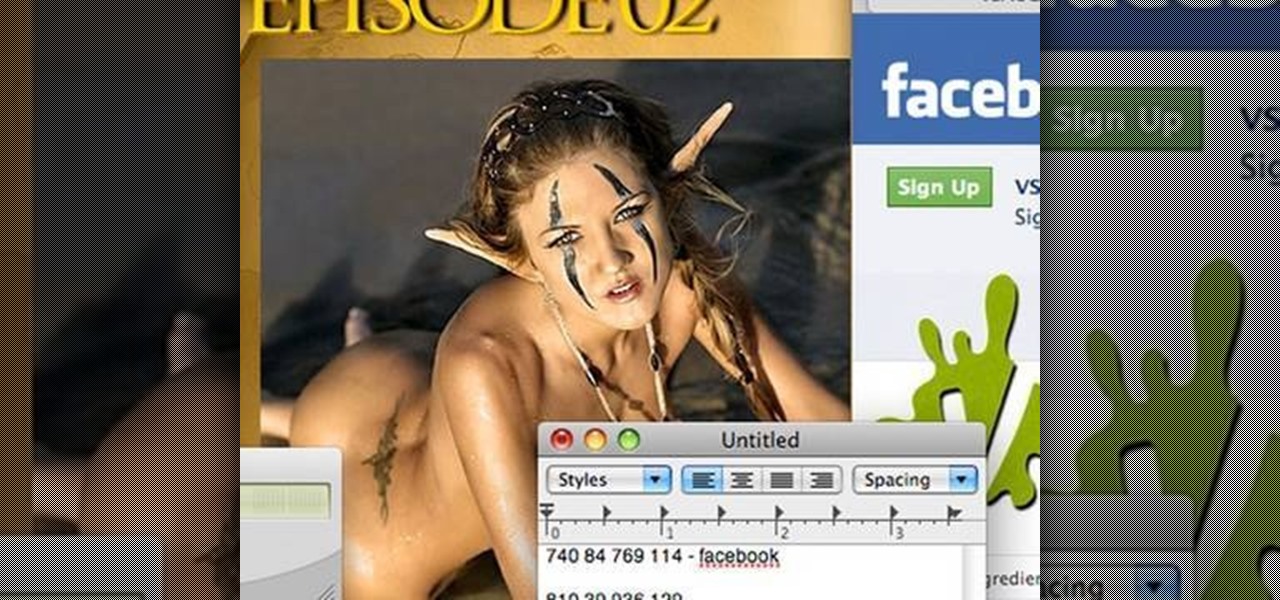
Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

If you or someone you know has younger kids and you're looking for an augmented reality toy, Pai Technology has just the educational option for you.
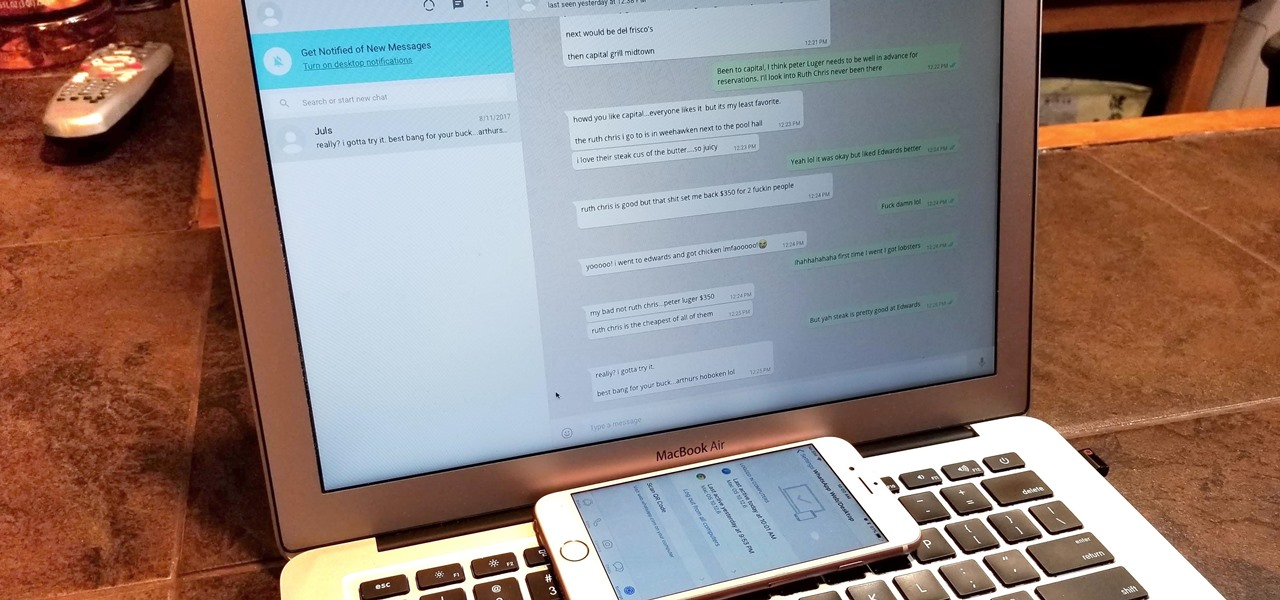
Typos are a constant annoyance that we all deal with thanks to the cramped touchscreen keyboards on smartphones. For many, nothing beats the feel of a good old physical keyboard when it comes to typing fast with minimal errors. Fortunately, WhatsApp has an awesome feature which lets you use their messaging service right on your computer.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

There are a ton of new features in iOS 11, but some of the best ones, in my opinion, are in the Camera app. They're not huge features, but they're much appreciated to anyone who's ever taken a Live Photo or portrait, or even to those who've needed to scan a QR code quickly.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

Google announced today that it's offering rewards to Android Pay users, and taking advantage of these deals could land you a free 2nd Generation Chromecast, among other prizes. The Tap 10 promotion is pretty self-explanatory: Tap to use Android Pay 10 times before February 29, 2016, and Google will give you a code to redeem a free Chromecast, free music, or both. You'll also be rewarded for Taps 1 through 9 as well. You'll receive a code for one music track from the Google Play Store for ever...

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

Google I/O, the national developer conference for the Mountain View giant, has come and gone. We saw the preview for Android L (which you can get right now on your Nexus 5 or Nexus 7), Android Wear, and Android Car and TV.

This is an easy step by step tutorial how to lock your jewels in a hotel room or in a public safe. Be aware that in a public safe it is more secure to use the second method of locking by a magnetic card, not by a PIN code that can be easily seen by someone nearby.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

With the Android 4.4 KitKat update slated for release sometime in October (according to Nestle), I'm sure you're excited to get your hands on and test out all of the new features of Google's latest mobile operating system.

In old-school Konami fashion, there's an Easter egg lurking inside your Samsung Galaxy S3, and I'm not talking about gingerbread men, robots, or jelly beans. In fact, it's actually an achievement, like those you would unlock in Black Ops on your Xbox 360, and it's pretty easy to find.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Last week, the whole world ushered in the new year, celebrating the start of 2013 with family and friends, and of course, that little thing we like to call alcohol. But just because New Years Day is over doesn't mean the party is. And surely, there will be some assholes out there that will drink and drive this year. It happens. So, how can you make sure you're not one of those assholes?

'Tis the season... for cheap (and free!) video games. THQ's Humble Bundle lets you get 7 games for any price you want, and now they're making it even better by offering fans a free Steam copy of Metro 2033 just for liking Metro on Facebook, which is gearing up for the latest Metro: Last Night release.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

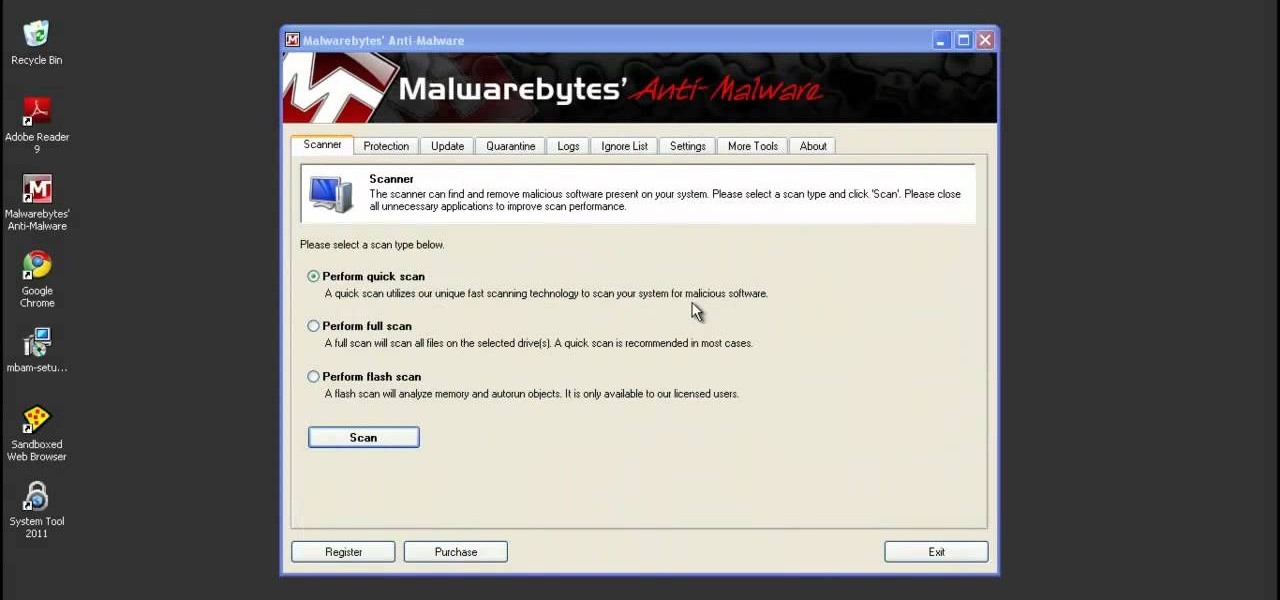
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

The personal computer is a strange and powerful entity, capable of bringing great joy. Just as often, you probably want to chuck the damn thing at the wall because it doesn't work right. If you want to pull a prank on a friend that will really upset them, messing with their computer is one of the best ways to do it. This hilarious video will show you how to do three great PC pranks quickly and easily, including changing the contrast on the monitor and pretending to edit websites using Javascr...

Need to secure your track to the road bed for your model railroad? Well, this video tutorial will show you how to do it, not to mention show you how to weather your flex track.

LEGOs are more than just a toy for young children— it's an emerging art form combining photography, stop-motion (i.e., brickfilms), and imitative models that portray today's pop culture as it is. It's something visual culture analysts are sure to be studying over the next decade, and Chris McVeigh, from Halifax, Nova Scotia, is sure to be studied for his LEGO mastery.

Arrr matey, it's getting a little drafty in here! Time to tie up a pirate bandanna to keep yer head warm! This simple how to show's you how to make a pirate banana just like the one Jack Sparrow wore in Pirates of the Caribbean. This is simple to do, costs almost nothing and is essential for creating your own pirate costume. You'll need a 2ft by 2ft square of light cloth. Walk to plank and watch the video! Arrr!

Tie loose ends together - in the literal and original sense sense of the phrase - by sewing together the ends and/or hems of your knitting projects like a pro. Whether you're fusing together two pieces of wool-knitted cloth to form the back of a beautiful winter sweater or just want to join patchwork knits into a rasta-cool beanie, knowing how to stick pieces together is integral for a tidy project.

Paracord, or parachute cord, has a very interesting history. As its name implies, it was used to suspend parachutes in WWII. The super lightweight cord is used nowadays as a utlity cord in the military and other applications. The paracord, also known as 550 cord, has even been used in outer space by astronauts repairing the Hubble Space Telescope.

Paracord braiding is a popular technique used to make lanyards and ties for survival gear. There are many different techniques a braider can use - the most common are the rattlesnake knot and the square braid. This video shows you the nuances of both techniques, a few variations, and how you can decide when to use one or the other. You can also alter the appearance and tensile strength of your paracord braid by changing how tight you make your knots.