Did you try to impress your friends with chopsticks but it didn't work out? Then try making cheater chopsticks the next time you go out for sushi. In this how-to video we show you the step by step process of using and making cheater chopsticks with rubberbands. Follow the cheater chopstick guidelines below.

Not all Halloween costumes have to be grotesque. This look is a pretty, nature inspired peacock feather eye, that can even be worn in a non-costume way. To create this look, use these MAC cosmetic products Studio Fix Fluid Foundation, BE Mineral Foundation, Mineralize Skinfinish Duo in "Medium Dark," NYX Pinky Blush, Bobbi Brown Shimmerbrick in "Gold," Blackground Paintpot, Mutiny Pigment, Teal Pigment, Black Tied e/s, Woodwinked e/s, Blacktrack Fluidline, Urban Decay 24/7 Eyeliner in "Zero,"...

Planters or organized beds with planter borders can not only provide mowing definition, but contain the flowers and hopefully keep out weeds that may grow into them from surrounding areas. Backyard planters can be big or small, permanent or portable. The simplest planters consist of edging for flower or vegetable beds. In the past, many used recycled railroad ties for this, and they still add a distinctive rustic appeal to garden beds. In recent years, however, pressure-treated landscaping ti...

The Rapala Knot is the knot that the Rapala brothers recommend to use with Rapala lures. The Rapala Knot attaches the lure with a loop at the end of the line. The loop will allow the lure to move freely and naturally. The Rapala brother also emphasize that the line is attached directly to the eye of the lure without the use of a snap or swirvel. Again this is to insure a natural movement. Follow along with this HowTo video tutorial to learn how to tie a rapala loop the next time you go fishing.

This copper and bronze eye makeup look is great for the fall, and really adds focus and drama to the eyes. The cosmetic products used to create this look are Studio Fix Fluid Foundation, Make Up For Ever HD Powder, Emote blush, Nars Orgasm blush, Cream Color Base in “Pearl,” Painterly Paintpot, Deep Damson e/s, Coppering e/s, Black Tied e/s, Brule, Shroom e/s, Blacktrack Fluidline, Urban Decay 24/7 Eyeliner in “Zero,” Loreal Voluminous Mascara, Fleshpot Lipstick, and Bare Necessity Dazzleglas...

Bumble bee eyes? Not quite, but this combination of yellows and blacks might cause a buzz! Watch and learn how to create attention grabbing eyes using these make up techniques and tips.

Looking for a classic, yet stunning look? Follow these beauty tips in applying silver, grey and black eye shadows to create a sophisticated, attention grabbing look.

Terry shows us how to set up the prussik for glacier travel. This is a demo of what to do with the ends of the prussik. Remember you have to know this knot if you are going to be a mountaineer. Terry places one on. In a real world situation he may place two on so that he has one going to the person behind him and one to the person ahead of him.

A parachute-style dry fly has several advantages over a standard hackled dry fly. The parachute name comes from the fly's propensity for soft, upright landings that don't spook trout. The body of the fly rides lower the surface film like a real mayfly and some people find the parachute wing is easier to see. Another important quality is that because the hackle rests horizontally on the water, parachute flies float well and also imitate mayfly spinners laying flush in the water, as well as dun...

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

This Halloween, Belle costumes will be out in full force as devoted Beauty and the Beast fans represent the tale as old as time. Not only was the live-action version of the animated classic the top-grossing film of 2017 (so far), it's also likely to be a contender during awards season. If you're too swept up in all things Beauty, then a Belle costume may just be the look for you this Oct. 31.

Universal Studios and Cinemark Theaters have enlisted mobile augmented reality game Seek to promote The Mummy, a reboot of the action-adventure film franchise starring summer movie mainstay Tom Cruise.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

After 2 months of trial, I'm finally here to tell you a secret that WORKS!! A permanent hair removal secret from Burma - for natural hair removal permanently!

If you haven't come up with a funny, innovative costume yet for Halloween, you're running out of time. While all your friends are busy perfecting their month-long DIY costume project, you're still being lazy about it and have just now started to search online for ideas.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Ant-Man isn't one of the most famous Marvel superheroes. In fact, with the news of his individual movie came great doubt that the comic book legends could succeed in telling the tiny story of an oddball hero on the big screen. Yet with its humor and unique story, Ant-Man has become a hit movie in its own right—and the hero will most certainly make a hit Halloween costume.

Holidays can be challenging, especially around Christmastime—but not if you invoke your inner MacGyver spirit. In my latest "life hacks" guide, I show you 10 amazing tips and tricks that'll hopefully make your holiday season a little more merry.

A lot of my hacks use salvaged parts from an old microwave, with the microwave oven transformer (MOT) being the most useful component.

In this video we're making a weather predicting light! Good luck! Video: .

This is a very easy and exciting new Halloween nail polish design! The color code is based on Halloween pumpkin and Halloween night combination to suit the Halloween mood perfectly.

Your closet is an area that holds important things such as keys, glasses, clothes and shoes. However, for some reason, it's always messy. Why is this? I know my closet is messy because I don’t have a lot of time to sit down and organize every little thing in there. I have never really even given much thought into organizing it.

You have paisley ties, you have striped ties, now try a duct tape tie. Duct tape comes in a variety of colors and with the help of one of your boring old ties as and outline, you can have an imaginative new tie that you can be sure no one else has.

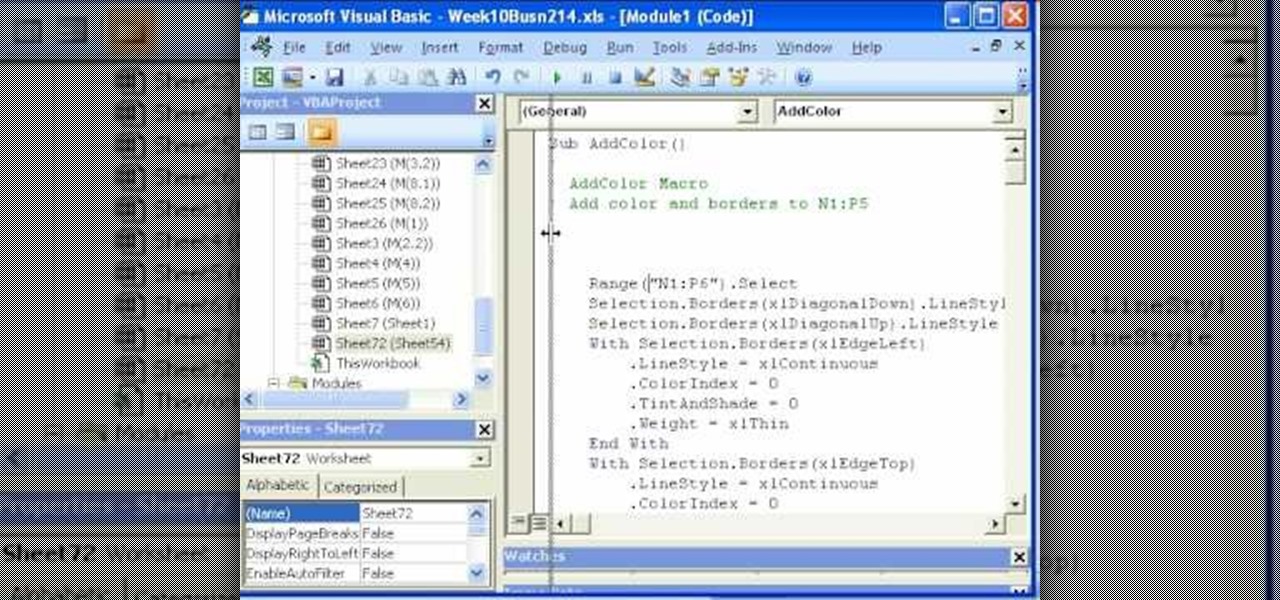
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 52nd installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to record and use macros in Microsoft Excel 2007.

Mike Callahan from Butterscotch describes how to manage the passwords on your iPhone by using the 1Password app. The application costs $5.99 for the Pro version. First, you enter an Unlock Code to give you access to the app. The icons across the bottom of the screen correspond to different features of the app. The Logins icon stores your login information. The Wallet icon stores information about your credit and bank cards. The Passwords icon holds all your passwords. The Add icon allows you ...

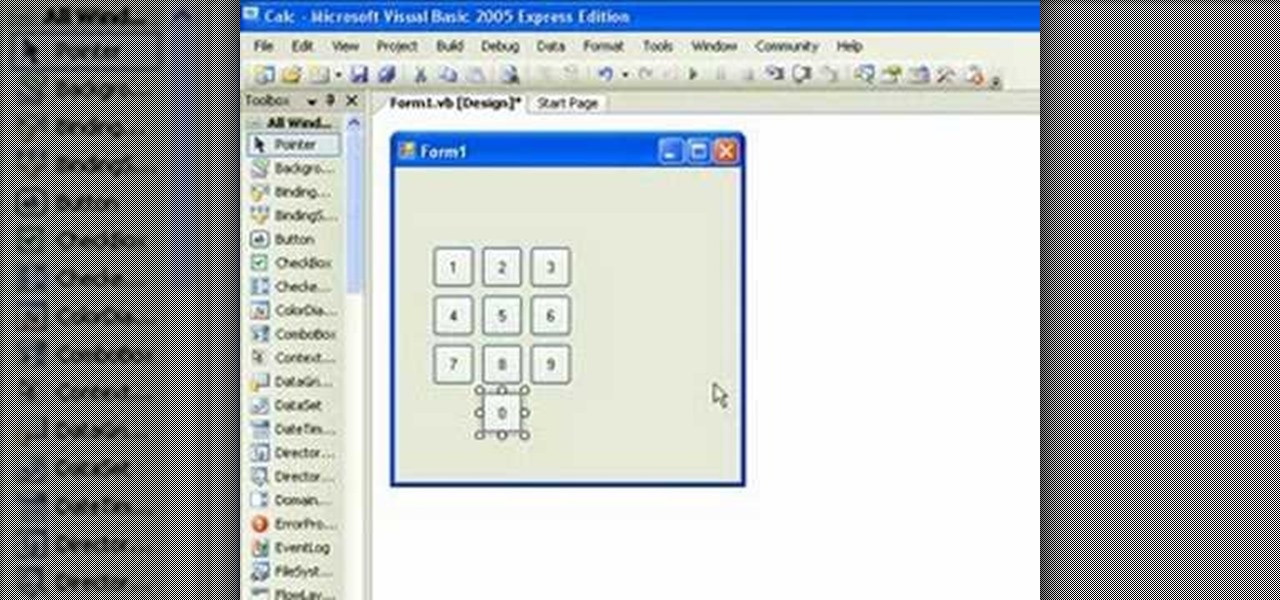
If you're new to the Visual Basic IDE, looking to brush up on your VB programming skills, or simply have a burning desire to code a simple calculator, this three-part video lesson is for you.

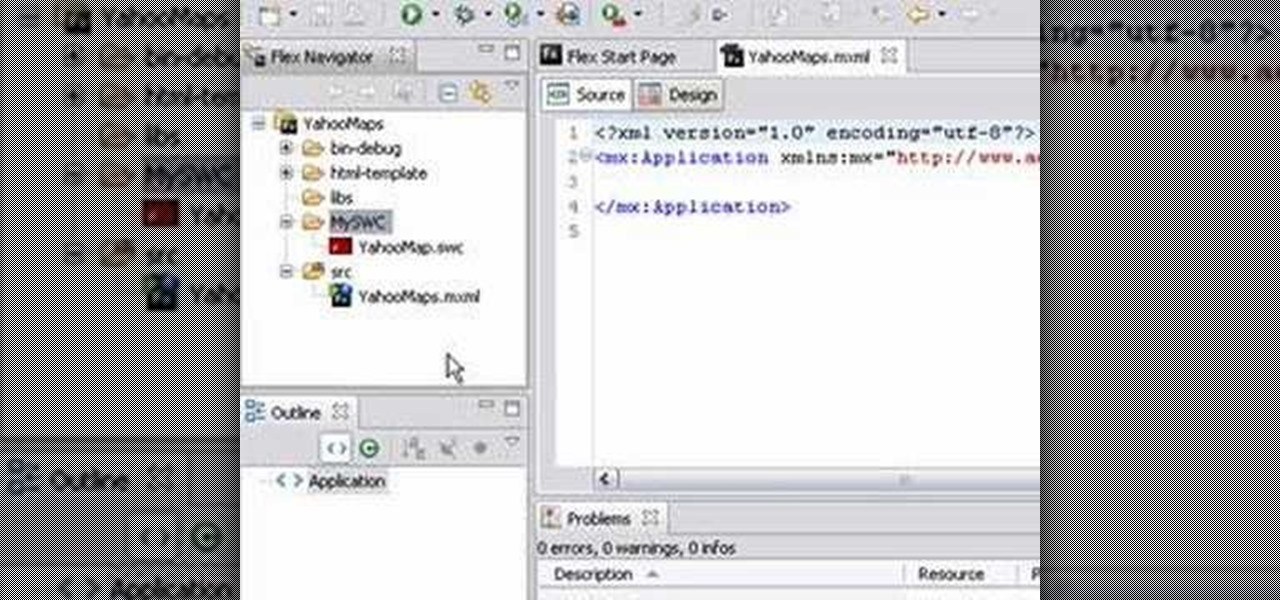
This video tutorial series shows you how to use the Yahoo Maps AS3 API in Adobe Flex 3. This new API gives you the ability to place Yahoo maps directly into Adobe Flex 3. Mike Lively Director of Instructional Design at Northern Kentucky University will be taking you through this tutorial.

Tying line to line knots in fly fishing. Learn about fly fishing knots, equipment, and techniques in this free video.

In this video series our expert will demonstrate a wide variety of knots to use during camping adventures, rock and mountain climbing trips and much more.