Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

Thanks to Metaverse, it has never been this easy to create your own AR game.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

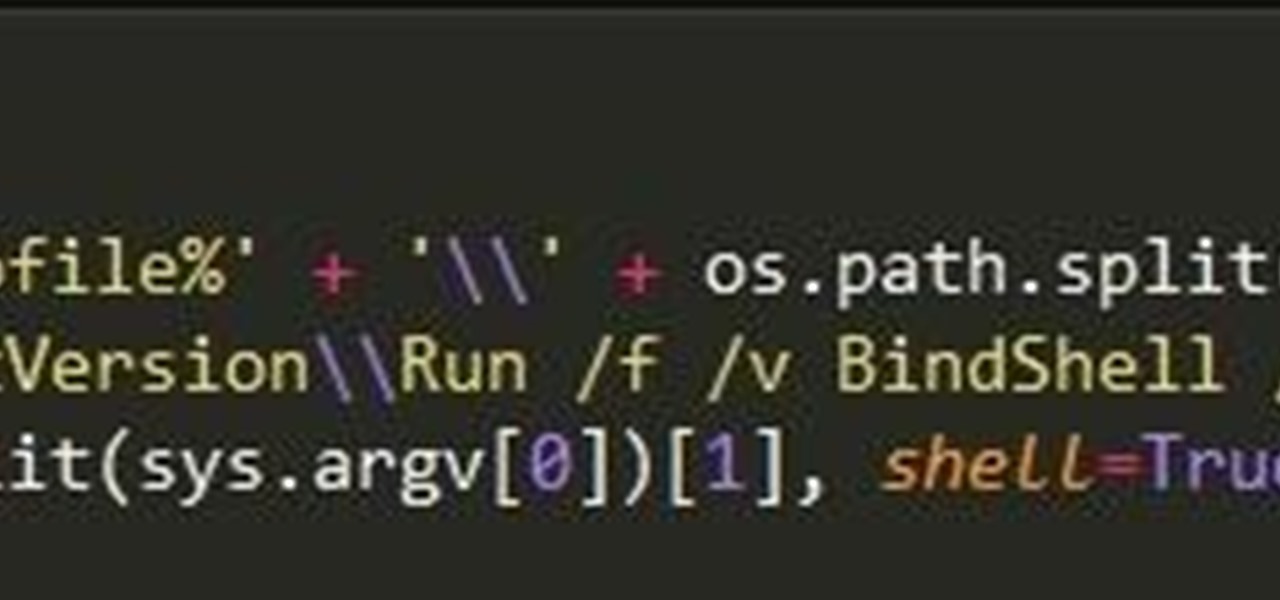
I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices yet. While there are ways to port BlinkFeed over to other devices, it's reliability is dependent on the ROM, sometimes causing bugs and crashes.

Microsoft's latest Xbox commercial features Aaron Paul, the actor best known as Jesse Pinkman on Breaking Bad. Check it out below, but keep an eye on your own Xbox One, if you've got one.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.

Life hacks are tips and tricks to help make life easier. Shortcuts and clever workarounds for life's daily problems. Sometimes common sense isn't so obvious until you've actually seen it. In this video, I'll be sharing with you 10 life-changing hacks you can use right now, from finding your lost smartphone to sleeping better at night.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Parrot, a company that specializes in personal drones, has recently come out with new products that'll make those '90s robots look as dated as lava lamps and tie-dye.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

It may finally be dying down a bit, but there are still plenty of cat lovers addicted to Grumpy Cat, who has surpassed her internet meme stardom to move onto books, calendars, and even a soon-to-be film. For those of you who just can't get enough of the crotchety-faced Tardar Sauce, make this Christmas a Grumpy Christmas with this free printable paper ornament of Grumpy Cat.

Although mowing is key to keeping your lawn healthy and good looking, it isn't anything worth jumping up and down for when it comes time to doing it. As it turned out, the first time I mowed my lawn wasn't nearly as fun or exciting as Hank Hill made it out to be. Maybe it was the beer.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

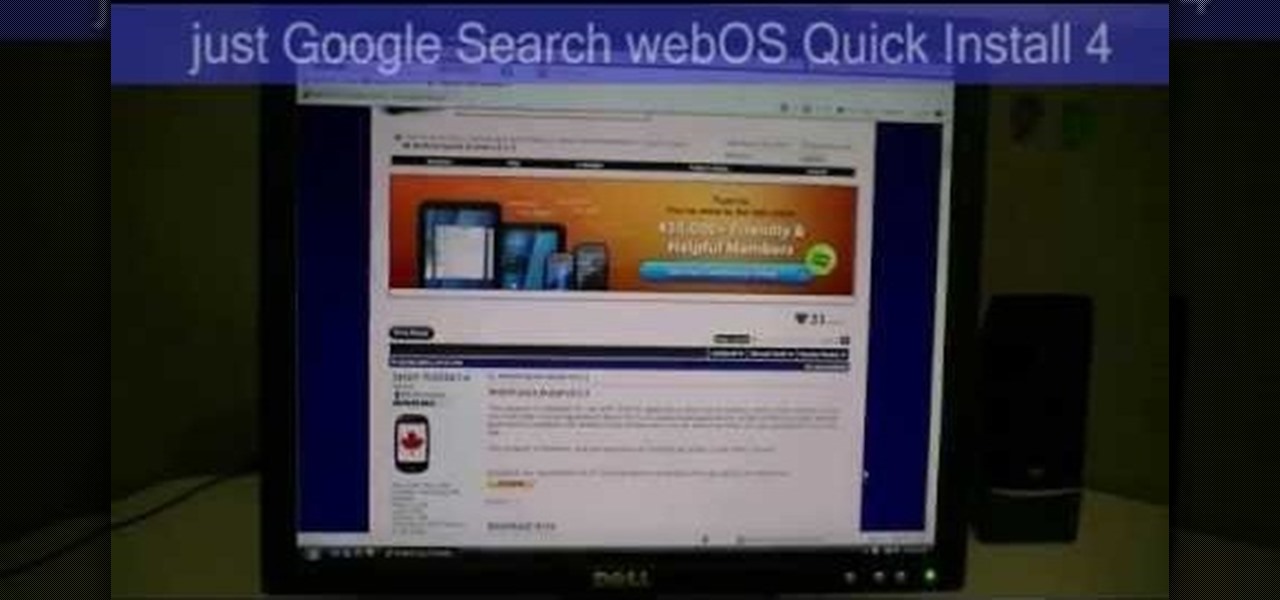
In this two part segment, we learn how to properly overclock the HP TouchPad. One of the few complaints about the tablet was the occasional slow reaction time of the processor, but now you can speed up your TouchPad for a faster webOS. This guide walks you through everything from downloading Novacom drivers to inputting the Konami code.

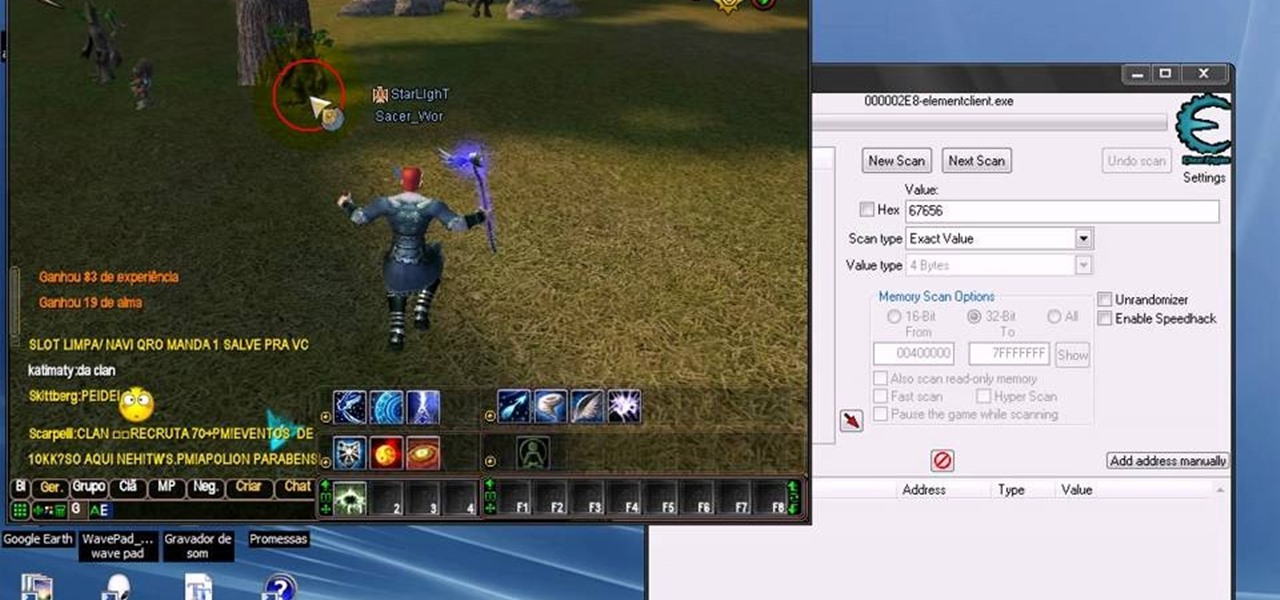
Tired of grinding out endless, boring quests for meager returns when you're playing Perfect World International? Want to rocket to high level and immense piles of treasure immediately? Cheat Engine is your answer! This free game hacking program frees you from having to hunt for cheat codes or exploit glitches to get ahead in PWI. Just follow along with this easy and quick hacking tutorial, which shows you how to use this program to change many of the values of your character and in the game.

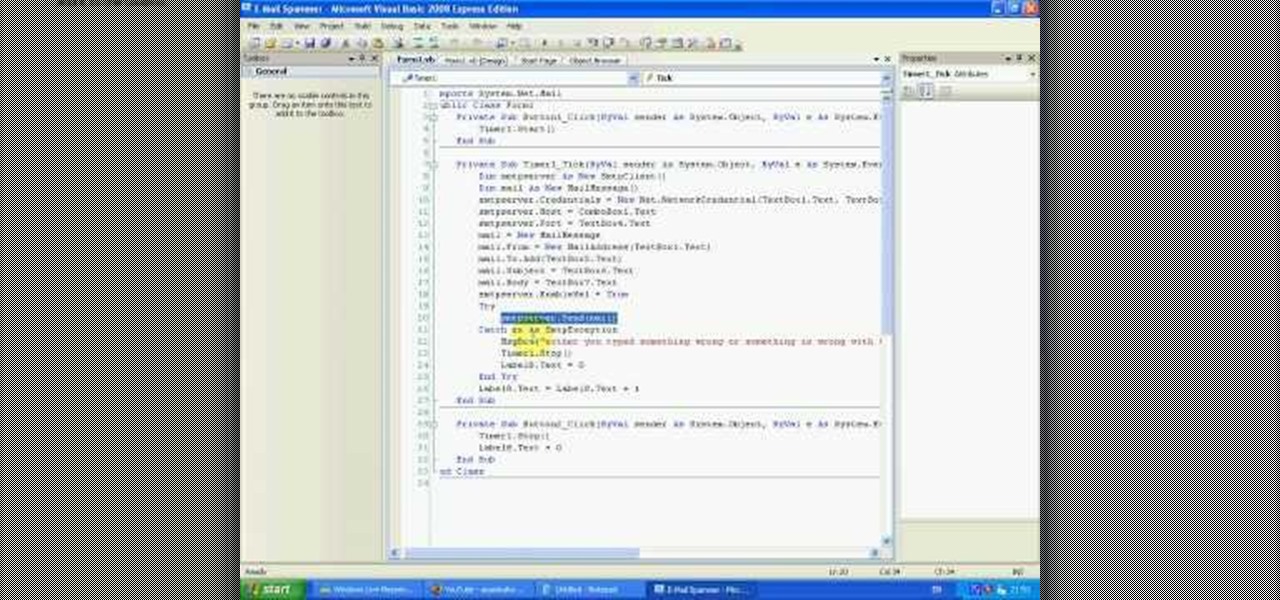
Looking for a program that will let you send out mass emails or spam? Or maybe you're just looking for a way to prank your friends or get revenge by sending them an email bomb? If you have Visual Basic 2008, you can write your own program that will ensure the recipient never forgets what you sent them! This video gives you the basic code to set up the program, and you can tailor it to your own needs quite easily.

Tired of clicking on interesting looking links in Facebook, only to discover that they are hidden behind a page you have to 'Like' before you can see? If you're surfing using Google Chrome, you can completely bypass this privacy setting. When you get to the page, go to the menu bar and click on 'Inspect Element.' Then you'll see the code for the page, and you'll be able to get around the block to see the page you want.

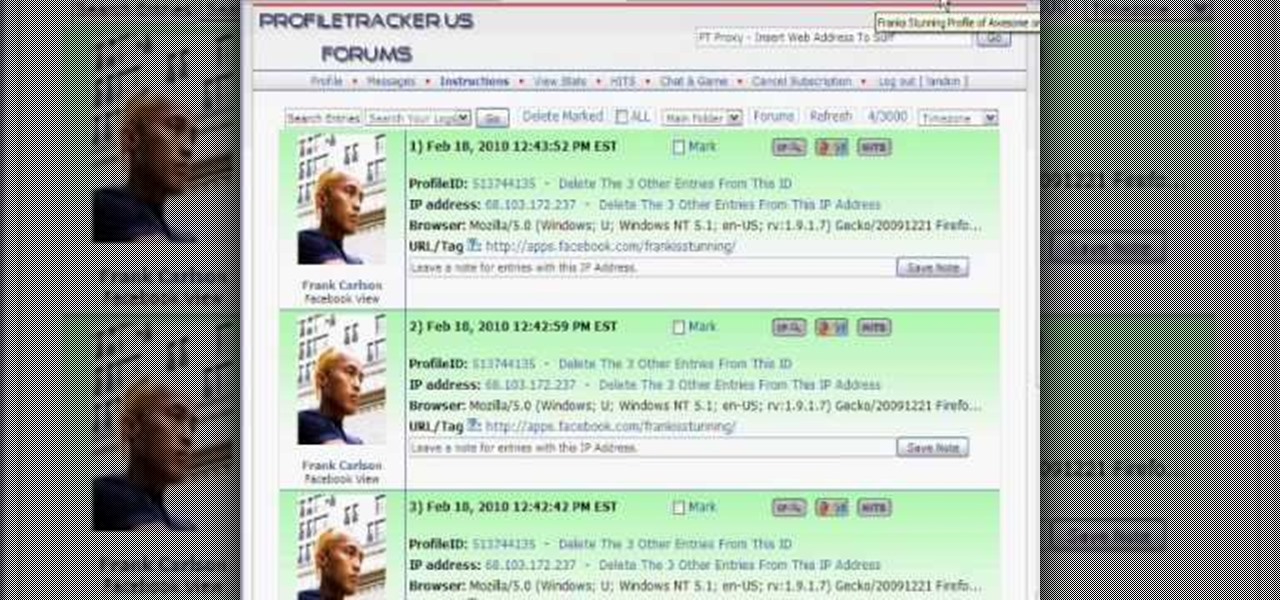
Want a way to monitor who is coming onto your Facebook profile? You can use a third party app, the FBspace Tracker, to enable your profile to secretly log who is viewing you. Even better, FBspace Tracker lets you set up your profile with custom HTML code. This video shows you where you can download the app, then how to install it and set up your Facebook profile through the app. Make your profile not only unique, but secure as well!