A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.

At last, what you all finally waited for! Hi! Fire Crackers,

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

The hardware running your One is nothing short of powerful, but the people at OnePlus can't control how developers choose to utilize that power—or rather, not utilize it. Most popular developers have removed all signs of lag from their apps, but others still have archaic lines of code that can make your shiny, new device feel like a first-generation smartphone.

If you're trying to get a new iPhone 6 or 6 Plus, we know you've been struggling to find one, and we're here to help. With Apple's preorder numbers topping 4 million in the first 24 hours, it was nearly impossible to get one during the first wave.

This past year, Facebook spent $19 billion purchasing the popular messaging app WhatsApp, and for good reason. Mark Zuckerberg isn't going to spend that type of money on just any application. WhatsApp is widely popular and frequently used by more than 500 million users worldwide, which is almost twenty percent of the Earth's population.

I love Android, and I think its apps are great—the polish that came with the Ice Cream Sandwich update truly put Android design on the map. That being said, one of the more frequent complaints from iOS fans continues to be that apps just "run smoother" and "look better" on iOS than they do Android.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...

How do you know if the Beats By Dre Studio headphones that you are about to buy online are genuine? Always ask the seller to use the youVerify app before you buy. Smarter Selling, Safer Shopping.

Video: . How can you tell if the Louis Vuitton handbag that you are about to buy online is not a fake? Follow these 6 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping. Step 1: Branded Dust Bag

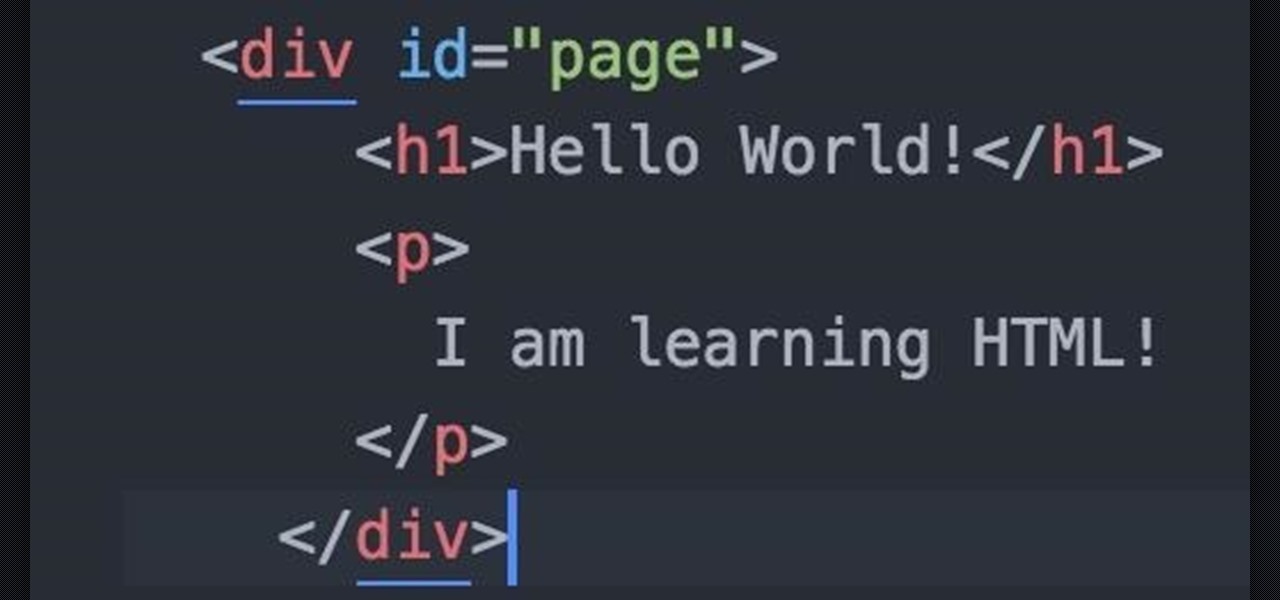
This HTML Web Design tutorial will explain how to add a Heading tag for your website. The heading tag is very important because it helps search engines to determine what the main topic is on a particular web page within your website. The HTML codes for heading tags range from h1 to h6 with h1 being the most important or in other words the main heading HTML web design tag. Make sure to give the h1 tag the most importance in terms of titles on your web page for headings. Another rule I recommen...

Has your grandmother ever called you complaining about her internet not working? Don't you wish you could just see what she was talking about and fix it instead of having her try to explain why the mouse won't double-click on the thingamajig?

If you don't have a car, or just prefer to take public transit to work, you know that an unexpected change in the weather can quickly...er, dampen your day. If you're not expecting it, rain or snow can turn your trip into a long, hellish ordeal—especially if you bike.

Last week, Google updated the YouTube layout to be more in tune with other Google properties. One thing that's different is the new, more Google+ look of your YouTube homepage. Though some may like the change, some definitely do not. Also new is the "Guide" on the left side when you're watching a YouTube video. for you folks looking to get back to the normal YouTube layout, it's as easy as copying and pasting some code into your browser.

Whether it's forgetting your driver's license or misplacing your cell phone, forgetting things at home can be a pain in the butt. Car keys, wallet, purse, papers, sunglasses—the list can go on. Sometimes I even surprise myself at the important things I forget... Oops.

For over three years, Facebook users have been able to clog up their Facebook chats with little pictures of smiley faces and red hearts, but now it has finally gone a step further...

An isomorphic (or self-transposing) keyboard is "a musical device where a grid of notes is displayed to the user and the interval change between notes in constant for any given direction." For those of you who didn't grow up playing the piano like I did, that basically means that it lets you move between keys easily without having to learn new patterns because the keys are laid out so that a chord is the same pattern in every musical key.

Want to know when you have a visitor, even if you're not home? You could always set up a security system and live-stream it with your iPhone. But if you don't have a spare iPhone, or just don't want to go to the trouble, this simple hack will add text message alerts to your doorbell so that it lets you know when someone's there.

Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

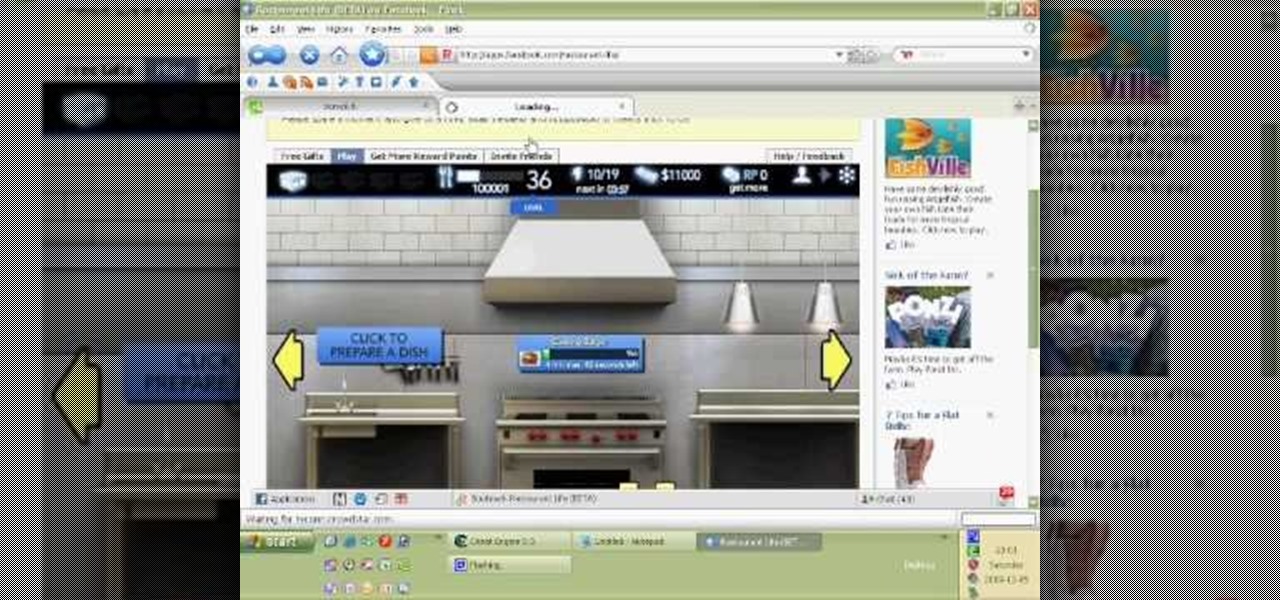
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

Have an old bike combination lock that you can't remember the code for? If it's a simply four-digit cable lock, you can easily figure out the combination with a quick peck-and-go method. Best of all, this technique doesn't require any tools or special know-how, and let's you reuse the cable lock again versus just damaging it with bolt cutters. All you need is a bit of patience and you'll have your figure out your combo in no time.

Backpacks are handy for camping, hiking, school and travel, but they can be difficult to pack properly. In this tutorial, learn how to pack your bag so that its light and efficient.

In this tutorial, we learn how to make your home safe and secure with tips from Lowe's. You should do a safety check on your house at least once a year. Start with the entryway, making sure you have an insulated wood door in the doorway. Make sure there is a lock and a deadbolt lock on the door as well. Once inside, make sure you have timers to control your lighting, so it can come on even when you're not at home to detract any robbers. In the garage, make sure you have an electronic door ope...

In this video tutorial, viewers learn how to enable hidden God Mode in Windows Vista 32 bit and 7. This option does not work on Windows Vista 64 bit. Begin by right-clicking on the desktop. Then go to New and select Folder. Now name the folder to a desired name and paste this code behind it: .{ED7BA470-8E54-465E-825C-99712043E01C}. Users will now have a full list of control options for their computer system. This video will benefit those viewers who use Windows 7 and Vista, and would like to ...

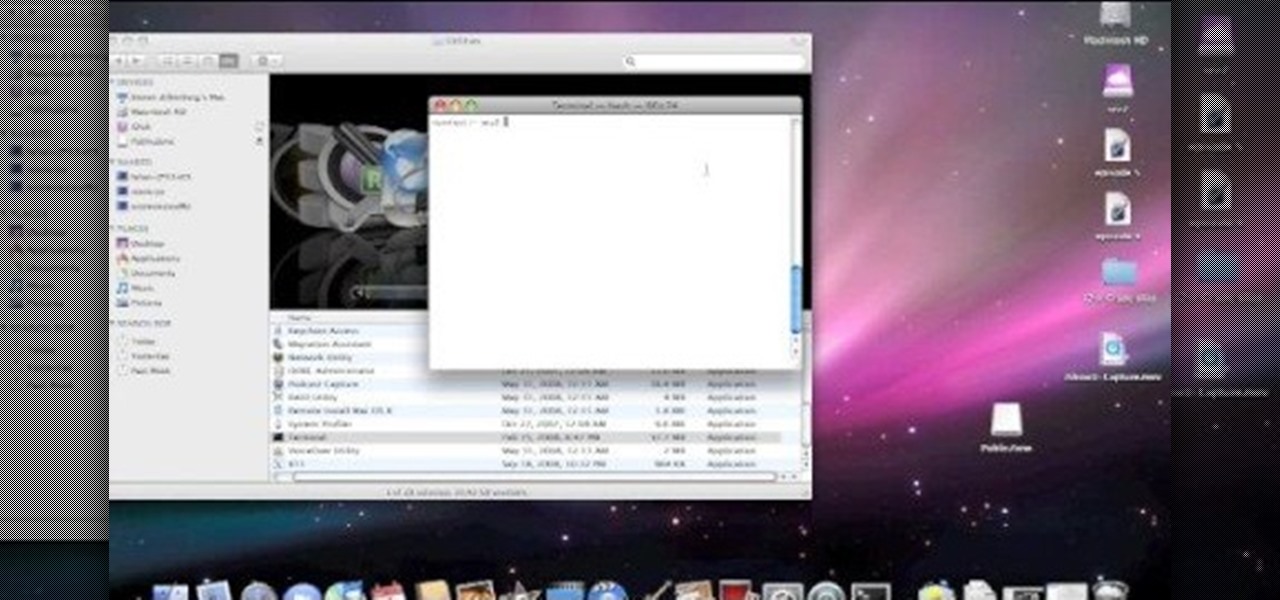
In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

Ubuntu and Windows may have trouble syncing time because when they are dual booted, they both assume that your hardware clock is set to a different time setting. Ubuntu assumes that your clock is set to UTC and Windows assumes that your clock is set to local time. Answers Launchpad has solutions to fix the syncing issues. To correct the issue, configure Ubuntu to be set to local time. Launch your terminal window and click on the description box. In the code string change the UTC default value...

JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. Again, far left Pepsi, near left Pepsi, near right Mountain Dew and far right Mountain Dew. This hack will allow you to see the stats, set the price and see error logs.

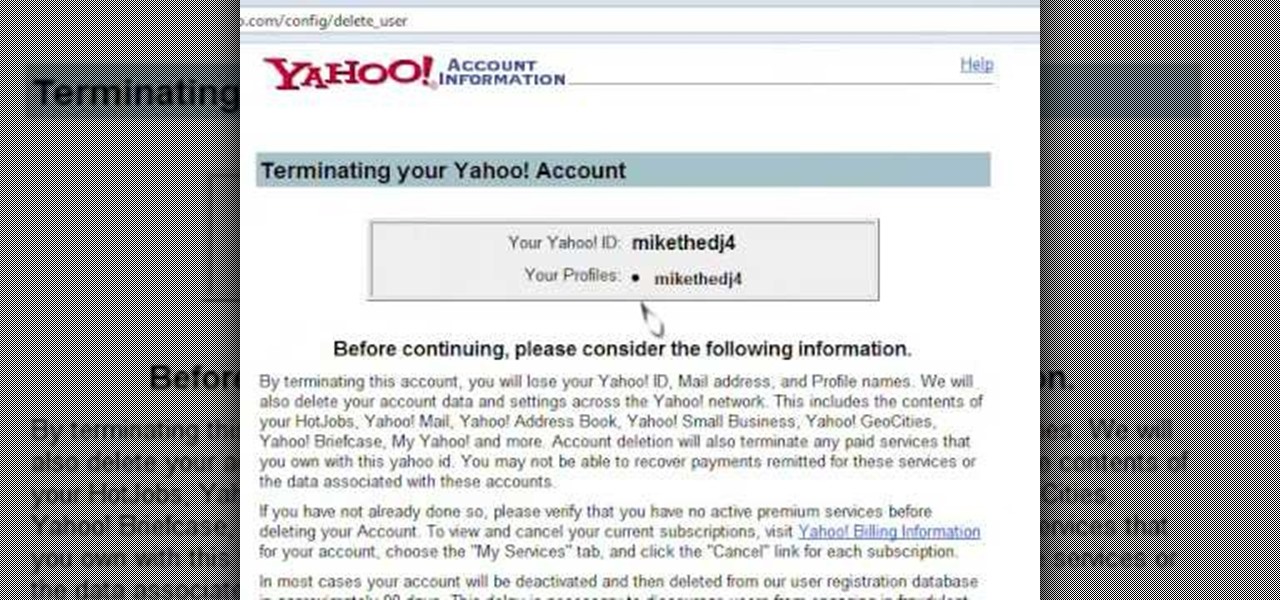
Learn how to delete your old Yahoo or Yahoo mail account in simple steps. First open your web browser and enter the web address for Yahoo to open it. Now log into your account using your Yahoo username and password. Go the account termination page, confirm your account termination and enter code give. Finally press 'Yes' and enter your password . Now your Yahoo or Yahoo mail account will be deleted.

Learn how to delete your old Yahoo account from this video in simple steps. First open your web browser on your computer and go to the Yahoo home page. Now sign into your account using your username and password. Now copy and paste this link "http://edit.yahoo.com/config/ delete_user" in your address bar. Enter your password to confirm the deletion of your account. Finally enter the code to confirm and delete your account.

Learn how to change your HTML font and size with this video. First go to edit menu> preferences and then select fonts. Here there are many fonts that have their own categories-proportional font, fixed font and code view. On the right hand side, one can even change the size. Once the settings are changed, click on "OK". That's it, the font as well as its size are changed. It will help while working on the software for better viewing in case of small screens.