This video shows how to download songs from MySpace using the software Gopher. First the software should be downloaded from the site indicated. After the download is completed install the program and head over to the MySpace page where the song can be streamed. Next the MySpace friend ID should be found as indicated and the code should be entered into Gopher. Select the song to be downloaded from the list and save it to your hard drive following the steps of the video closely. Happy downloading!
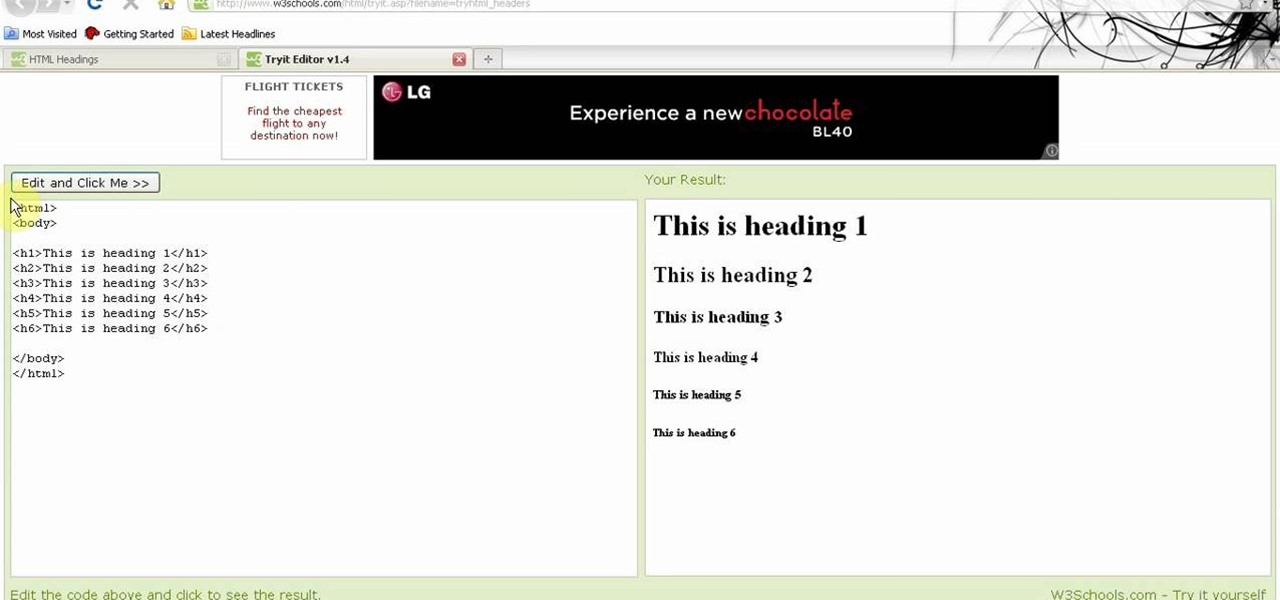
1. Visit 3schools for free and fantastic web building tutorials. 2. Find the subject you are interested in researching and simply click on it and it takes you to a video.

This video will show you how to enable MMS on your iPhone 3G and 3GS on 3.1 firmware. First, copy and paste the terminal code. Hit enter. Go back to the description and click the link to the file. Connect your iPhone and go into iTunes. Hit options, check for updates. Go to where you have downloaded the program.

Get all of the info on Thesis themes for you WordPress blog. Watch this video tutorial from 4Blogger to learn how to add a background box and color in a Thesis sidebar.
Take a look at this video if you've ever been curious on how people send video messages via the iPhone.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel. All training and refresher courses must be done in accordance with federal and provincial regulations and the Canada Labour Code.

A three-part lesson in how to count and play your way through 12-bar blues changes on your harmonica. Required: a copy of "Harp Attack," a 1990 Alligator Records release.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

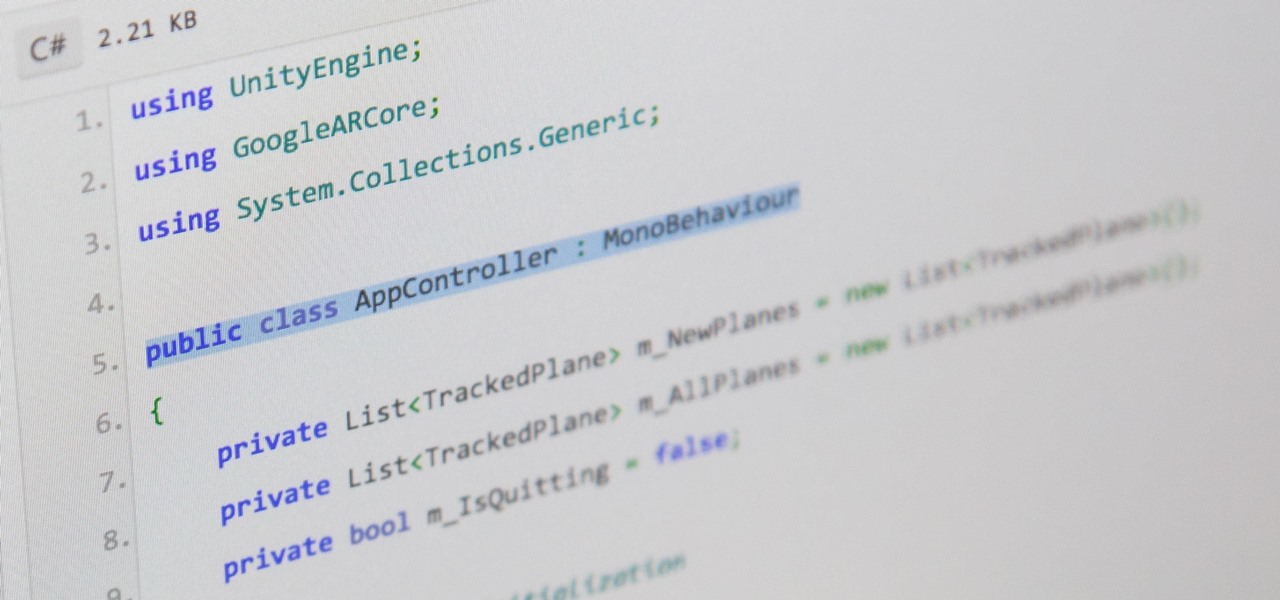
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

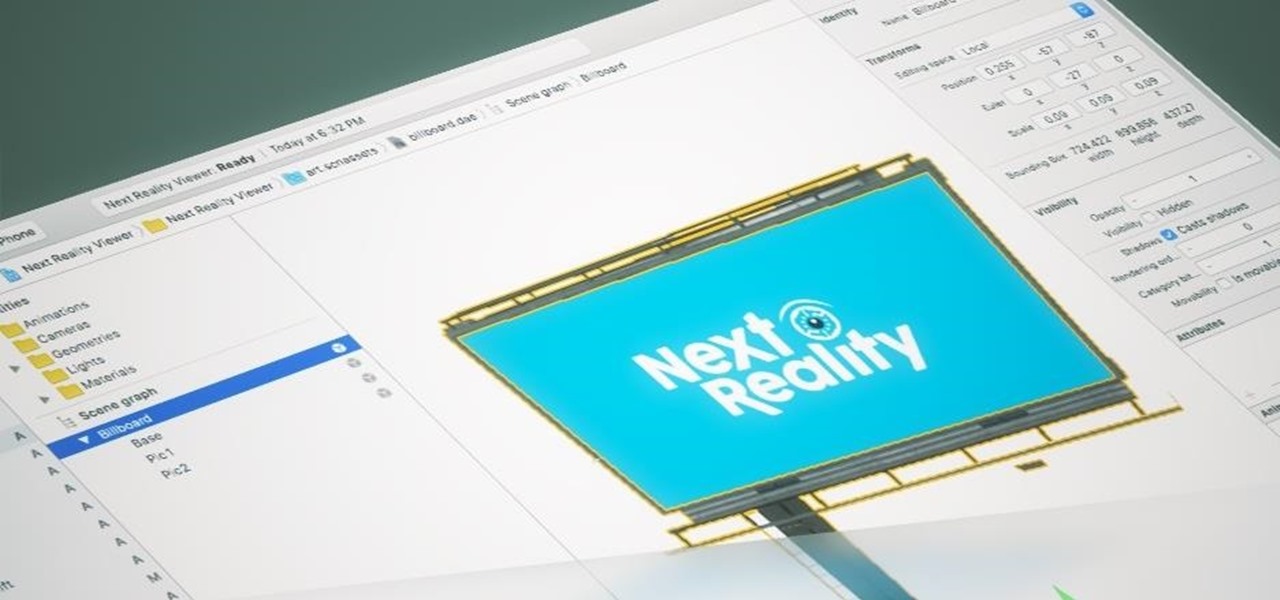
If you need a little inspiration for tonight's Halloween festivities, this augmented reality magazine cover featuring the Dark Knight himself, Batman, may do the trick.

The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

Oh, Waze—you know, that Google-owned traffic navigation app that tempts drivers into stopping at local food joints like Dunkin' Donuts and Taco Bell? Well, now you can even order a large iced coffee through the app before you even arrive at a fast food hotspot.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Hello NullByte! This will be my first How To series.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

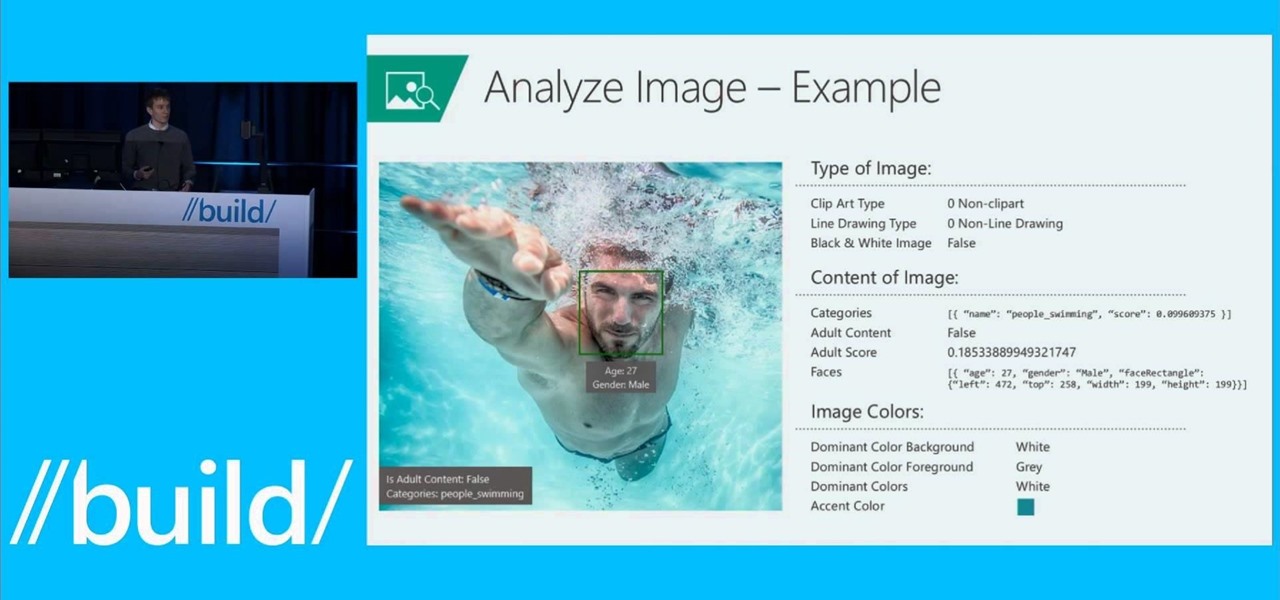
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

Welcome back, my greenhorn hackers!

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

This tutorial is about how to create the floating bar with social media buttons on a weebly website. Weebly has change its layout on the dashboard. Its a new video of new layout of weebly dashboard. I found many quesiton regarding 4 different HTML files instead of one index.html. Users were asking about in which they have to change the code so here is the solution. Watch the video, drop your comments and feel free to ask.

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

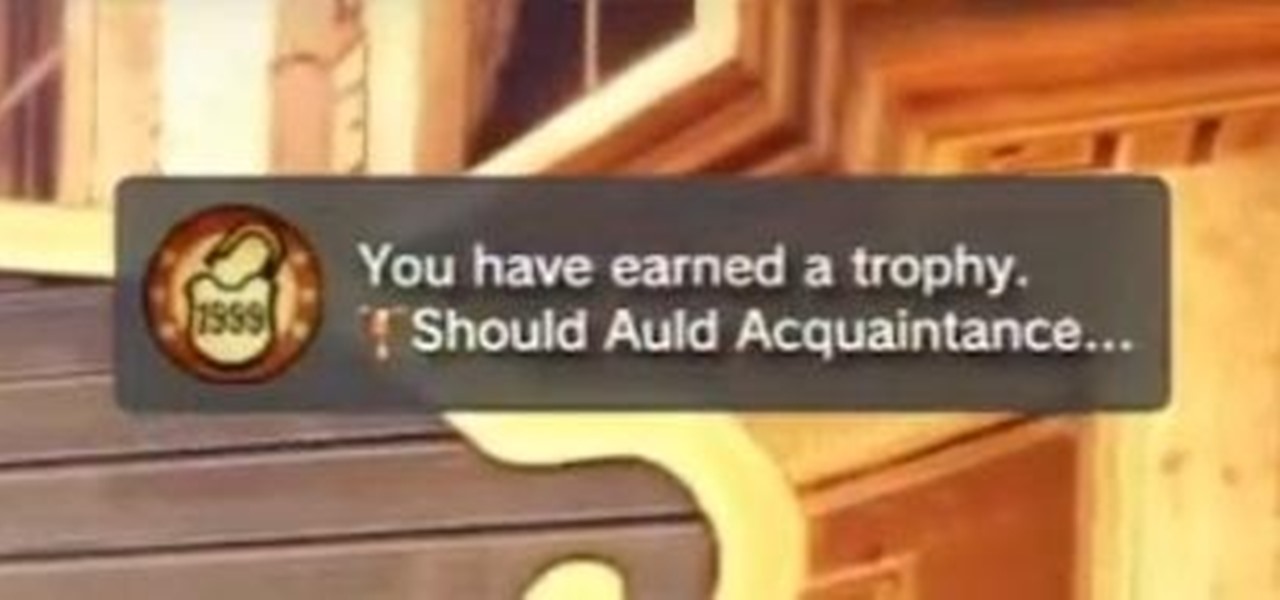
Is there anything better than finding a couple dollars sitting in your coat pocket that you forgot about? Well, after checking my trophy list for BioShock: Infinite, I realized that unlocking 1999 mode is actually an achievement. Hooray me. The achievement trophy is called "Should Auld Acquaintance", and instead of beating the game in easy, normal, or hard difficulty, you can just use the Konami code (found here) to skip right to 1999 mode and get that trophy.

This is a super cute girly pink punk nail design that is done in the backdrop of pink and black gradient - ombre nail art style!

You can make Siri do all kinds of things it was never designed to do. From installing it on older jailbroken iDevices to using it to bypass an iPhone's lock screen, people have managed to come up with some interesting hacks—and that's only the beginning.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

If you've ever wished you could keep tabs on the fish in your aquarium, Justin of Antipasto Hardware Blog has just the mod for you! He created this DIY "shark detector" that sends out a tweet whenever Bruce the shark breaches a perimeter that he set up in the tank.

Proud new papa Gjoci wanted to make sure he never had to worry about whether or not his baby girl was breathing, so he built this amazing breath-detecting baby monitor using a Wii remote, a printed circuit, and a laser. First, he opened up the Wiimote and took out the camera, then used an Atmel Atmega88 microcontroller to make a printed circuit. Low-power infrared lasers shine on the baby's clothing and the Wii camera detects the motion of the baby's breath, activating an alarm if the motion ...

This is OSCAR, the Overly Simplified Collaboratively Actuated Robot. He's built from an old Roomba and an Android tablet, and he's about to make Google+ a lot more interesting. The robot is controllable by users in a Google+ Hangout, allowing the audience to interactively explore OSCAR's environment via his on-board camera.

Knots are very useful for all types of situations. The video will show you how to tie a double over hand knot. You basically tie a loose single knot and then pass one end around again and back through the loop to make it a double knot. This looks like a pretty strong knot so try your hand at it.

This instructional sewing video shows an easy way to tie a knot in your thread for hand sewing an quilting. This is a simple sewing trick, but it's worth taking the time to learn how to tie a failsafe knot. Don't let your sewing projects fall apart at the seams.

Sandy from Afloral.com shows you how to make an elegant hand-tied bouquet using calla lilies with this flower arrangement tutorial. This is a classy bouquet for a bride or a bridesmaid. Watch this how to video and you can make this hand tied calla lily bouquet in no time.

In this tutorial, Sandy from Afloral.com shows you how to make a vibrant hand-tied gerbera daisy bouquet. This is an adorable, cheerful flower bouquet for a wedding or formal event. Watch this how to video and you can make a hand tied gerbera daisy bouquet in no time.