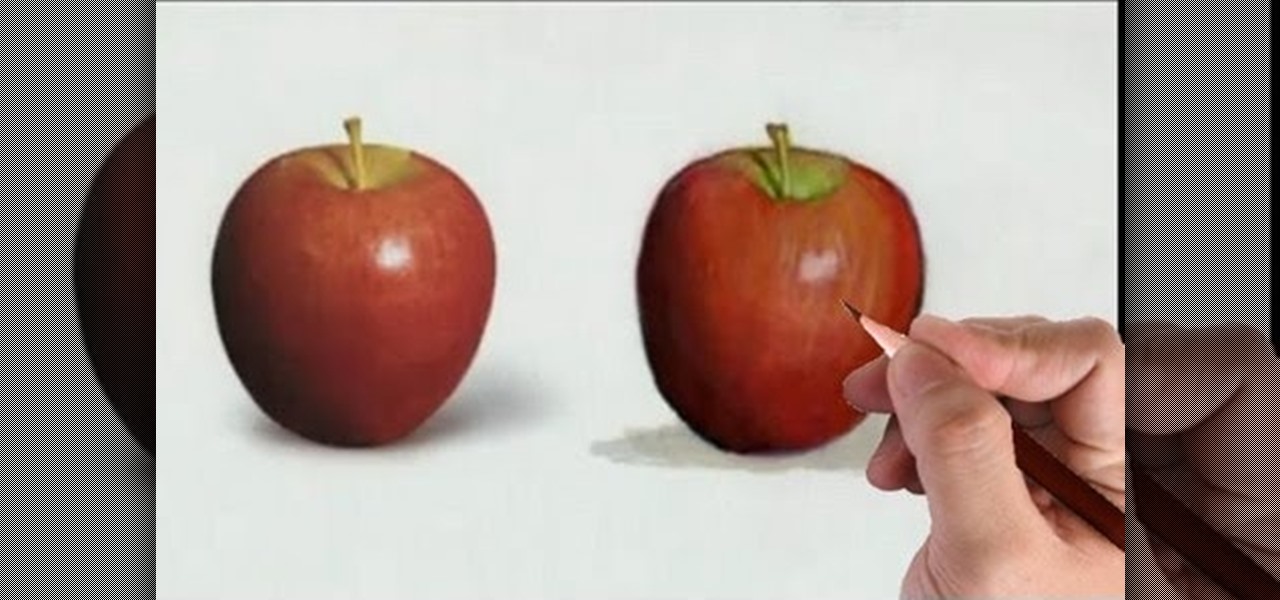
This video quilting tutorial shows an easy way to attach fringe onto a quilt. Tied thread fringe is a great way to add simple decoration and definition to a quilt. Learn how to tie fringe onto a quilt by watching this instructional video.

Ties and slurs look very similar but are not the same musical notation. This music theory how to video teaches you the difference between ties and slurs and how to play them.

Learn how to tie saltwater flies using new fly tying materials and techniques. These flies are for redfish, snook, tarpon, bonefish striped bass, and many other species.

The Art of Fly Tying shows you how to tie a Green Caddis Larva (Step by step) for fly fishing.

This video shows you how to properly use ratchet tie down straps. It would be a good idea to keep these in the back of your truck or your car to tie down stuff.

This video will show you how to tie a spider's hitch, probably the quickest & easiest way to tie a double knot for fishing.

'Loose Change' is cool secondary quest in Dragon Age 2 that varies depending on whether you chose to be a smuggler or a mercenary when you enter Kirkwall. This video will walk you thorough the mercenary version of the quest, allowing you to, in fact, tie up your loose ends.

This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

This video gives you four steps on how to properly break into a baseball glove. If a glove isn’t correctly broken into, it may affect a player’s performance. The first step is to condition the leather, softening it by adding either glove oil or cream. Remove any excess oil with a paper towel. Make sure to repeat this step throughout the year. The second step is shaping your glove by placing a ball where you would normally hold a baseball and then tying two large bands around the glove in ...

In this Music & Instruments video tutorial you will learn how to change the nylon strings on a classical guitar. Take the peg winder and unwind all the old strings. Then unravel all the strings from the bridge. Make sure the bridge doesn’t fall off. Take a new string and insert the finished end in to the sixth hole passing it from the hole of the guitar towards the end of the body. Then tie a knot and pull the string tight over the bridge as shown in the video. Now pass the unfinished end o...

A demonstration on how to make a lucky star from folded paper with origami is shown in this video. For this you need to get a strip of paper. Attractive papers are available at the stores for this. First to start up take an end of the strip of paper and tie a knot, flatten it and bring it as close together as you can. Then with the small free end fold it in, flip it over fold the long free end in such a way as it gets a pentagon shape. Next flip the free end over the edges. Continue to turn i...

Benson Trenh and Mark Norris show viewers how to build a bottle rocket using common household items. To build this creation you will need tape, a hole puncher, scissors and string. Also use a black plastic bag, or any color, for the parachute! Cut the black plastic bag into a square, any size you would like! Next, take the square and punch a hole at each edge of the square and string the string through the hole tying a knot. You should now have the parachute! For the body of the rocket, get a...

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

Watch this fine art video tutorial to learn how to illustrate with markers and colored pencils. "This video shows my process for making an illustration (non tradigital). I use illustration markers (usually prismacolor) and color pencils (usually prisma once again) and a wax blending stick. I make my illustrations in two steps:

This tutorial will show you how to take something simple like brown paper bags and curl you hair with them.

New techniques may improve a swimming pool workout from Masters coach Nancy Kirkpatrick Reno. Before sticking a toe in the water, consider this advice: * Swim in a pool that's at least 20 to 25 yards long; those pools can usually be found at high schools and some gyms. A 50-meter Olympic-size pool is best, but not everyone has access to that. "If you're going to become a lap swimmer," Kirkpatrick-Reno says, "you can't go any shorter or you'll be constantly turning." An outdoor pool is prefera...

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Apple just released the first developer beta for iOS 13.4.5 on Tuesday, March 31. The update follows the previous week's stable release of iOS 13.4.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

Lover it or hate it, Android 10 is a big improvement over Android 9 Pie. Based on previous versions, most flagships released in the last two years will get Android 10, but the question is when. So while you wait for those cool new gestures, how about I show you an app that gives you a nearly identical experience?

Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.

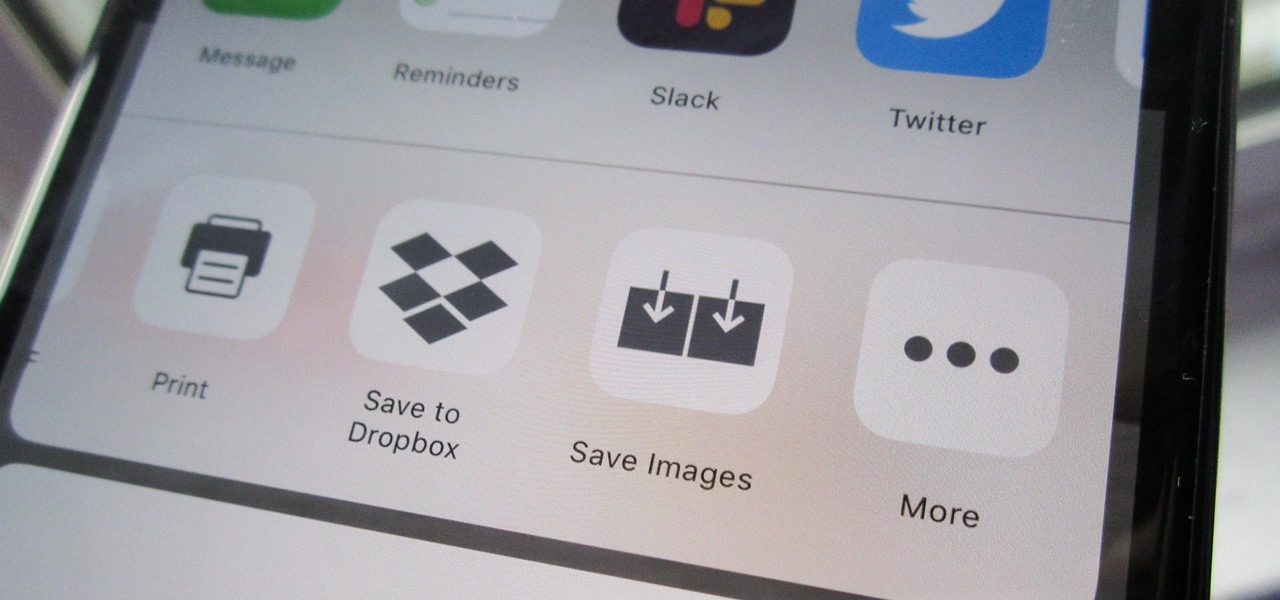
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

On Tuesday, at the Unite Berlin developers conference, Unity unveiled new tools designed specifically for augmented reality that could literally raise the technology to the next level.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

While TouchWiz as an Android skin isn't a favorite among many, Samsung Internet is a fantastic web browser that S9 owners should be happy to have preinstalled out of the box. But you don't need to buy Samsung's latest flagship to try their browser — Samsung Internet is available to all compatible Android phones.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

Thanks to iCloud and AirDrop, it's really easy to sync photos between an iPhone and a Mac. But if you have an Apple phone and a Windows computer, this process isn't quite as simple. Thankfully, Microsoft has just released a new iPhone app that makes it a breeze to move photos and videos from your iPhone to your PC.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

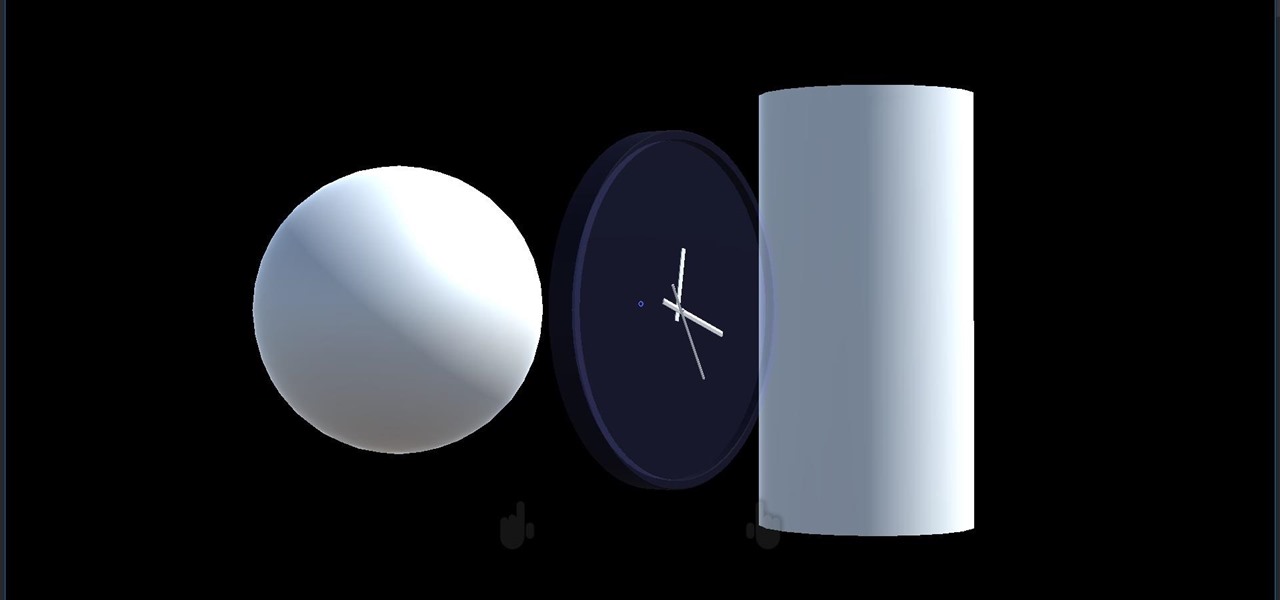
We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.