As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

For those of you still waiting for the new iPhone 5, you may be a little annoyed when you start using the new Maps application. If you're one of the many Apple users that has already updated your current iPhone to iOS 6, then you're probably already missing Google Maps. While the new Maps does have turn-by-turn directions and sweet 3D imaging for a few large cities, it misses out on everything that made Google Maps legit. Public transit routes—gone. Street-view—missing. High-res imaging of sm...

If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots.

I collect straight razors from the Victorian era and then add some steampunk style. Step 1: Remove the Old Scales
Let's face it, pretty much everyone has an automatic dishwasher. They are super convenient and are becoming cheaper to allow the general public better access to them. With that being said, though, dishwashers are also becoming a lot smaller.

Not sure what to do with that old 2G iPhone now that there have been three newer versions since then? Don't toss it or let it collect dust! Jump on the Droid bandwagon and turn your old Apple device into an Android just like the EVO. This hack will require a little fancy computer work and a jailbroken iPhone, but it will allow you to access the entire world of Droid without buying a new smartphone. Cool!

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack cash in Restaurant City (07/02/09).

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack the food quiz in Restaurant City with Cheat Engine (09/10/09).

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack eating and cooking speed in Restaurant City with Cheat Engine (09/08/09).

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine (09/08/09).

Have you ever wanted to collect fossils, but just couldn't find them? Well, don't give up, keep trying, and when you do finally find a fossil, it will be followed by more and more as you get used to where and what to look for.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

You may have beaten God of War before, but have you collected all of the treasure chests throughout the game? No? Then it's time to try again. Grab your copy of the classic PlayStation 2 game and get ready to break some records, because this 52-part walkthrough will not only show you how to defeat the full game, but it will show you the locations for all of the treasure chests. Yep, this shows you 100% of those treasure chests. So, if you want to play again in a different way, this is how you...

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

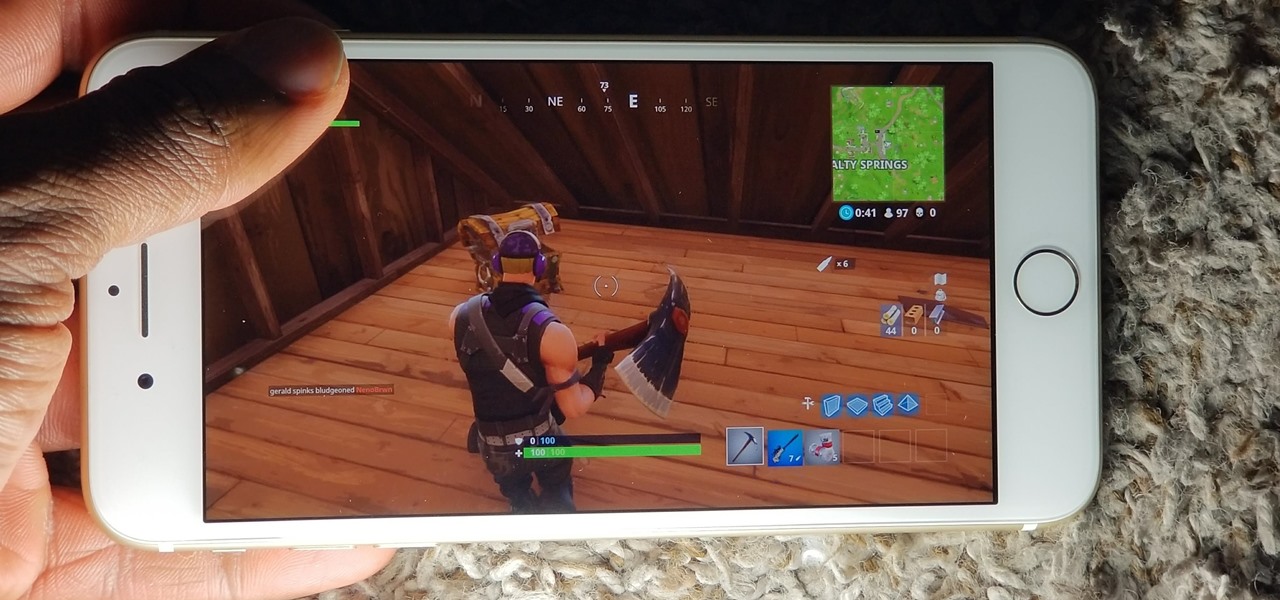
While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

War leaves a lot of stuff behind. Torn families, delegitimized institutions, mass graves, and unexploded ordinances litter the post occupation landscape. Whether or not you have driven the imperialist out, or are still in the phase of armed resistance, you will need the ability to safely diffuse bombs. My bomb defusing Silvia-bot can do it all. She can catch grasshoppers, cut wires, collect samples, tase enemies and even play chess! Materials

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

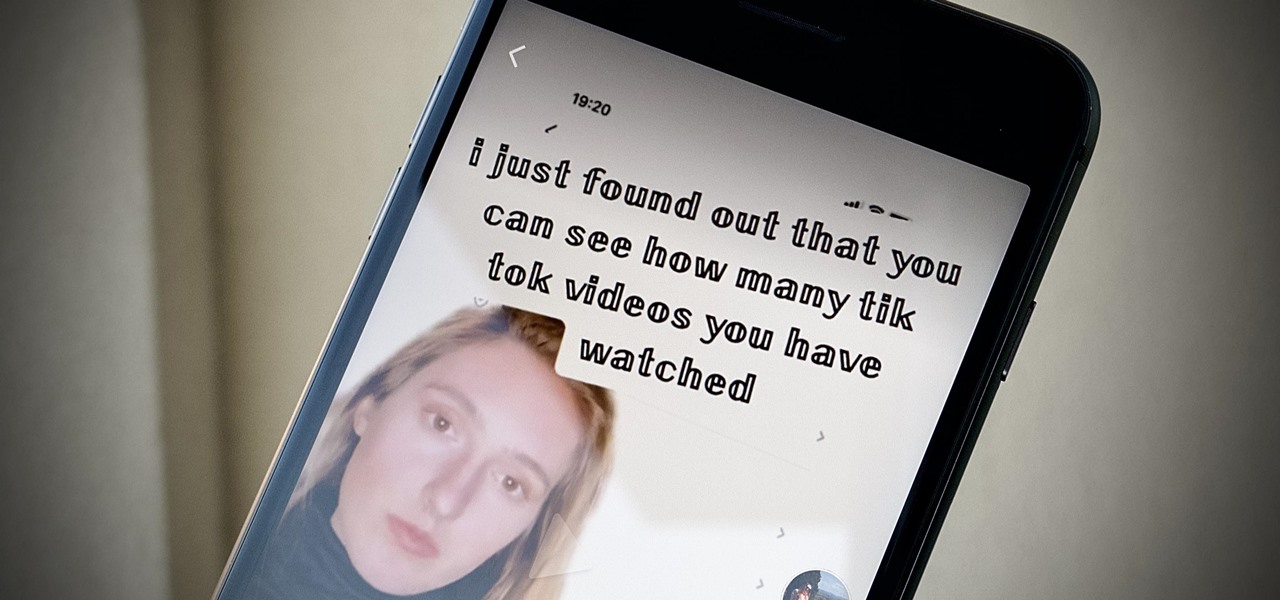
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

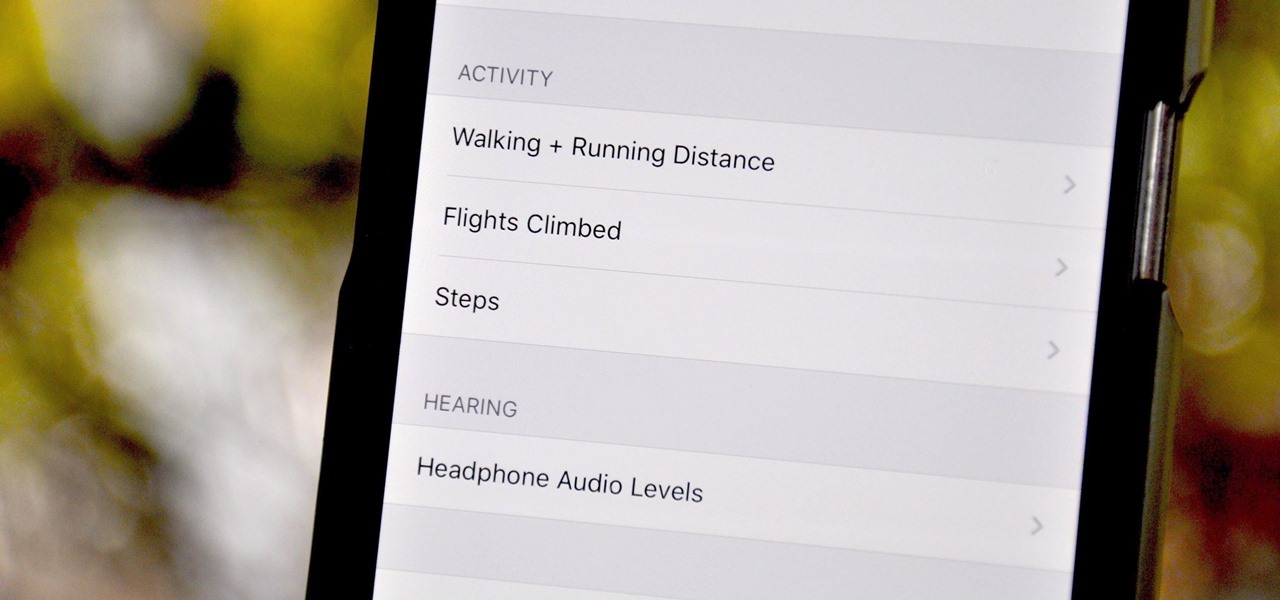
Your iPhone tracks how many steps you take, how far you walk, and how many stairs you climb each day. That may seem a bit frightening, but it's all for a good reason: the Health app stores this data so you can view your progress in one place. But interestingly, opening the Health app isn't the easiest way to view this info.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

Despite hints hidden in internal iOS 13 code, Apple did not unveil its long-rumored smartglasses at its annual iPhone launch event on Tuesday.

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.