
How To: Recover if you have been a victim of identity theft
If you have been a victim of identity theft, you are not alone. This happens to millions of people every year.


If you have been a victim of identity theft, you are not alone. This happens to millions of people every year.
Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

In this video from the ID Theft Center, learn exactly what identity theft is and how to prevent it from happening to you. Identity theft can happen to anyone - young, old, living, dead - thieves do not discriminate. This helpful video will tell you exactly what to look out for and how to avoid scams. Your host will explain how identity thieves operate and how to cut them off at the pass.

In this video, presented by the experts at the St. Louis Community Credit Union, learn how to prevent thieves from stealing your identity or account information. These days, between paper bills, Internet banking, social networking and all the other ways we interact, there are many ways for crooks to get into our private lives.

This video shows the method to prove some trigonometric identities. This involves the use of algebra and knowledge of basic trigonometric identities. The video demonstrates three examples to illustrate this problem and its solution. The first problem shows a relatively simple problem involving sines and cosines. The video shows some basic algebra steps to simplify the problem and prove the identities. The second example involves a slightly complicated problem involving square of combination o...
Identity theft can happen anywhere, even in social networking. Why are we so careful when using our credit cards online but not when we sign on to Facebook?

One of the best features of Apple's Final Cut Studio is the graphics interface feature Motion. With its ability to create and edit motion graphics, you can easily create title sequences for your indie film, or maybe even a professional movie, with 2D or 3D visual effects compositing.
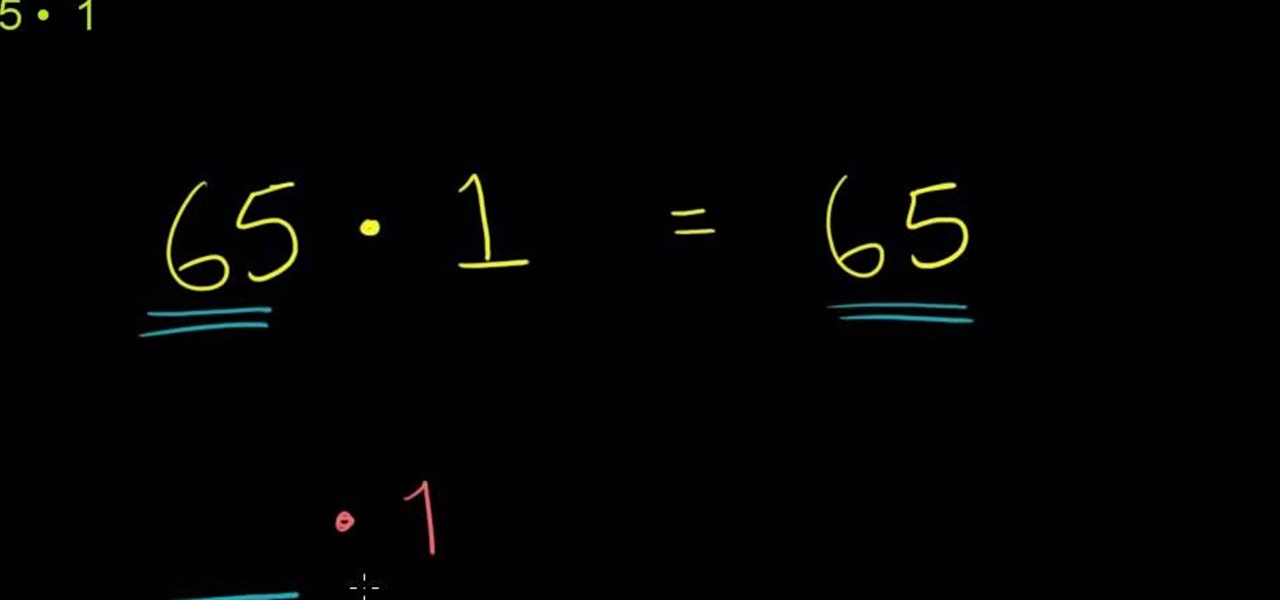
From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to unpack and solve word problems requiring use of the identity property of 1.
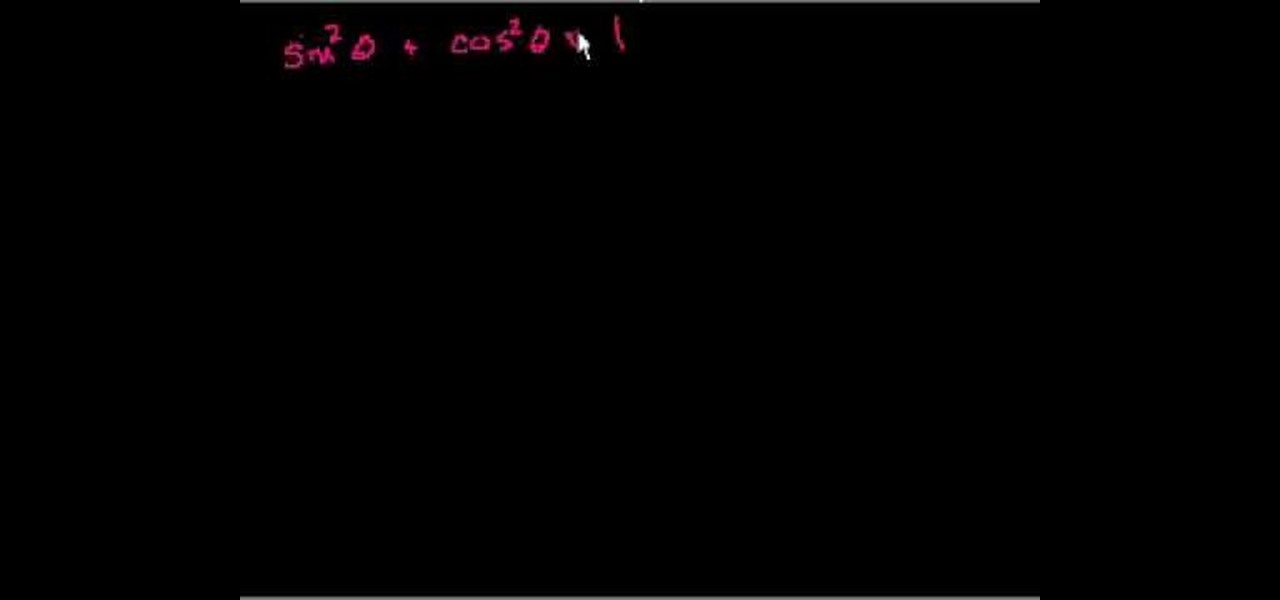
Need help wrapping your head around trigonometric identities? Watch this free video trig lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll l...
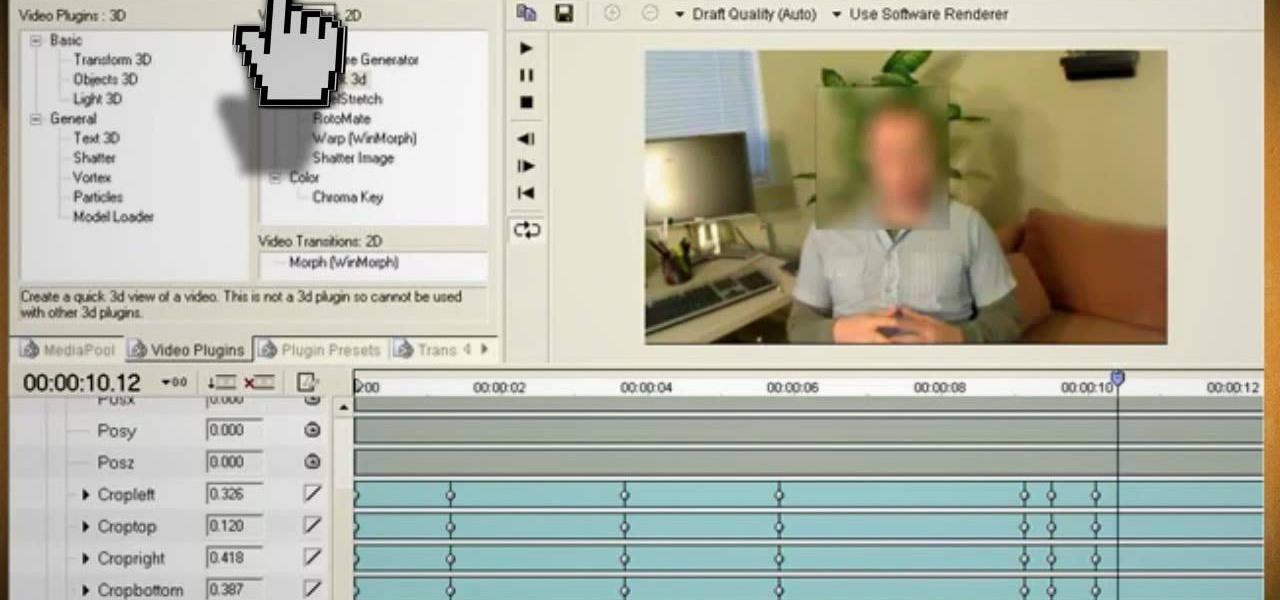
Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

When you watch the news or a television show where someone doesn't want to be identified, it is common to see the face blurred out or obscured. In this Adobe Photoshop tutorial you will learn how to blur someone's face in an image and preserve or hide their identity. So if you are producing videos or podcasts or need to hide part of an image, this tutorial will show you how to do it in Photoshop.

What better way to finish off your Thanksgiving meal than with a nice hot slice of apple pie? As Thanksgiving as Thanksgiving desserts come, apple pie has mesmerized our collective taste buds since it was invented because of its perfect balance between tartness and sweetness.

In this video by knot tying collective Tying it All Together, you'll learn how to create a wide Solomon bar knot, which is composed of two differently colored ropes that brush against each other in near parallel formation.
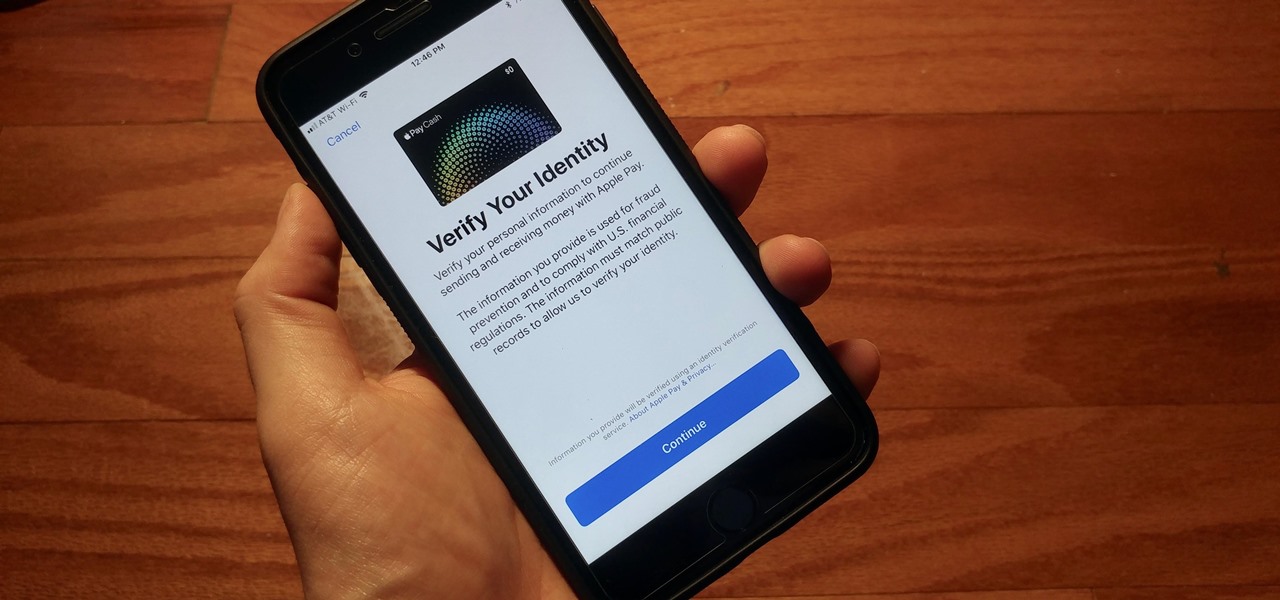
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.
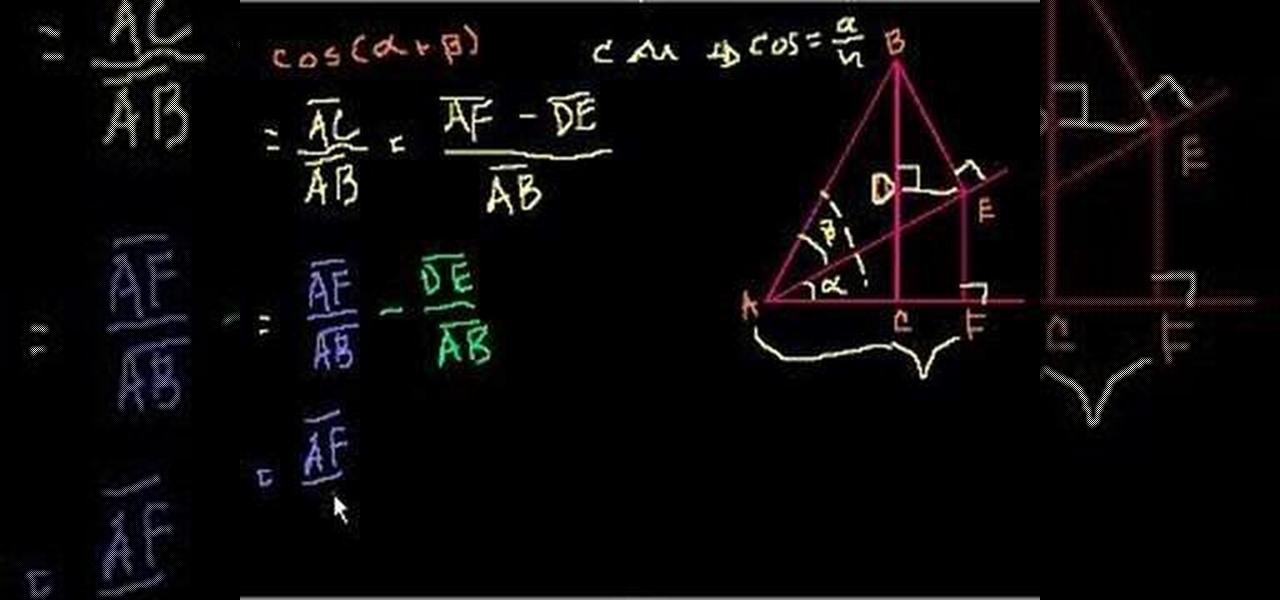
Need help proving the cos(a+b) = (cos a)(cos b)-(sin a)(sin b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series ...

There’s only one you, right? WRONG! There’s a lot of bad apples out there, and If you’re not careful, they’ll steal your identity in an artichoke heartbeat. So remember to watch your tail!

Super heros' secret identities are their most guarded secrets. Many choose to protect them with masks, but how to make your mask if you're a new superhero or a filmmaker trying to simulate a super hero? This video will show you how to make your own cheap superhero mask at home, which will be a great prop for your next film or Halloween costume.
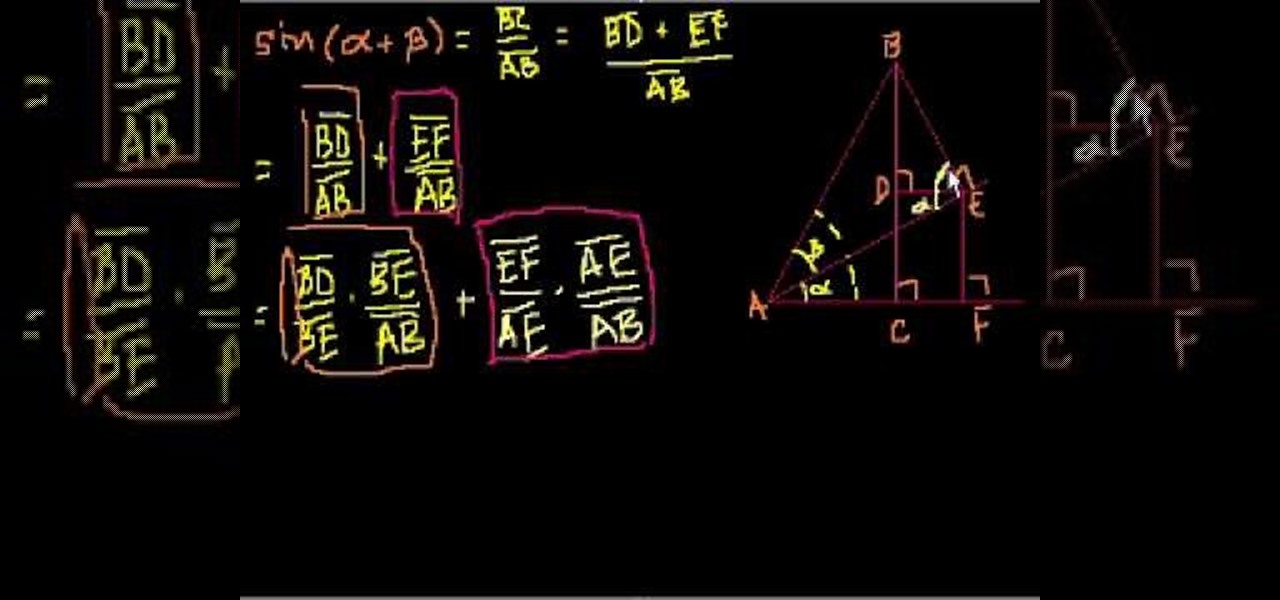
Need help proving the sin(a+b)=(cos a)(sin b)+(sin a)(cos b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of...

Last year, Lytro released their first light field camera to help photographers have more control over focusing. This innovative and revolutionary camera allows users to change the depth of focus of a photograph after the picture is taken.
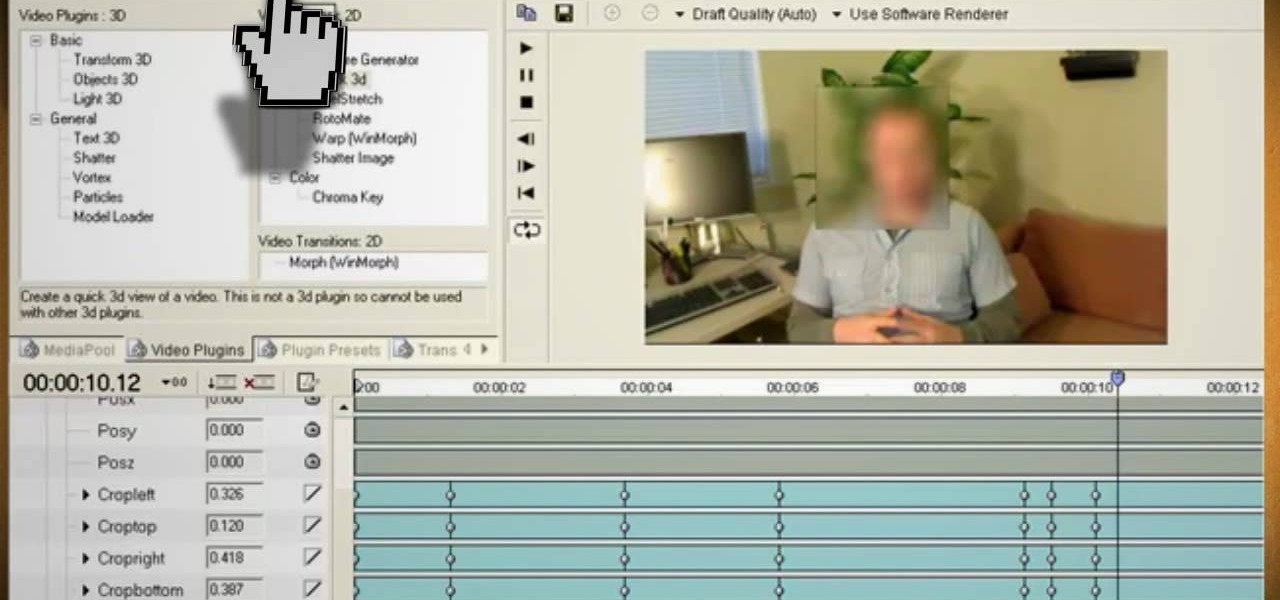
This video will show you how to use video and audio to hide your identity. After you have your audio and video you will need a converter program, for example Format Factory which will convert the audio and video into the necessary formats. You will be encoding your clip as an AVI Video, as well as MP3. To start you will need to change the pitch of the audio track. A good program to use for this is Audacity. Play around by making the pitch either higher or lower. Save it as a Wav file To edit ...

First you want to find X using the identities given for a 45-45-90 triangle. When comparing the triangles in the video, we find that X must be 6. Next, use the identity to solve for the measurements of the sides of the triangle. In the video example, 6 is the length of the two sides and 6 times the square root of 2 is the length of the hypotenuse. The video is very short and does not explain a lot of things in detail, but that is because the examples are easy to figure out.

So, how does someone keep their hacking life completely secret? What This Is:

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

This is a tutorial on Rerooting Blythe Doll Hair from the CRAFT Video Podcast. Blythe dolls are great for making three-dimensional self portraits. There is an enormous community of customizers working with the Blythe Doll. One of the main online sources for customization is Puchi Collective, which houses oodles of tops for changing her eyechips, face makeup, and clothes.

This card looks fabulous and it is so easy to put together, the longest part is cutting the paper, but if you enjoy papercutting then this is just for you, however you could adapt the design and use the full Rope design paper from Anna Griffin to create this beauty. I have used embellishments and paper cut shapes to add to the card front and create something really cool. Step 1: Now Watch the Tutorial

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

GO BANANAS in collaboration with Transhuman Collective presents Mumbai in spectacular Augmented Reality. The visitors at the MCHI Property Show 2013 had a blast while experiencing different elements of Mumbai in this surreal zone. They travelled inside future Mumbai, took blessings from Lord Ganesha, Broke the Dahi handi, The Dabbawala delivered them lunch and could play the hero inside a Bollywood action shoot.
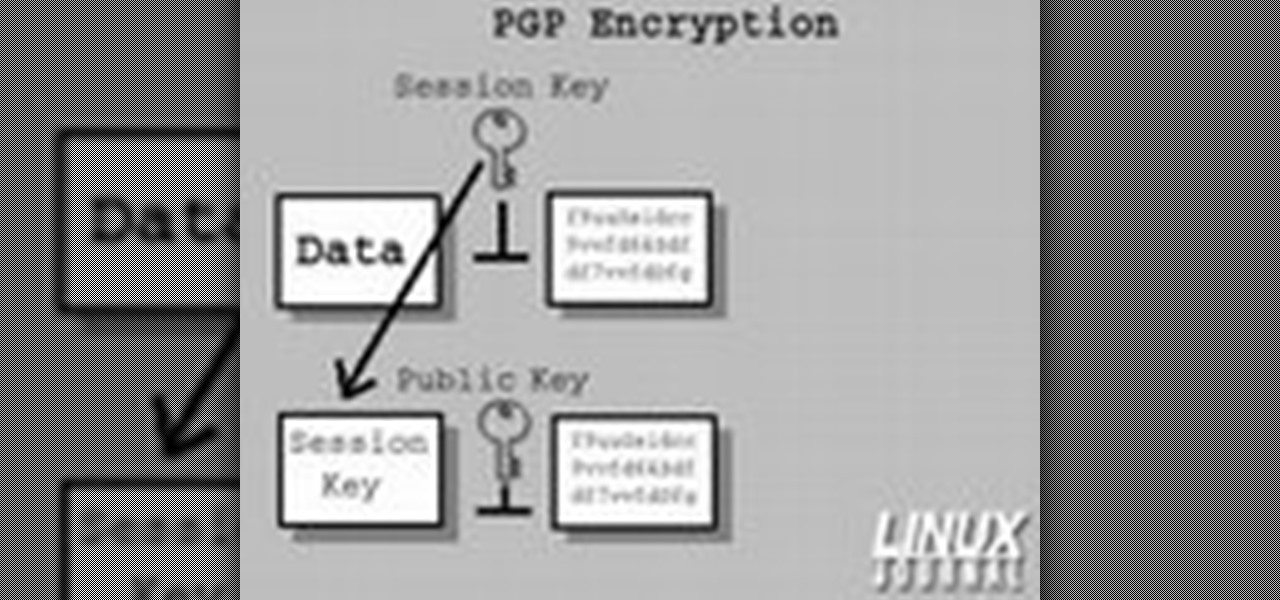
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.
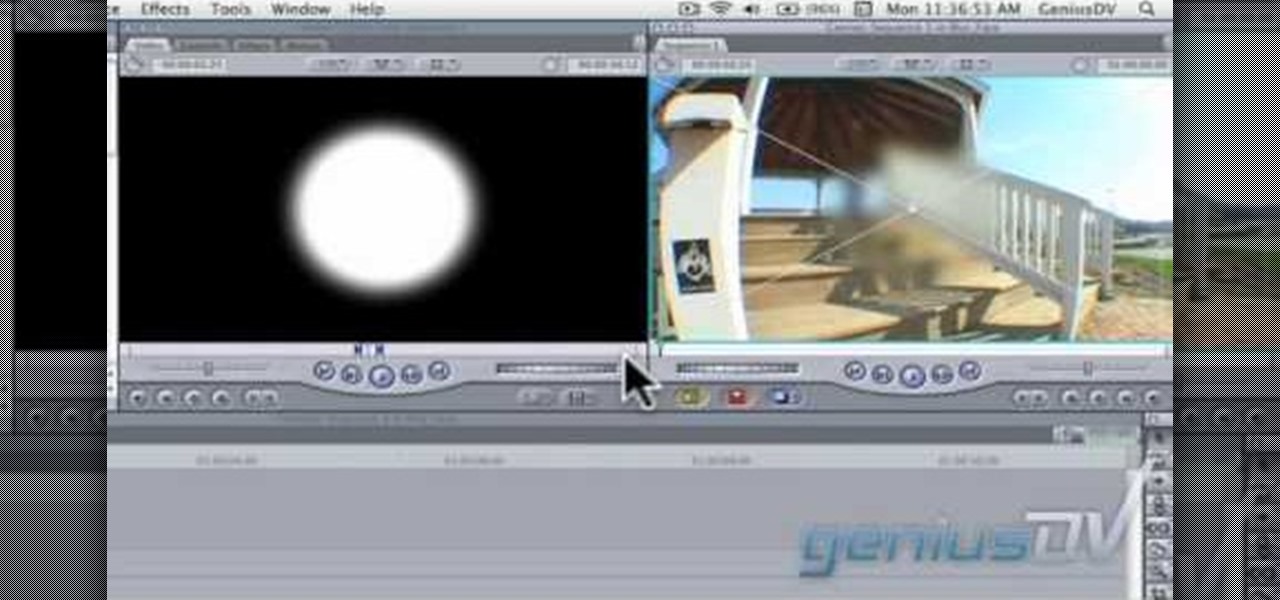
In this clip, you'll learn how to blur out a person's identity with matte tracking in Final Cut Pro or Express. Whether you're new to Apple's Final Cut Pro non-linear video editor or just want to better acquaint yourself with the popular video editing program, you're sure to benefit from this video tutorial. For more information, including detailed, step-by-step instructions, watch this tutorial.
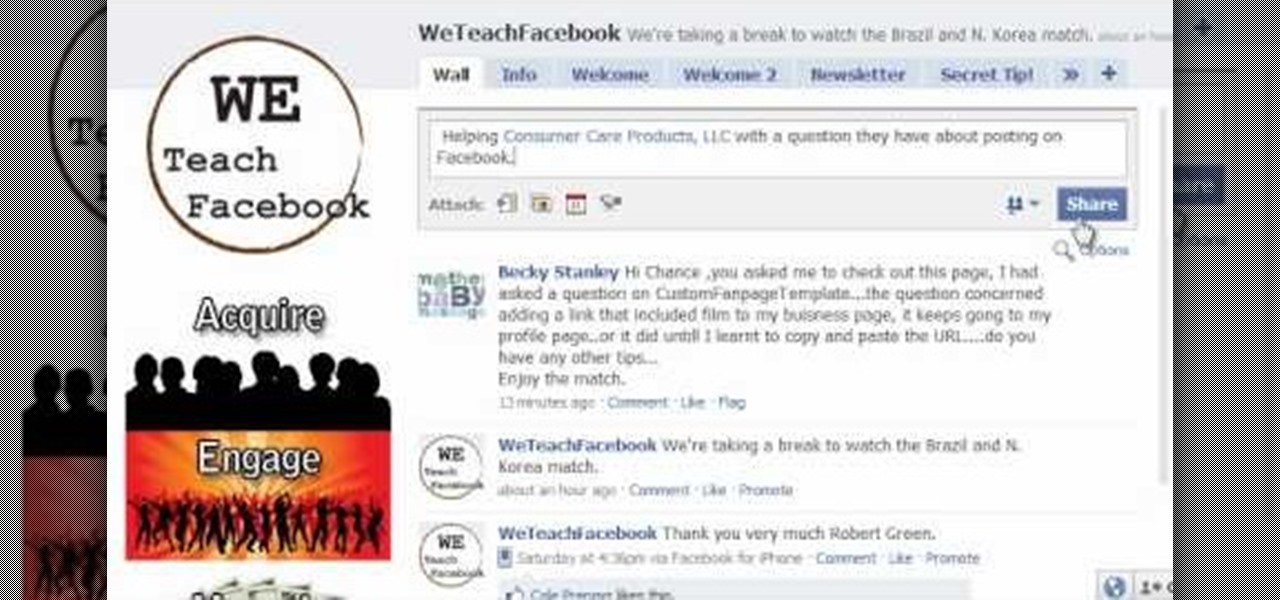
In this tutorial, learn how to use your Facebook Fan Page to comment and write on other people's walls like you would a personal account. Your fan page is linked to your personal page, and sometimes you don't want to use your real identity to write messages. Check out this clip and get the hang of a FB glitch that will allow you to "tag" your friends so you can write on their walls.

If you've ever participated in a Anonymous protest against scientology or celebrated Guy Fawkes day, you probably know that drinking through a Guy Fawkes mask is tough, especially if you're keeping your identity a secret. Watch this video to hear an Anonymous member explain how to drink water without compromising your anonymity.
Looking for an easy way to make certain that your sensitive personal information is secure? With Identity Finder, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, take a look.
Got something to hide? Learn how to censor or "GMask" an image simply by using the Mosaic option in PhotoFiltre to pixelize the entire thing or just a small (Naughty!) area. It's not that difficult to protect the identities of the not-so-innocent, especially after following the instructions in this video.

Need to change your IP address? In this how-to, you'll find instructions for changing your IP address from the Windows command prompt with the ipconfig console application. For step-by-step instructions, take a look. NB: Changing your IP will not protect your identity; it's merely a simple expedient for getting around certain problems ones might encounter while using the Internet.

Today's word is "incognito". This is a noun, adjective and adverb. As an adverb it means without revealing one's identity.

Steal someone else's fingerprints, use identity thief powders, & photograph the prints. Print the 3d prints & adhere to your fingers!

Liquid Pop Collective put this video out some years ago; adding digits to your Liquid makes it far more stylish and sophisticated than just relying on the old hand-chasing alone. This is an advanced hand-chasing technique.

Liquid Pop Collective put this video out a few years ago; it is quite effective in breaking the style down into it's "learn-able" pieces. This video breaks down the popping techniques used in Liquid dancing.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.