
How To: Write an autobiography
No matter what age you are or what kind of life you've lived you can put your story out there by writing an autobiography. Every life can be interesting if written about in a well formulated, and honest manner.


No matter what age you are or what kind of life you've lived you can put your story out there by writing an autobiography. Every life can be interesting if written about in a well formulated, and honest manner.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.
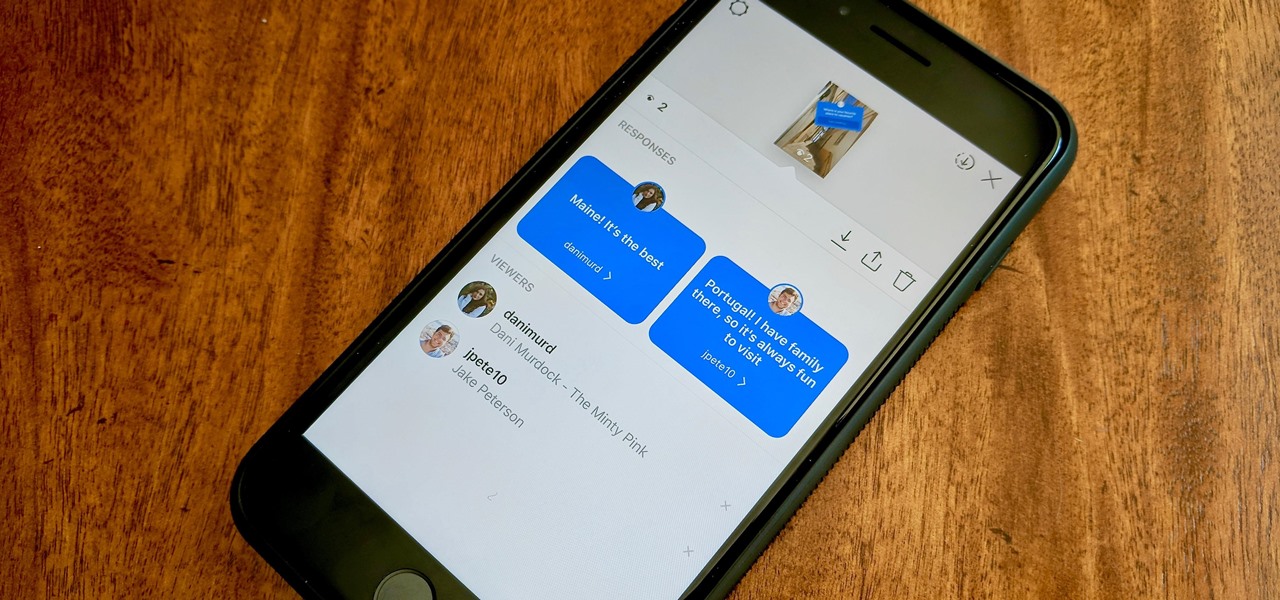
Users on Instagram have taken the app's new "Questions" sticker and run with it — it's tough to find a story in your feed that doesn't proudly sport "Ask me a question." However, it appears there's some confusion when it comes to the anonymity of your answers to these questions. News flash — your username is attached to every response.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Just yesterday, Google announced that it is banning all apps that contain any form of lock screen ads. Today, they posted a list of the Best Apps of 2017 for the Play Store. Given the new policy of cracking down on apps with advertisements on the lock screen, you wouldn't expect to see one of those in the list of top apps. Unfortunately, that's exactly what happened — Google is promoting obvious adware in their list of best apps.
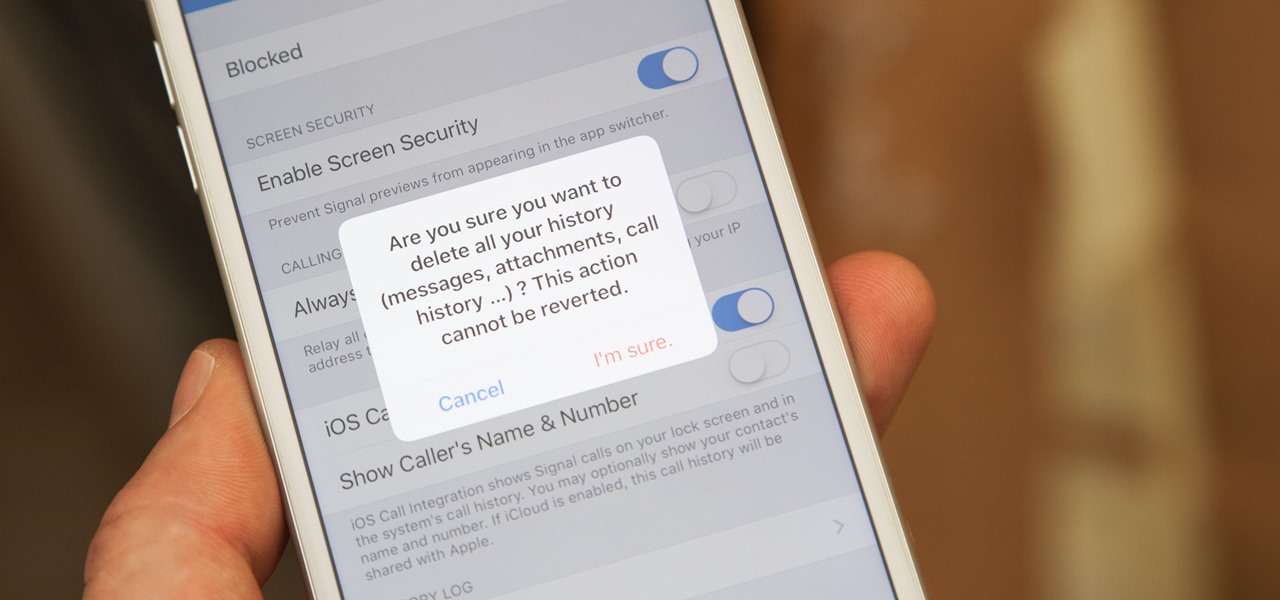
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

If you thought the selfie would only ever be used to bombard your feed on Instagram, you were wrong. Dead wrong. JetBlue is looking to take those selfies and use them to check you in for your next flight.
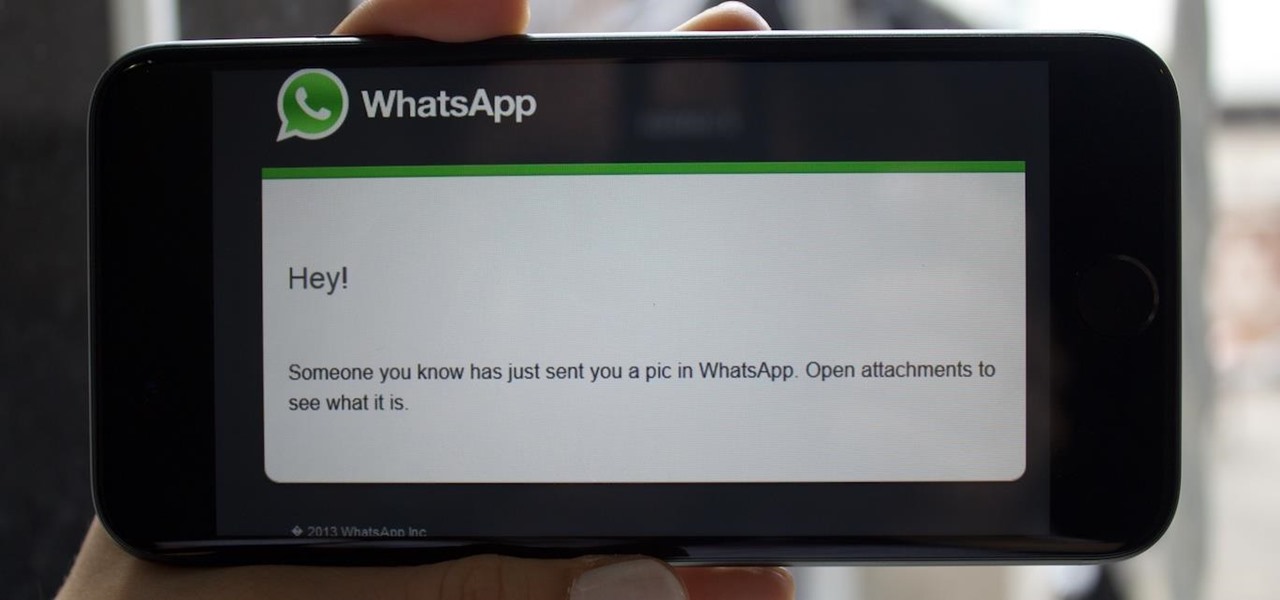
If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update.

If you're in the market for a new tattoo, the biggest hurdle to clear is imagining exactly how it's going to look. It's going to be part of your identity for the rest of your life, so you have to make sure it looks just right—or as your mom probably told you, "Think of what it's going to look like when you're 60."

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

While text messaging has become one of the most frequent ways we communicate with our friends, the missing body language, tone of voice, and eye contact can make it difficult to tell when someone is being dishonest. That said, it's not impossible. There are a number of subtle hints you can train yourself to recognize that will to help you detect written lies hiding in your SMS and iMessages. Here's what you should look out for.
These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.
Part of the process to answer the topic question is to discover the answer to three other questions, which are: (1) Who am I? (2) Who do I want to help? (3) How do I want to help?

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.
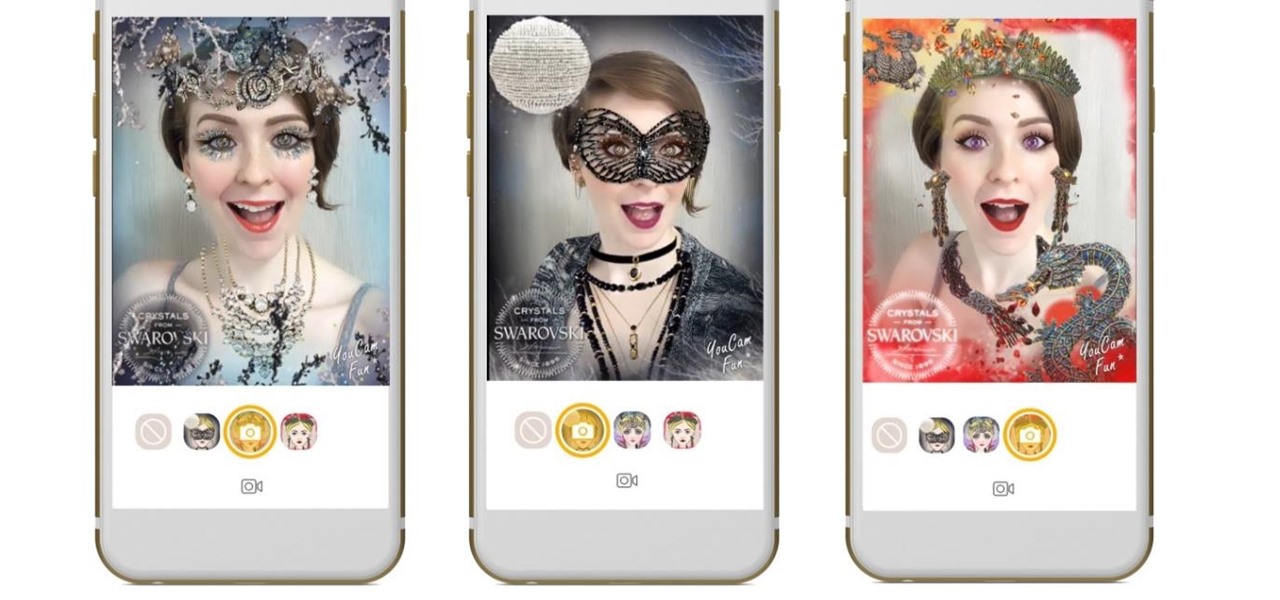
Nowadays, with the convenience of online shopping, brick-and-mortar retailers and malls have to work harder to draw shoppers to stores. This year, many of them are turning to augmented reality for assistance.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.
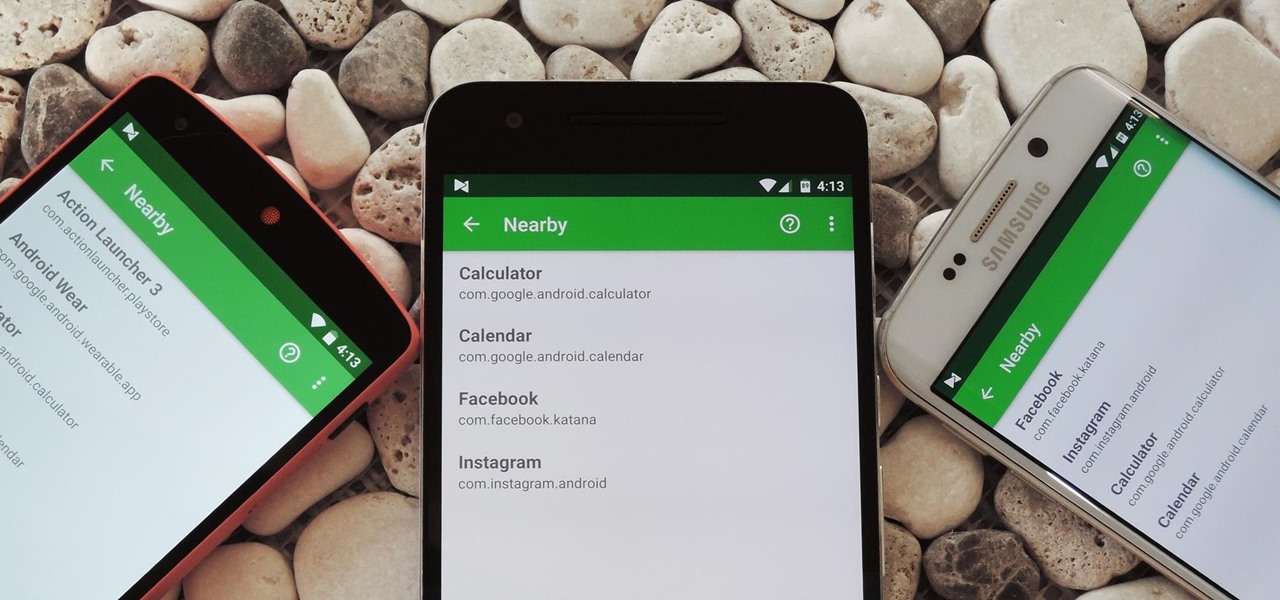
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.
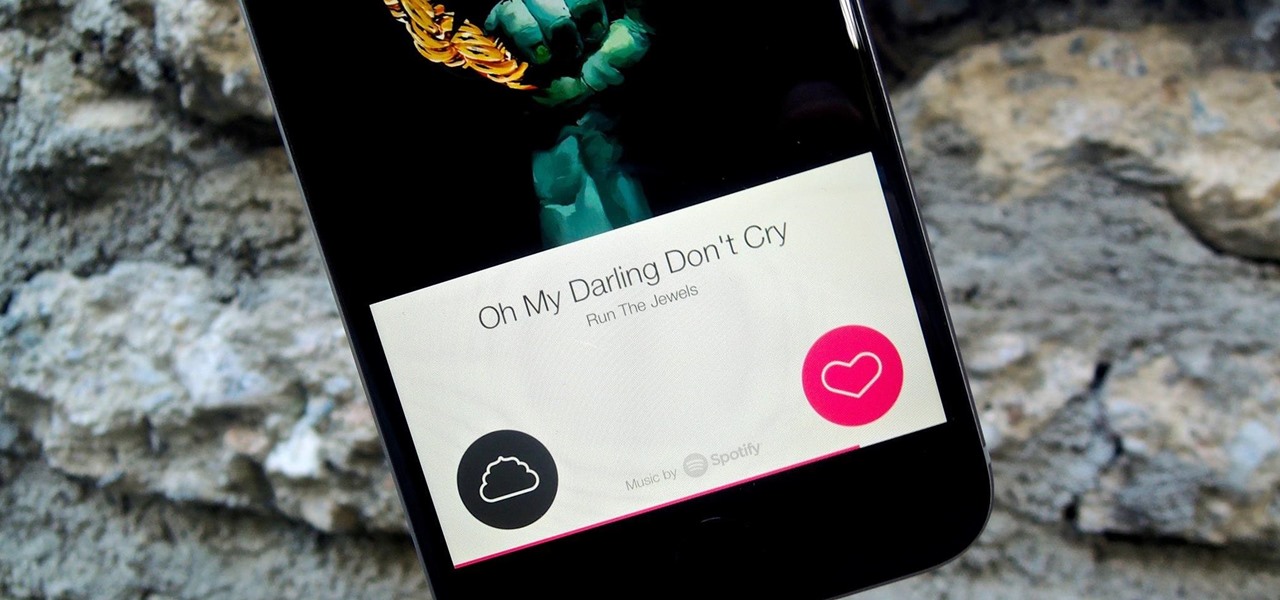
Everyone's a music aficionado these days. Whether you're having a party or on a road trip with friends, someone is always complaining about the music. There's no possible way to satisfy everyone, so instead of having your music drowned out by persistent nagging, turn Spotify into a democracy, allowing the consensus to pick what plays.

Believe it or not, the 2012 Presidential Election is (finally) almost over. While most of us are breathing a collective sigh of relief (no more political ads!), it still seems like it hasn't been that long since the last election results were announced. This time, though, one of the biggest differences is how people will watch. Since traditional cable is on its way out, and mobile devices are getting more popular every day, a lot of people will be watching this year's election results online ...

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.

It appears we're in the midst of an augmented reality art boom, because in the same month that the famed Christie's auction house launched its mobile AR app, leading art gallery and art seller Saatchi Art has also announced its entry into the AR space.

Crafting is an important aspect of Animal Crossing: Pocket Camp, as it helps you get animals to come to your campsite. However, it's also one of the best ways to get ahead in the game, and there are a number of reasons for this.

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

It seems that mobile app developers are constantly coming up with new ideas to apply augmented reality, with Apple's ARKit promising to increase adoption in apps exponentially.

Your friends are ditching Snapchat for Instagram. After the social network turned camera company announced it lost $13.30 per user in its first quarter as a publicly traded company, well, it doesn't look too good for the platform's future, y'all.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.