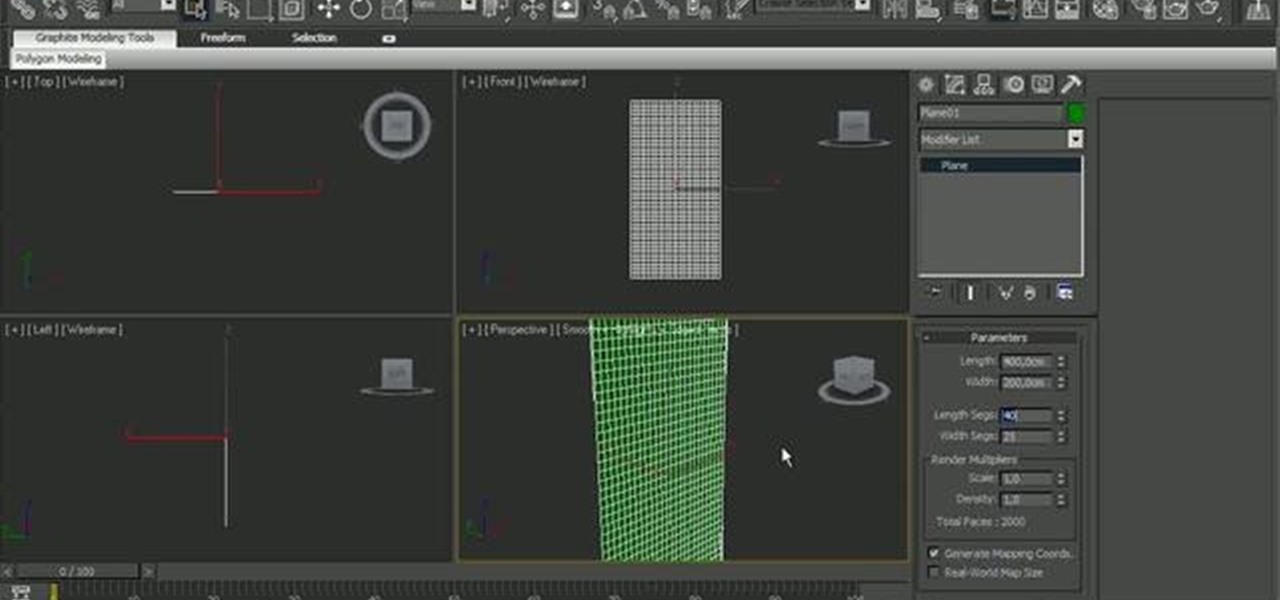
In this clip, learn how to simulate a hardbody collision with cloth in MAXON C4D. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own Cinema 4D projects, watch this 3D modeler's guide.

Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision.

This tutorial shows you how to apply collision tools to a static mesh in the Unreal Tournament 3 Editor (UT3).

A tutorial covering a classic rigid body simulation of ball crashing through a wall of bricks. The first two parts cover building a (procedural) brick wall, and the final two parts cover converting it into a RBD simulation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed...

Particles are a great world to explore. In this video tutorial from CreativeCOW leader Alvaro Castaneda, well learn how to create particles in very simple ways in Maya. We also add collision objects gravity and render them in a liquid like mesh. Create particles and add collision objects in Maya.

In this clip, you'll learn how to utilize octrees to resolve certain detection problems when working in MS Visual C++. Whether you're new to Microsoft's popular general-purpose programming language and IDE or are a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free, official video tutorial. For more information, including detailed, step-by-step instructions, take a look. Use an octree to solve collision detection problems in Visual C++.
ATTENTION COLLISION REPAIR INDUSTRYHave you ever put your stud in your stud gun to repair a dent and the stud falls out before it reaches the panel? Sure it has, it has happened to all of us. However, the new Magna-Spot eliminates this problem with their exclusive (MPS), which secures the pins in the electrode. You can read the press release below to learn more of the benefits.ENTER AND WIN THE NEW MAGNA-SPOT STUD GUNDetails to this contest are going to be revealed in layers as follows:

Destroying crowds of little people has been a favorite passtime of dictators since time immemorial, but also a colossal waste of manpower. Now you can get some of the same thrill without all the needless death using 3D Studio MAX. This video will show you how to model, animate, and duplicate with particle flow a series of small robots. Then it will show you how to use a collision object (here a meteor) to destroy them all in fiery glory.

See how to take advantage of 3ds Max 2010's in-built tear modeling feature, which provides 3D artists to quickly cut a cloth as if due to a strong stretching force or a reaction to a hard collision with other rigid body meshes. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the application, you're sure to be well served by this video tutorial. For more information, take a look!

Check out this Softimage Xsi tutorial in the fluids simulator. This is a great video showing SPH in ICE off. You can quickly see how flexible this is. Changing collision geometry while the simulation is running and ICE and SPH just deals with it.

Not comfortable with your leather wallet? Even your canvas one feels a little too bourgeois? Well, grab that roll of duct tape, check out this video and learn how to make a duct tape mini-wallet, the bluest of blue collar bi-fold wallets. Be the envy of the local collision repair shop with this super cheap and easy bifold.

Cars make many people sleepy, and after a long day out many car passengers like to spend the ride home napping out. Not when you're driving they don't! This video will show you how to quickly and easily prank someone who has fallen asleep in your car by pretending to have a near-collision, while will give their groggy brains quite a scare.

Take a look at this instructional video and learn how to use the walk tool in Google SketchUp. The walk tool allows you to explore model from eye height. When you click and drag, you'll see a plus sign appear. YOu'll be able to move slowly or rapidly accordingly. This tutorial covers how to walk around your model, collision detection, and how to use modifier keys for more options.

This Gears of War lesson will be taking a simple mesh from Maya and exporting it into the Unreal engine and applying a collision mesh to it so that it will move when you shoot it.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

In some places, it's illegal to ride your bike at night without lights or reflectors, so if you plan on going for a joyride on your street bike, then you need to be prepared to share the road with vehicles and be seen. Appropriate gear and lighting are essential for safety when riding a bike at night.

Worried about your next drive in the rain? Do you feel you & your car are not prepared? Stay safe in a downpour with these tips to handle slippery, wet pavement and reduced visibility.

Although it's impossible (at least for now) to travel back in time to see the Big Bang, The New York Times has provided its readers the closest simulation of the experience via its latest augmented reality feature.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.

Keeping your home clean is an endless battle with time, motivation, and the easy availability of cleaning supplies. That's where the Hard Surface Floor Cleaning Robot Vacuum comes in. This magical device will save you time by automatically keeping your floors clean, never requires motivation, and doesn't require additional supplies beyond occasionally emptying the dust bin.

Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

If you're an Apple user and want an untethered virtual reality system, you're currently stuck with Google Cardboard, which doesn't hold a candle to the room scale VR provided by the HTC Vive (a headset not compatible with Macs, by the way). But spatial computing company Occipital just figured out how to use their Structure Core 3D Sensor to provide room scale VR to any smartphone headset—whether it's for an iPhone or Android.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Apple CEO Tim Cook's most recent tech prophecy is that "AR will change everything." And now, that includes Apple's own website.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.

Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide just that.

As augmented reality continues its collision course with mainstream adoption, the technology will now have a role in one of the most anticipated boxing matches of the year.

Those going on crazy off-road adventures, taking their inspiration from various SUV commercials, are likely to encounter many unexpected, all-terrain dangers.

Facebook had a pretty big week in terms of augmented reality, with much of its news coming from the Oculus 6 keynote presentation. But Mark Zuckerberg's social media company found other areas of impact outside of Oculus 6 as well.

The long, long, loooong wait finally ended this week for the augmented reality community as the Magic Leap One was finally released. The Florida-based company has loomed over the industry for years promising something big, and now the AR cat is finally out of the bag. Now we get to see if it will live up to expectations, but early reviews are a bit skeptical.

The Audi A8 may be short on the wow factor as the industry's first Level 3 car, but Audi has revealed some interesting details about one stand-out feature underneath the hood: the car's ability to self-pilot itself at stop signs and lights.

Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject for us at Next Reality is the recently released information about Magic Leap's upcoming Magic Leap One: Creator Edition.