Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

There are countless methods and cleaners aimed at eliminating stubborn stains from everything to clothing, carpet, and furniture. But completely removing every last trace of a stain doesn't require an arsenal of chemical cleaners and repeated cycles in the washing machine. Most stains can disappear in a matter of minutes with a dose of alcohol.

A quick and easy guide to setting up the mop feature on bObsweep Pethair or bObsweep Standard. When the mop pad is properly attached, Bob will simultaneously sweep, vacuum, and mop all reachable spaces.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

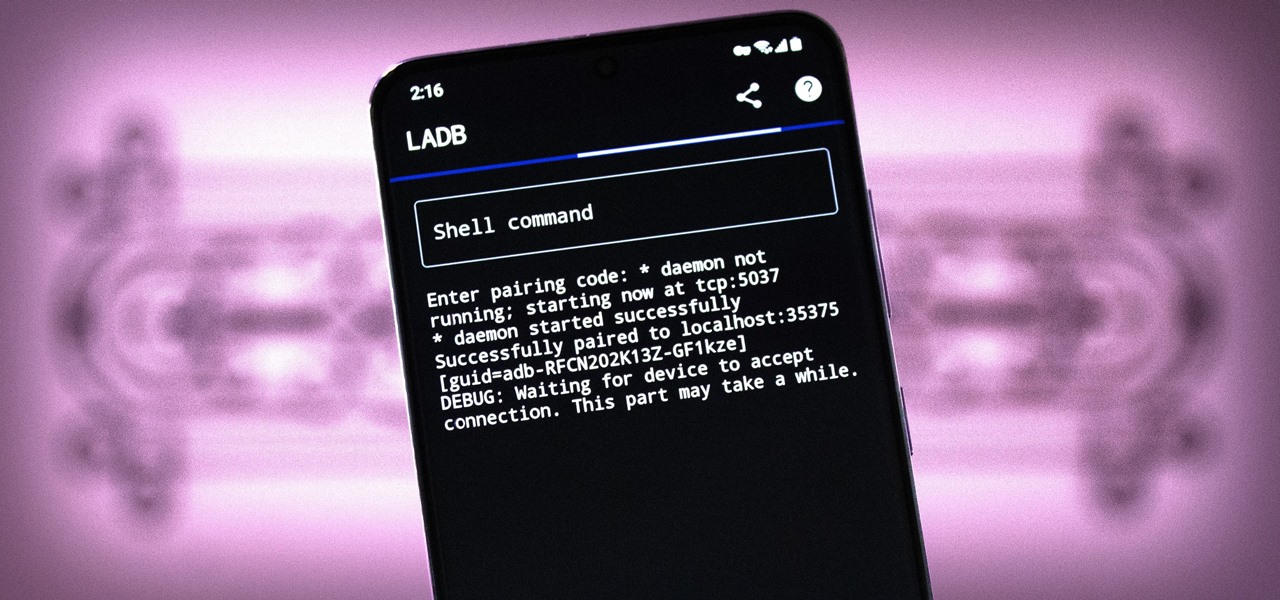
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

As unappealing as it sounds, transplants with fecal material from healthy donors help treat tough Clostridium difficile gastrointestinal infections. Researchers credit the treatment's success to its ability to restore a healthy bacterial balance to the bowels, and new research has shown that the transplanted bacteria doesn't just do its job and leave. The good fecal bacteria and its benefits can persist for years.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed on countless other TVs and set-top boxes.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.
Colonetix colon cleanser claim that it clean colon very easily and make colon healthy.know the facts and fiction about colonetix.

In this article, Conor J. Dillon notes a fascinating uptick in the use of the colon in the media. Everyone, from the New York Times to well, the entire Internet, seems to be using the colon a lot. I don't know that I ever noticed it, but now I'll be looking out for it everywhere. The colon does give you the sense that you're saying something important.

Taking good care of our colon should be one of our capital concerns. Do you know that like the air we breathe, the colon additionally becomes polluted with toxins? Toxin accretion will appear for as continued as you continuously eat. These toxins become the account of a abatement in activity and added problems like constipation, gas, bloating, etc. So now, imagine how acceptable activity could be after these toxins!

In this tutorial, we learn how to make a homemade honey facial mask. First, you will need to wash your face to make sure your skin is clean. Start off with 1/2 cup of honey, 1/2 cup glycerin, and 1 tablespoon pure soap. Mix this all together until everything is well combined. Last, add in your favorite essential oil to it, it doesn't matter what kind. Now you can grab your favorite sponge and dab a little bit of the mixture onto it. Spread it onto your face and then rinse with warm and cool w...

Make-up artist Claire De-Graft shows how to choose and apply foundation to dark skin. All you need is a large make-up brush, liquid foundation, facial wipe and cleanser, toner, and facial powder. Apply liquid foundation to dark skin tones.

Get the facial cleanser that you enjoy using. Keeping in mind not to strip the skin. Use a toner next, make sure your toner doesn't contain any alcohol. Put the toner on your face and neck using cotton balls. Next apply your favorite moistener and let it soak into your skin for fifteen minutes. You can also use vitamin E or almond oil. Take some freshly squeezed lemon juice and cotton balls and apply to the face and neck, focusing on the acne scars. If the lemon juice is to strong or if it st...

Kentucky Afield: Watch as Tim Farmer hosts the processing of venison, starting in the field and ending in the kitchen. Start with the deer down. Start with the tail and trim around the anus. You want to not break the colon nor the bladder for sanitary reasons. This is a long and delicate process of gutting a deer so that you may bring it easily back to the kitchen to make venison! Field dressing is an important hunting skill. Gut a deer, field dressing.

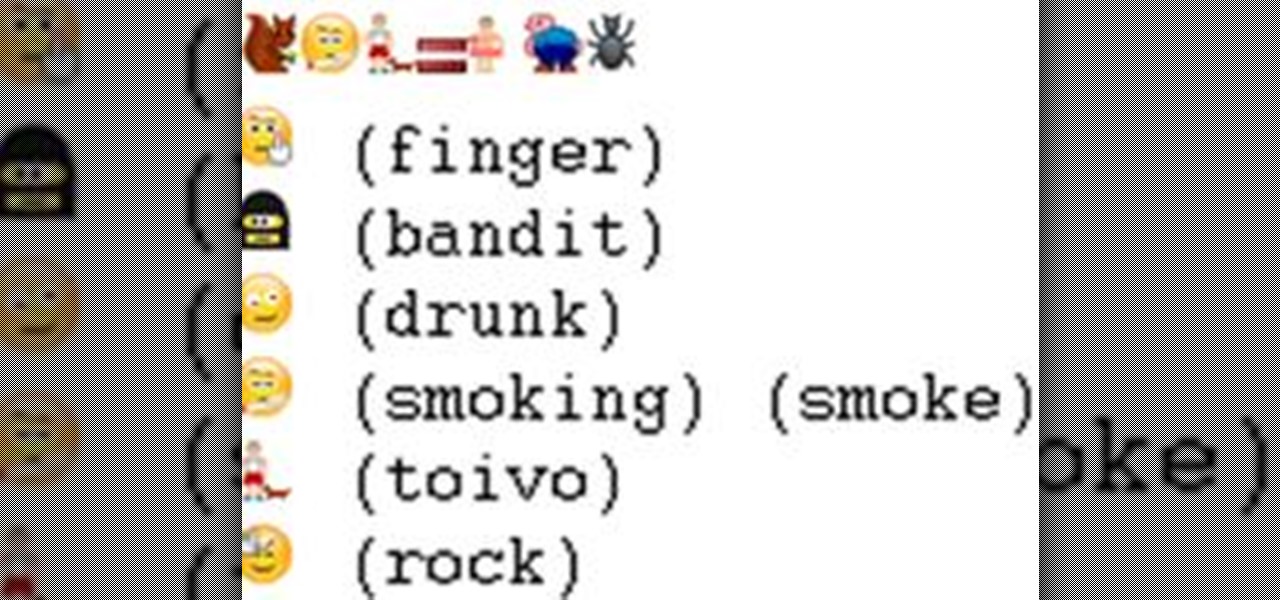
In this instruction, you will find out how to use the hidden Skype smileys and emoticons. You can not find this smileys in the standard Skype smiley menu. To use these smileys you need to memorize some words and put them in parentheses (). These words you can find in table below. There are 15 hidden Skype smileys. Also, there are a lot of flag emoticons, which you can get by typing flag, colon and international country code in parentheses, e.g. (flag:us) or (flag:uk). Here is the table of sec...

1) propose a skit where a 'volunteer' will fill himself with oil and brown dye, via an enema bottle and attempt to paint a canvas 5-10 feet away.

Through our friends at Azucar Surf we found this lovely surf house for sale. This house is for sale by owner Michael Lawson. This is what he has to say about it:

In a nutshell Bocas del Toro is an arcipelago on the Carribean coast of Panama. It's located about 20 mi south of the Costa Rican border and you can get there from both San Jose and Panama City. The main islands are Colon, Bastimentos, and Carenero, but there are over 100 islands you can explore by boat.

This video shows the steps taken before and during a barium enema or colon x-ray. The barium is used to insure a good view and accurate diagnosis. X-ray the colon.

LIFE magazine has posted a gallery of bizarrely wonderful old school scientific models. Don't miss the giant fetus or massive colon (double ew). Behold, science education before computers ruled our world.

If you suffer from pimples try to watch this video and put into practice what it suggests so as to get rid of pimples. If you have a problem with pimples it is suggested that you consult a doctor for appropriate treatment. However to get rid of a pimple overnight you can try this method: 1. Start by washing your face with lukewarm water and apply a cleanser that is ideal for oily skin. 2. Afterwards apply some toothpaste in the area where there is the pimple. 3. Leave it there for about 10 to...

Hello Java-ers, In the previous two tutorials, we learned about installing the JDK, Installing/CreatingAProject in Eclipse IDE, and data types in Java.

A colonoscopic examination involves gently inserting a fiber optic colonoscope into your rectum and large intestine to view your lower gastrointestinal tract. This video shows a polyp being removed from the wall of the colon. Do a colonoscopy.

Declare war on zits and blemishes! In this video, we show you how to battle the blemish war with tips for preventing, treating and concealing pimples. Cleansing is the key to prevention and concealer is king when it comes to covering up the zits that do pop up. Example Products:

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.

Want a face lift? Scared to go under the knife? Then, your solution is dimethylaminoethanol. Um... what is dimethylaminoethanol?