We all know that color coding is important because it helps us to quickly organize things based on visual cues. As students in high school, we used differently colored page tabs to denote different subject matters, and some of us color code file cabinets for easier and faster access. The same principle goes for this tutorial, which teaches you how to color code a knitting loom.
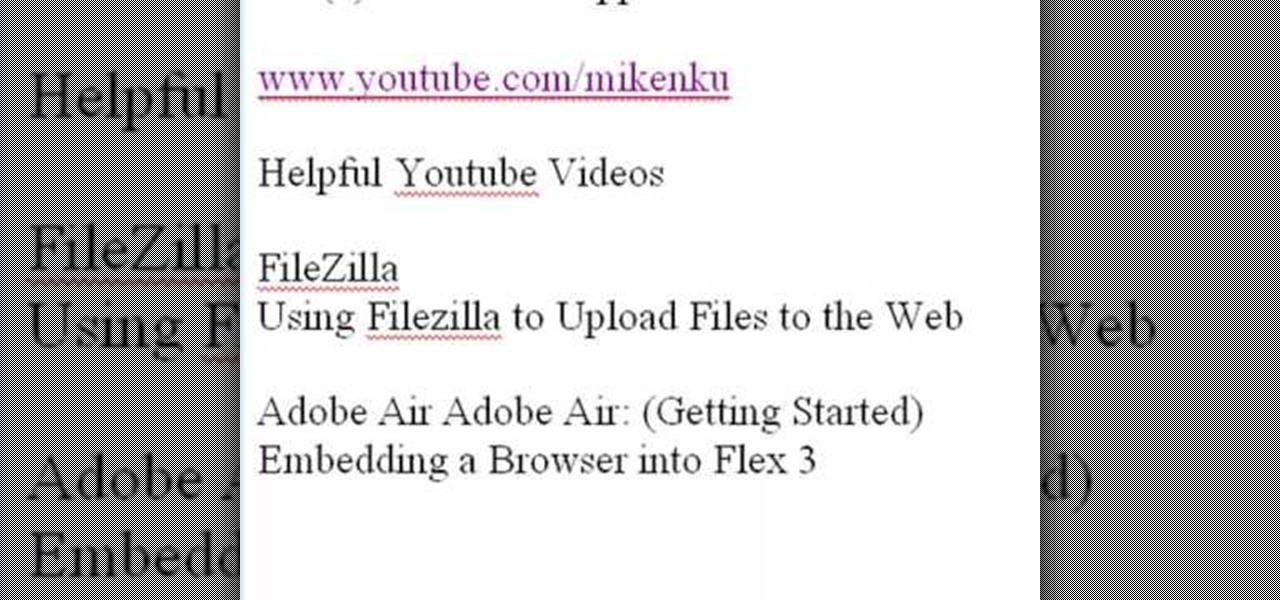
This tutorial series shows you how to put up an Adobe Air Flex 3 Encryption System. One of the weak points of Adobe AIR and Flex is there is no encryption system built in, making your data and applications vulnerable. But that's ok, because this tutorial will show you how to remedy the problem by adding an AES encryption system.

This video describes Resistor Color Codes and how to read them. It relates Resistor Color Codes to scientific numbers and engineering notation.

In this tutorial, we learn how to organize your closet by establishing a wardrobe system. If you have tops that you wear during the day, put these on a different colored hanger than your nighttime tops. Color code these in your closet and then hang up your nighttime tops with a light wood or your choice hanger. If you have other random tops, you can hang them according to how you would wear them the most. Dresses can be hung on another color hanger and then pants can be worn on another color ...
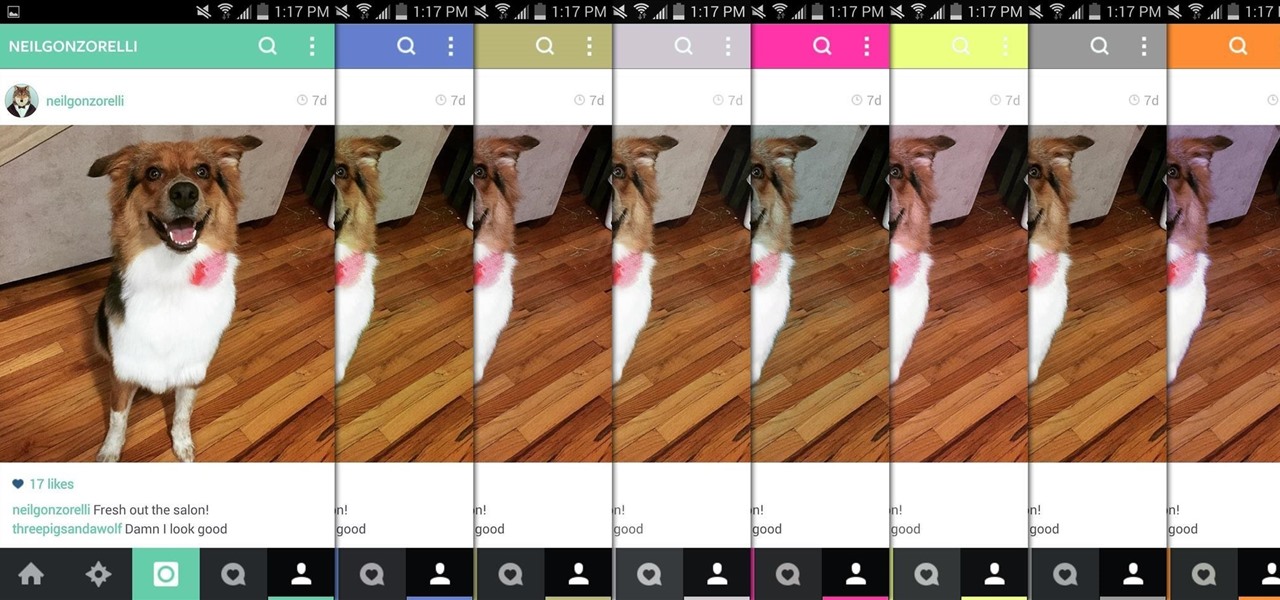
There aren't many complaints I can think of when it comes to the Instagram interface, and finding one would just be nitpicking. But like with most things in life, if given the opportunity, why not take advantage? "When in Rome," as they say.

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

Imagine that every time you print a document, it automatically includes a secret code that could be used to identify the printer -- and, potentially, the person who used it. Sounds like something from a spy movie, right?

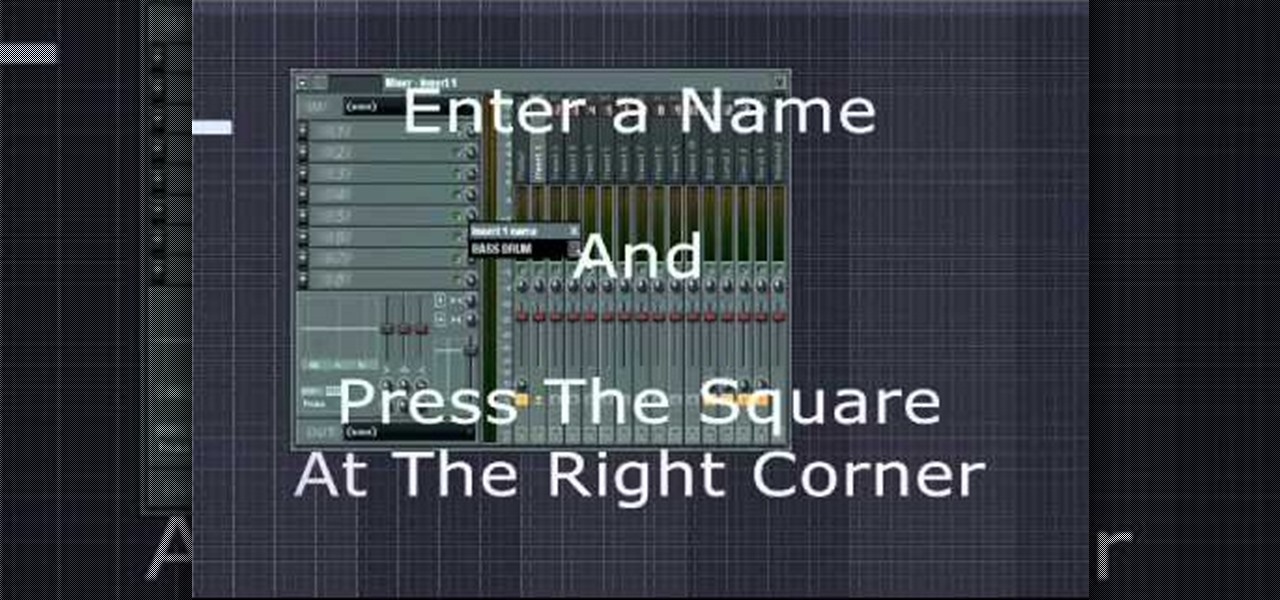
Keep your tracks organized by color coding the mixer channels when using FL studio. You'll have a much easier time making beats in FL studio with color coded mixer channels. You've got the tools, make sure you know how to use them properly.

Managing your busy schedule just got easier in Entourage 2008 for Mac. Using the powerful Entourage Calendar feature lets you organize your time wisely. The Microsoft Office for Mac team shows you just how to organize your schedule with the calendar in this how-to video.

The Buchla Electric Music Box is a system developed for people who are looking to control a lot of aspects of their sound at the same time. The color-coded connections make it easy for users to distinguish what is controlling different elements. The system is already set up for use with computers and lets you control the voltage of all musical parameters. You can configure it to have a variety of applications. This video will show you to patch a Buchla 200.

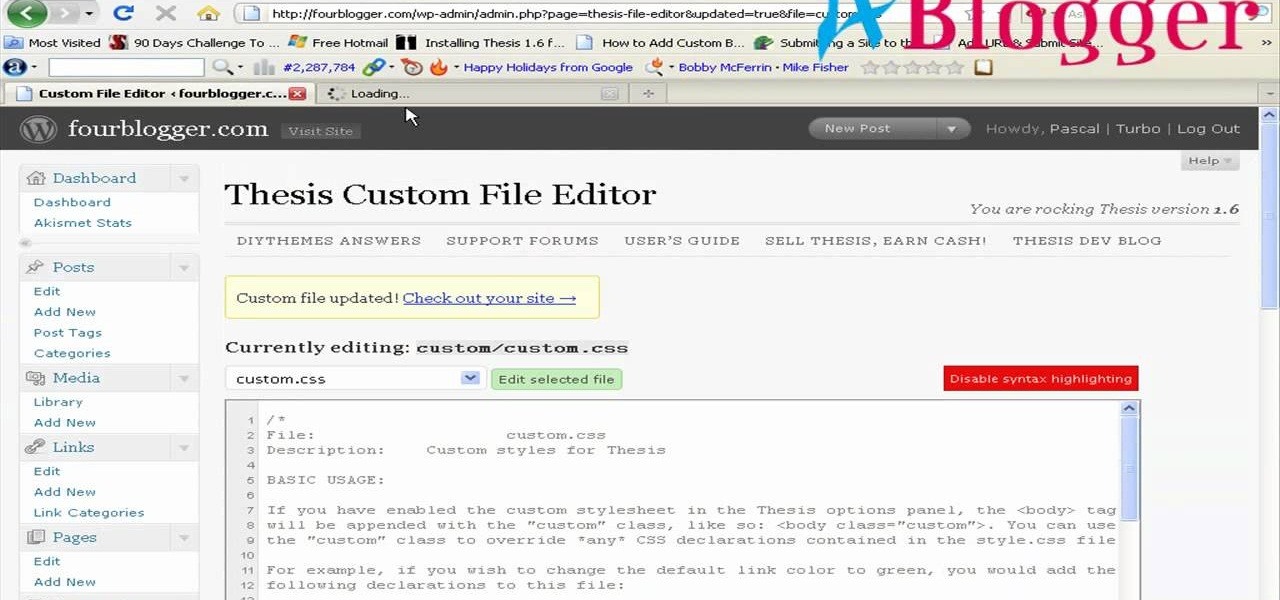
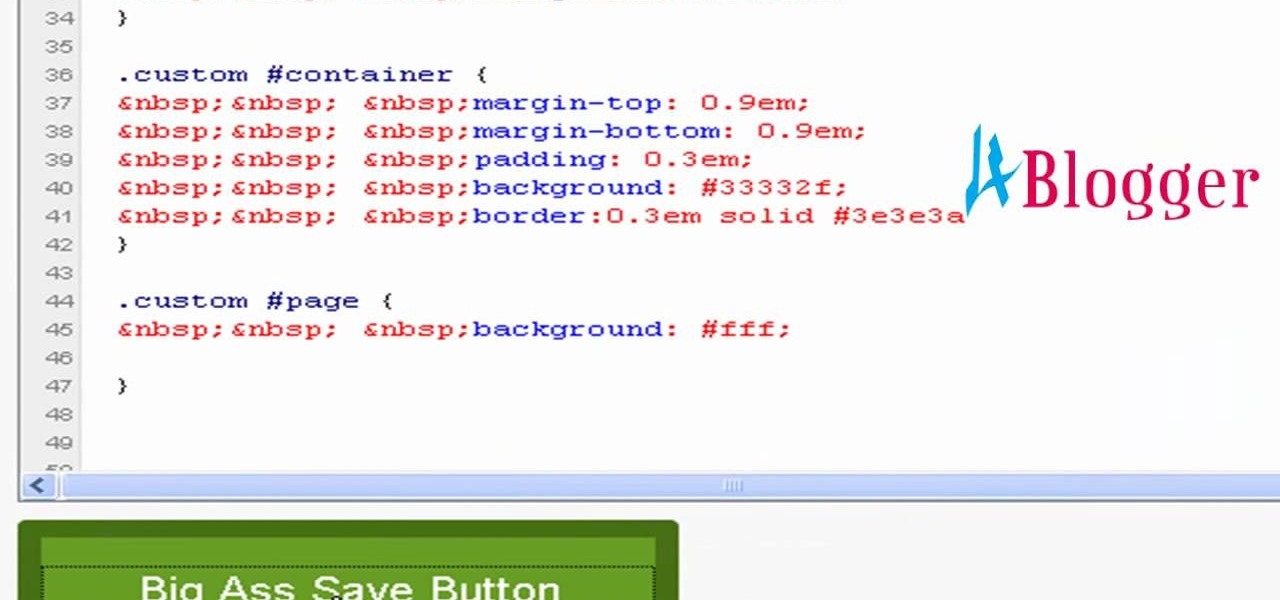
First you need to go to your site and click any post you want and see the simple heading and now you want to change the background. To do this, first you need to go to your word press admin and then click custom file editor in thesis options it will open your code window and here you will have to paste the code which is showing in the video. you will have to paste it in custom.css. After pasting the code you have to click the green save button.

You can change thesis theme background color and size in Wordpress blog to do this first you need to go to your word press admin. And then you have to click custom file editor. There you will see the "Thesis custom file editor". Now you have to select custom.css in edit selected file menu. Now you will see there a code box. Here you will have to past the background changing code. The code is showing in the video you can type it and then copy and paste it in the place of the code box which is ...

Keeping secrets out of the wrong hands warrants desperate measures—or maybe just sensical. If you have a secret, the best way to protect it is with a code—and the best way to transfer that secret message is via an electronic telegraph system. This video will show you how to make your own homemade electronic telegraph machine, so that you can send those encrypted Morse code messages to your friends without fear of prosecution.

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

To program your DirecTV remote for your XBox you will need to find your programming codes. Press menu on your remote and scroll down to parental fav's and setups, then system setup, select remote control, and program remote. You can use either AV1 or AV2 both should work. Then you will choose DVD, and then select the brand for your 360 and your program codes will come up. Put your TV in AVI mode and press your menu and select button at the same time. The lights at the top of the remote should...

This video will show you a few techniques for removing stuck pixels from an LCD screen. This is not a guaranteed fix. Please only use these as a last resort, as some of them can cause more damage to the LCD. Only attempt these if you are experienced and know what you are doing.

Add a chat program to your website and allow the logged in users to talk to each other! You can write this program using Adobe Flash CS3, PHP and MySQL. This tutorial shows you how to write your own Flash chat program incorporating all three systems.

This Dreamweaver CS4 tutorial takes you on a step by step process for installing an automated comment box system for your website. The system is a great way for communicating and interacting with your website users. It has a great feature that automatically sends you an email everytime someone comments in your website. Also it will allow you to post a reply by email.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

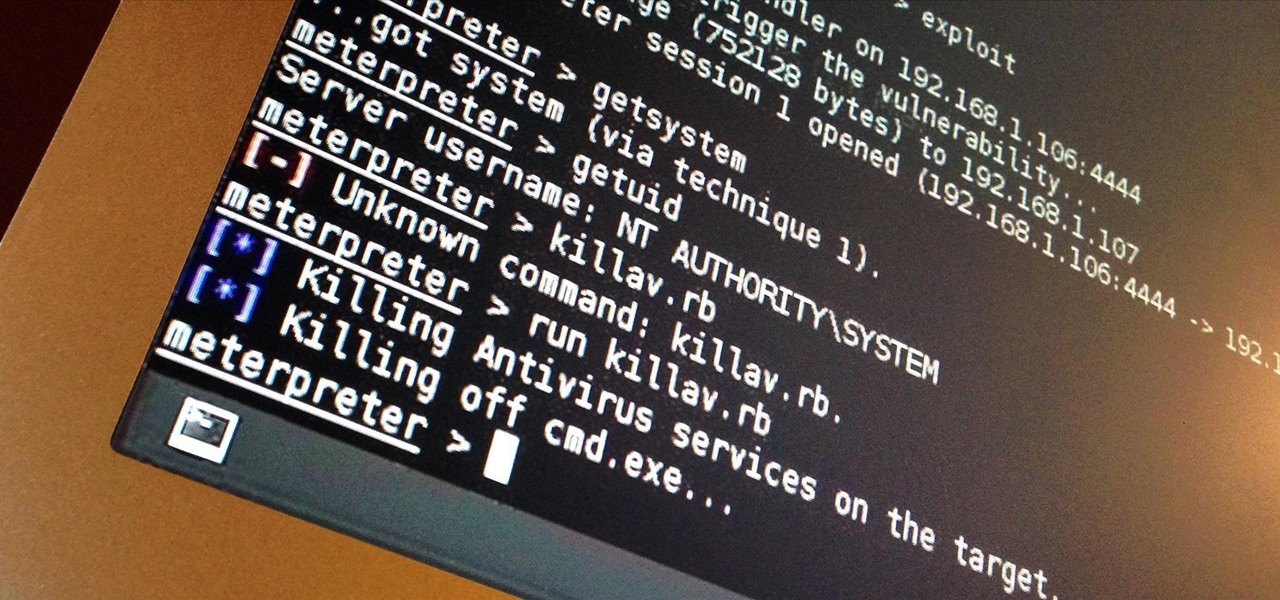
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

The bread at your local supermarket will most likely always be fresh, but how do you know which loaf is the freshest out of the bunch? You can squeeze and inspect them like an annoying TSA agent, but there's actually a much simpler way to do it.

No downloads or extra programs needed! This video is pure cheat codes, all for playing on Poptropica! You can do fun things like change your skin color, change your hair color and even get the elusive pumpkin hat to wear!

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

With the Android 4.4 KitKat update slated for release sometime in October (according to Nestle), I'm sure you're excited to get your hands on and test out all of the new features of Google's latest mobile operating system.

System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

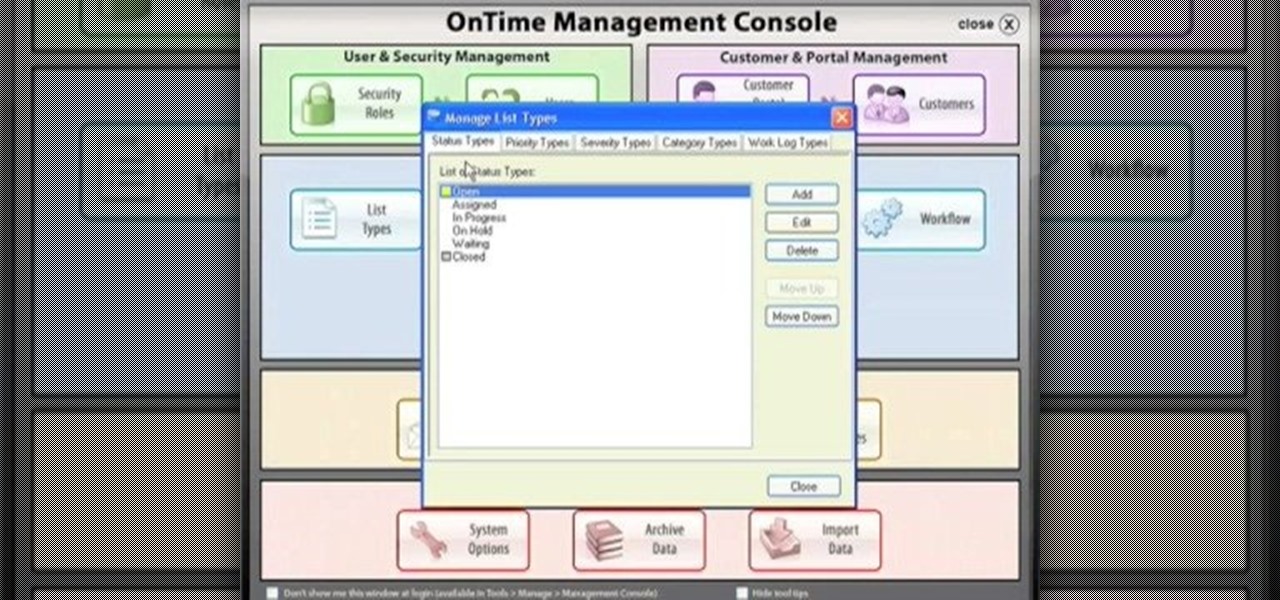
One great feature of OnTime 8.1 is the ability to add color schemes to the main grids of OnTime Windows and OnTime Web. This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers how to activate this functionality to allow color changes for items based on their Priority, Status, Severity, and Workflow.

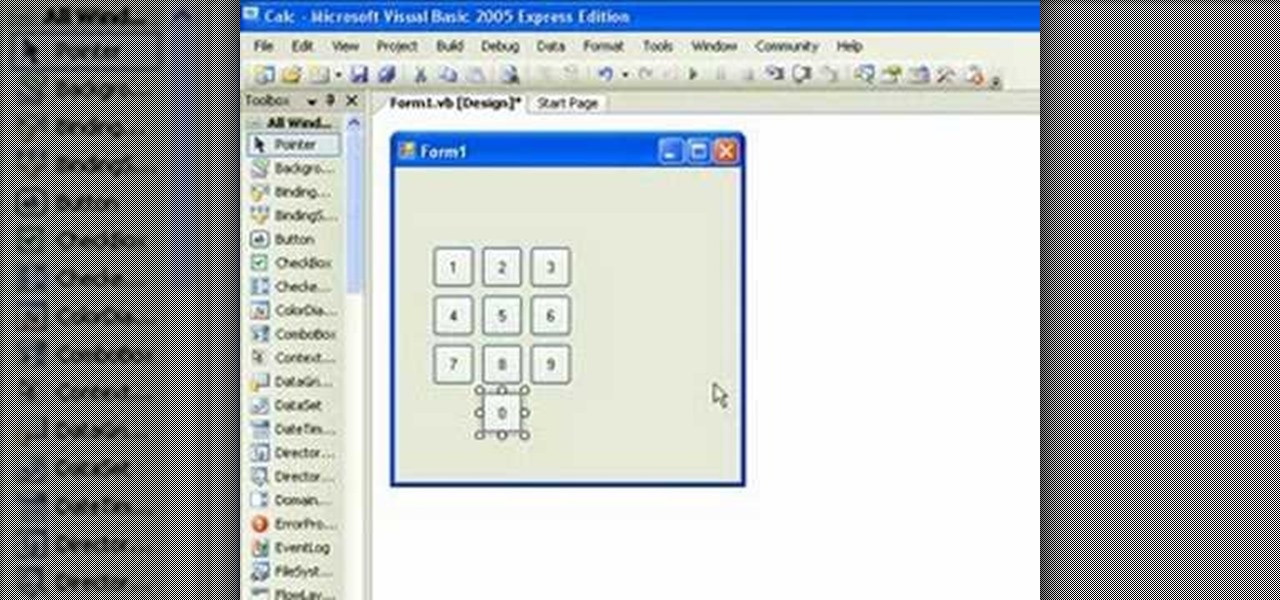
If you're new to the Visual Basic IDE, looking to brush up on your VB programming skills, or simply have a burning desire to code a simple calculator, this three-part video lesson is for you.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Most of us have family who live far away in different states or even different countries. While we'd love to have all our family with us on Christmas, it's much more likely that we'll be giving them a call on Christmas and mailing them some gifts.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Are you bored with the limited color options available for your pets by default in the Facebook game Wild Ones? Brighten your life by hacking! This two-part video will teach you how to hack Wild Ones using Cheat Engine to change the main and detail color of your pets to any color that you can find the HTML color code for.

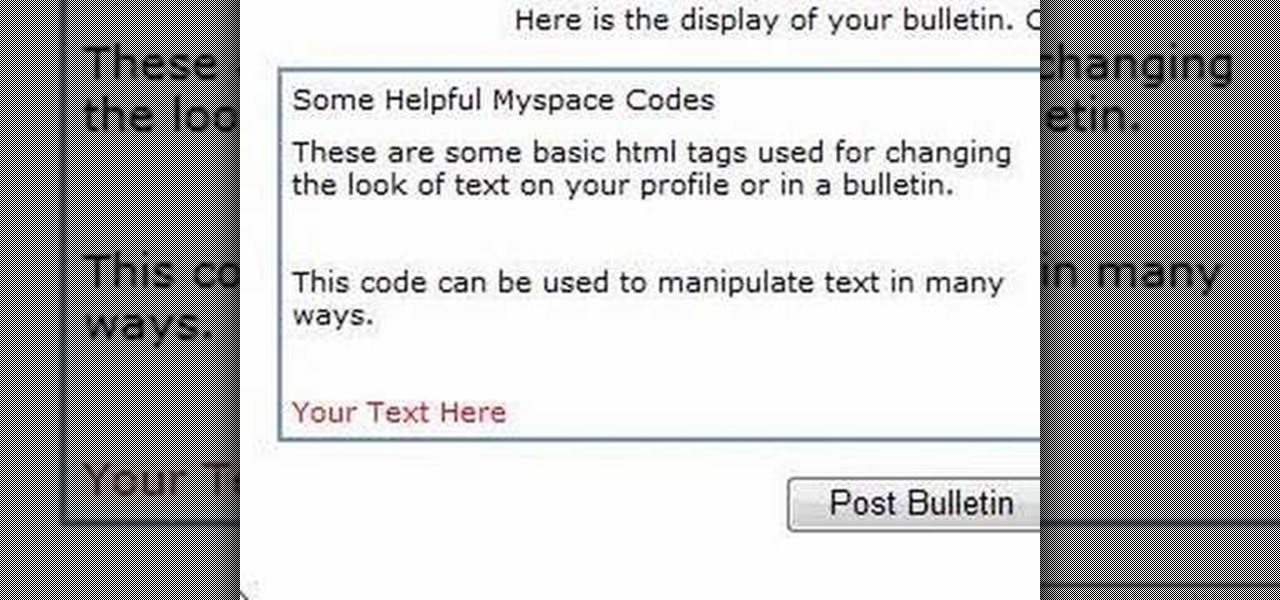
In this Computers & Programming video tutorial you will learn how to alter text on MySpace using HTML codes. Here are a few basic html codes used to change the look of text on your profile or in a bulletin. <b> for starting bold text and </b> for ending bold text. <i> this text will be italicized</i>. For underlining text use the code <u> </u>. <b><i><u> This text will be bold, italicized and underlined </b></i></u>. To change color of your text to ‘red’ use the code <font color=”red”> </font...

C++ is one the most powerful and fundamental languages commonly used to computer programming. If you've ever wanted to get started using, then please watch this video series. It's 29 parts will teach you everything you need to know about coding in this magnificent language, allowing you to create your own fairly full-featured computer programs. Honestly, if you have any questions about C++ at all, or want to learn it and don't think that you can because you've tried programming before and fai...

If you just purchased an Android enable mobile device with Bluetooth, then one of the main objectives you'll have on your to-do list is to set it up in your vehicle for hands-free dialing and phone calls. Activating Bluetooth inside your car is easy, and all you need to remember is a little number called zero. Actually, you need to remember it 4 times — Best Buy has answers. The Best Buy Mobile team explains how simple it is to activate Bluetooth settings on an Android cell phone.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

In this tutorial, we learn how to make your own board game for 99 cents. First, trace out a name onto the board spelling out each letter. After this, break the letters down into different spaces, and color code them for different moves on the board. Write down the key for the colors underneath the name so you know what the colors mean. After this, draw the name onto a piece of paper, measuring out everything so all the spaces are the same size. Then, color in the spots on the board. Next, use...