You may have seen a "check engine" sign on your car's dashboard when driving your vehicle. Maybe "service engine soon," or just "check". What does this mean if the alarm won't turn off, or comes on when you're driving? Find out in this automotive video tutorial how to read those trouble codes on your automobile.
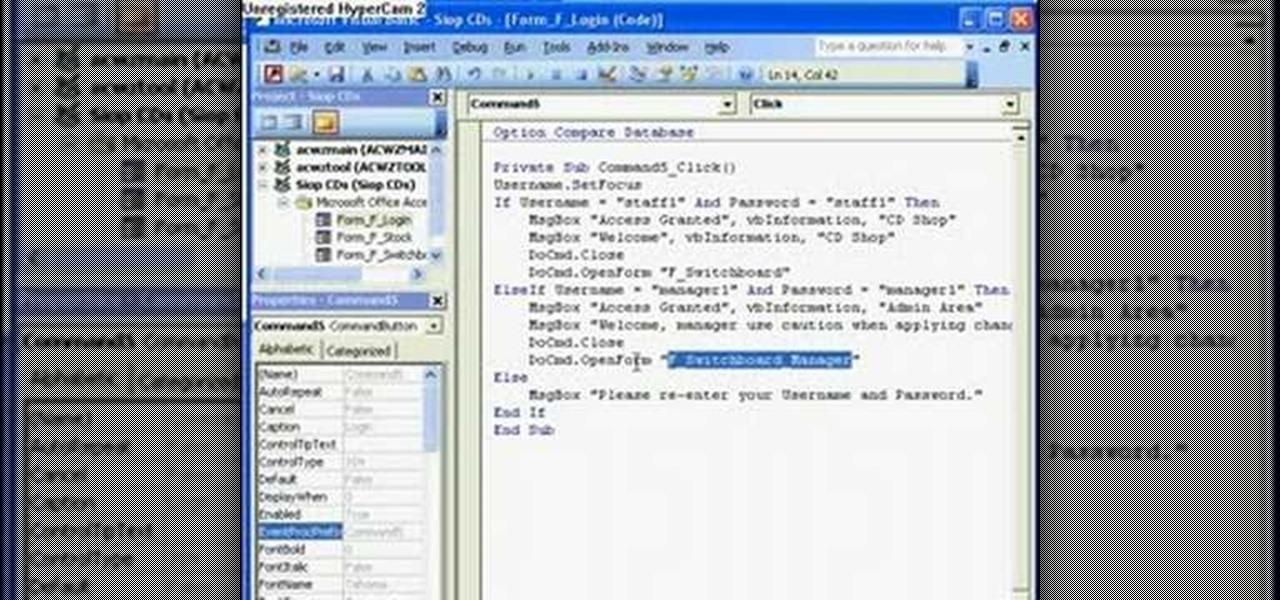
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a multi-user login form to password protect different areas of your database.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.
Change object colors via ActionScript in Flash 8

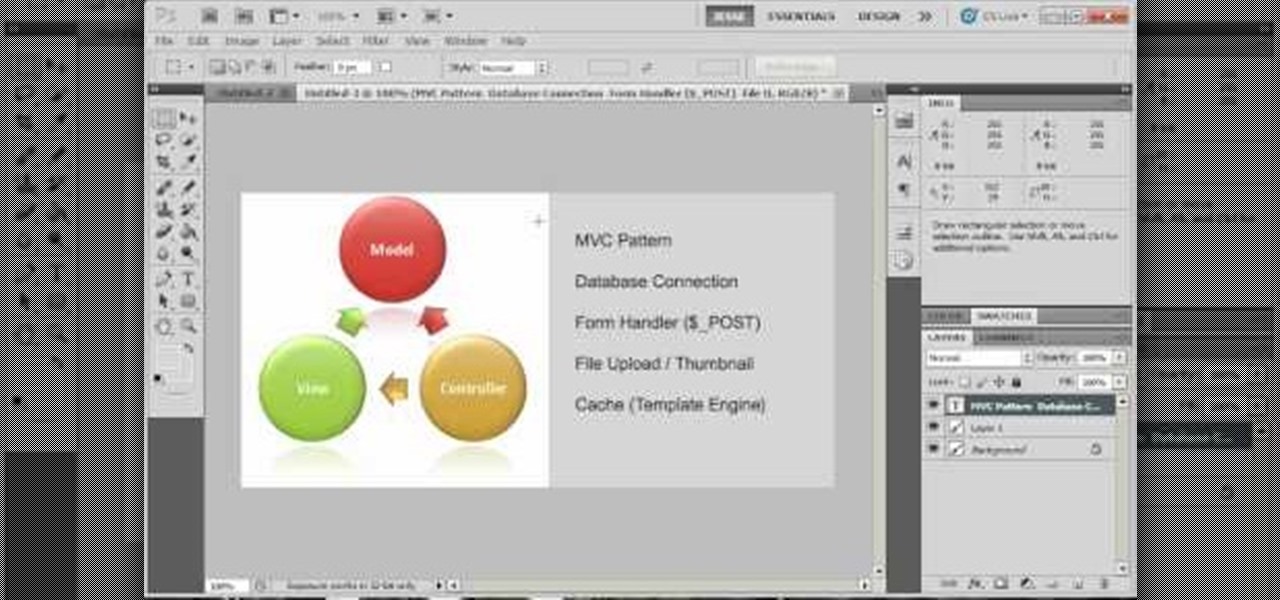
In this video tutorial, JREAMdesign looks at the task of choosing a PHP framework and a CMS. He helps simplify the act of choosing between the major framework contenders (Zend Framework, Symfony, Yii, Code Igniter, CakePHP) and content management systems (Drupal, WordPress, Joomla, Wolf CMS, Mod X) by summarizing what normally is expected from these systems and some of their typical features.

In this clip, you'll learn how to code a simple user authentication system with PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

In this video, we learn how to mix automotive or car paint. To begin, you want to look at your car information to find out what kind and color of paint they used on it originally. Once you have this information, you can take it to an automotive shop and they can do a code search for what to mix together to get this specific color. You may have more than one option on how to make the color, depending on what it is and what year your car is. Next, you can have the paint made and tested to see i...

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

You can drag and drop an email onto your Calendar icon in Microsoft Outlook, which then immediately gives you the option of setting up a new calendar entry. You can even color code your various events for easy reference later!

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

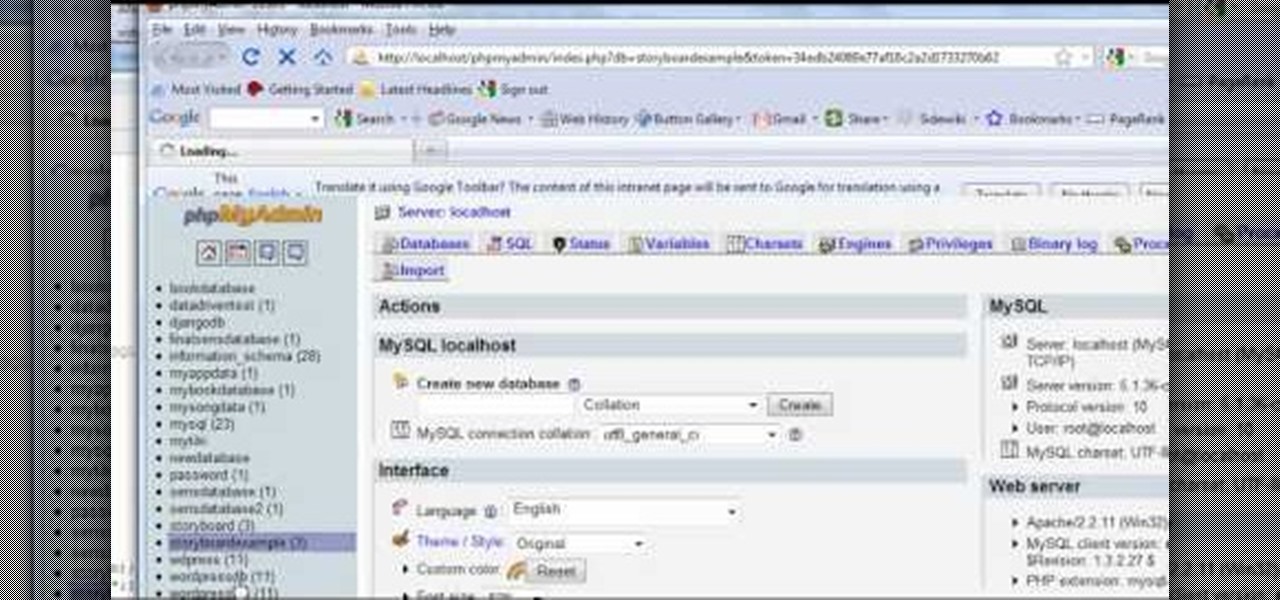
Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

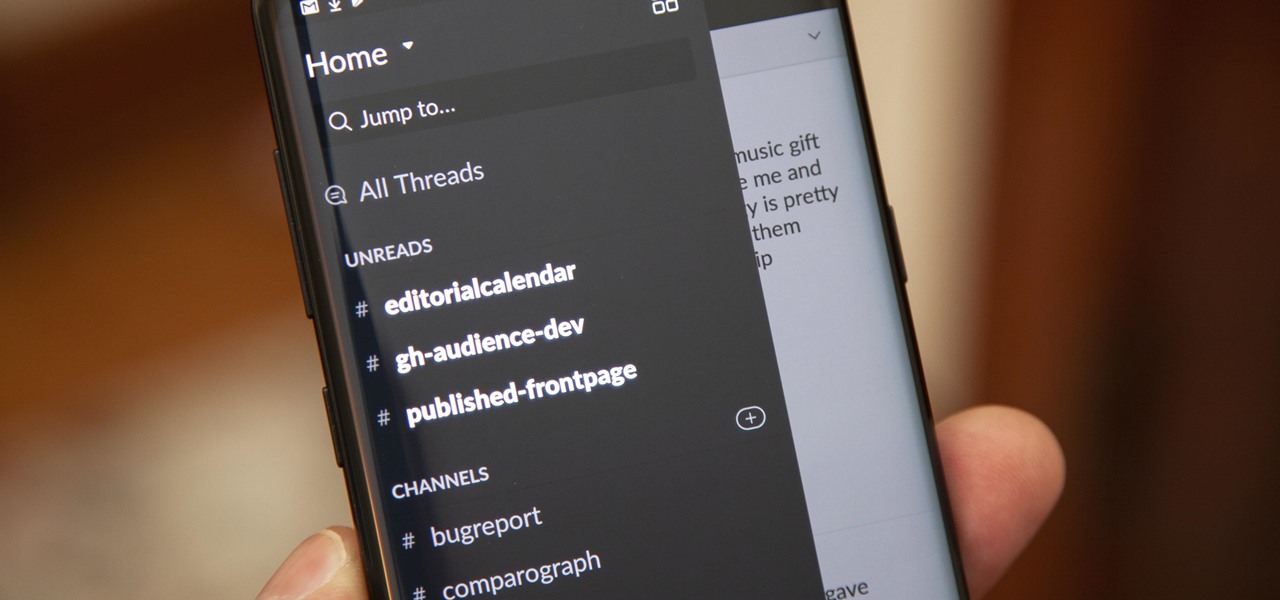
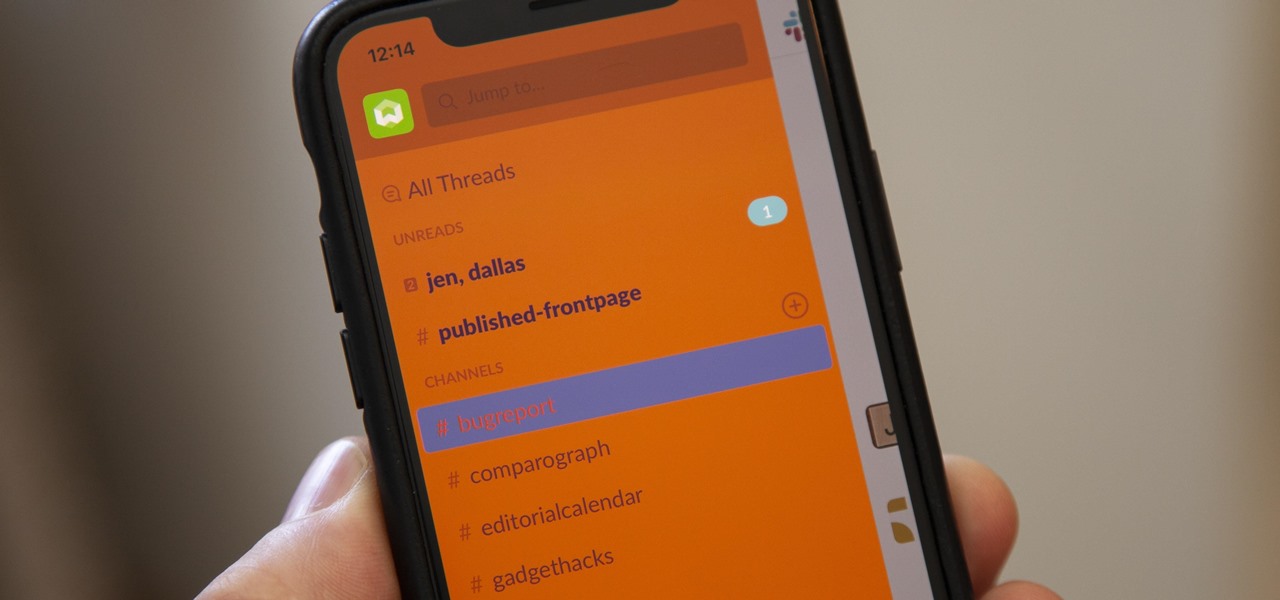
Slack recently released a dark mode for its Android and iOS apps, and for the most part, it works great. Super dark gray backgrounds and light gray fonts, which is much easier on the eyes than blinding white backgrounds and black text. But there's one thing that is not affected by the new night mode setting — your sidebar.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

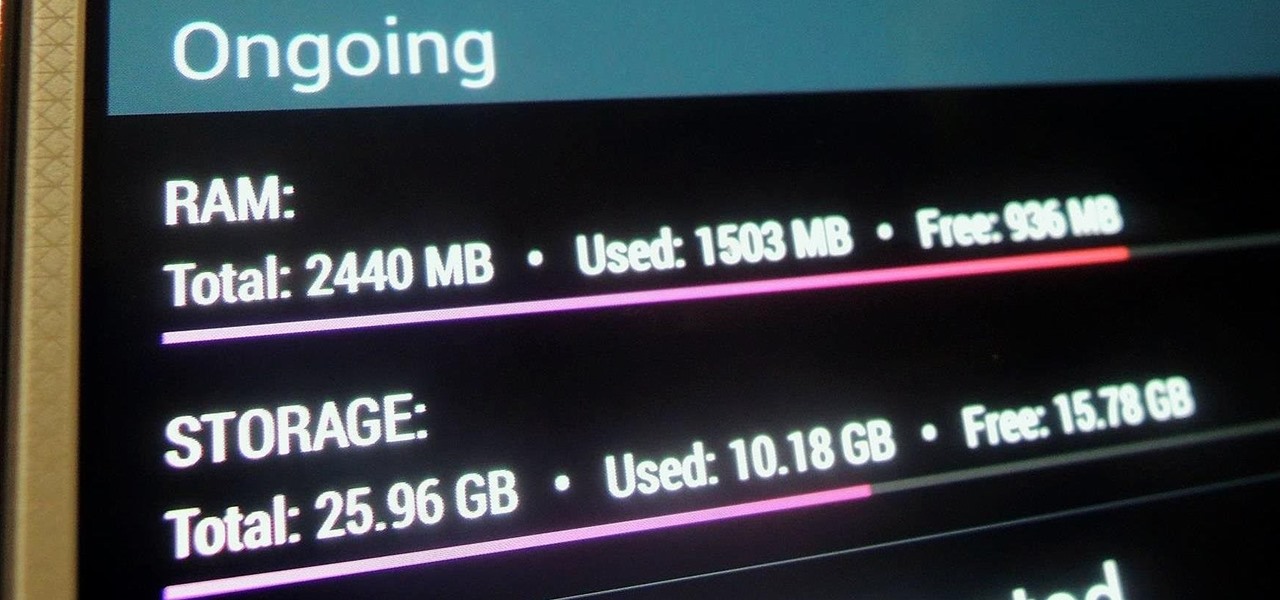
Modern smartphones can easily handle anything you throw at them, but it's always good to keep a tight grasp of what your phone is actually doing and how well it's doing it. System information can be viewed by looking through your Application Manager, but this process makes it difficult to keep an eye on usage in real time.

We all know about partying like it's 1999, but what about gaming like it's 1999? The folks over at Irrational Games, the studio behind the new BioShock: Infinite, which was just released today, decided to go a little retro and include a hidden game mode for the most hardcore gamers. By default, the game starts out with the normal Easy, Medium, and Hard difficulties, with "1999 Mode" made available only after you beat the game. But if you enter in one these secret Konami codes provided below, ...

Both the Gears of War 3 Limited and Epic Editions contain a DLC code that allows you to unlock and play the Adam Phoenix character. The code is a little hidden, and unlike most DLC codes, isn't printed on the back of the manual. This guide from IGN will show you where to find the Adam Phoenix DLC code.

After running a diagnostics test on a 2002 Jeep Liberty, if you get the code P0442, that means you have an Evaporative Emission Control System (EVAP) leak detected, which is just a small leak, but a leak nonetheless. This video will show you how to smoke test the EVAP leak to find the problem spot inside the vehicle.

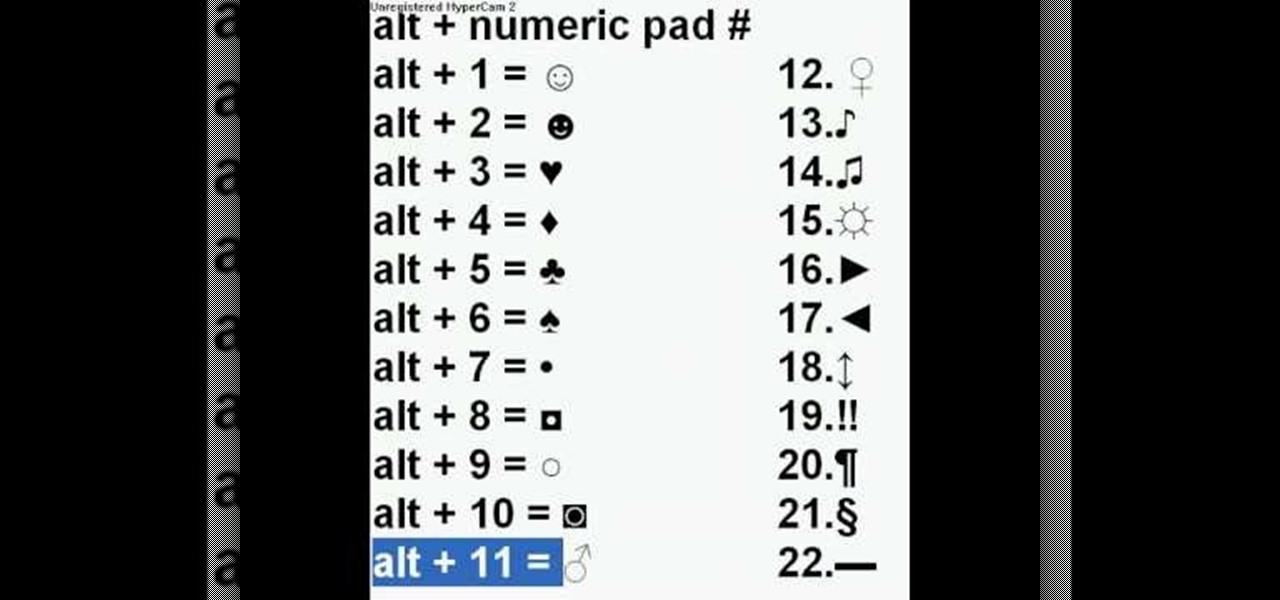
It is possible to add a little extra personality and ting to your facebook, myspace, or most any messaging system online by adding characters such as hearts, smiley faces and many more. With this video you will see the simple alt codes you can use to personalize your messages by pressing alt + a number.

If you're a Visual [blank] programmer heretofore intimidated by the thought of programming for the Linux operating system, take heart: this video tutorial will teach you how to visually code GUI applications with Ruby and Glade.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

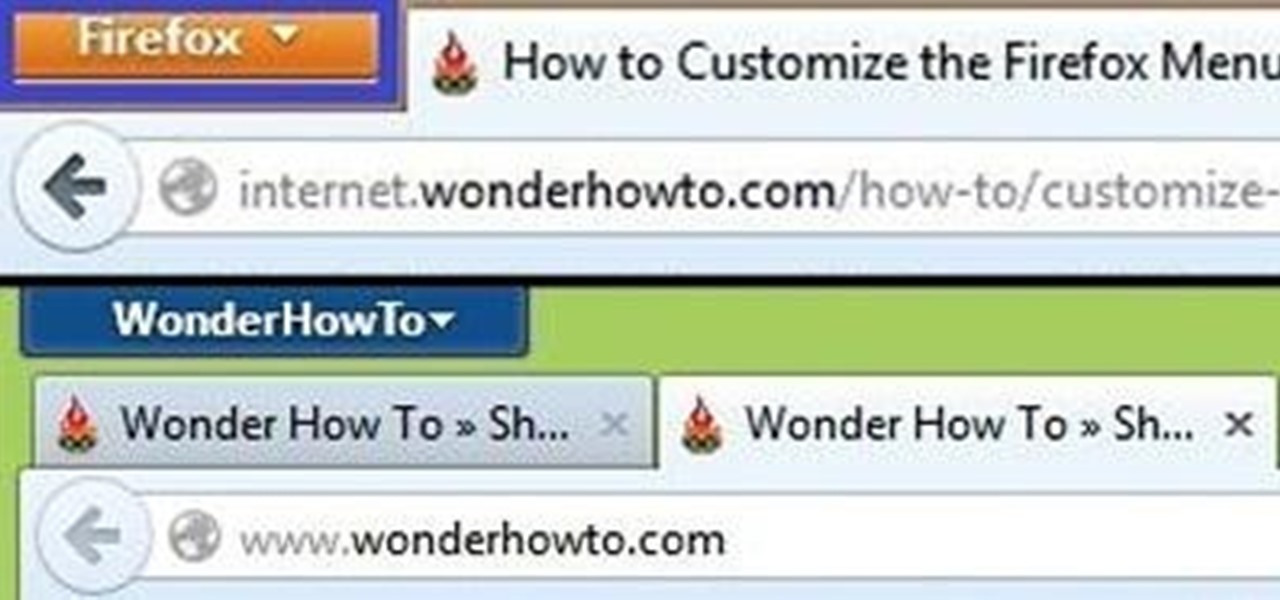
Browser customization is one of Firefox's best attributes. You can personalize your Firefox with extensions, add-ons, themes, and so on. And if all of that still doesn't cut it, you can even customize the Firefox Menu button to say whatever you want. To start off, you'll need to download a user file editor called ChromEdit Plus. Click Add to Firefox, then hit Allow when prompted and wait for it to install. You will need to restart Firefox afterwards.

This video crocheting tutorial shows how to crochet the basic Tunisian stitch, and how to use it to perform a color change. Crochet Andy's directions are especially easy to follow thanks to color-coded yarn. Learn how to crochet the basic Tunisian stitch by watching this instructional video.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

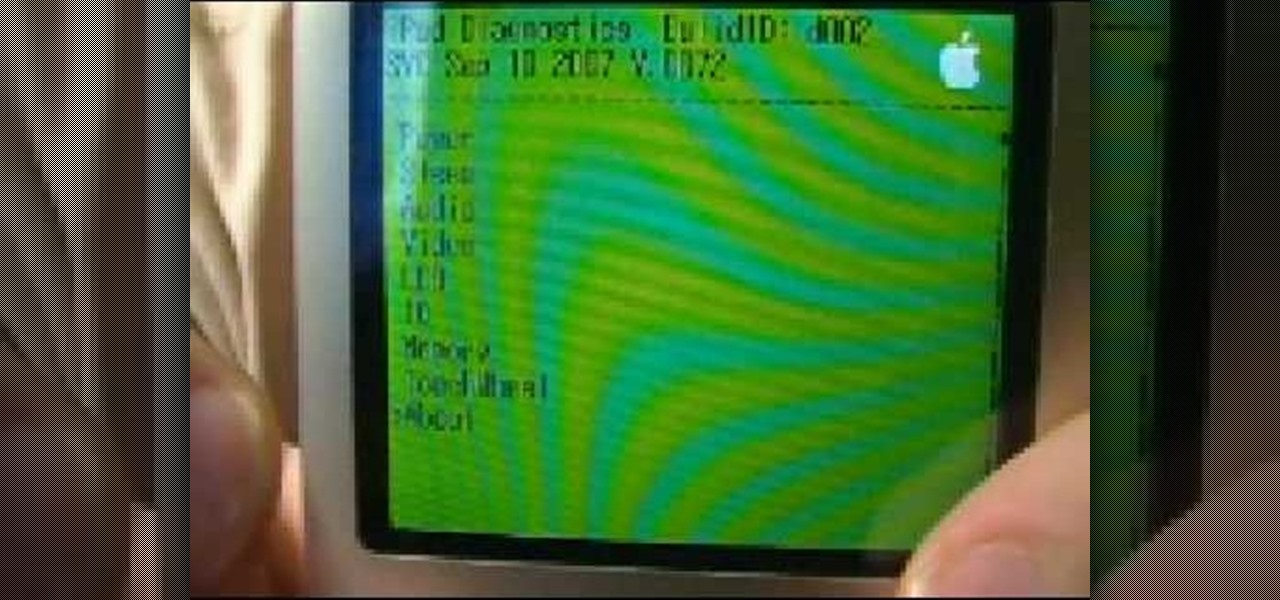
In this clip, learn how to access the cool menu screens on your iPod that you never knew existed. This video will walk you through how to get to your 3rd generation iPod's cool colored LCD screen database. This hack is easy, doesn't require codes or tools and won't harm your device, so give it a try!

In this flash tutorial the instructor shows how to create a custom cursor. This is created using shapes and simple Action Scripts. First open the flash tool and create a simple shape. Then convert the shape in to a movie clip and add simple animation to it where it switches colors. Now create a new layer and add Action Script code as shown in the video. This Action Script code is a command to make the shape follow the cursor. Now the shape follows the cursor as the cursor moves and appears as...

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

For some reason, the Slack app on Android and iOS is a little less customizable than Slack on other platforms, so you can't adjust the sidebar theme to different colors directly inside the app. But that doesn't mean you can't customize the look of your mobile app at all. It's just a little less convenient.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.