The personal computer is a strange and powerful entity, capable of bringing great joy. Just as often, you probably want to chuck the damn thing at the wall because it doesn't work right. If you want to pull a prank on a friend that will really upset them, messing with their computer is one of the best ways to do it. This hilarious video will show you how to do three great PC pranks quickly and easily, including changing the contrast on the monitor and pretending to edit websites using Javascr...
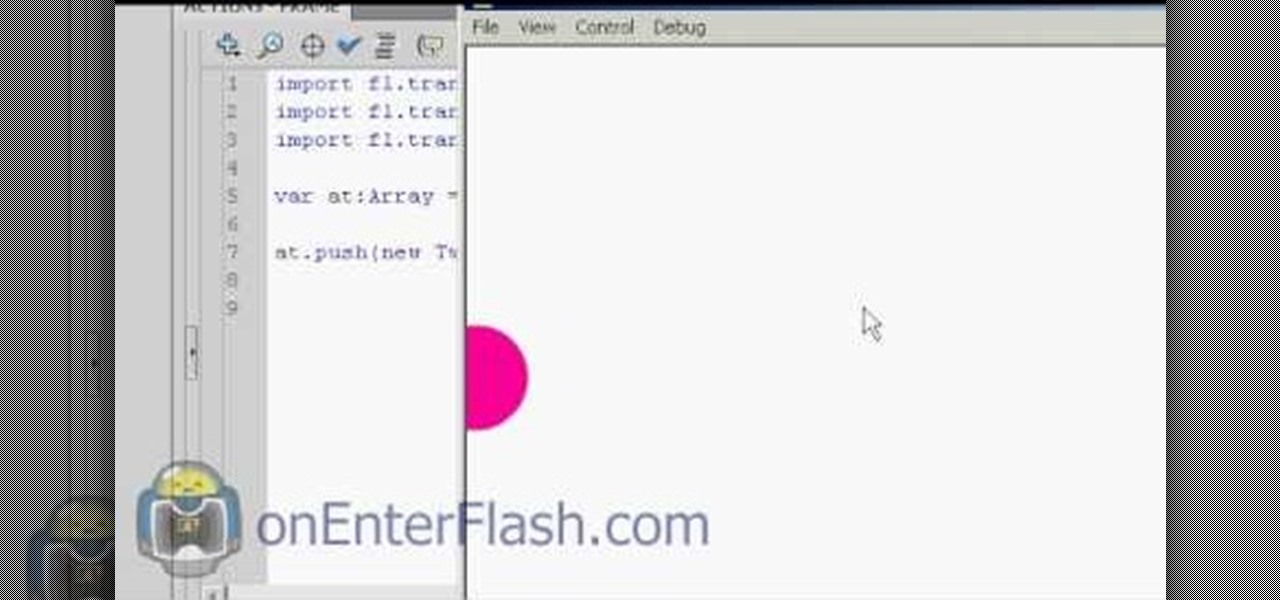
Most of you viewers out there who are familiar with Flash, After Effects, or other creative software know what a tween is. But can you write the code for them? This video will teach you how to code different classes of tweens using Actionscript 3 in Flash CS4.
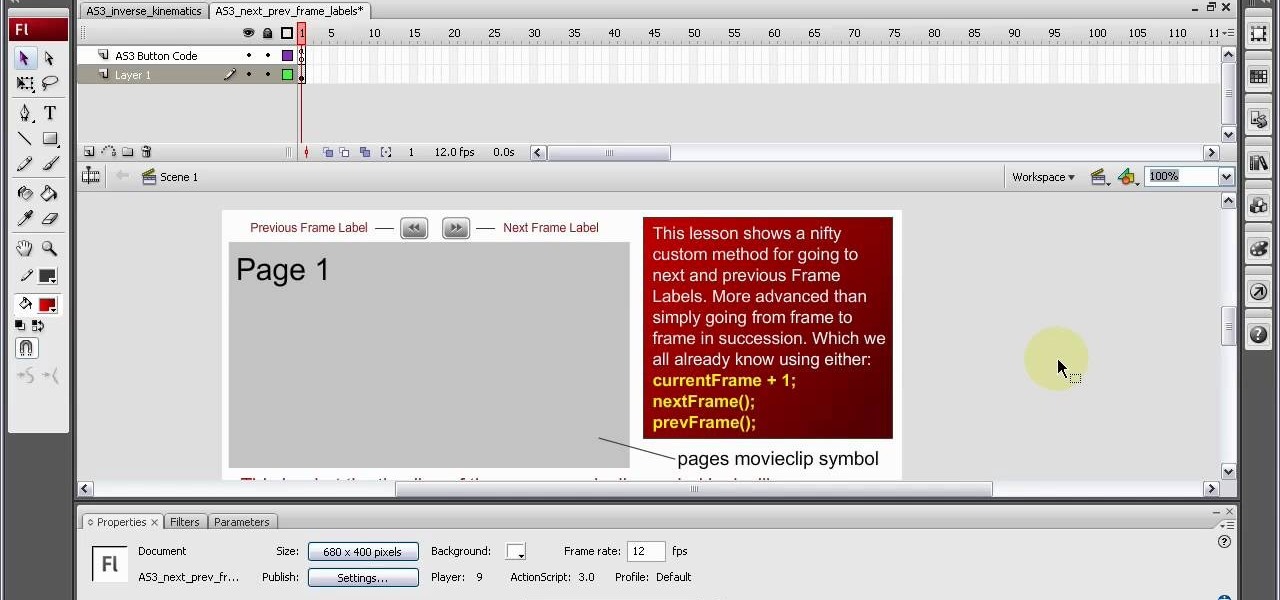
Frame labels are titles associated with certain segments of content (such as playing a tutorial in sequence and assigning each clip a separate frame label). This tutorial shows you how to set up a custom navigation system for your frame labels, so users can switch back and forth between segments.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

Looking to up the ante in the home secuirty department? If you are concerned about the safety of your family and home, consider purchasing a burglar alarm system by following these helpful tips.

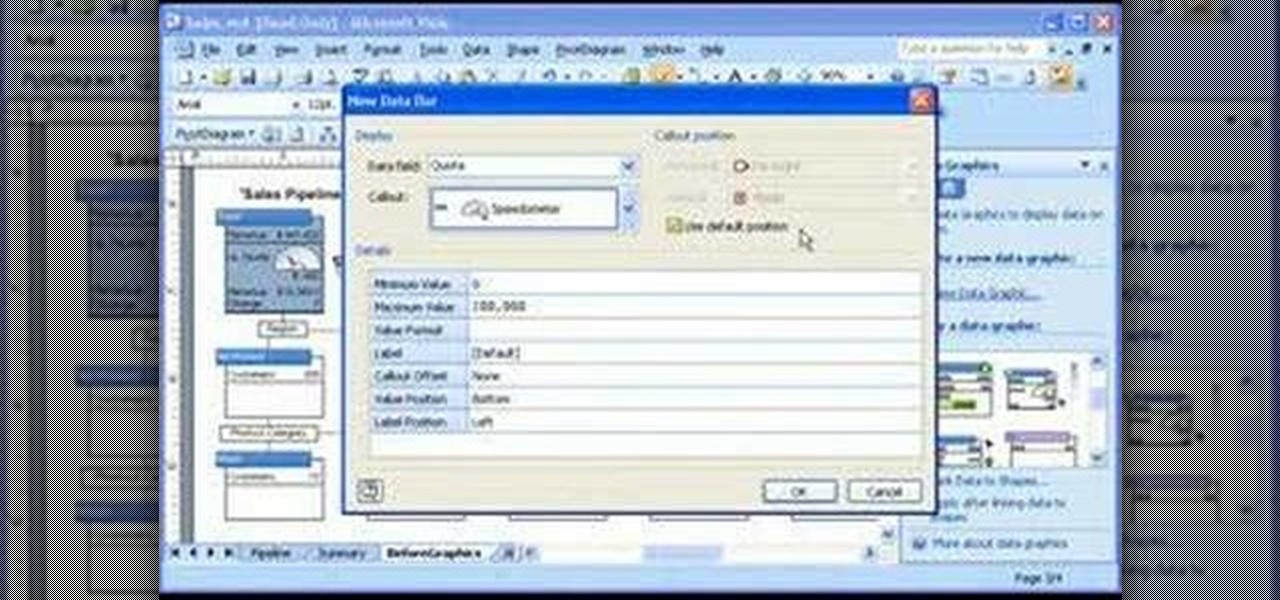
Take a look at this instructional video and learn how to customize progress meters, icons, color coding, and other graphical elements to emphasize sales trends, product performance, critical deadlines, or whatever information is contained in the data behind your diagram.

This video explains how to read a tape measure. Discover how tape measures are divided into different fractions. Color coding is also used to help with spacing things 16 inches on center.

Have you seen odd, square codes on some specific merchandise? These are called QR codes, or quick-response codes, and they are a type of bar code which your smartphone can read and then take you to a particular website, give you coupons or even a business card. Here's how you can get the most out of QR codes.

Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

If you want to embed a video on your website and customize the player so it doesn't look like crap, you've come to the right place:

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

The modern car is a complicated beast, but fortunately the engine code system makes figuring out what's wrong with a complex vehicle simpler. In this video you'll learn how to use a simple scanner to scan your car and figure out what has made the check engine light come on.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

In this video, we learn how to connect an Apple wireless keyboard to the iPad. This is great if you need to write something that requires a lot of typing. First, go to "system preferences" then click on "Bluetooth". Once you're in this, make sure the "discoverable" check box is not checked, then highlight your keyboard. In the bottom left hand corner click the minus sign, then click "remove". Now, on your iPad click "settings" then "general" then tap "Bluetooth". Almost right away you should ...

This how-to video explains how to fix DVD/CD player related issues with error code 31,32 or 19 in the computer that is having either Windows Vista or Windows 7 as their operating system.

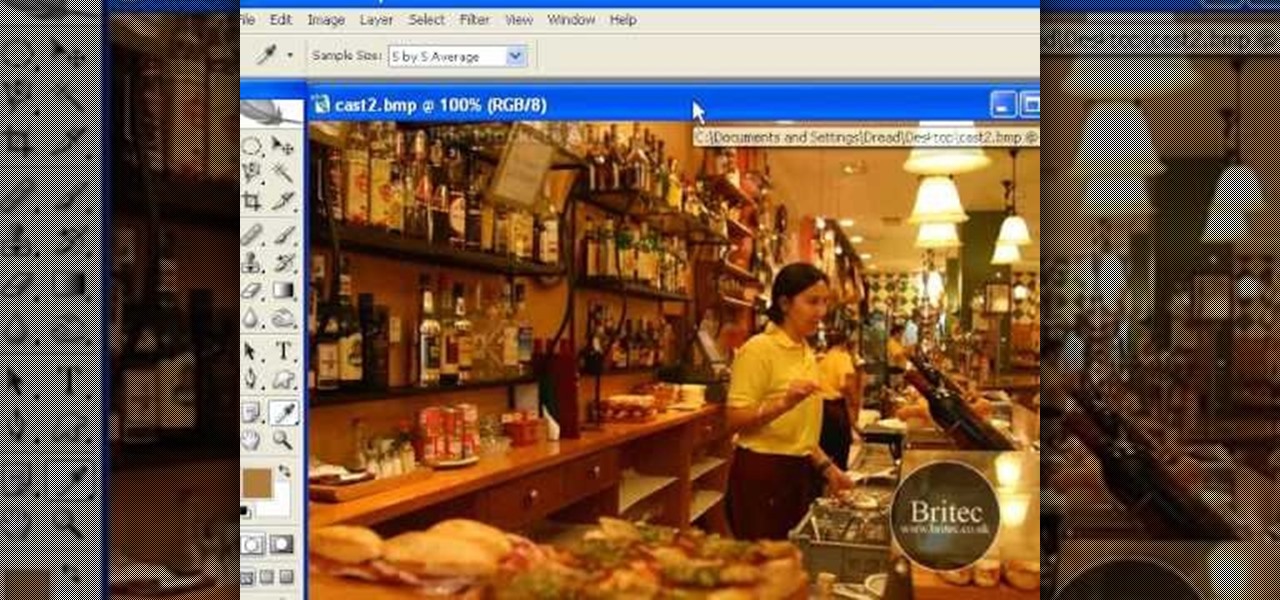
Looking for instructions on how to remove color casting when restoring photos in Photoshop? Look no further. Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from the folks at Britec Computer Systems. This video offers a step-by-step guide on how to get rid of color (or colour) cast when restoring scanned photographs.

Watch this video and you'll learn the simplest and most effective way of creating your own ethernet crossover cable. Starting with a general overview of what you'll be needing a crossover cable for, this video walks you step-by-step through the process of stripping the cable, separating the color-coded component cables within, organizing them for easy transfer to an rj45 adapter, and finally, crimping. Special detail is payed to organizing the colored cords, since they must be placed in preci...

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specific message.

Nostalgia sometimes gets the best of us—hence the reason we geek-out when we see emulators for SNES on Apple devices or N64 on Android.

A lot of people seem to have idle problems in their Honda vehicles, especially the Integra models. And idling problems are really hard to pinpoint. But you're in luck, because Eric has some great tips for hunting down those engine idling problems and eradicating them for good! Some of these tips include bleeding a cooling system, checking for vacuum leaks, reading the check engine light codes and diagnosing overheating.

Being able to load and unload .swf files to content areas in your website is useful, as it gives you the opportunity to show visitors a variety of different animations. This tutorial shows you how to use the Flash code to set up a system for loading and unloading multiple .swf files to the same area of your website.

Send a little dose of system shutdown to your friends or foes using these codes!

At the end of last year Google released Chromium OS, the source code to their soon-to-be-released operating system Google Chrome OS. This has allowed millions of people to preview the new OS and make suggestions. Do you want in on that action? This video will show you how to install and run Google Chrome OS on a Mac using a virtual machine like VMWare or Virtual Box. Now you can be a part of the future of operating systems. Maybe.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.