Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

The status bar is an omnipresent force on our Samsung Galaxy S3s; always there to give us that vital information about battery life, date and time, Wi-Fi access, and much more. But there's just something about that default black bar that's so...boring.

IF you have a Saturn S-Series and it's thrown a P0340 or P0341 error code at your on the scanner after the check engine light has come on, you might be wondering how your cam position sensor can be off if you don't actually have one in your car. Watch this video to learn exactly what this code means to your car and some thoughts on how you might fix it. Three words: spark plug wires.
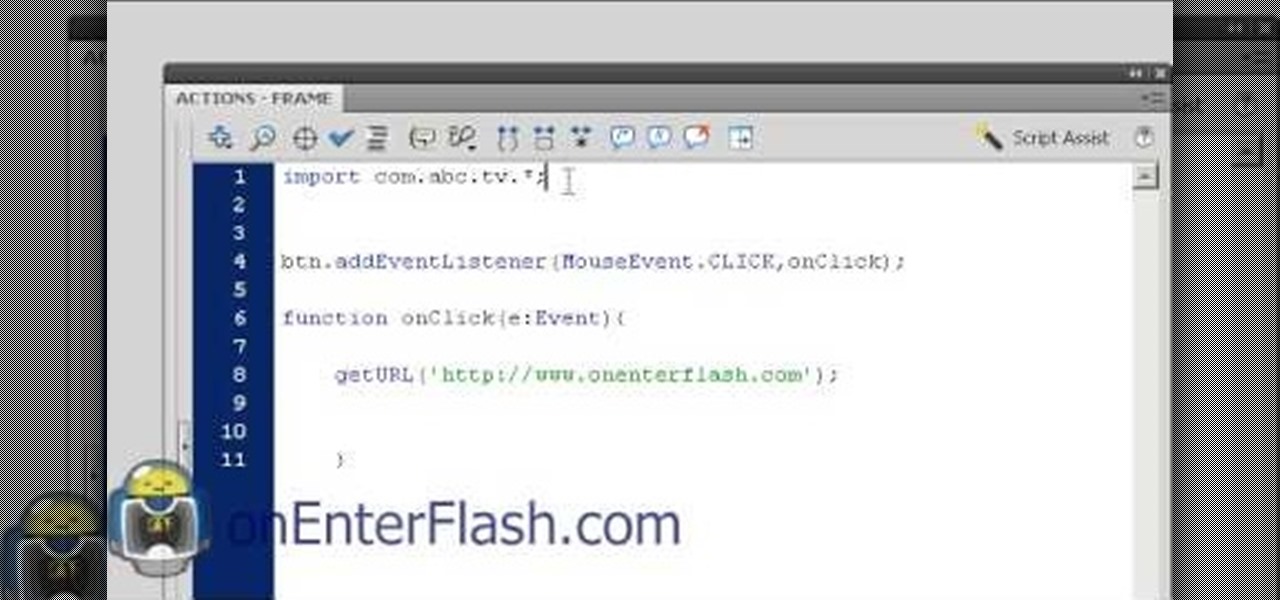
Custom classes are powerful tools in Flash CS4 that enable you to reuse sections of Actionscript 3 code more easily, greatly smoothing the software development process. This video will teach you how to create, integrate, and use custom classes in Flash CS4. Don't waste your coding time repeating yourself, watch this video.

It's time to go achievement hunting! In this video from the great men at Achievement Hunter, you'll be playing the game Skate 3. In this tutorial, you'll be finding out how to get some extra characters and use a couple of cheat codes. The characters are unique and different and the codes are pretty fun to use. So check out the tutorial and have fun!

First go to your Wordpress admin and click the "custom file editor" in thesis options. Now copy that code which is showing in the video and paste it in the custom.css file and click on the big green save button. Now select

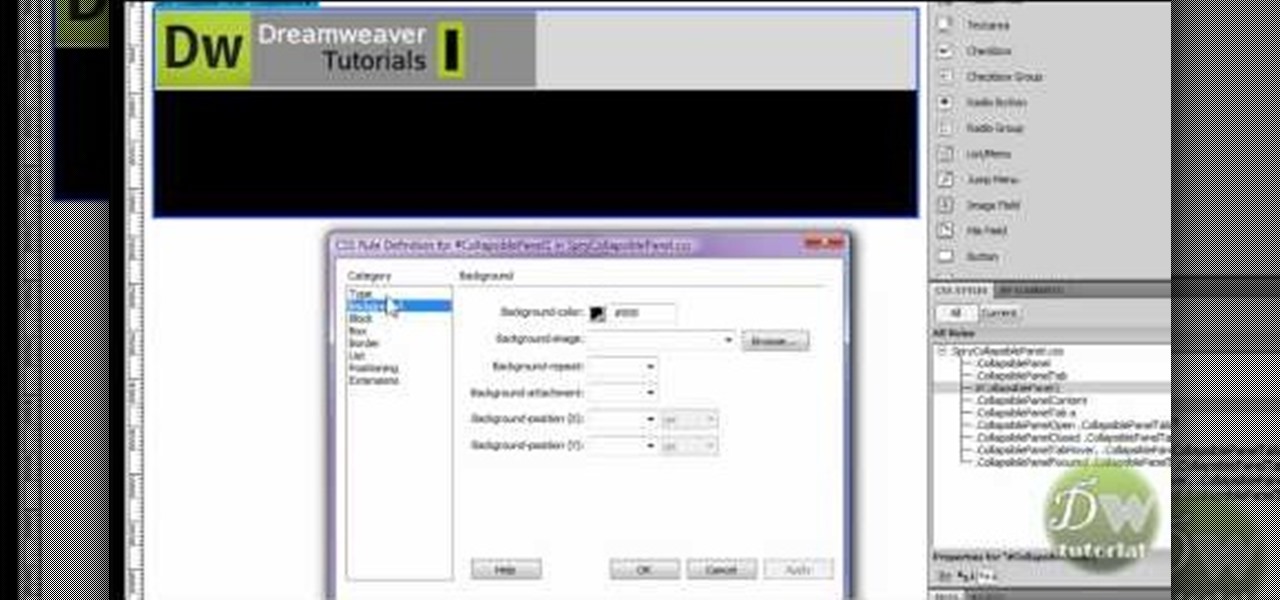
James from DreamWeaverTutorial.co.uk shows you how to use collapsible panels with the spry module in Dreamweaver CS4. The spry collapsible panel works similarly to an accordion widget, except it only has one section which features a tab panel and a content panel. When you click on the tab panel the content panel either appears or disappears (toggles on and off). You can add background colors, text colors, images, rollover effects and more, and James shows you exactly how to do all that in thi...

This video shows how to make a call of Duty Modern Warfare Text in Photoshop. For Call of Duty enthusiasts, learn how to make modern warfare text in Photoshop following the steps in this tutorial from Creative Ice Media Group. The video breaks down into two types of texts and how the two can be made. The tutorial goes over what font to use and what color code to use. In addition learn what auto glow color effects to use. Follow the steps in this video to learn how to make a Call of Duty Moder...

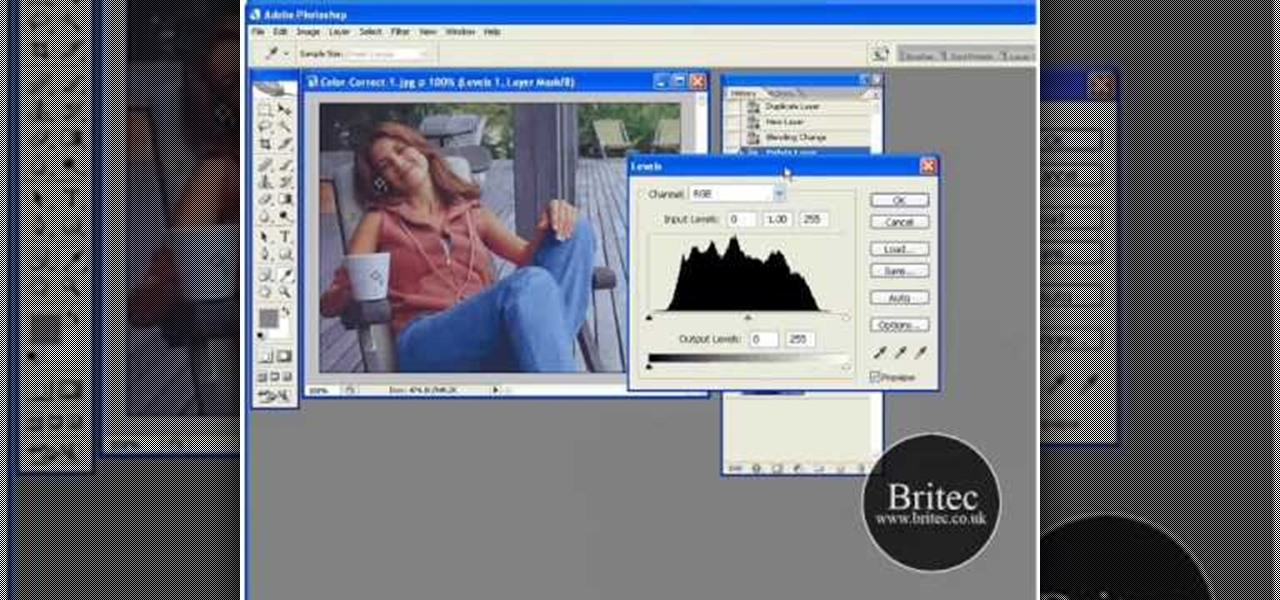
Want to color correct a digital image within Adobe Photoshop? Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from the folks at Britec Computer Systems. This video offers a step-by-step guide on how to color correct images using Photoshop's curve adjustment tool.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

In this tutorial, we learn how to cheat the airbrush system when applying makeup. The OCC makeup trial is great for someone who is just getting started as a makeup artist, and doesn't have an airbrush system. You an use this makeup with a nice brush, depending on which one works best for you. You can go from light to full coverage with this makeup, and play around with the colors until you find the one that works best for your skin. If you have a friend with different skin tone, you can split...

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

Learn how to eliminate cord clutter with the folks from Martha Stewart's REAL SIMPLE. Nothing is more annoying than a pile of messy cords. Those dozens of wires around your home?in your kitchen, by your computer, behind your TV?can be a tangled nuisance. Control cord clutter with these quick tricks and clever organizing products. Let REAL SIMPLE guide you on the best solution to eliminate cord clutter.

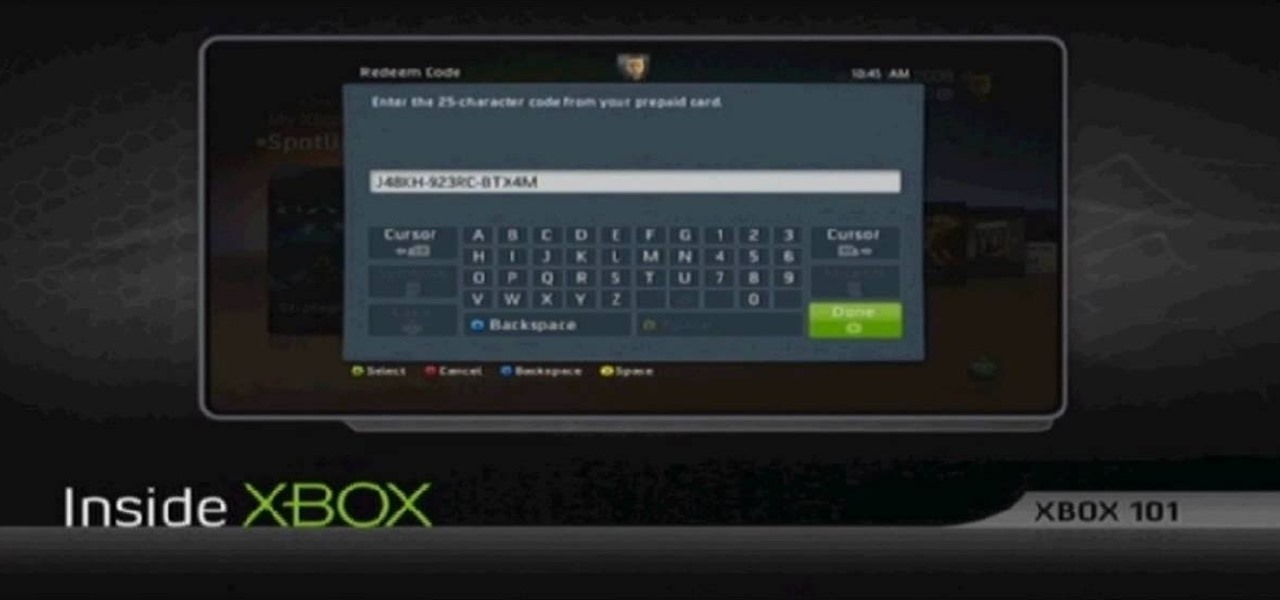
In this tutorial, we learn how to redeem a code for Microsoft Points (Xbox 101). First, you will need to log onto your Xbox Live account on your console. From here, pick a game that you want to purchase. Make sure you research the information about the game and you really want it, because you cannot return it. After this, choose the option to redeem a code and then type in the code for your Microsoft Points. After you do this, you will be bale to purchase the game that you want and you will h...

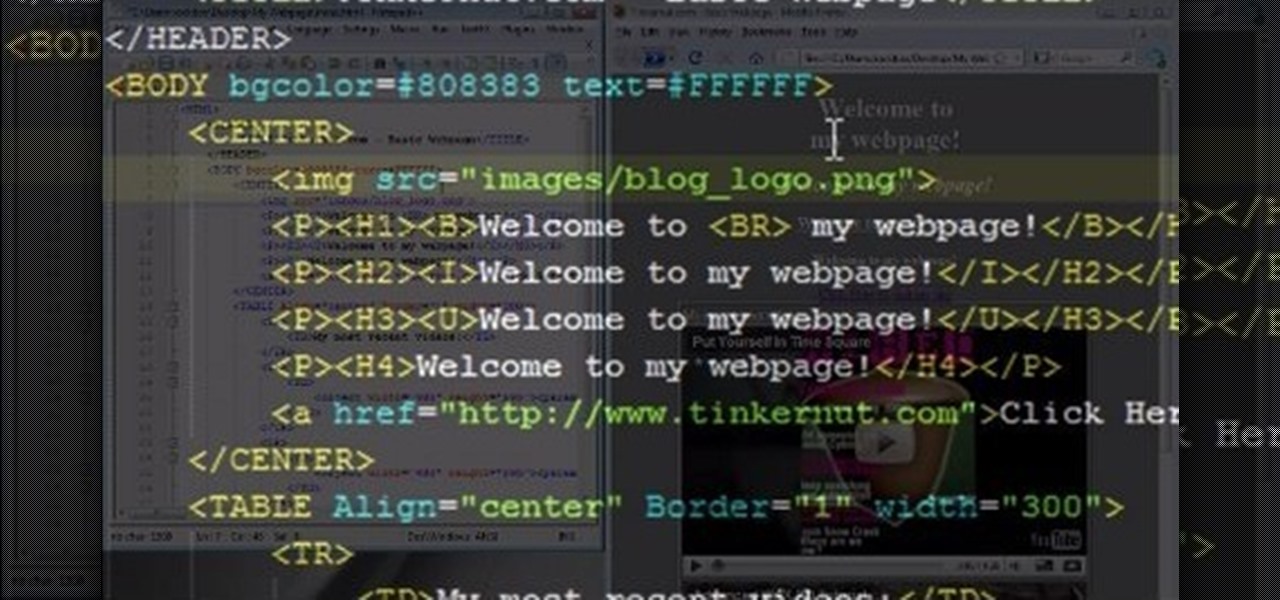
You can create a free website using HTML. HTML is hyper text mark up language. Create a folder "my webpage" with all of the images and information for the webpage. Use notepad to write the HTML for the website. Notepad plus is the best which can be found on Sourceforge. Open the browser and the notepad and begin to construct. These codes will help in the creation of the page: <html> opens instructions </html> closes instructions. These are called tags. One opens the commands or instructions a...

Balsamiq is a really cool software suite that allows you to create Apps visually without having to write any code! This two-part video lecture will introduce you to Balsamiq and show you how to use it to create your own cool Apps. If you want to learn Balsamiq, you really couldn't do any better than this.

You've seen code blues called on TV, but how about in real life? If you are becoming a nurse it is important to know what goes on as part of a code blue situation. This nursing how-to video presents a mock code blue presentation with faculty. Follow along and learn what is involved in caring for a patient that has gone into code blue.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to enjoy this feature.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

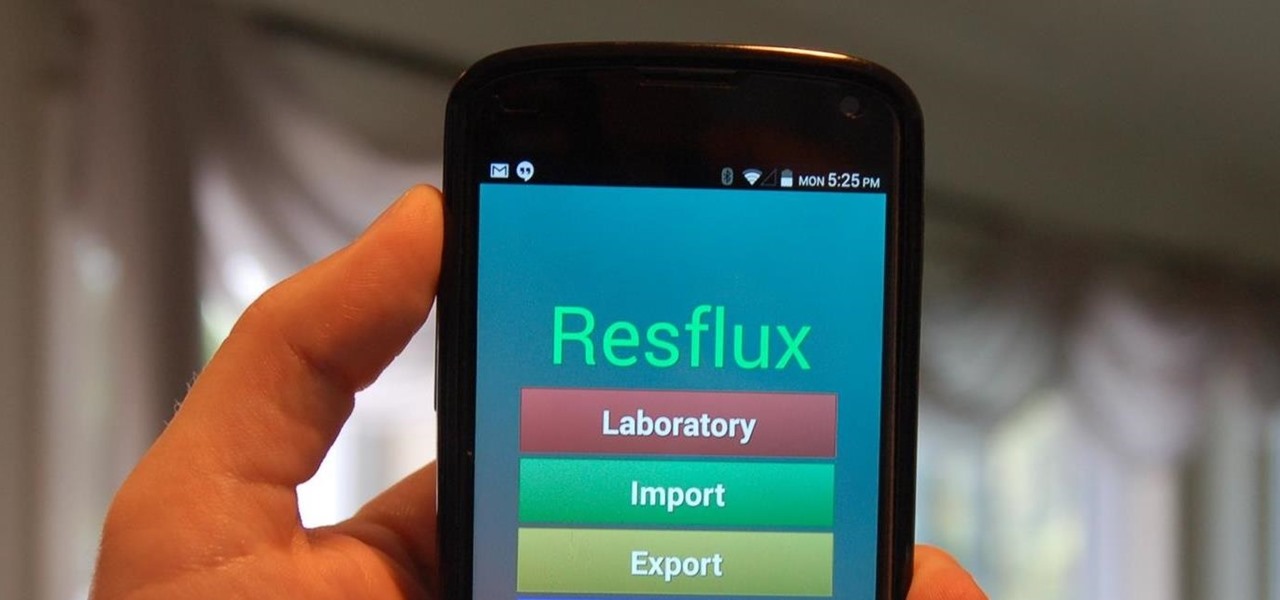
Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

How do you know if the Beats By Dre Studio headphones that you are about to buy online are genuine? Always ask the seller to use the youVerify app before you buy. Smarter Selling, Safer Shopping.

When you use a scanner to look for error codes on a car, many can show up at once and confuse you as to the nature of the problem. Often, all of the codes are responses to the same problem. Watch this video for tips on interpreting multiple error codes.

Watch this software tutorial video to learn how to uncover Outlook 2007's best features: drag-and-drop calendaring and color-coding. This how-to video will allow you to use drag-and-drop calendaring in Outlook to make your calendars better.

This software tutorial shows you how to use the plug-in Colorista to color correct in Final Cut Pro. This is an introductory tutorial which will cover the basics for new Colorista users within the Final Cut Pro software. An easy-to-use color correction plug-in that delivers great results quickly from within Final Cut, After Effects, Motion, Premiere Pro, or Avid systems.

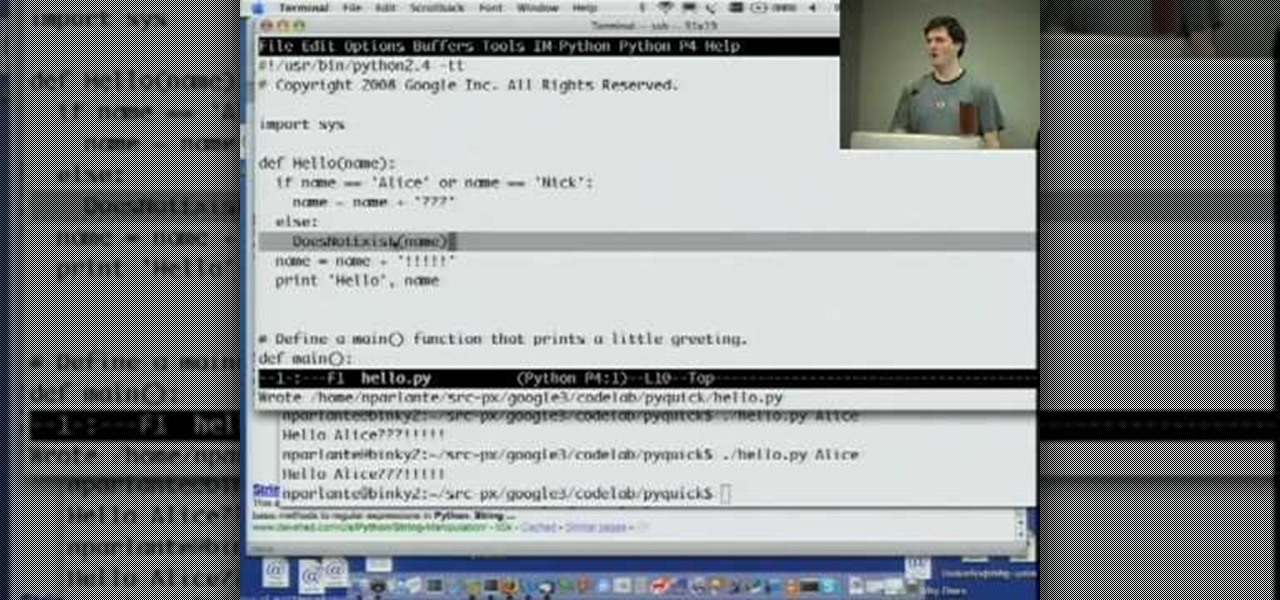
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...