The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

This is a very easy and exciting new Halloween nail polish design! The color code is based on Halloween pumpkin and Halloween night combination to suit the Halloween mood perfectly.

Interested in learning how to code and create a modern website from scratch? Let this eight-part video tutorial series be your guide. It's easy and this series presents a complete, step-by-step overview of the process. For more information, including detailed instructions, and to get started creating and coding your own website groups, take a look.

Revision3 Internet Television and Tekzilla Daily with Veronica Belmont demonstrate how to unlock Vista's super user mode. First, open the start menu and type CMD. Right click the command prompt and select the run as administrator option. Type the code net user administrator / active:yes. Hit enter. Your system should reply with the command completed successfully message. Then, the next time you restart your system, you'll see the administrator as an option in the welcome screen. If you use th...

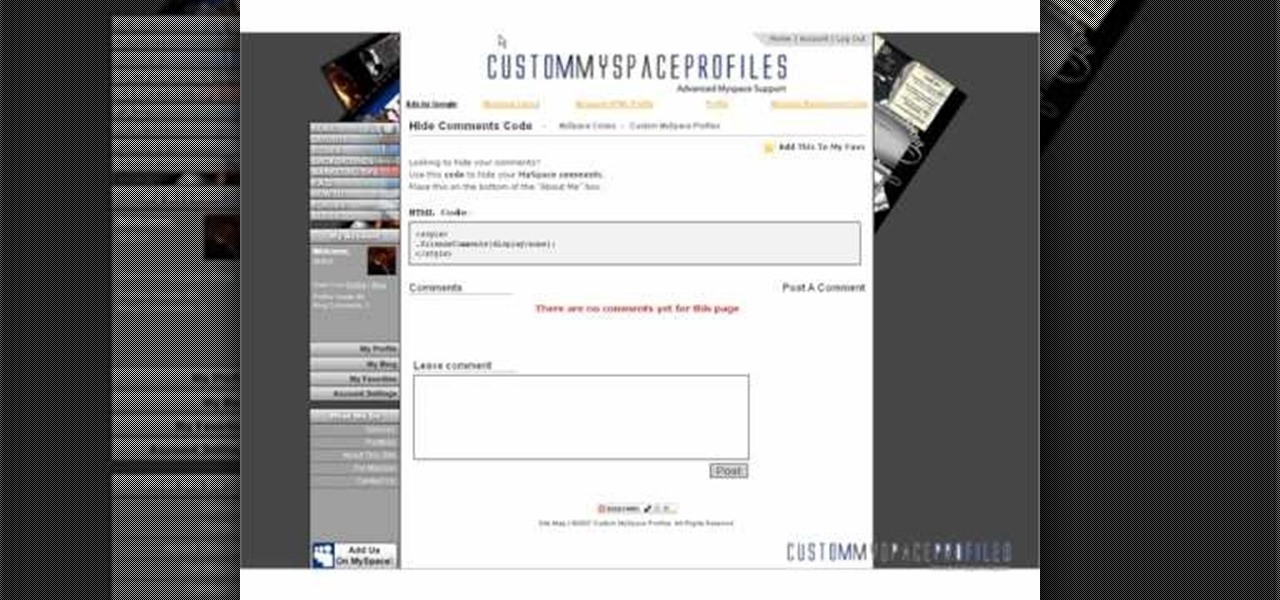
This tutorial will show you how to hide your MySpace comments using the custom MySpace profiles website. All you have to do is visit the website mentioned in the video, and copy a simple code in the codes section. The code that you will be looking for in the list is the 'Hide MySpace comments' code. The code is then pasted in to your MySpace profile under the 'About Me' section. If you follow the directions entirely in this tutorial, your MySpace profile comments will be disabled until you re...

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

Photo retouchers can do a lot with Photoshop, from making a so-so gal look like a model to virtually applying makeup and cleaning up ugly cellulite. But don't you wish you could look perfectly airbrushed at the first take?

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

If you don't have a car, or just prefer to take public transit to work, you know that an unexpected change in the weather can quickly...er, dampen your day. If you're not expecting it, rain or snow can turn your trip into a long, hellish ordeal—especially if you bike.

Arceus is a legendary God Pokemon released on Pokemon Diamond/Pearl. Arceus can be caught without Action replay codes but this video will show you exactly how to access and catch Arceus in Pokemon Diamond using codes from Action Replay.

In this video tutorial, learn how to unlock (or jailbreak) your Blackberry, with these step-by-step instructions. This video also shows you how to get a IMEI Unlock Code from "Unlock To Talk", however, this code costs money. You can access a code here.

In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack Bejeweled Blitz with cheat codes (07/21/09).

This software tutorial shows you how to use the Colorista plug-in for After Effects to do basic primary color correction. Colorista is an easy-to-use color correction plug-in that delivers great results quickly from within Final Cut, After Effects, Motion, Premiere Pro, or Avid systems. The tutorial is for new Colorista users.

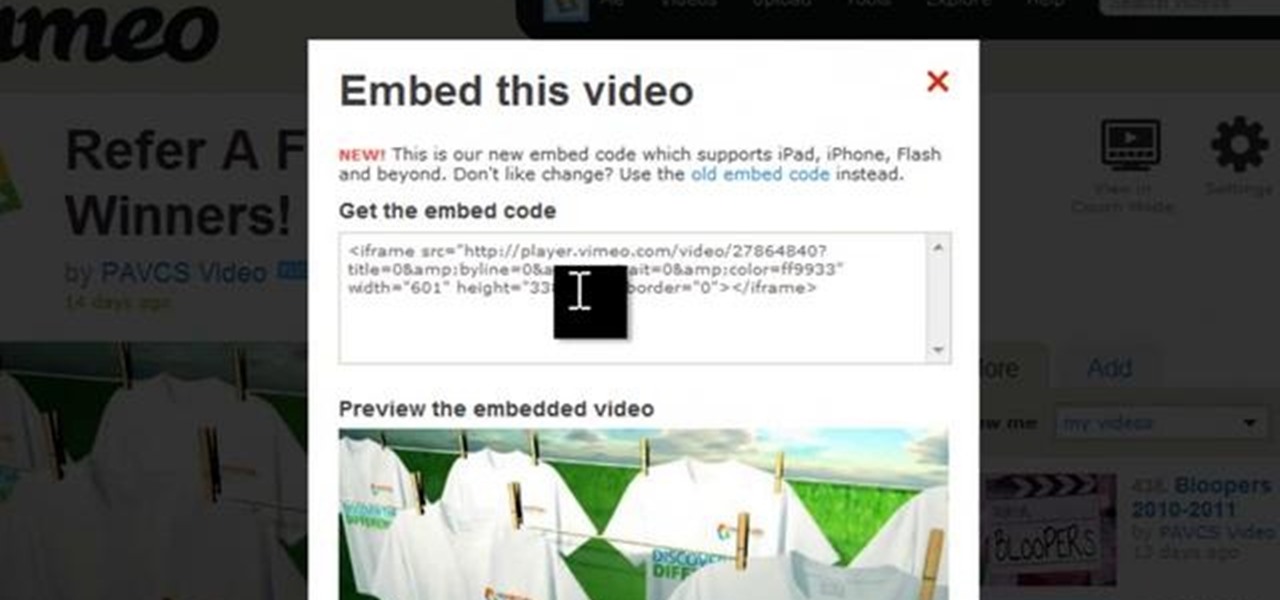
If you want to embed an iFrame into a Blackboard 9.1 page, you'll need to grab the code from whatever source you want (YouTube, Vimeo, Google Docs, etc.) and use the Build Content option in Blackboard. Select "Item" under the "Create" menu and turn off the Text Editor so that you can properly paste the code in. Take a look at this tutorial to see all the steps in action.

If the speedometer on your car isn't working and the check engine light is on, get your scanner out and look for code P0500. If you get that code, watch this video to learn a quick easy fix for the problem.

Just because your car shows an error code doesn't mean you should pull any parts. This video will show you how to confirm error code P 0340 on a Nissan (Bad Cam Sensor) by using a lab scope to check the cam sensor.

Despite being on the Xbox Live Arcade and PlayStation Network, Scott Pilgrim vs. the World: The Game is actually a pretty hard video game. But, things get a whole lot easier with this cool play modes available with a few secret cheat codes. This video tells you those cheat codes to enable zombie mode, boss rush mode, and two others in the XBLA game.

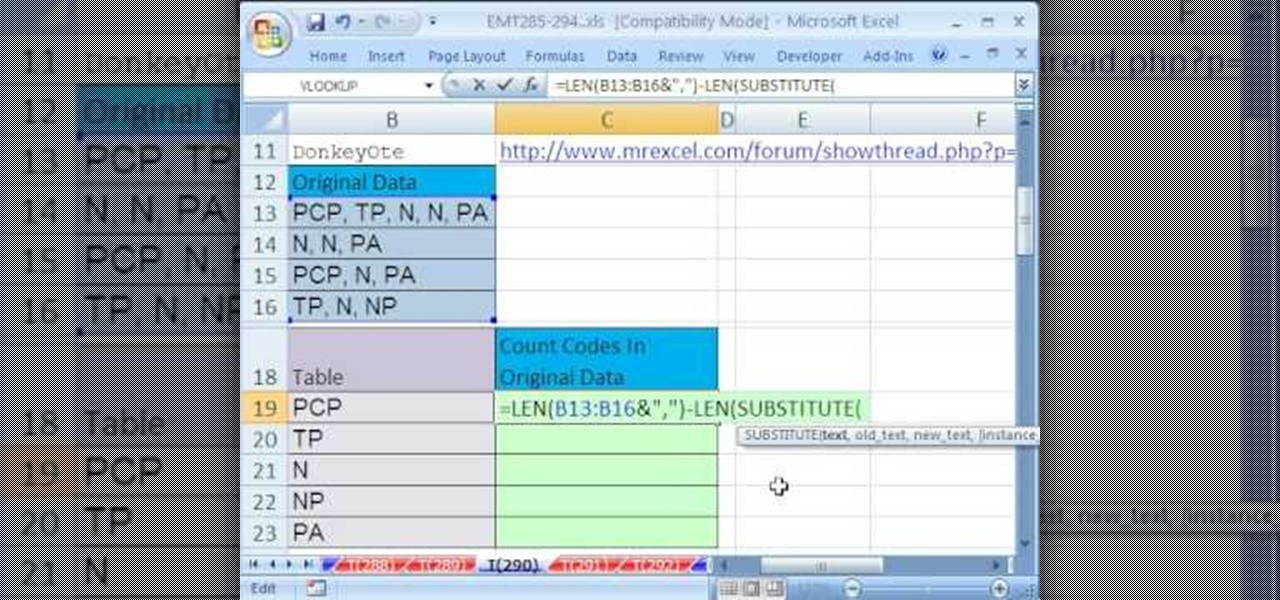
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 290th installment in their series of digital spreadsheet magic tricks, you'll learn how to count codes from a column of text strings that have multiple codes.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

In Android 10, Google is letting you adjust the accent colors to give your phone a bit of flair. When combined with the new system-wide dark mode, you are looking at eight different color combinations. That is seven more than we had in the previous version and seven additional ways to help your phone stand out.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!