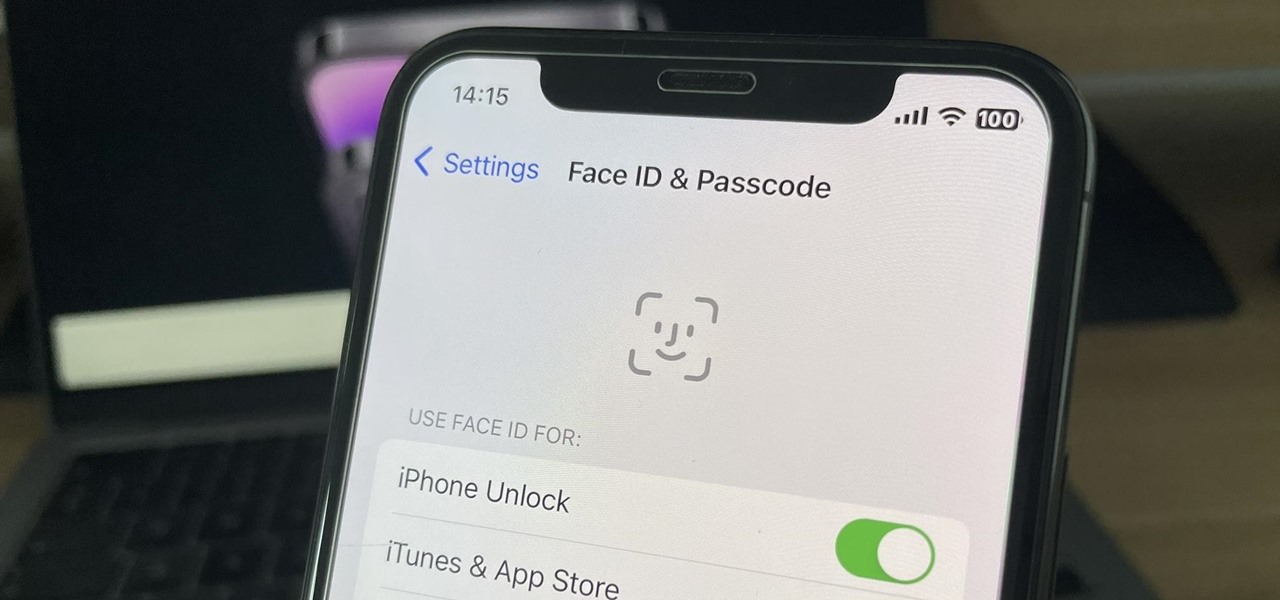
The iPhone 13 and iPhone 14 series models have a new feature on iOS 16 that lets you use Face ID when your iPhone is in landscape orientation. This is most helpful when trying to make purchases in apps and games where you use your iPhone rotated on its side. If you're having issues using Face ID in landscape mode, there may be some easy solutions to getting it working.
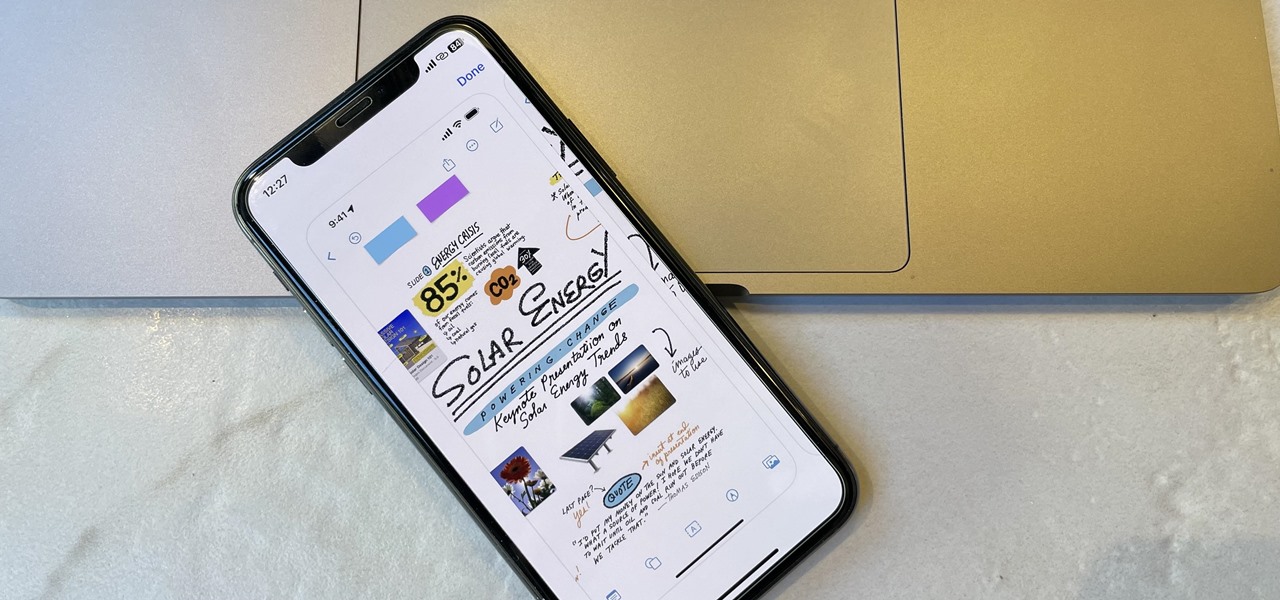
When you need to take notes, sketch out projects, brainstorm with others, create mood boards, or map out ideas without constraints, look no further than Freeform, Apple's new collaboration-friendly digital whiteboard.
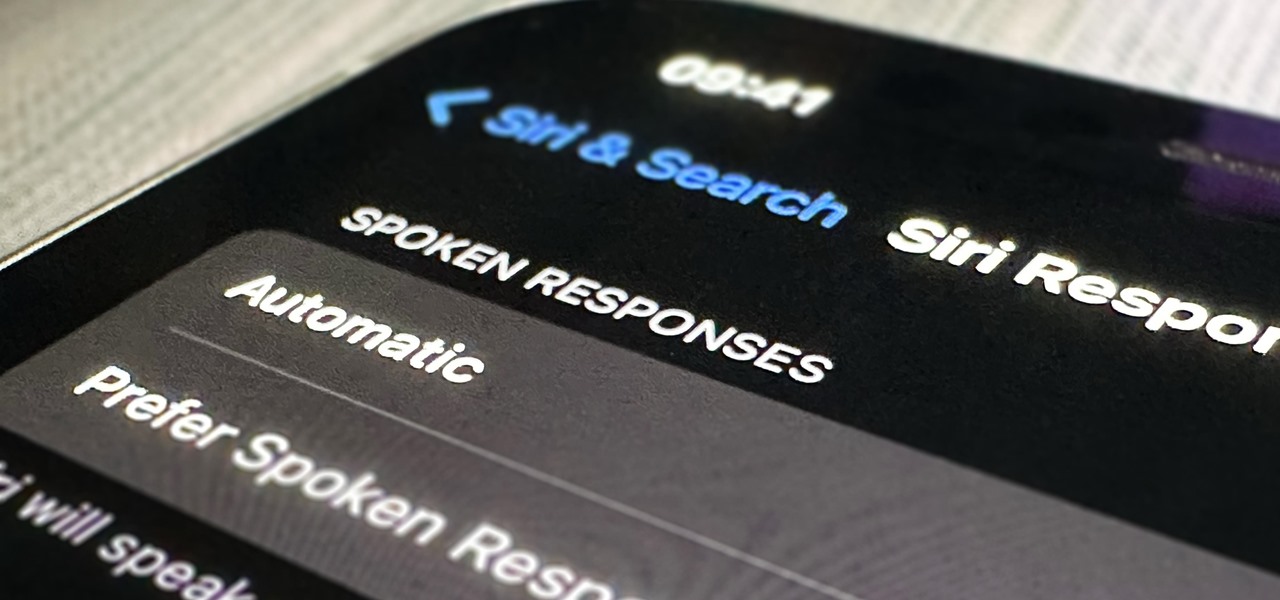
Apple's iOS 16 update changes the way Siri speaks responses, defaulting to a more "automatic" solution that lets your iPhone decide when it should or shouldn't talk out loud. That may sound like a good thing, but it makes it harder to keep Siri quiet when you only want muted responses. Thankfully, a new iOS update gives you back some control.
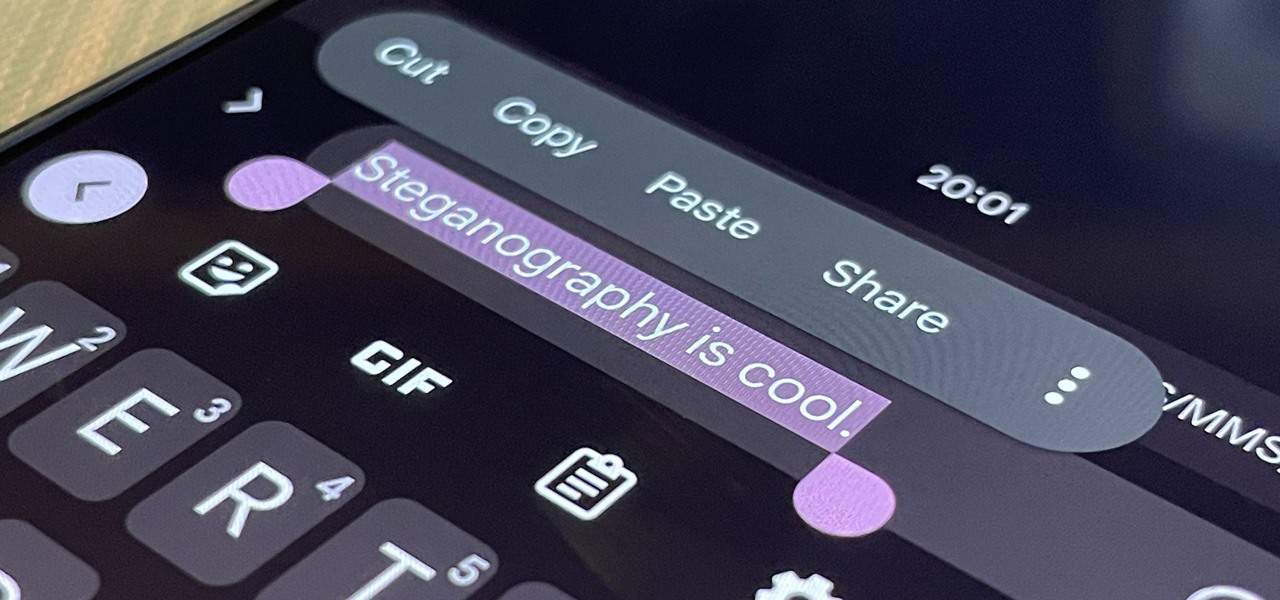
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

Part of the mainstreaming of augmented reality is learning to adopt new habits around the hardware delivering these groundbreaking next-gen interface experiences.

I drop my smartphone a lot. Like an absurd amount of times. Practically multiple times a day. So it's surprising that my iPhone 12 Pro has lasted nine months without a cracked screen yet. Part of that has to do with the late-2020 model's durability, and the other part is thanks to my protective case.

In the Facebook app for Android and iOS, the shortcut bar has a few necessary tabs to go home and view notifications and settings. But other tabs can make the interface feel cluttered if you don't use them often enough — or at all. Thankfully, there's a quick trick to get rid of them for a cleaner navigation bar.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

I always keep my iPhone's Portrait Orientation Lock on so that my screen doesn't randomly rotate while I'm lying down. However, there are certain apps that I do turn it off for. It's kind of a pain since you have to swipe down the Control Center and toggle the orientation lock — but that ends now. Instead of doing it manually, a new iOS update can automate app orientations for you.

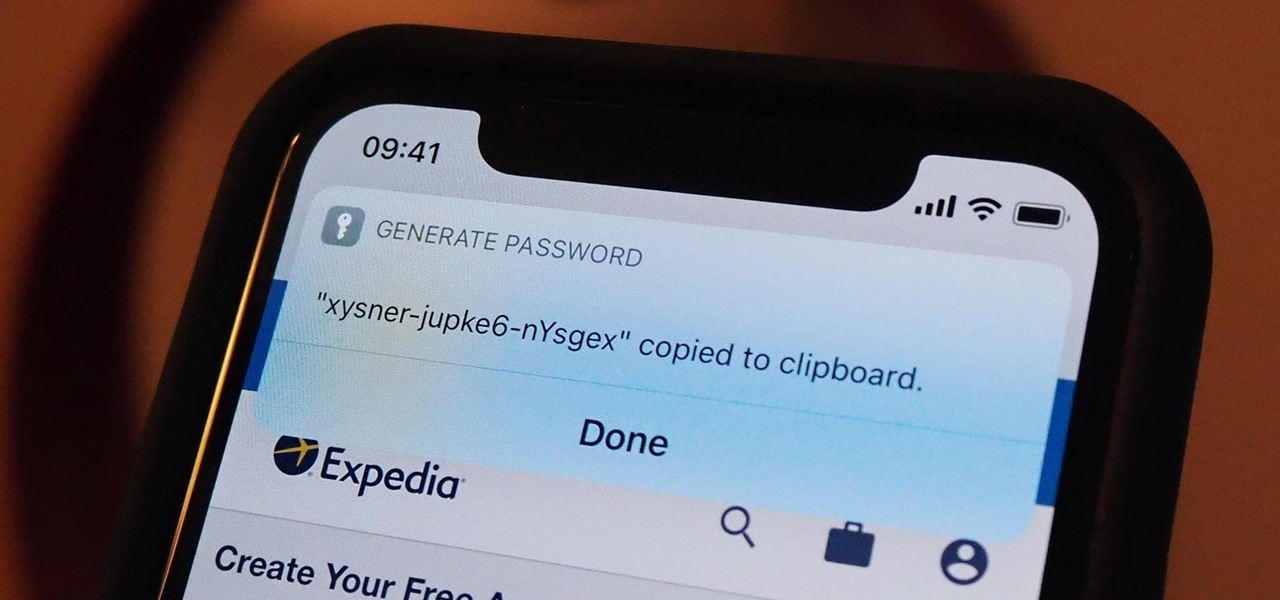
Apple's password manager, iCloud Keychain, lets you securely save important login credentials for apps, websites, and services that sync up across all of your Apple devices — iPhone, iPad, iPod touch, and Mac. One of its biggest highlights is that it can create strong passwords for you. Unfortunately, it doesn't always work, and in those cases, there are other ways to generate random, strong passwords.

Except for the second-generation iPhone SE, all new iPhone models omit the Home button. In its place, the Side button takes charge, taking care of tasks like pulling up Siri, activating AssistiveTouch, and opening Apple Pay. If you swap your older Home button model for an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you'll need to relearn simple actions like shutting down and restarting the device.

There have been third-party iOS apps for live conversation translations, and Google Assistant pushed out its own feature for iPhone last year. Still, iOS 14 now has a default translator for real-time multi-language talks in person. So you can finally chat with people who use a different language without missing anything or having to install any complicated apps on your device.

You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

Since iOS 8, it's been possible to use third-party tools such as Bing Translator and Microsoft Translator to translate foreign language webpages in Safari into your primary language. Now, in iOS 14, there's a better way to do it.

While there are other photo-editing apps to choose from on the App Store, Apple Photos is more than good enough for most needs on the iPhone — and things only get better with age. With each new iteration of iOS, Apple refines and improves Photos for the better, and iOS 14 adds a lot of new features into the mix.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

The smartphone market is stagnating. Without hordes of new users rolling in every year, the best way to boost profits nowadays is to poach customers from the competition. That's exactly what Apple appears to be doing with iOS 14.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

There's a serious issue with Google Fi's service for iPhone that prevents sending any MMS pictures via the Messages app. The problem doesn't affect all iPhone users on Google Fi, but if you're like me and keep getting that frustrating "Not Delivered" alert, there's a fix.

Who here binges TV on a regular basis? I know I do. Never before have we had so many options for watching our favorite shows, especially when you consider how easy it is to stream from anywhere on a mobile device. But sometimes, all that choice gets a little overwhelming. What services are really worth the money? Where should you be investing your Friday-night binges?

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.