It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

OnePlus, whose phones always challenge for the title of best spec-to-price ratio, releases two main devices every year. There's the primary flagship in late spring, then an iterative update with the "T" suffix in fall. Typically, there's not much difference between the two, but this year, OnePlus is mixing up the formula a bit.
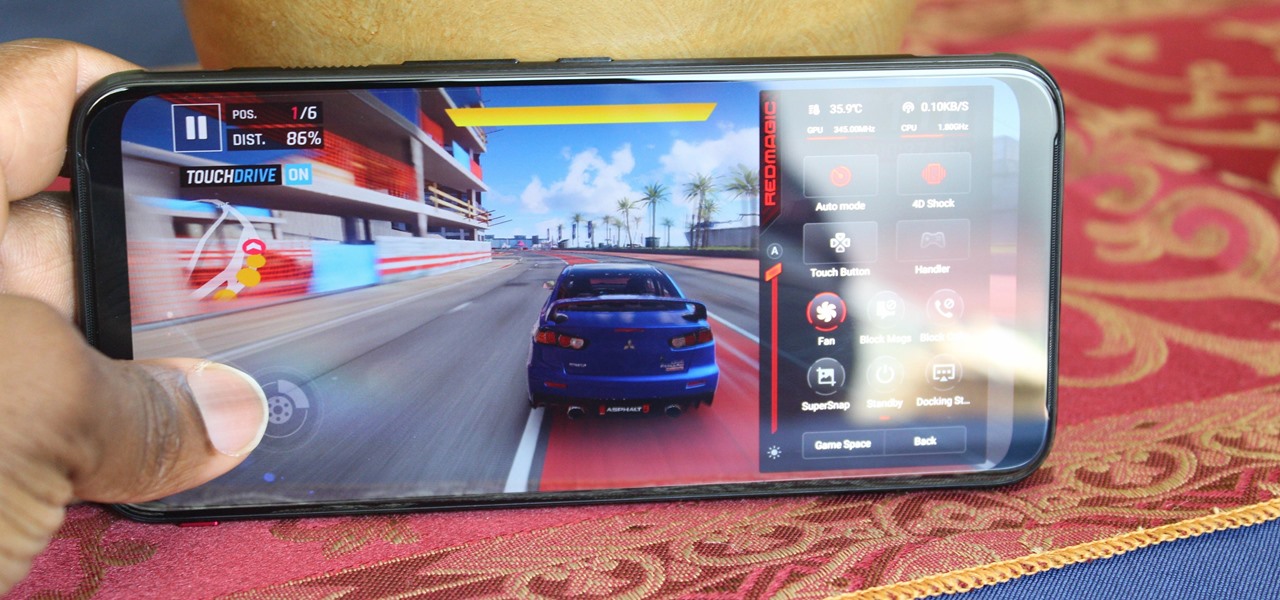
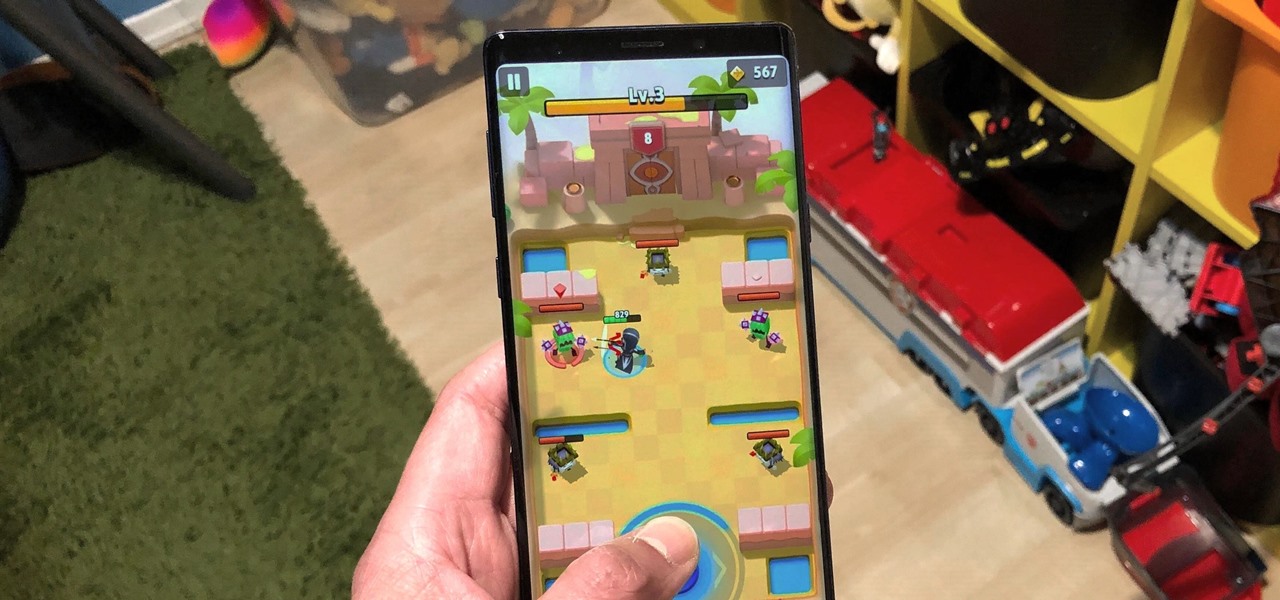
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.
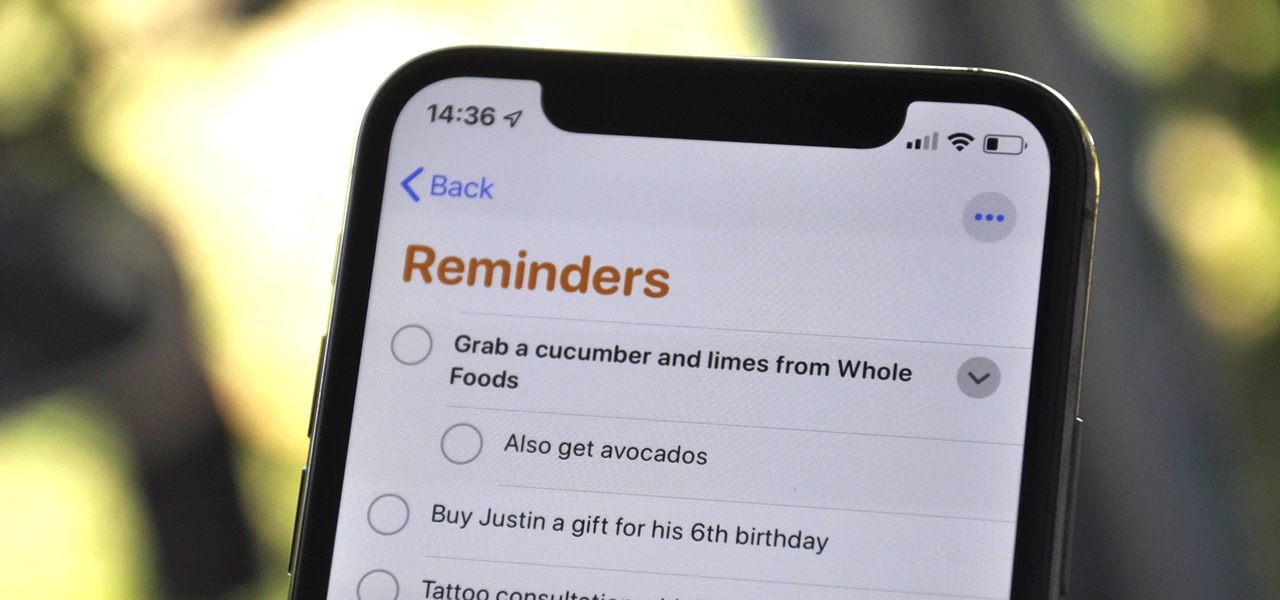
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked.

Safari has always done a great job at letting you browse the web, but it has never so much as offered a way to download files locally. Other apps have stepped in to help fill the gap, but they never felt as integrated into the iPhone as a native downloads manager would. They aren't needed anymore though, because Apple added one in iOS 13, pushing Safari on the iPhone closer to its sibling on the Mac.

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

As part of the iOS 11 update, Apple added a document scanner function that creates high-quality digital copies of physical documents, but it was only available inside the Notes app. With iOS 13, Apple has built its scanner right into the Files app, enabling you to quickly create PDFs with your iPhone and do more with them.

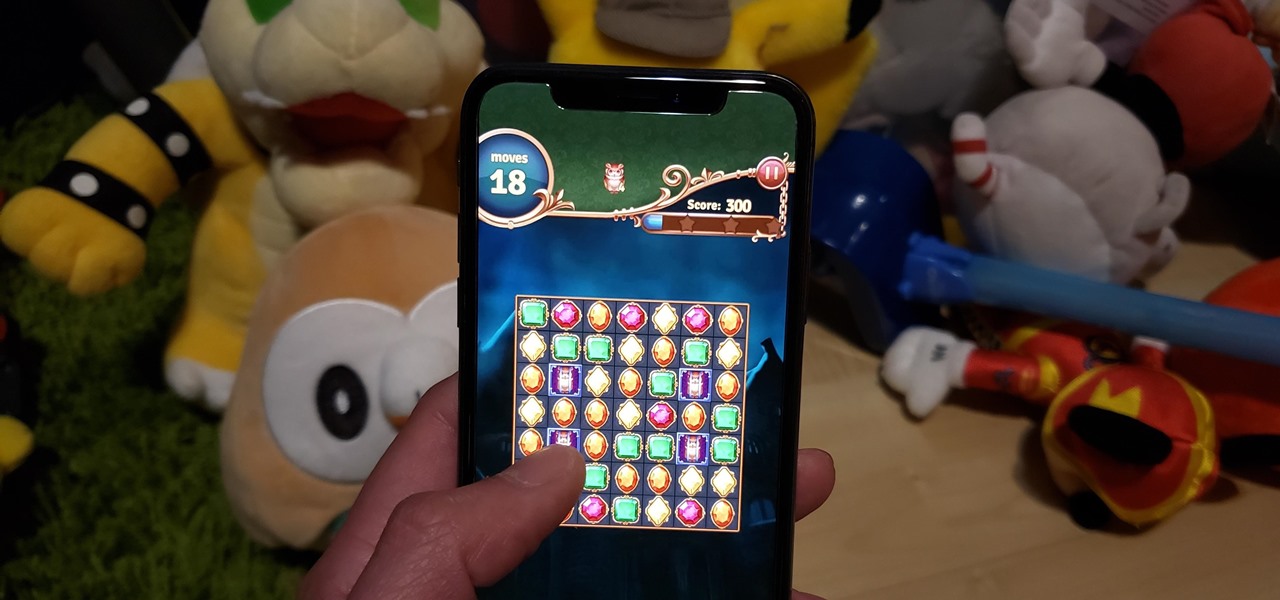
Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

There are many reasons to use Filmic Pro if you're a mobile videographer. Chief among them is its automated controls, called "pull-to-point" sliders. These pull-to-point controls not only allow you to manually adjust focus, zoom, exposure, ISO, and shutter speed before and during the action, they also let you set start and end points to automate each function, leaving you free to focus on filming.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

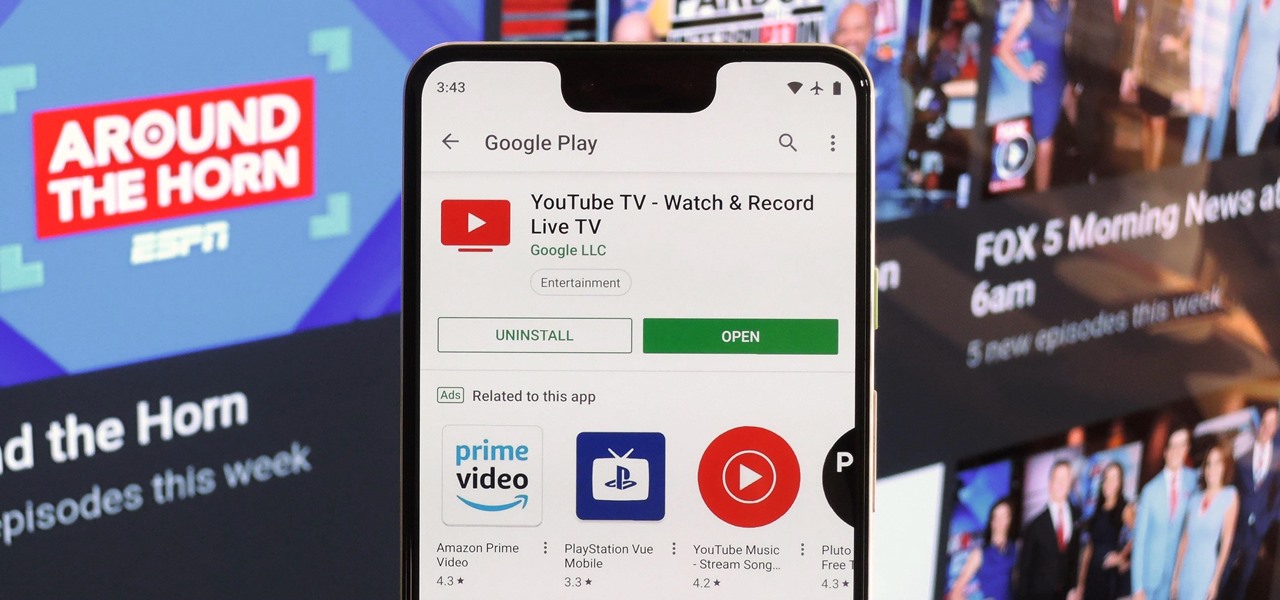
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

The great thing about competition is it drives innovation. But when a company tries to one-up its competitor, it's not always with something brand new. Sometimes, one party will draw heavy inspiration from the other — but hey, it's still all good, because the consumers benefit either way.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.